Investigating Swap File URL's
03/09/2022 Saturday
The swap file is a Windows feature that takes advantage of space on the hard drive when the RAM fills up to improve the RAM performance. Swap file enhances the efficiency of modern Windows apps as well. It stores data for starting applications faster and is a part of the virtual memory management system of Windows operating systems. Swap file is similar in concept to Page file. However, the Swap file stores contents of inactive processes whereas the Page file stores some parts of the active process. Details about the page file can be found here.
Digital Forensics Value of Swap File URL's Artifact
When a user starts an app and stops using it, the system stores text-based artifacts to the swapfile.sys for a faster and seamless app return. A swap file can give details about how an app runs on the system. By capturing URL's, we can collect essential information related to the case at hand.
Location of Swap File URL's Artifact
Swap File ULR’s artifact is extracted from the swapfile.sys file located at C:\swapfile.sys
Analyzing Swap File URL's with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract Swap File URL’s from Windows machines and what kind of digital forensics insight we can gain from the artifact.
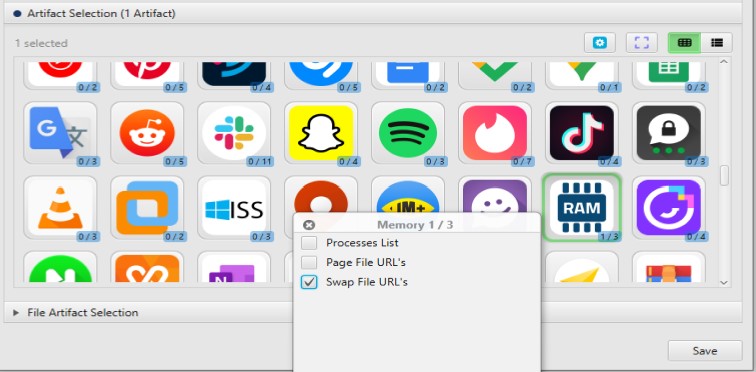
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select the Swap File URL’s artifact:
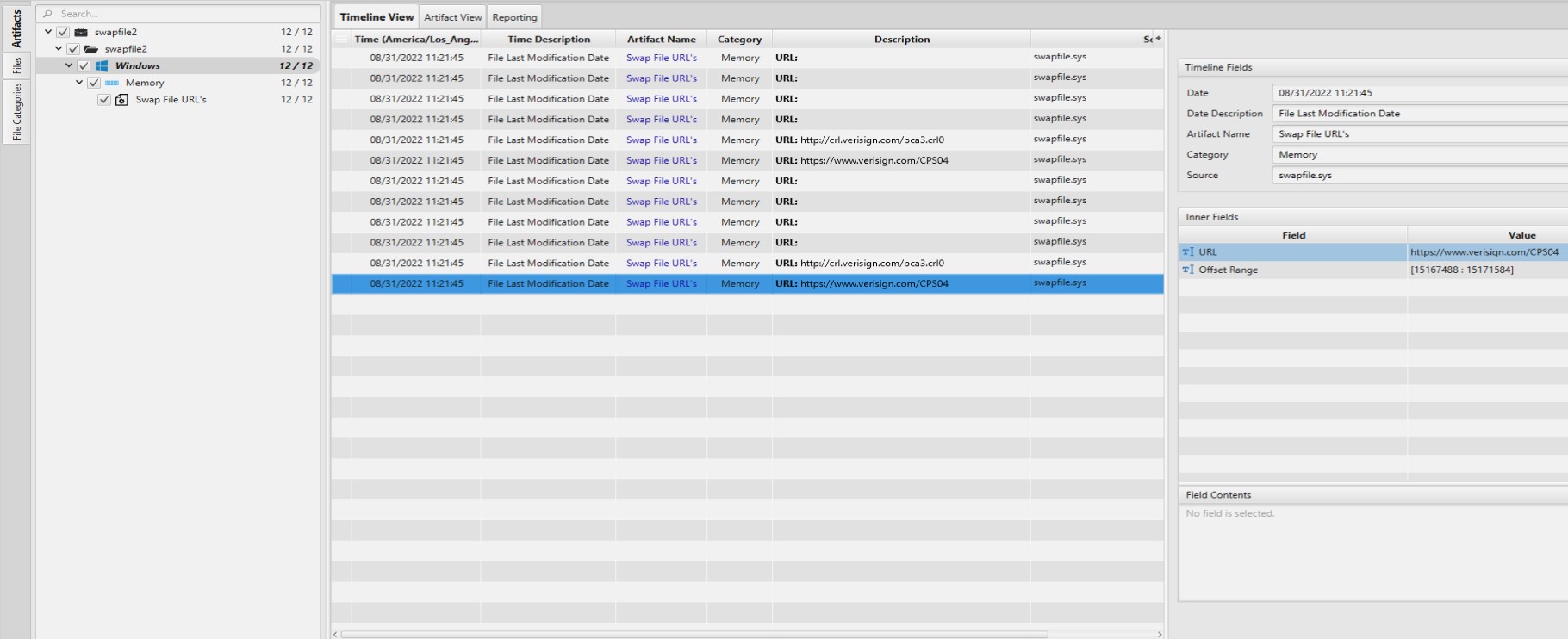
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of the Swap File URLs artifact in ArtiFast.
Swap File URL's ArtifactThis artifact contains the URLs extracted from the swapfile.sys
- File Last Modification Date - File last modification date.
- URL - URL.
- Offset Range - Offset range.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
