Investigating Page File URL's
25/03/2022 Friday
Operating systems have the ability to use a portion of the hard drive as a virtual memory when the RAM becomes full. Microsoft Windows uses a paging file, called pagefile.sys to store chunks of data that do not currently fit into the physical memory. Although reading and writing data from the page file is slower than the actual RAM, the paging file can store data that are less frequently used, leaving the RAM for more frequently accessed data.
Digital Forensics Value of Page File URL's Artifact
Pagefile.sys is considered an important source of evidentiary information during investigations. The analysis of the file can reveal valuable information such as visited URL's that can be relevant to the case under investigation.
Location of Page File URL's Artifact
Windows OS supports up to 16 paging files; however, normally only one is used. The pagefile.sys is a hidden system file that is located at C:\pagefile.sys.
Analyzing Page File URL's Artifact with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Page File URL's artifact from Windows machines
and
what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Page File URL's artifact:
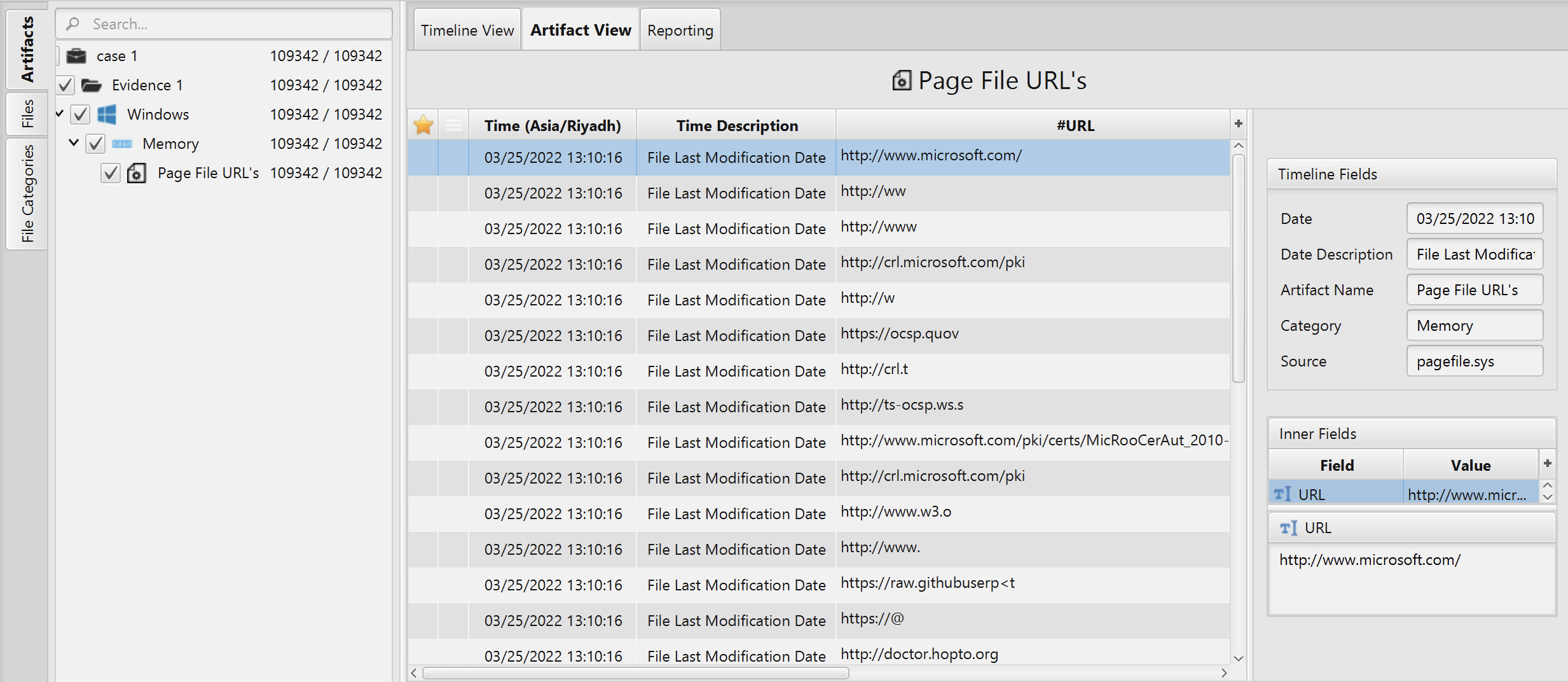
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is the details you can view using Page File URL's artifact in ArtiFast Windows.
Page File URL's Artifact
- File Last Modification Date
- Offset Range
- URL
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
