Investigating Artifacts Using YARA Rules with ArtiFast
27/08/2022 Saturday
Yara Rules are used for identifying and classifying malware by creating rules that search for specific binary or textual patterns. YARA rules work like a piece of programming language and identify PE and ELF files based on the conditions defined in the ruleset.
Digital Forensics Value of YARA Rules
YARA is a powerful tool for forensic analysis, threat intelligence, and threat hunting. Ever since the first introduction of YARA rules by Victor M. Alvarez, the tool has been used in malware classification, incident response, and analyzing executables in a corporate network. Therefore, having YARA rules at hand for digital forensic analysis can make malware detection faster.
YARA Rules in ArtiFast
After ArtiFast has been installed, if there isn’t a “yara_rules” folder within the ArtiFast installation directory, we need to create it. YARA rule files should be placed in this directory.
- yara.max_file_size - defines the maximum file size.
- yara.min_file_size - defines the minimum file size.
- yara.checked_extensions - file extensions to process. You can increase the extensions according to your needs.
- yara.rule_timeout - defines the upper limit for YARA Rule processing time in seconds for a single file.
Analyzing Yara Rules Artifact with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to analyze artifacts from Windows machines using YARA Rules and what kind of digital forensics insight we can gain.
After you have created your case and added evidence for the investigation, and created the YARA Rule in the specified directory, at the Artifact Selection phase, you can select YARA Rules from the Grid View:

Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of YARA Rules in ArtiFast.
Yara Rules Artifact
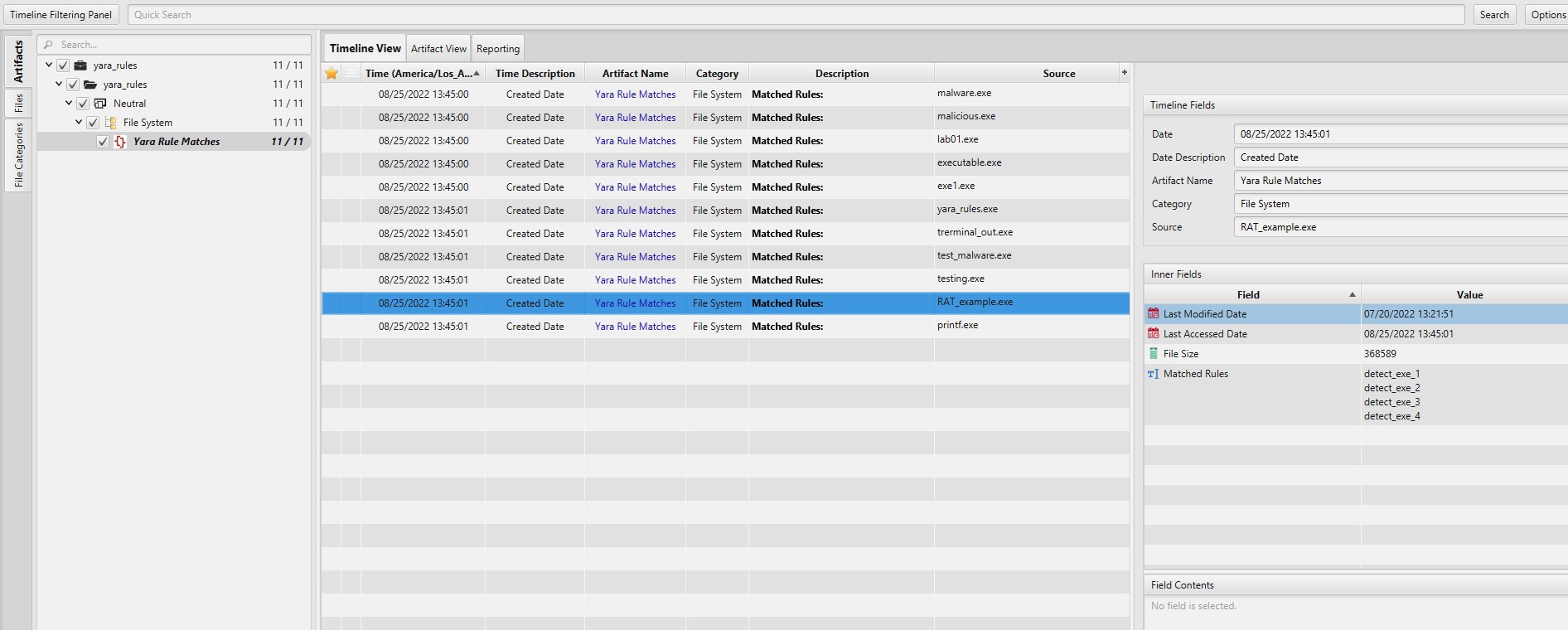
The artifact contains results that match the YARA Rule set by the user. The details you can view include:
- Created Date - Executable file's creation date.
- Last Modified Date - Executable file's last modified date.
- Last Accessed Date - Executable file's last accessed date.
- Matched Rules - Matched YARA Rules.
- File Size - Matched file size.
For more information or suggestions, please contact: asmaa.elkhatib@forensafe.com
