Investigating Windows Management Instrumentation (WMI)
16/06/2022 Thursday
Windows Management Instrumentation (WMI) is the infrastructure for management of data and administrative operations on Windows operating systems. WMI contains a vast variety of tools for controlling Windows operating systems locally and remotely. WMI is used especially in enterprise networks for getting information about accounts, processes, configuring networking and running commands over the Windows Remote Management (WinRM).
Digital Forensics Value of Windows WMI Artifact
WMI is installed by default on all Windows platforms. Even though it is a system administration tool, an attacker can use WMI for data collection, VM and AV detection, code execution, lateral movement, persistence and data theft. Therefore, this artifact can be very useful during investigations involving a targeted, dedicated adversary. Investigating Remote WMI usage over the WinRM is important as well. Windows Remote Management is not enabled by default; however, even when enabled, examiners may overlook the malicious usage of the protocol. Thus, it is important to regularly conduct network forensic analysis of TCP ports 5985 and 5986.
Location of WMI Artifact
The information gathered by WMI is stored in a collection of system files called repository.
The default location of WMI is at "C:\Windows\System32\Wbem\Repository\"
Structure of WMI Artifact
This part provides a general overview of WMI architecture. WMI is constructed using Object-Oriented hierarchy and structured in parent-child relationship. Root Namesapace is at the top and child of a namespace is a namespace or a class. Being a special namespace, the Root expands into Child namespaces. A child namespace is the parent of one or more classes. Classes expand into Objects. Objects are the leaves which contain the information. WMI has a query language similar to SQL and called WQL. Using the tree structure and hierarchy, administrators can query objects and retrieve information. WQL runs on the Windows terminal and WMIC (WMI Command-line), which is a command-line interface to WMI.
WMI components
- WMI repository: this is the database that stores static data related to WMI.
- CIM Object Manager: CIM is a Common Information Model, which is a standard for defining management information of systems. CIM Object Manager is the intermediary between an application and WMI providers.
- WMI API: it provides access to the WMI infrastructure. Applications can make API calls that are passed down to the CIM Object Manager and sent to the WMI providers.
- WMI Consumer: this is either a monitoring application or a management application (like PowerShell).
- WMI Service: an intermediary between WMI providers and WMI repository.
- Managed Objects: any logical or physical component that can be managed via WMI.
- WMI providers: an object that monitors, reads and collects data programmed to manage. Some WMI providers are built-in operating systems, others are developed by C++, VB or PowerShell.
- Classes: is the implemented functionality of a WMI provider..
- Methods: some classes have methods that offer specific data and results for querying the required information easier.
%SystemRoo%\System32\wbem\Repository path contains
- CIM (Common Information Model),
- index.btr: index file, structured in binary tree,
- index.map: transaction control file,
- objects.data: CIM repository wherer managed resource definitions are stored,
- objects.map: transaction control file,
- mapping.ver: XP only, specify the index of curret mapping file.
Analyzing WMI with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to analyze WMI artifact from Windows machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select WMI artifact:
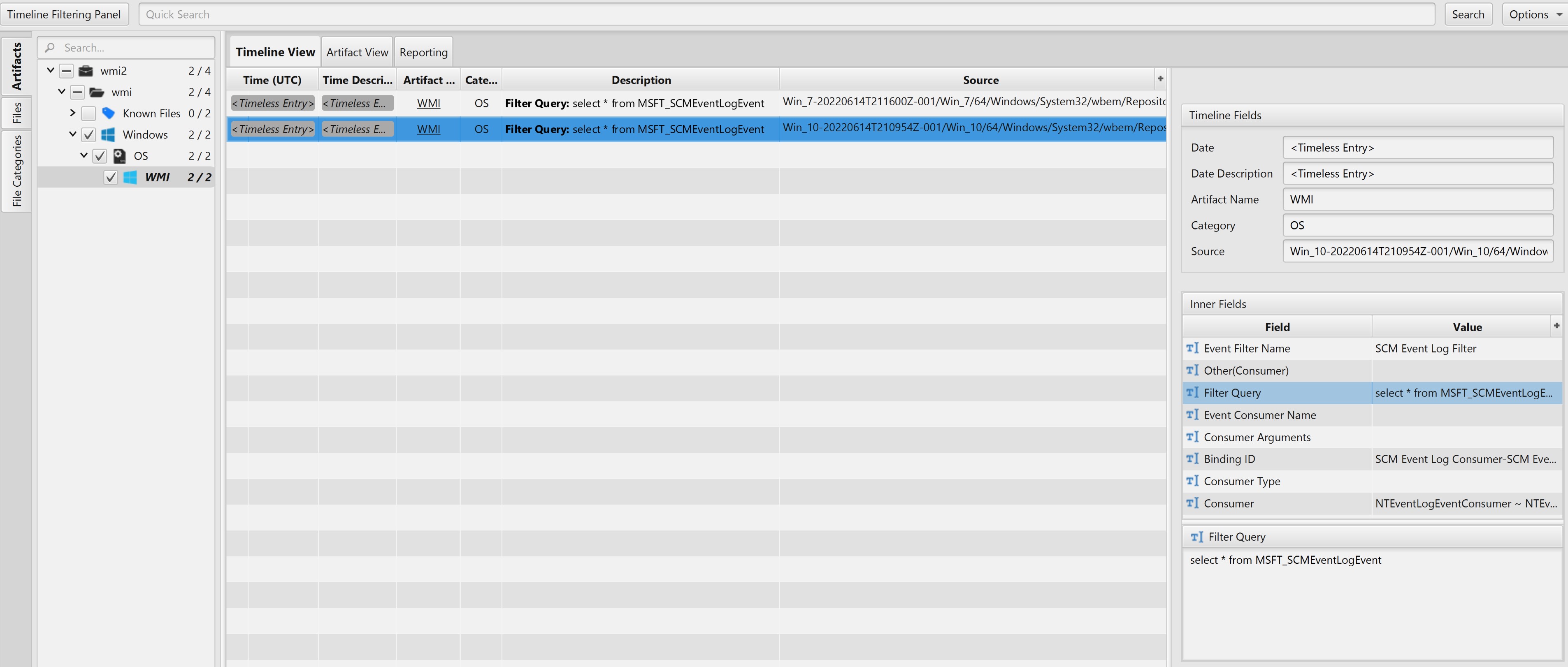
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of the WMI artifact in ArtiFast.
WMI Artifact
The artifact contains WMI repository content. The details you can view include:
- Binding ID - Binding of the query and the index details.
- Event Consumer Name - Name of the WMI consumer.
- Consumer Arguments - Arguments for customizing filter events that are caught by the consumer.
- Consumer Type - Consumer can be system or user defined.
- Consumer - Consumer defines what the system should do with any events caught by the event filter.
- Event Filter Name - An event filter is a WMI class that describes which events WMI delivers to a physical consumer.
- Filter Query - WMI query details.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
