Investigating WinZip
31/08/2022 Wednesday
WinZip is a cross-platform trialware that helps users to zip, unzip, share, organize and manage files. WinZip was introduced in 1991 and developed based on MS-Dos PKZIP archive format, which Phil Katz invented. WinZip is one of the most popular file compression tools. Currently, it supports PDF editing and operating system optimizing features in addition to compression features.
Digital Forensics Value of WinZip
Given its popularity and wide usage, WinZip is considered an essential source of evidentiary information during investigations. Forensic analysis of WinZip can mainly provide details about zipped, archived, and shared files.
Location and Structure of WinZip Artifacts
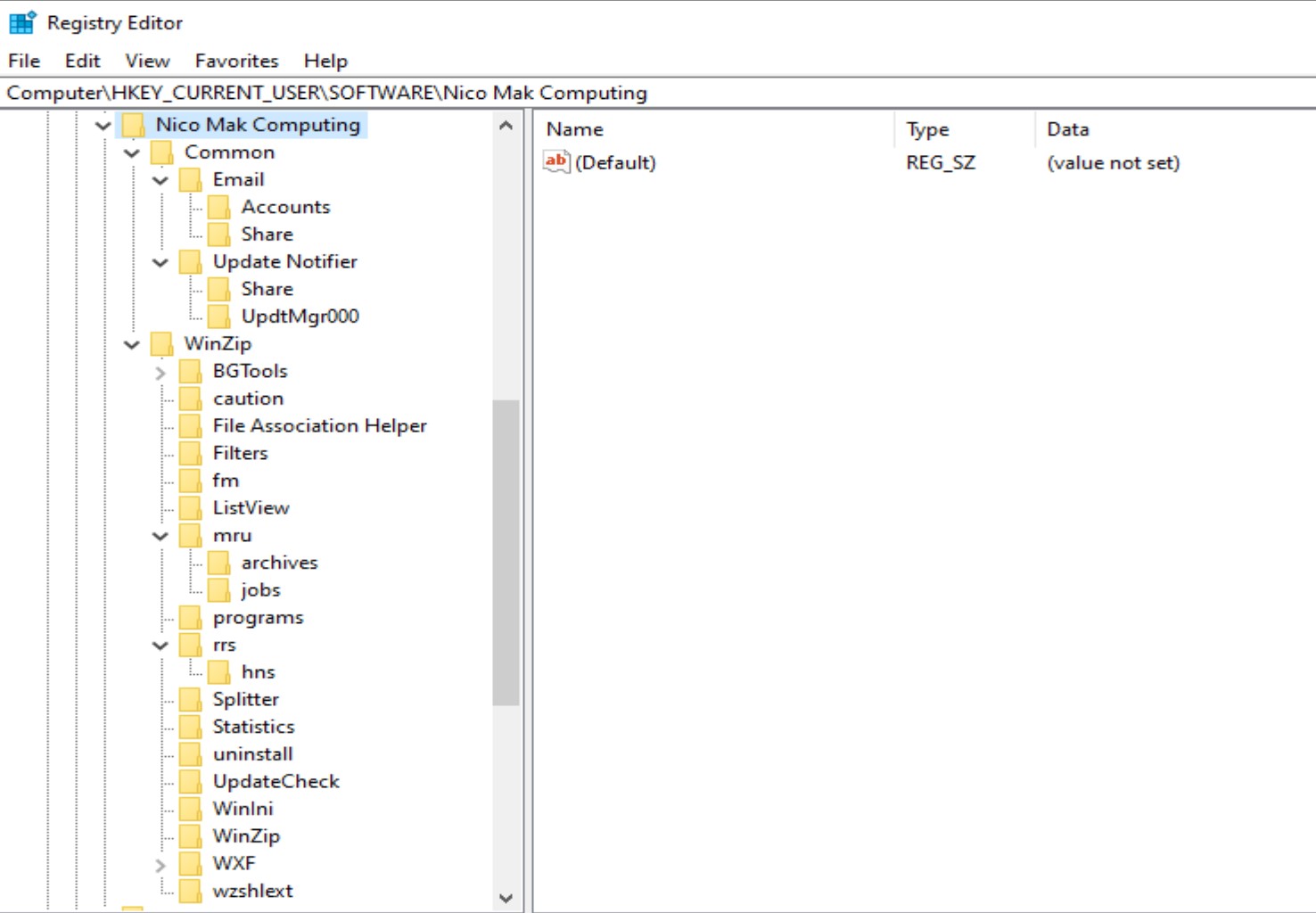
WinZip artifacts are located at NTUSER.DAT\Software\ Nico Mak Computing
The figure below shows the WinZip artifact-related keys in the registry. WinZip artifact contains the user’s email address, extracted zip files, archived files, and user directories.
Analyzing WinZip Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract WinZip artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifacts.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select WinZip artifacts:

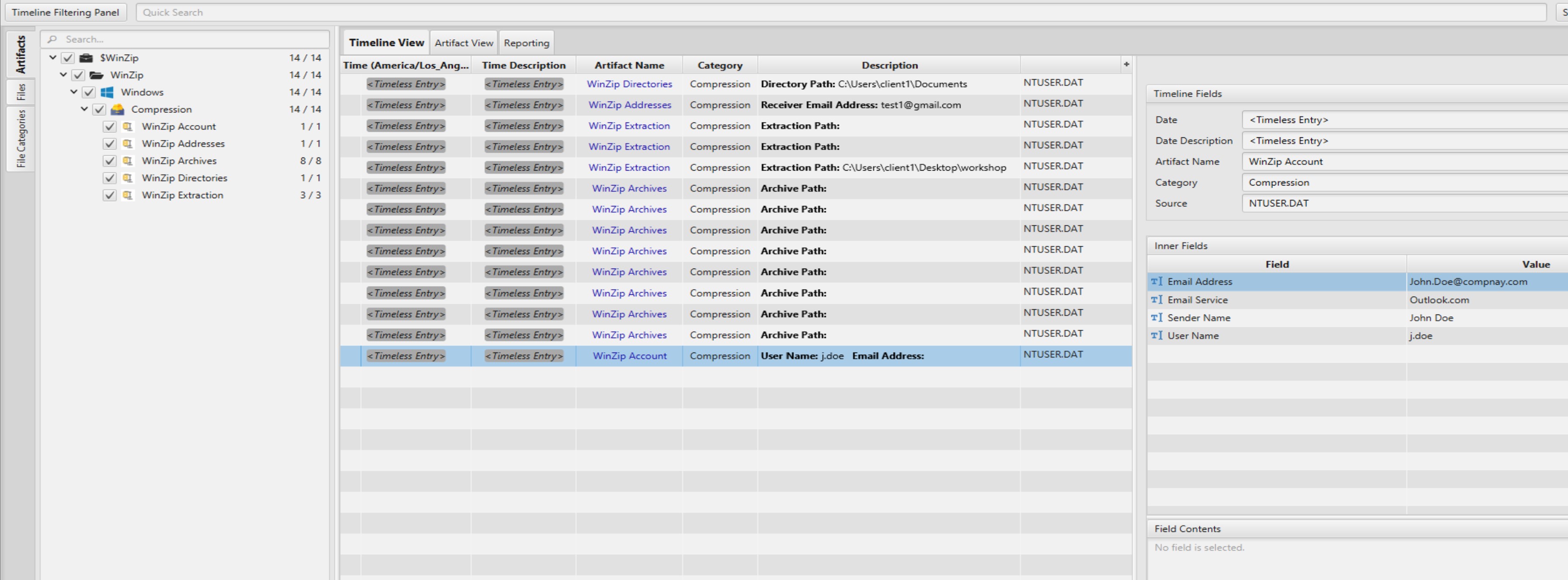
Once ArtiFast parser plugins complete processing the artifacts for analysis, they can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of WinZip artifacts in ArtiFast.
WinZip Account: This artifact shows the information about the user account.
- Sender Name - The sender's name
- Email Address - The sender's email address
- Email Service - The email service name used to send the email
- Username - The Username required by the email service
WinZip Addresses: This artifact shows the receivers’ email addresses.
- Receiver Email Address - The email address of the person to whom the email is sent.
- Directory Path - The directory path where the last file has been saved.
- Last Open Location GUID - The GUID of the last open location.
- Last Save Location GUID - The GUID of the last save location.
WinZip Extraction: This artifact shows the information about the extracted ZIP files.
- Extraction Path - The Path to the extracted file.
WinZip Archives: This artifact shows the information about the Archived files.
- Archive Path - The Path to the Zipped file.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
