Investigating Windows Update Log
09/06/2021 Wednesday
Windows Update log is a log or record of all notable changes made to a Windows system. Every detail of each update implemented by the Windows Update service is recorded by the Windows System. If anti-malware software is installed, the history of its updates is also recorded. Any third-party software built on the device can also capture logs for storage in the Windows event logs.
Digital Forensics Value of Windows Update Log Artifacts
In Windows Update Log is used to automate the operating system, check applications updates, manage multiple servers in a data center, and check for evidence of program execution. Event logs include records of a user’s actions on a computer that can be used as evidence in forensic investigations. Tracking such information is essential throughout the digital analysis process
Location of Windows Update Log Artifacts
In Windows 10 Windows Update Log artifact is located at C:\Windows\Logs\WindowsUpdate
Structure of Windows Update Log Artifacts
Windows Update Log are generated using ETW (Event Tracing for Windows) to analyze the operation of the Windows Update agent and service. To read ETW file format, it has to be converted into a log file (.log).
Analyzing Windows Update Log Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to analyze Windows Update Log artifact from Windows machines and what kind of digital forensics insights we can gain from the artifact.
After you have created your case and added evidence for investigation, at the Artifacts Parser Selection Phase, you can select Windows Update Log artifact:
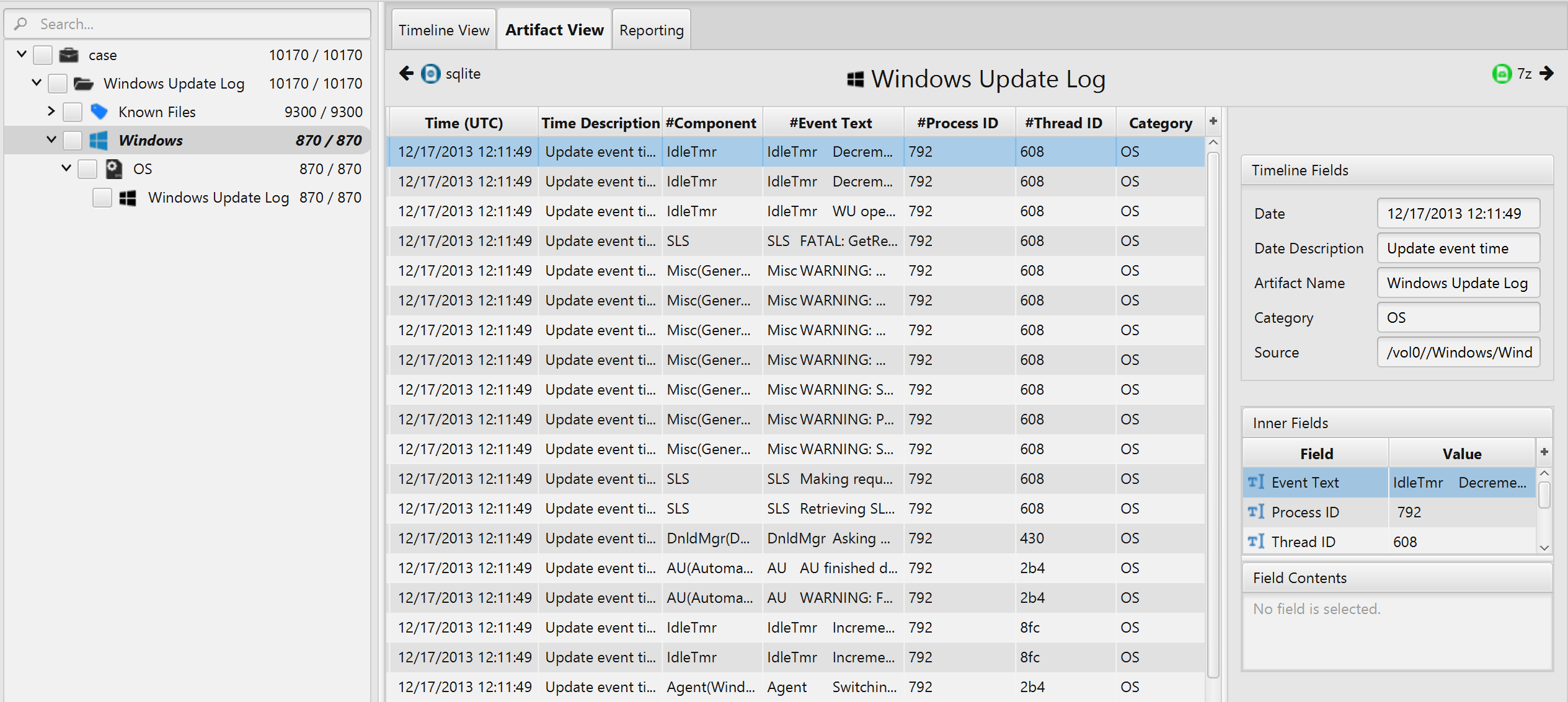
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Windows Update Log artifact in ArtiFast software.
Windows Update Log Artifact
- Component - The component written to the log file.
- Event Text - Update event text.
- Process ID - Process Id.
- Thread ID - Thread Id.
- Event Time - The date and time for the event update.
