Investigating Windows Terminal
11/07/2022 Monday
Windows Terminal is the modern terminal application in Windows 10 operating system. It is a terminal application for command-line tools and shells like command prompt, PowerShell, and Windows Subsystem for Linux (WSL). Windows Terminal can only be installed on Windows 10 version 18362.0 or higher.
Digital Forensics Value of Windows Terminal Artifact
Windows Terminal can interpret various command-line applications. The versatility of the Windows Terminal provides valuable information during the investigations. Especially the settings of the Windows Terminal provides information about the installed command-line tools. Stored values give details about WSL, including remote IP addresses, domain name and port numbers used.
Location of Windows Terminal Artifact
Windows Terminal data can be extracted from the following location:
C:\Users\%UserProfile%\AppData\Local\Packages\Microsoft.WindowsTerminal_8wekyb3d8bbwe\LocalState\
Structure of Windows Terminal Artifact
Windows Terminal is a package that can be installed from the Microsoft Store. After installation, the Windows Terminal application creates a “settings.json” file under the C:\Users\%UserProfile%\AppData\Local\Packages\Microsoft.WindowsTerminal_8wekyb3d8bbwe\ directory. This file is text based and it contains configuration details of the Windows Terminal application.
Analyzing Windows Terminal Artifact with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract Windows Terminal artifact from Windows machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Windows Terminal artifact:
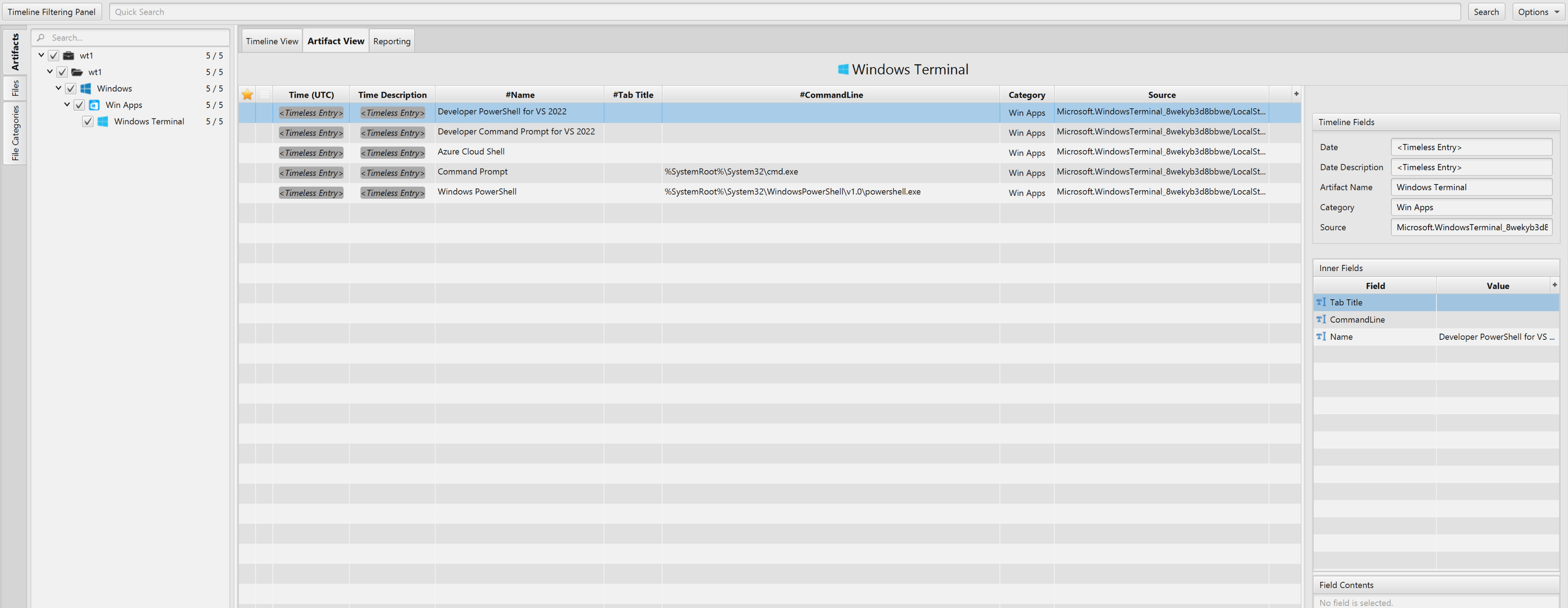
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of the Windows Terminal artifacts in ArtiFast.
Windows Terminal Artifact
The artifact contains information related to Windows Terminal application. The details you can view include:
- Tab Title - The name of the tab (If the user opened multiple tabs).
- CommandLine - The commands inputted into the Windows Terminal. These can be IP Addresses, ports when used in WSL and PowerShell cmdlet when PowerShell is used.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
