Investigating Windows Startup Programs
15/09/2022 Thursday
Startup programs refer to programs that run automatically when the user logs into the system. This means that these apps will lunch following a system reboot without any interaction from the user. Unless configured to do so, applications run will show no notifications or any type of indications that a program is running. This makes it an ideal medium for malware persistence.
Digital Forensics Value of Windows Startup Programs Artifacts
After a successful exploitation of a system, cybercriminals usually try to maintain persistence on the target system. Windows startup programs are one of the locations that threat actors use to place their malware and evade detection. Therefore, this artifact can provide valuable information especially, while investigating hacking incidents.
Location of Windows Startup Programs Artifacts
Startup Programs are stored in several locations. The following registry keys are among these locations:
- Software\Microsoft\Windows\CurrentVersion\Run
- Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
- Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
Analyzing Windows Startup Programs Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract Windows Startup Programs artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifacts.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Startup Programs artifacts:
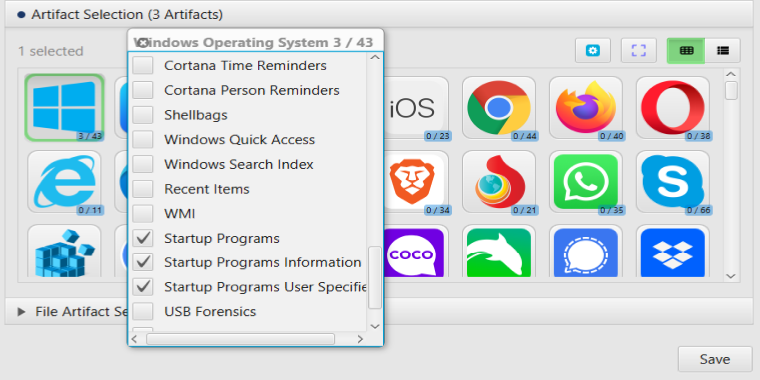
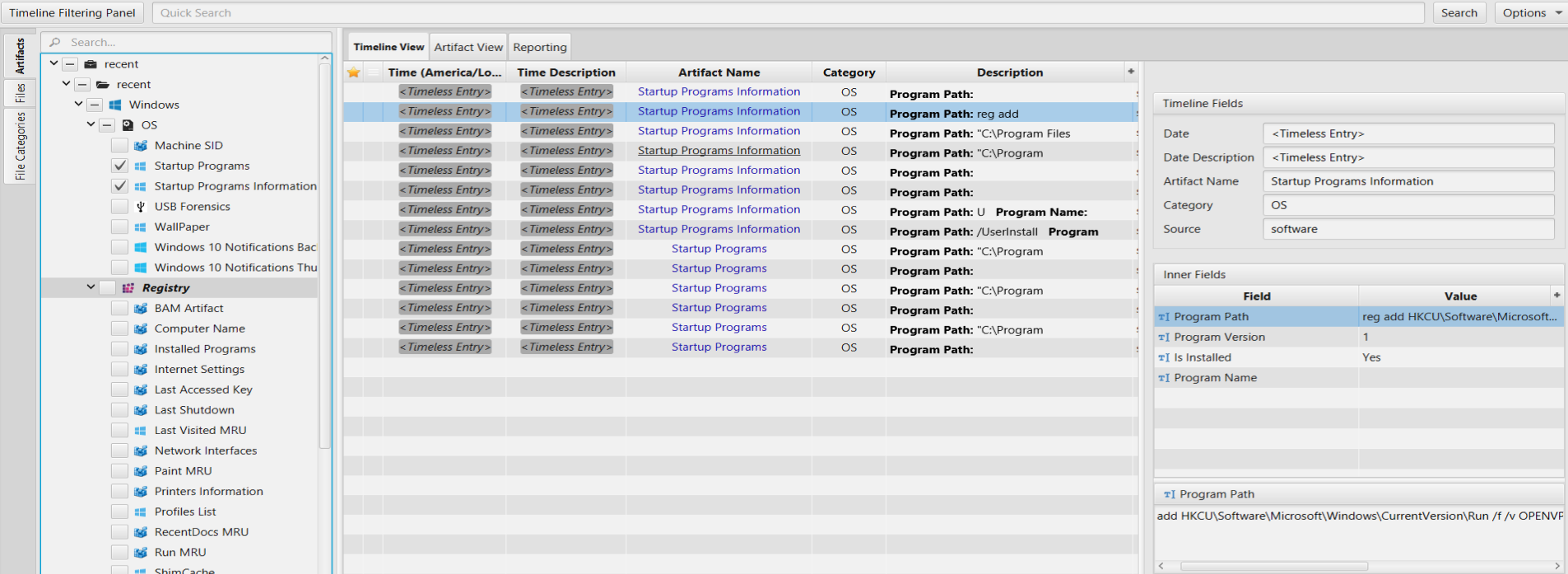
Once ArtiFast parser plugins complete processing the artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Startup Programs artifacts in ArtiFast.
Startup Programs: This artifact contains application configured to run at system startup.
- Program Name - The Name of the application.
- Program Path - The path to the executable file.
Startup Programs Information: This artifact contains information about the auto-run programs.
- Is Installed - Indicates whether the application is installed or not.
- Program Name - The Name of the application.
- Program Path - The path to the executable file.
- Program Version - The program version.
Startup Programs User Specified: This artifact contains information about programs specified by the user.
- Application Name - The name of the application
- Created Date/Time - The created date/time of that application
- Last Accessed Date/Time - The last accessed date/time of that application
- Last Modified Date/Time - The last modified date/time of that application
- Size - The size of the executable file in bytes.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
