Investigating Window OpenVPN
17/02/2023 Friday
OpenVPN is a virtual private network application, similar to ExpressVPN, ProtonVPN, and NordVPN. A VPN application provides a secure connection for individuals and businesses. OpenVPN solutions primarily target businesses by offering VPN integrated solutions such as OpenVPN Cloud and Self-Hosted Access Server. In addition, OpenVPN Connect client software is available for both individual users and businesses. The software is compatible with several widely used operating systems, including Windows, macOS, Linux, Android, and iOS.
Digital Forensics Value of OpenVPN
OpenVPN maintains artifacts which hold useful information that give details about the user’s browsing behavior. When this software is used by a cyber attacker, its left-behind artifacts can reveal his goals by showing information about the connection and the websites that the attacker was interested with.
Location of OpenVPN Artifacts
OpenVPN artifacts are found in the following location:
%systempartititon%:\Users\%username%\AppData\Roaming\OpenVPN Connect\profiles
%systempartititon%:\Users\%username%\AppData\Roaming\OpenVPN Connect\log
Analyzing OpenVPN with ArtiFast
This section will discuss how to use ArtiFast to extract OpenVPN from Windows and what kind of digital forensics insights we can gain from the artifacts.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select OpenVPN artifacts.
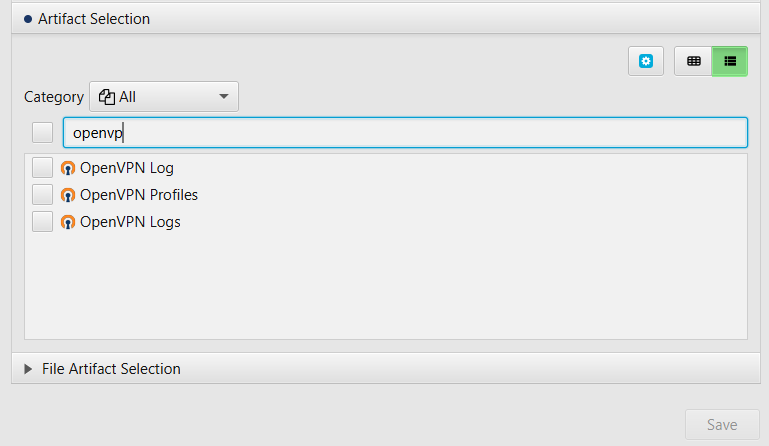
×
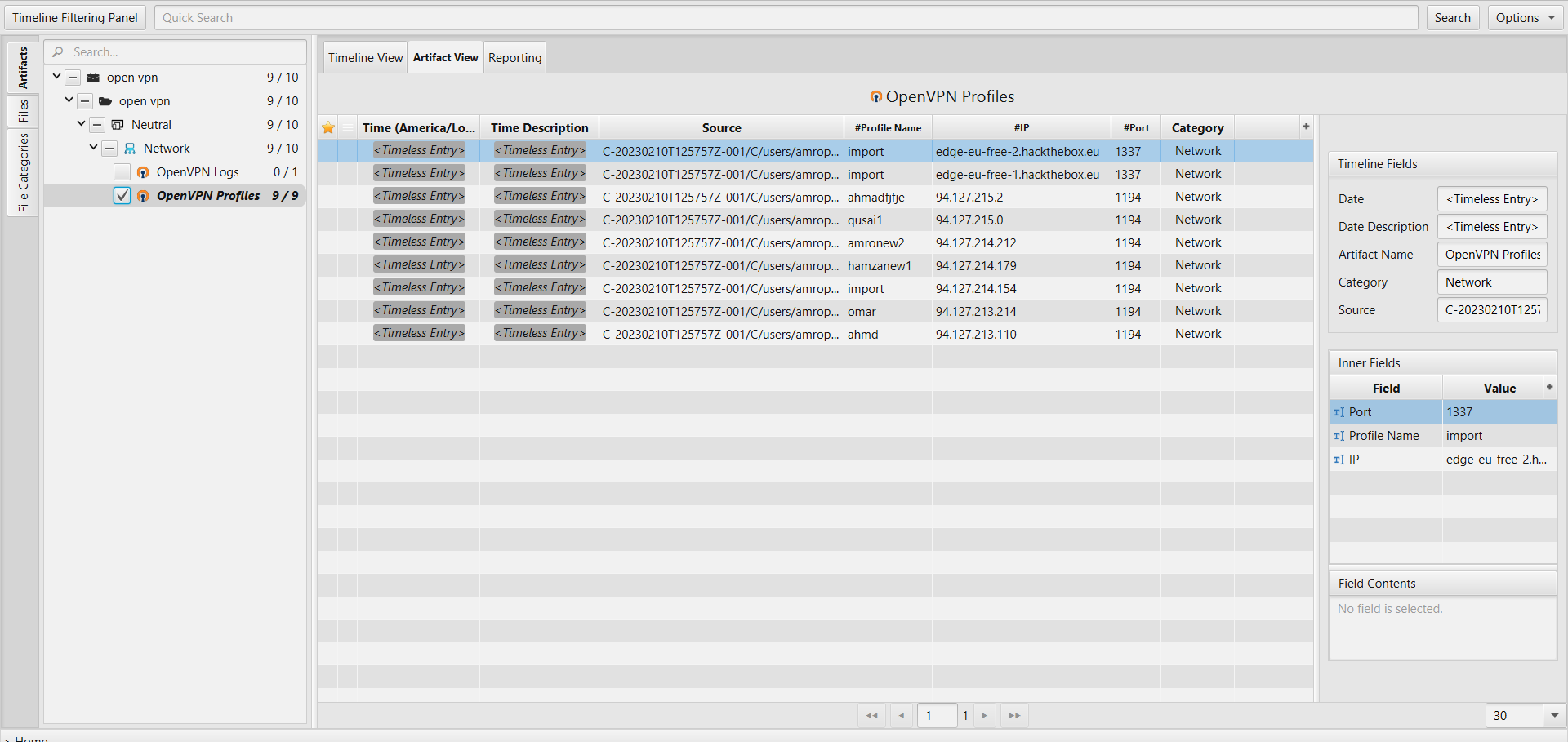
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Window OpenVPN artifacts in ArtiFast.
OpenVPN Profiles Artifact
- Profile Name - The name of the user profile.
- IP - The IP address of the connection.
- Port - The port number for this connection.
OpenVPN Logs Artifact
- Entry Date - The date of the log record.
- Entry - The contents of the log record.
For more information or suggestions please contact: kalthoum.karkazan@forensafe.com
