Investigating Window Installed Services
31/03/2023 Friday
Windows Installed Services EVTX is a log file generated by Windows operating system starting from Windows Vista. It records events related to the installation and removal of services. Services are programs that run in the background and provide various functions to the operating system and other applications.
Digital Forensics Value of Installed Services
This log can provide insights into any changes made to the system configuration related to the installation or removal of services. An investigator can use this information to identify any malicious services that may have been installed, modified, or removed from the system, and potentially link them to any suspicious or criminal activities. By analyzing the installed services log file, forensic investigators can also determine the timeframe of when certain services were installed, removed or modified, providing a timeline of events that can be used in reconstructing previous events on a particular device.
Location of Installed Services Artifacts
Installed Services artifacts are found in the following location:
%System32%\winevt\Logs\
Analyzing Installed Services with ArtiFast
This section will discuss how to use ArtiFast to extract Installed Services from Windows and what kind of digital forensics insights we can gain from the artifacts.
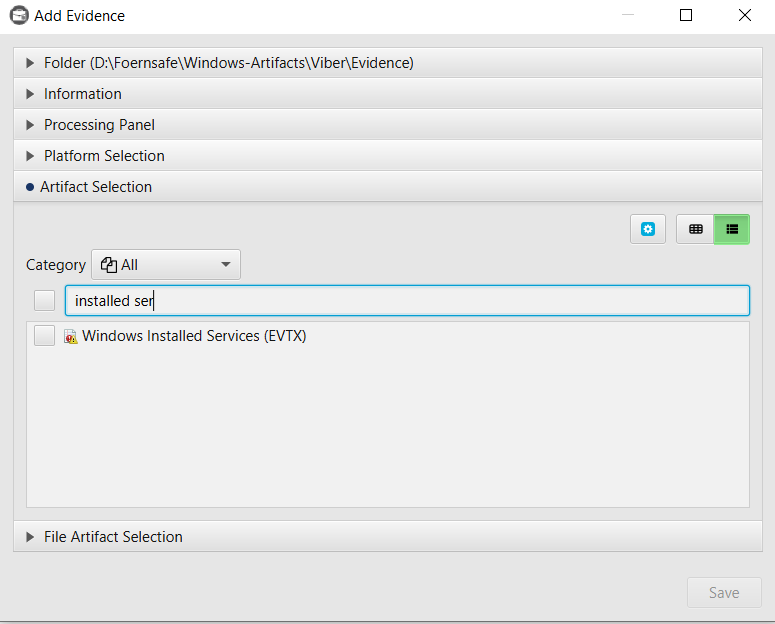
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Installed Services artifacts.
×
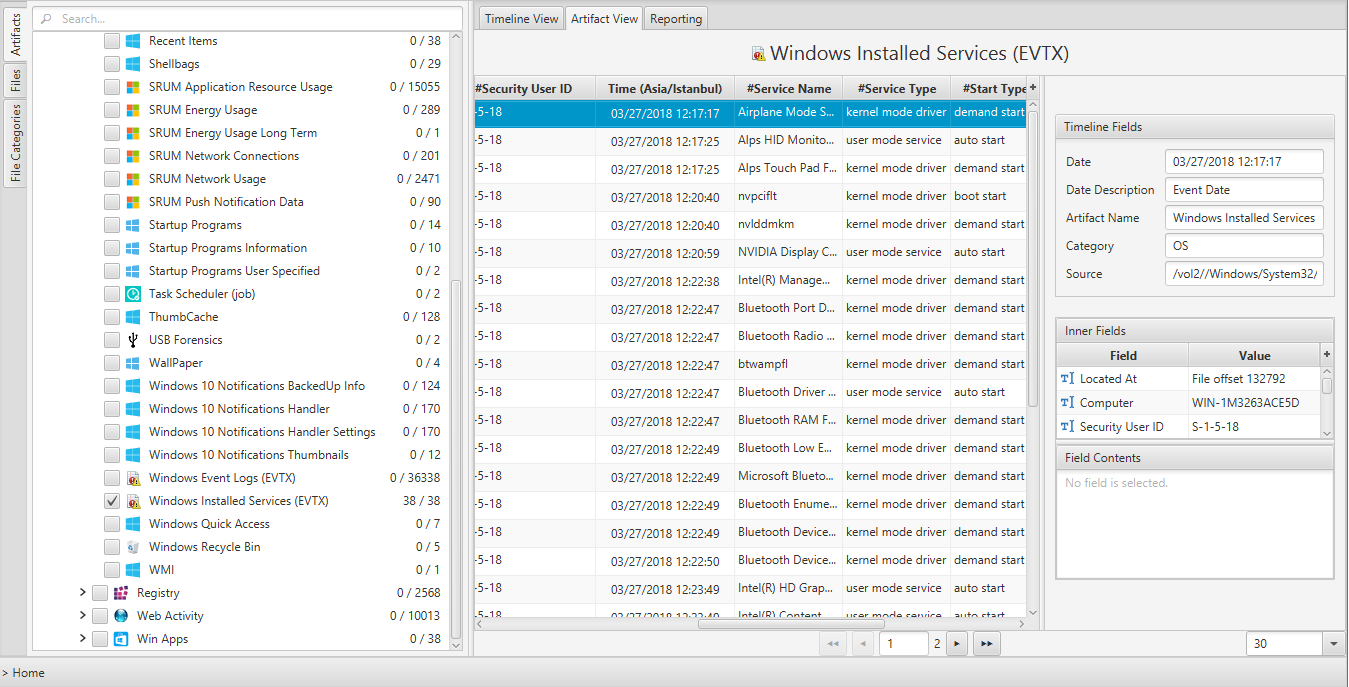
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Window Installed Services artifacts in ArtiFast.
Windows Installed Services (EVTX) Artifact
- Date - The date and time of the event.
- Located at - The offset of the event in the logfile.
- Computer - The computer name.
- Security User ID - User security ID.
- Service Name - The name of the service of this log record.
- Image path - Service file name.
- Service Type - Indicates the service type of this record.
- Account Name - The account corresponding to this event.
- Start Type - The startup type of this event.
For more information or suggestions please contact: ekrma.elnour@forensafe.com
