Investigating User Accounts
04/02/2022 Friday
Windows stores user accounts and security descriptors for users on the local computer in a file called SAM (Security Account Manager). SAM is a part of a system defined database where configuration data is stored and retrieved. Using cryptographic measures, this file can be used to authenticate local and remote users to prevent unauthenticated access to the system. User Accounts data can be extracted from this file.
Digital Forensics Value of User Accounts Artifacts
User Accounts artifact helps investigators identify the users on a Windows system. This information includes the username, full name, level of privilege the user has, last time the system was logged into with the account, last time a failed password login attempt was made, and other information. Analyzing this artifact helps tie a user to any activity on the computer. If, for example, a file download appeared in the system and the action needs to be traced, this artifact can provide clarity about the timeline by showing which account was logged into right before the incident. If the account is password protected, it can show what privileges the account holds as well.
Location of User Accounts Artifacts
User accounts artifact source file is located at: C:\Windows\config\SAM
Within the SAM hive, the artifact data can be found at:
SAM\Domains\Accounts\Users
Structure of User Accounts Artifacts
The SAM file containing the User Accounts artifact is a registry hive. This is a database where necessary operating system and/or application configurations are maintained. It is made up of keys and values. Keys can be containers that may contain other subkeys. Keys point to values, which are variable length data sets. Windows provides an executable file called regedit.exe that can be used to view and make changes to the registry database.
Analyzing User Accounts Artifacts with ArtiFast Windows
This section will discuss how to use Artifast Windows to extract User Accounts artifact from Windows
machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection
phase, you can select User Accounts artifact:
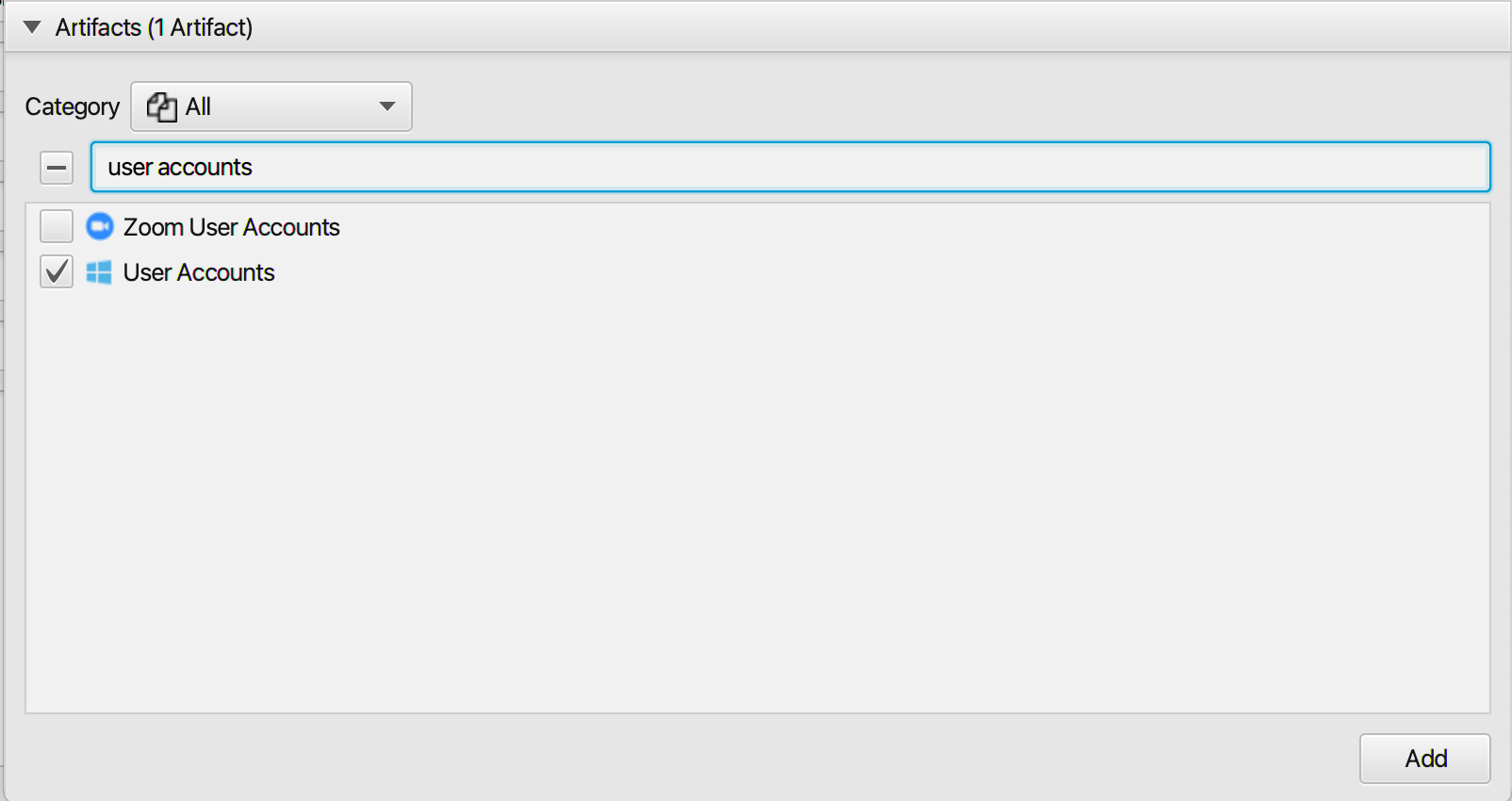
Once Artifast parser plugins complete processing the artifact for analysis, it can be reviewed via "Artifact View" or "Timeline View," with indexing, filtering, and searching capabilities. Below is a detailed description of the User Accounts artifact in Artifast software.
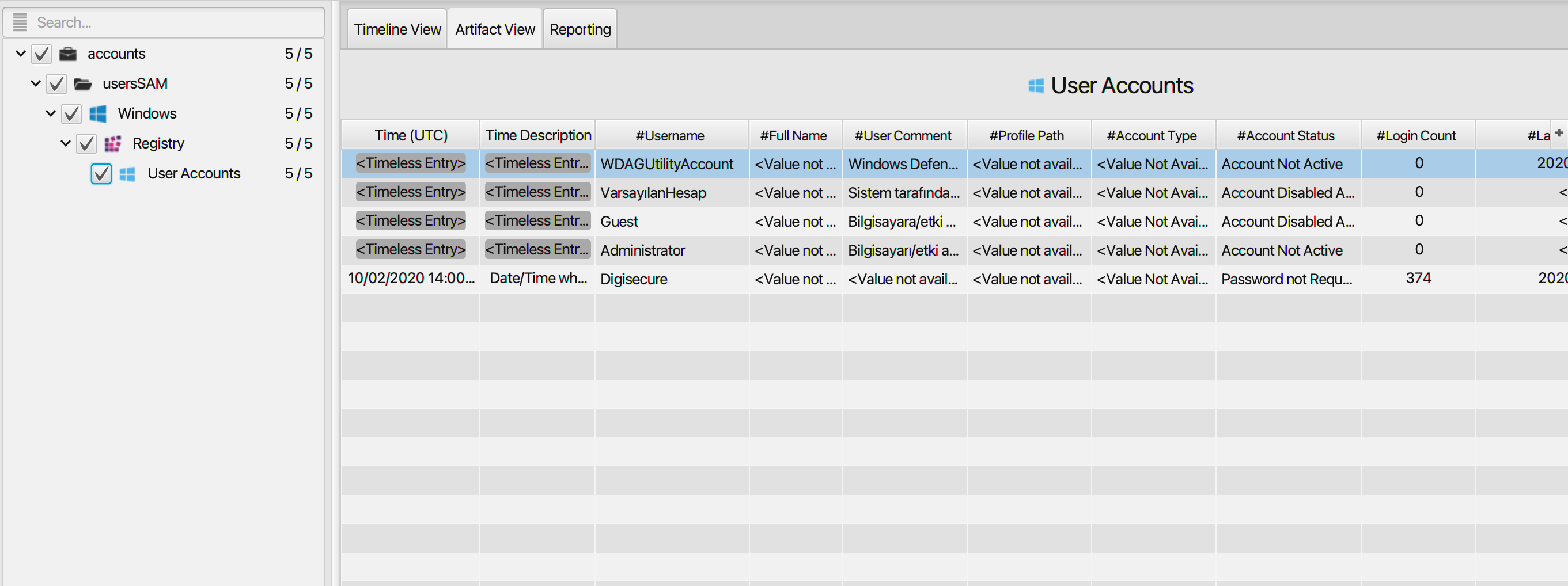
User Accounts Artifact
The artifact contains information on the user accounts in
the system. The details you can view include:
- Username - Account username.
- Full Name - Full name of the account user.
- User Comment - User account comment.
- Profile Path - The path to the user profile folder.
- Account Type - User account type. It could be a default admin user, custom limited or guest account.
- Account Status - Current status of the user account. Is it "Password Required and Active", "Account Not Active","Password not Required", or "Account Disabled and Password Not Required".
- Login Count - The number of times the user has logged into the system.
- Last Login Date/Time - Date/Time when a user last logged into the system using the account.
- Last Password Reset Date/Time - Date/Time when the password was last reset.
- Last Password Failed Date/Time - Date/Time of last incorrect password login attempt.
- Logon Script - Any logon scripts that get run when logging in as that user.
- Last Write Date/Time - Last date/time the registry key containing the artifact data was written to.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
