Investigating USB Devices
14/01/2022 Friday
USB devices are one of the most widely used storage devices due to their speed, large storage capacity, small size, mobility and more. The advantages of USB devices are indisputable; however, they are also considered as a main security threat to businesses as well as individuals. USB devices can be used to perform a variety of malicious activities including confidential data leakage and malware or viruses propagation. Hence, it is important to be able to retrieve information related to the USB devices that have been connected to a system.
Digital Forensics Value of USB Forensics Artifacts
USB device history can be an excellent source of evidence during an investigation. Examiners may find themselves in need to identify which USB device(s) were plugged into a machine and how they have been used. This information is particularly important in cases involving malicious activities such as data leakage or intellectual property theft. USB Forensics artifact retain information such as the USB device serial number, vendor ID, product ID, and timestamps (ex. first install date and last insertion date).
Location of USB Forensics Artifacts
USB devices analysis can vary depending on the Windows flavor and the type of USB device that has been
connected to the system. However, artifacts related to USB devices can be retrieved from the Registry hives
at the
following locations:
- SYSTEM/MountedDevices
- SYSTEM/CurrentControlSet/Enum/USBSTOR
- SYSTEM/CurrentControlSet/Enum/USB
- NTUSER.DAT/Software/Microsoft/Windows/CurrentVersion/Explorer/MountPoints2
Another source of information is the Plug and Play log files. In Windows XP, the log file is called setupapi.log and it is found at C:\Windows\setupapi.log. On the other hand, for Windows Vista, 7, 8 and 10, the log file is called setupapi.dev.log and it is located at C:\Windows\inf\setupapi.dev.log.
Analyzing USB Forensics Artifacts with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze USB Forensics artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifacts. After you have created your case and added evidence for the investigation, at the Artifacts Selection phase, you can select USB Forensics artifact:
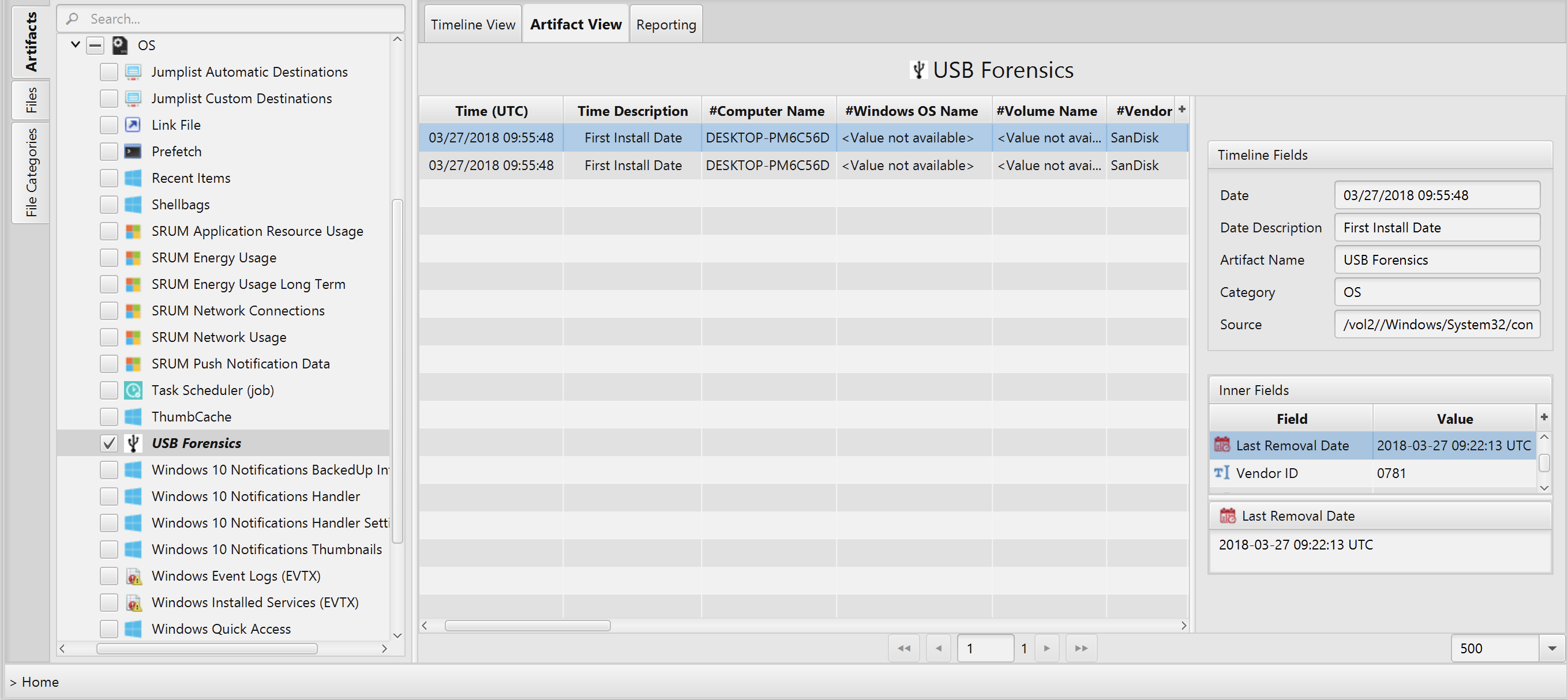
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a list of the details you can view using USB Forensics artifact in ArtiFast Windows.
USB Forensics Artifact
This artifact contains information about the USB devices that have
been connected to the system. The details you can view include:
- Computer Name
- Windows OS Name
- Volume Name
- Vendor
- Product
- Version
- Serial Number
- Parent Prefix ID
- Vendor ID
- Product ID
- Drive Letter
- Device GUID
- First Install Date
- Last Arrival Date
- Last Removal Date
- Last Insertion Date
- User Name
- MountPoints2 Key Date
- NTUser.dat Path
- SetupApiDevLog Dates
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
