Investigating Sticky Notes
18/10/2021 Monday
Sticky Notes is a desktop note-taking application that came with Windows 7, Windows 8, and Windows 10. It’s known for its instant launching as it enables its users to quickly and easily take notes on the post-it notes version of Windows.
Digital Forensics Value of Sticky Notes
Sticky Notes can contain a valuable amount of information about Windows user activities as it can capture small and big notes, images, and can create reminders with the help of Cortana. Sticky notes can also identify addresses, emails, and phone numbers.
Location of Sticky Notes Artifact
Sticky Note built-in application artifacts are stored at:
C:\Users\informant\AppData\Roaming\Microsoft\Sticky Notes\StickyNotes.snt
Sticky Note Windows application artifacts are stored at:
C:\Users\%UserProfile%\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalStat\plum.sqlite
Structure of Sticky Notes Artifact
Sticky Notes structure is made of a database file that is used for storing Sticky Notes information.
Analyzing Sticky Notes Artifact with ArtiFast Windows
This section will discuss how to use ArtiFast to extract Sticky Notes artifacts from Windows machines and
what kind of digital forensics insight we can gain from the artifacts.
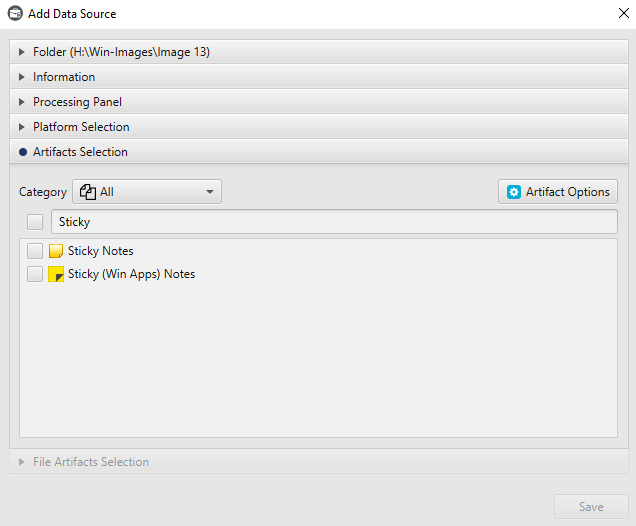
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Sticky Notes Artifact:
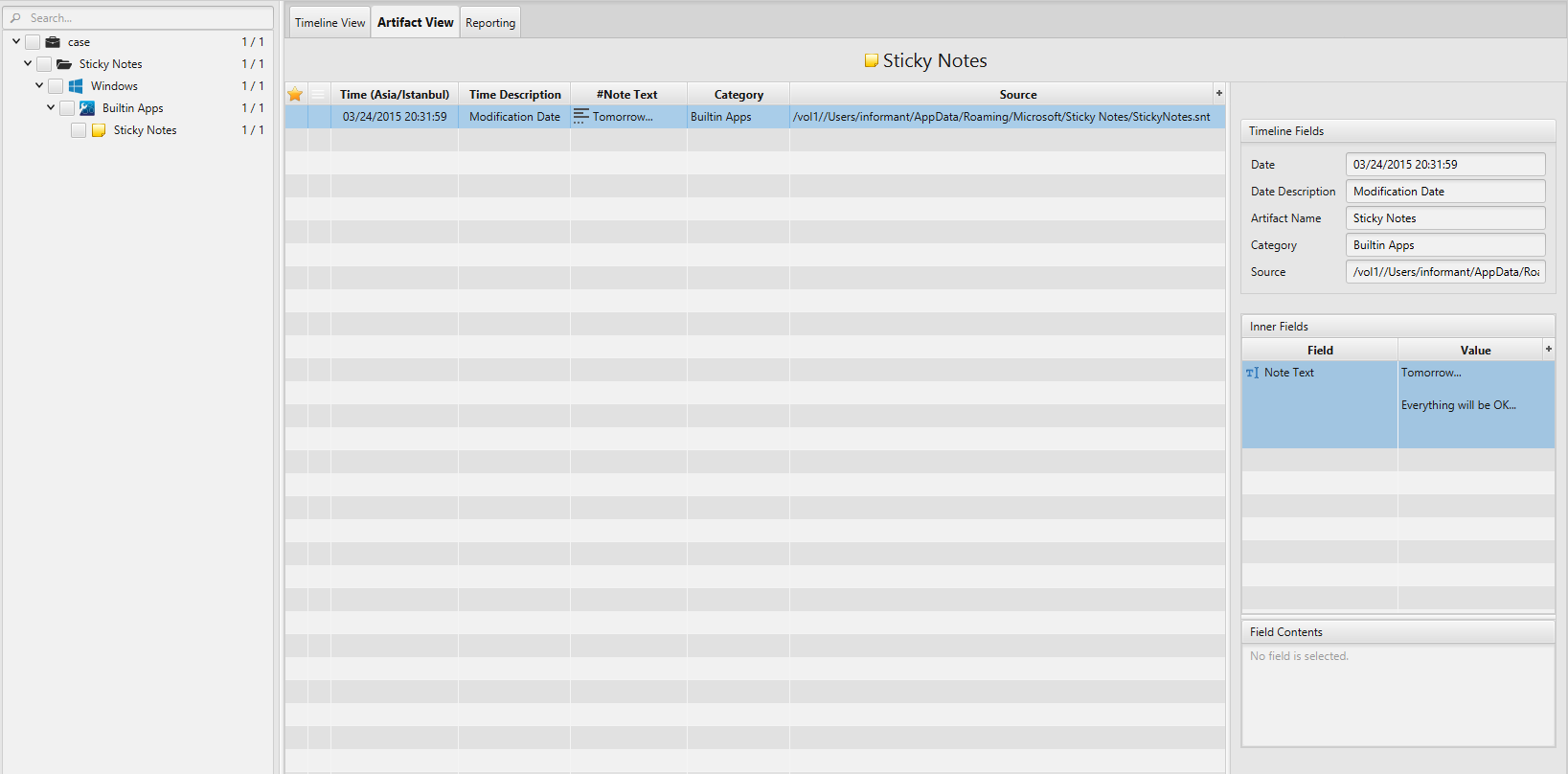
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. ArtiFast can analyze both Sticky Notes Windows application and Sticky Notes built-in application. Below is a detailed description of both artifacts in ArtiFast Windows.
Sticky Notes (Builtin) Artifact
This artifact contains information of the sticky
note built-in application such as:
- Note Text - Note text.
- Modification Date - The date and time when the modification occurred.
Sticky (Win Apps) Notes Artifact
This artifact contains information of Sticky Note
Windows application such as:
- Creation/Time - The creation date and time of the sticky note.
- Updated Date/Time - The update date and time of the sticky note.
- Text - Text of note.
- Title - Title of the sticky note.
- Theme - Sticky note color theme.
- ID - Note ID.
- Parent ID - User parent ID.
- Is Open - Indicates whether the sticky note is open.
- Pending Insights Scan - Indicates whether pending insights scan.
- User Created Date/Time - The user creation date and time.
- User Updated Date/Time - The user update date and time.
For more information or suggestions please contact: lina.alsoufi@forensafe.com
