Investigating Run MRU
29/04/2022 Friday
The Run utility on Windows Systems enables the user to directly open an application, folder or document. In
Windows 10, the Run utility can be accessed by right-clicking on Start > Run or by using the keyboard shortcut
Windows Key + R. As seen in the figure below, the Run utility includes a drop-down list that shows the last
commands executed via the Run dialog.
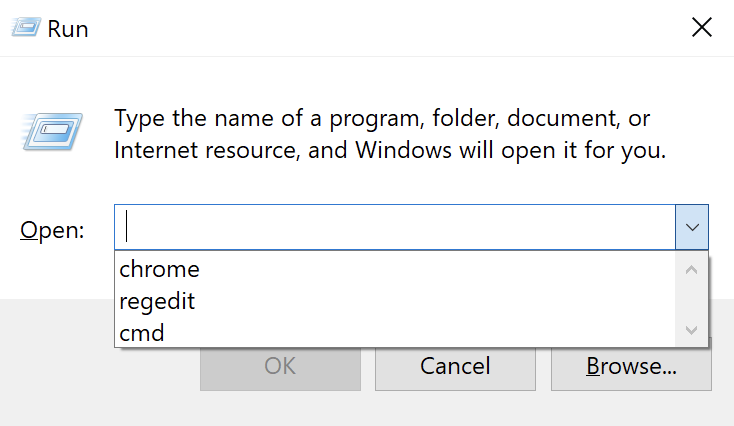
Items typed into the Windows Run dialog are recorded in the Registry under the RunMRU key. Deleting a value from RunMRU key will cause that entry to be removed from the history list of the Run utility. However, deleting the RunMRU key or any of its values does not remove the history list in Run utility immediately. The user has to close the Run window for the action to be effective.
Digital Forensics Value of Run MRU
The information maintained in the RunMRU key may shed some light on the user’s activity on the system. The Run MRU artifact is also used when suspecting an attack by a malicious actor as it can indicate the execution of a program or even a script on a device. In addition, this artifact proved to be helpful when investigating access to files and applications on removable storage devices or remote systems.
Location of Run MRU Artifact
RunMRU key is located at: NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
Structure of Run MRU Artifact
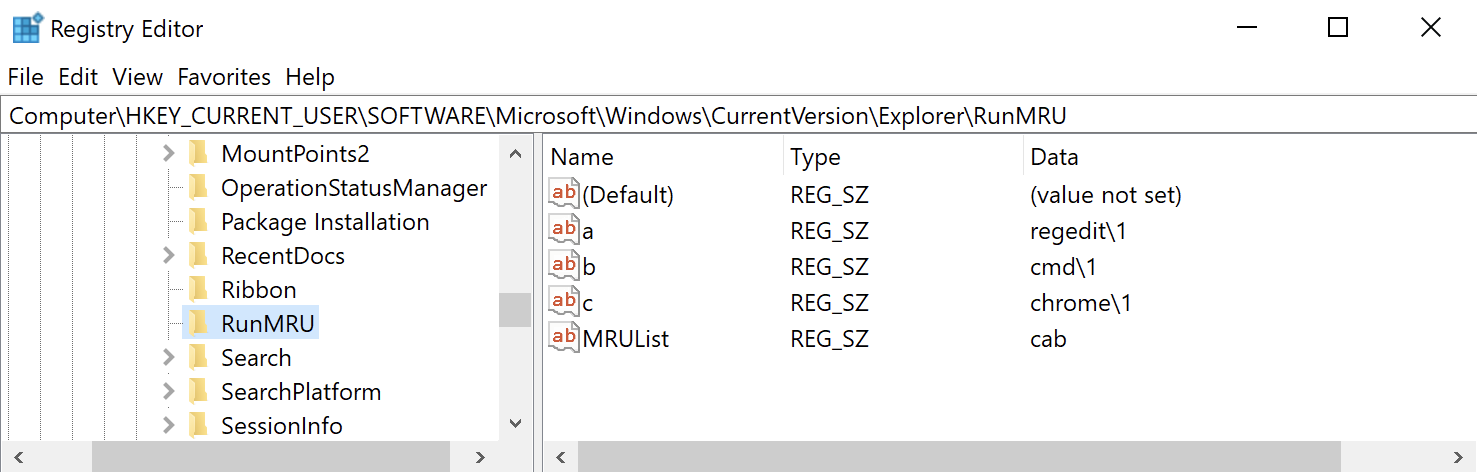
RunMRU key contains multiple values that are named for lowercase letters. These values store the commands
that a user run using the Run utility. The first value added is named “a”, the second value is named “b”,
then, “c” and so on. However, the names of the values do not always reflect the order in which the commands
were typed into the Run box. This information is maintained in the “MRUList” value which is a string that
lists the order in which each value beneath the RunMRU key was last accessed. For instance, in the figure
below, the first letter listed in the MRUList is “c”. The value named “c” stores the command “chrome” which
means that the most recent command typed into the Run box is “chrome”.
Analyzing Run MRU Artifact with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Run MRU artifact from Windows machines and
what kind of digital forensics insight we can gain from the artifact.
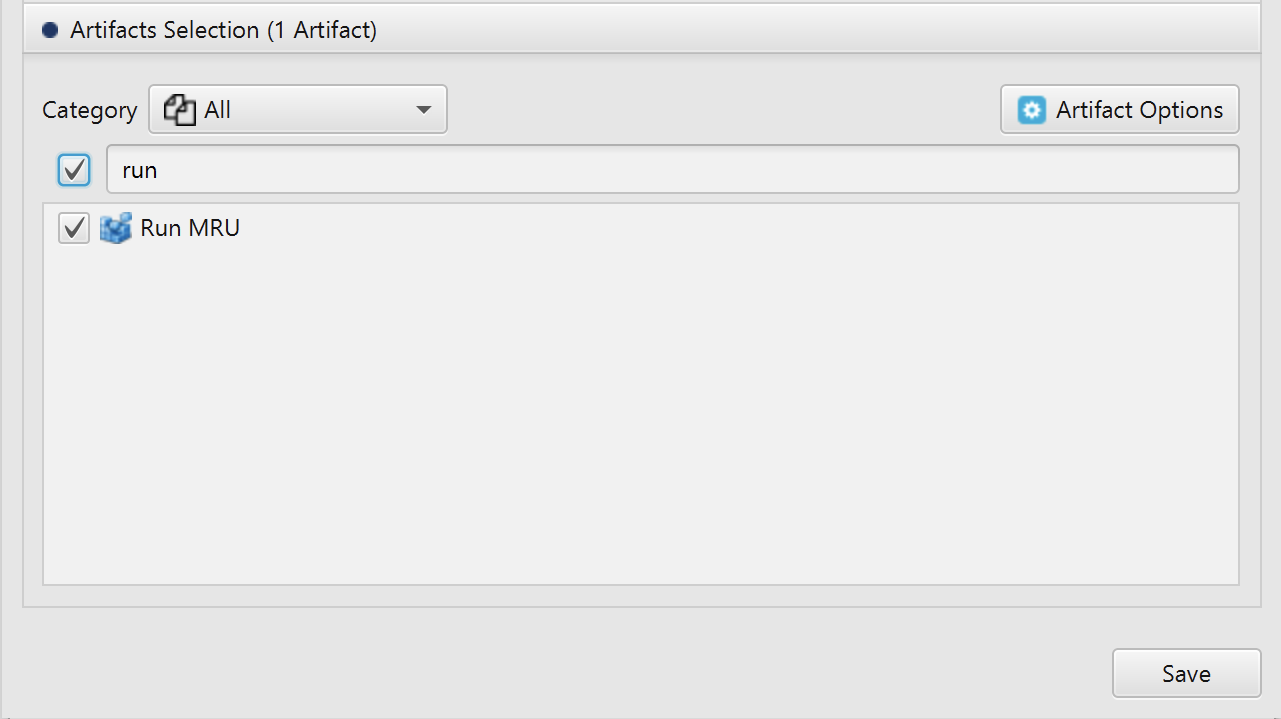
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Run MRU Artifact:
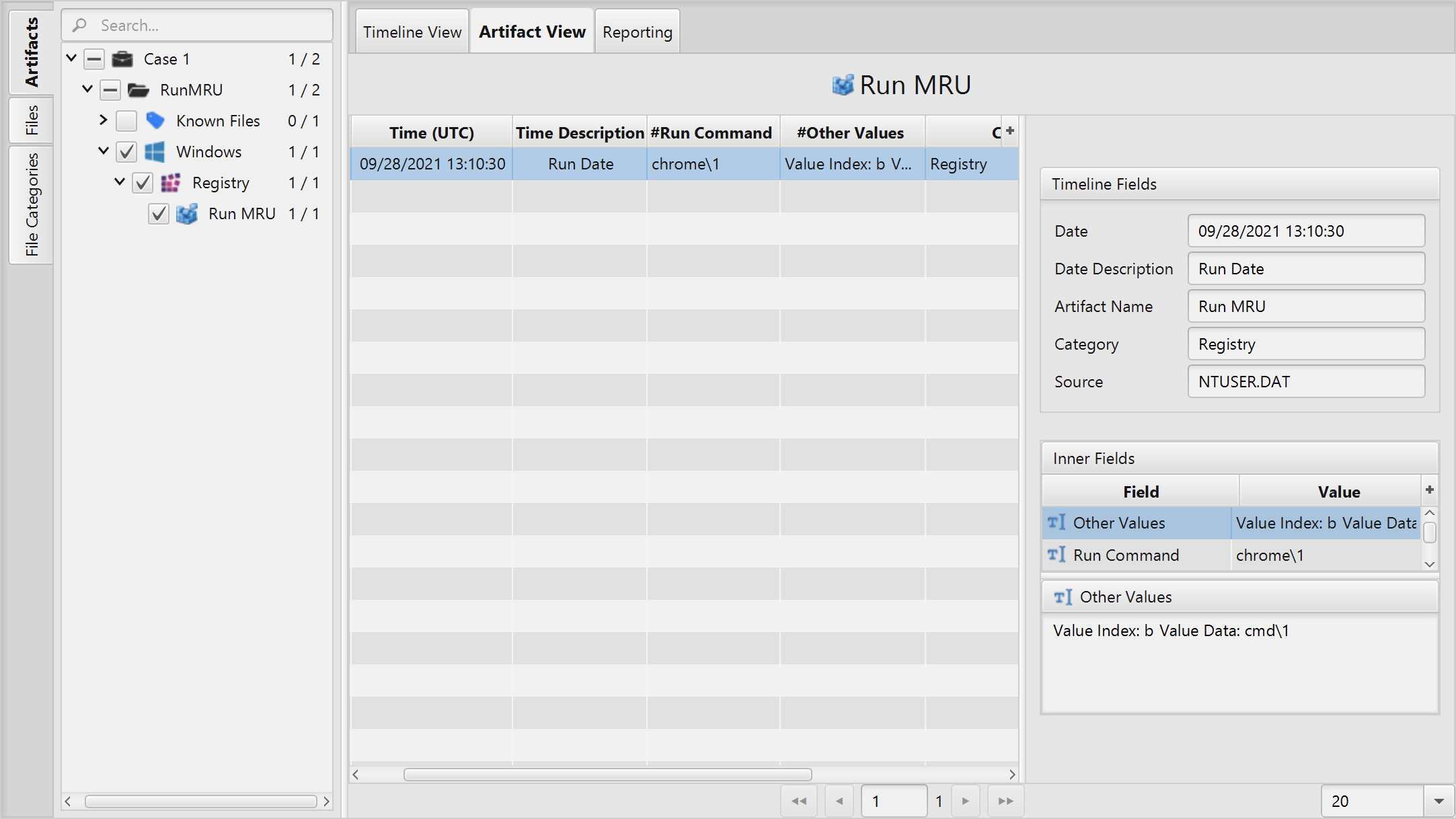
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a detailed description of Run MRU artifact in ArtiFast Windows.
Run MRU Artifact
- Run Command - The last command string that the user inserted in the Windows Run utility.
- Run Date - The date and time the RunMRU key was last modified.
- Other Values - The other values inserted in the Windows Run utility.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
