Investigating Remote Desktop Connection MRU
31/12/2021 Friday
The Microsoft Remote Desktop Connection (RDC) allows a user to connect and gain access to other Windows systems over a network. It is a built-in application that implements Remote Desktop Protocol (RDP) through Terminal service or Remote Desktop Service to access and control all apps, files, and network resources on a remote system.
Digital Forensics Value of RDC MRU Artifact
RDC is commonly used by system administrators to perform administrative tasks such as configuring computers and solving computer and network issues. However, it can also be used by threat actors to perform malicious activities on remote Windows systems. Thus, Remote Desktop Connection MRU artifact can be useful in determining the systems an attacker has accessed.
Location and Structure of RDC MRU Artifacts
Information about the systems that are accessed via the Remote Desktop Connection are stored at the following location:
- NTUSER.DAT\Software\Microsoft\Terminal Server Client\Default
Analyzing RDC MRU Artifacts with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Remote Desktop Connection MRU artifact from Windows machines and what kind of digital forensics insight we can gain from the artifact. After you have created your case and added evidence for the investigation, at the Artifacts Selection phase, you can select Remote Desktop Connection MRU artifact:
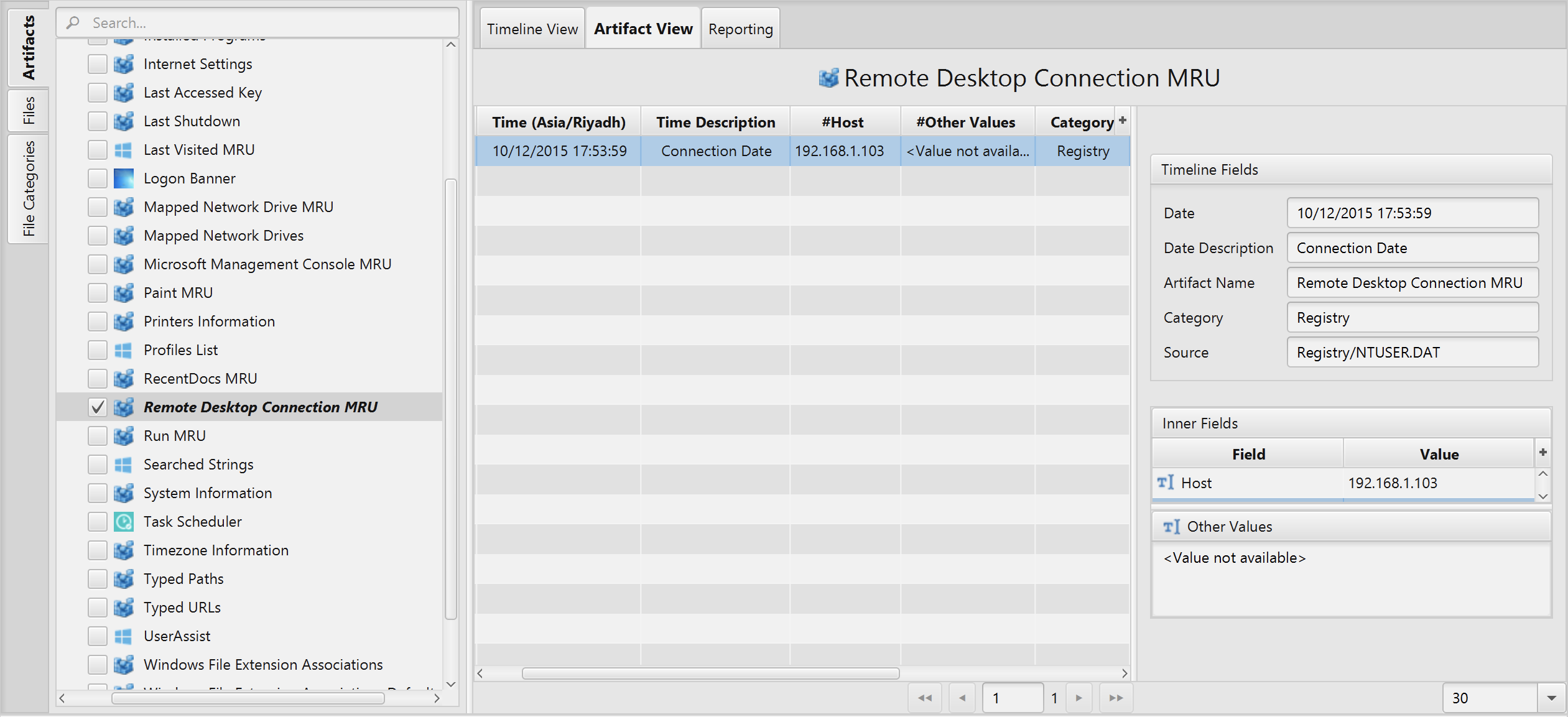
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a detailed description of Remote Desktop Connection MRU artifact in ArtiFast Windows.
Remote Desktop Connection MRU Artifact
- Host - Host name or IP address of remote server.
- Connection Date - Connection date.
- Other Values - Other values .
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
