Investigating Proton VPN
23/09/2022 Friday
Proton VPN is a community supported VPN service that was initially developed to provide anonymity to the Proton Mail users. Proton VPN became one of the most used VPN services around the world. According to Proton VPN website, Proton VPN currently serves users from over 63 countries and provides cross-platform support to users.
Digital Forensics Value of Proton VPN Artifacts
Proton VPN provides no logging and Tor over VPN features which makes it a possible medium for cybercrimes. During a hacking investigation case, VPN configuration files, profiles, and connection details can provide valuable information for examiners.
Location and Structure of Proton VPN Artifacts
Proton VPN configuration file is stored at the following location:
C:\Users\[username]\AppData\Local\ProtonVPN\ProtonVPN.exe_Url_5k5woeau2v3gmtlay4mjwsftlqxjnn2p\2.0.1.0
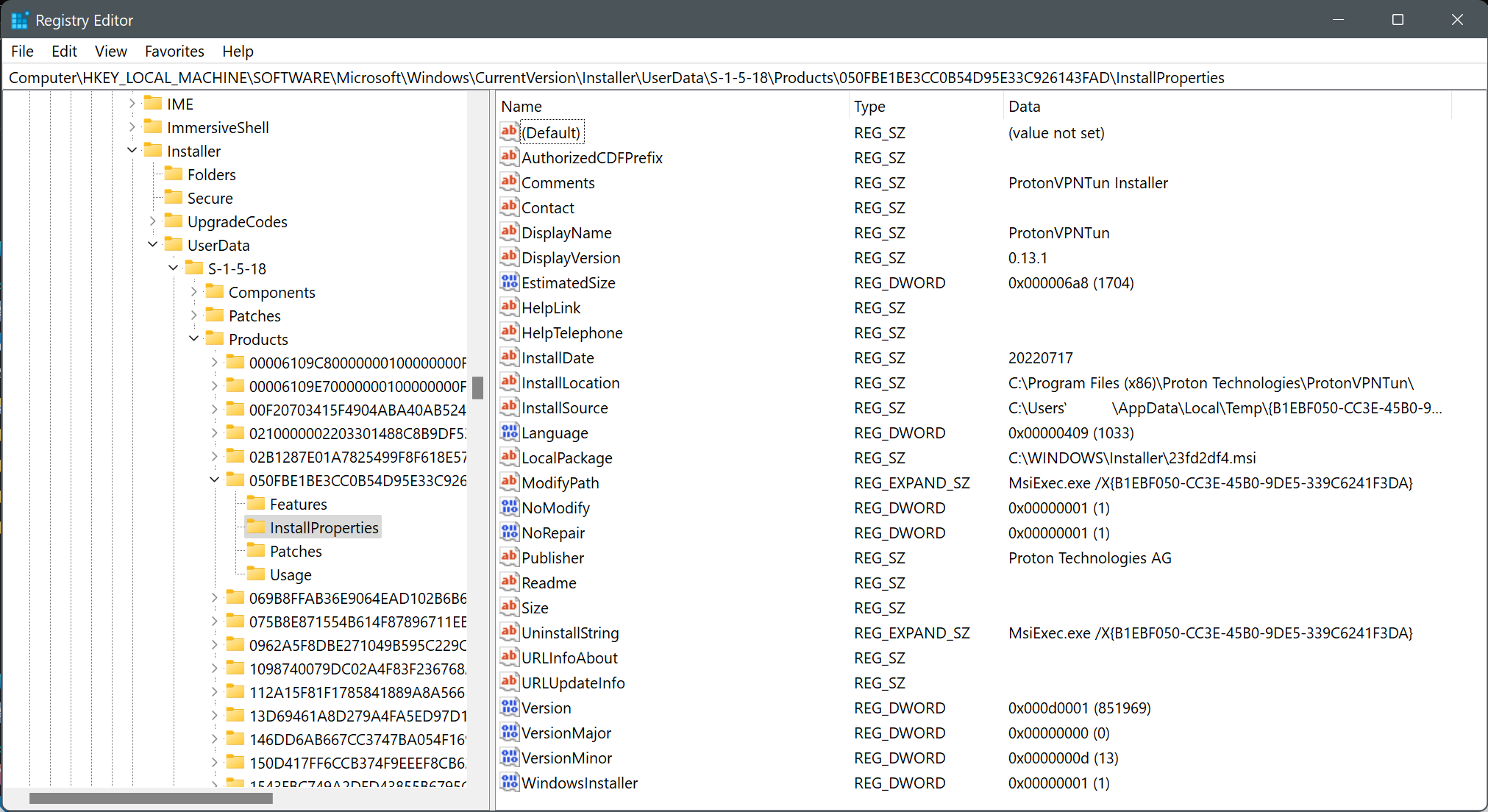
Artifacts related to Proton VPN can also be retrieved from the Registry hive at the following location:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\015E6E139914A1F449BE4C2A24CDFFAF
Analyzing Proton VPN Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract Proton VPN artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Proton VPN artifacts:

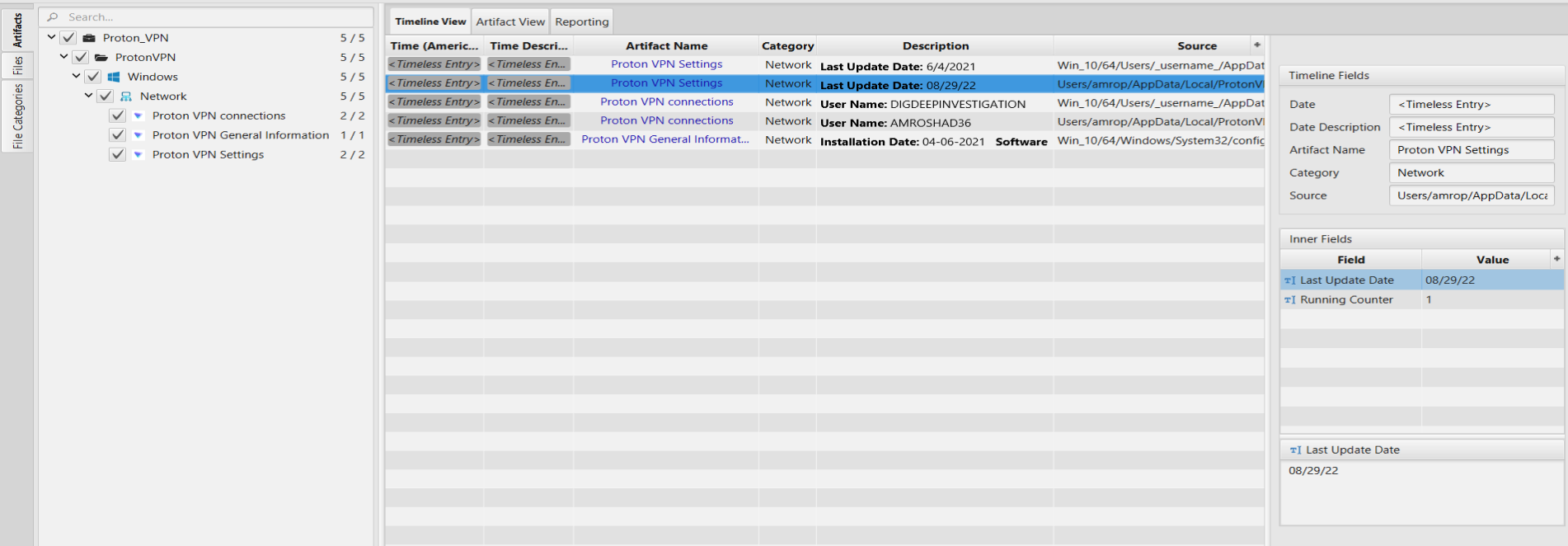
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of the Proton VPN artifacts in ArtiFast.
Proton VPN General Information
The artifact contains general information about the Software.
- Software Name - Name of the software. In this case it is Proton VPN.
- Software Version - Version of the Proton VPN.
- Installation Date - Software installation date.
- Estimated Installed Size - Estimated installed software size in megabyte.
Proton VPN Settings
The artifact contains information related to the settings and configuration set by the user.
- Last Update Date - The date when the Proton VPN was last updated.
- Running Counter - The number of times in which the program was used by the user.
Proton VPN Connections
The artifact contains information about the connections made by the user.
- User Name - The user name used to establish the connection.
- Connection Type - The connection type selected by the used to establish the connection.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
