Investigating Microsoft Office
21/01/2022 Friday
Microsoft Office is a set of office/productivity related applications widely used around the world. Microsoft Office includes a variety of applications such as Microsoft Word, Excel, Access and Microsoft PowerPoint. Each application is designed to offer a specific task or service to its users. For example, word processing, managing emails, and creating presentations. Microsoft Office applications are available on desktop, mobile, and via web browsers.
Digital Forensics Value of Microsoft Office Artifacts
Microsoft Office documents are everywhere. They are one of the most common electronic documents used around the world. Given its popularity and broad usage, Microsoft Office suite software is considered an important source of evidentiary information during the digital forensic analysis process. Microsoft Office artifacts retain information such as the user ID, the files and directories recently accessed by the user and other valuable information that can be vital when conducting digital forensic investigations.
Location of Microsoft Office Artifacts
Microsoft Office artifacts are stored in NTUSER.DAT registry hive. If the user is not signed into a Live account, the files and directories recently accessed by Access, Excel, Word, PowerPoint, and Publisher are found in the following subkeys:
- NTUSER.DAT\Software\Microsoft\Office\<version>\<program name>\File MRU
- NTUSER.DAT\Software\Microsoft\Office\<version>\<program name>\Place MRU
However, when a user signs into a Live account through the sign in option, a LiveId_xxx subkey is created for each new Live account. Therefore, the File MRU and Place MRU of each user will be maintained within this key at the following locations:
- NTUSER.DAT\Software\Microsoft\Office\<version>\<program name>\User MRU\<LiveID_xxx>\File MRU
- NTUSER.DAT\Software\Microsoft\Office\<version>\<program name>\User MRU\<LiveID_xxx>\Place MRU
Similarly, Microsoft Office Word Reading Locations artifact is found in NTUSER.DAT registry hive. Unlike Microsoft Office Recent Files and Recent Places artifacts, however, this information is created when a document in Word is closed and it is stored under the Office key at the following location:
- NTUSER.DAT\Software\Microsoft\Office\15.0\Word\Reading Locations
Analyzing Microsoft Office Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast to analyze Microsoft Office artifacts from Windows
machines and what kind of digital forensics insights we can gain from the artifacts.
After you have created your case and added evidence for investigation, at the Artifacts Selection
phase, you can select Microsoft Office artifacts:
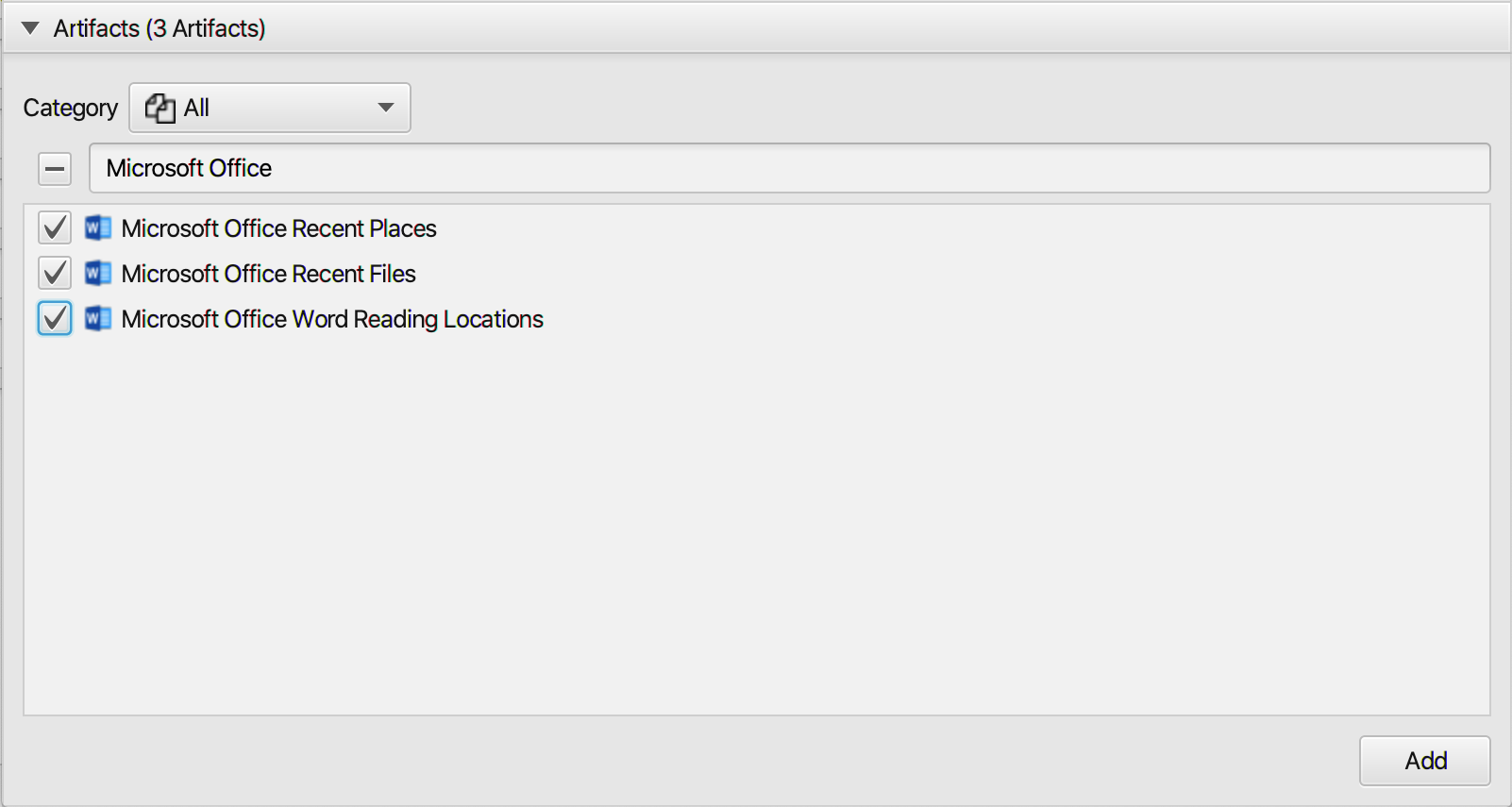
ArtiFast can analyze Microsoft Office Recent Files, Recent Places and Microsoft Office Word Reading
Locations. For demonstration purposes, all the artifacts have been chosen, however, you have the option to
select one or more artifacts.
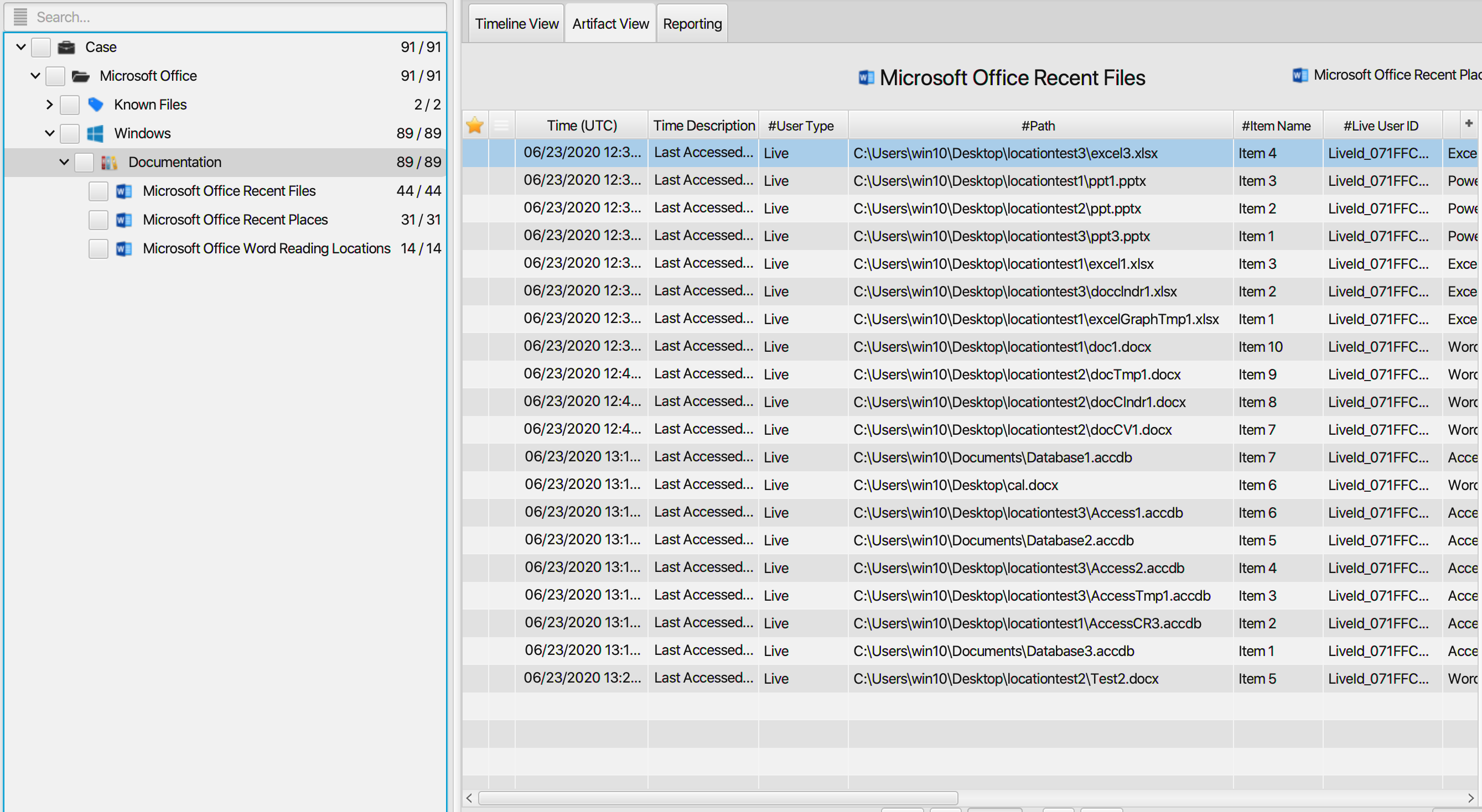
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Microsoft Office artifacts in ArtiFast.
Microsoft Office Recent Files Artifact
This artifact contains information related
to the recently accessed files. The details you can view include:
- User Type - Type of the user.
- Path - The path to the file.
- Office Version - Office version.
- Office Program Name - Name of the program used to open the file.
- Located At - Full path to the value within the registry key.
- Live User ID - The unique identifier of the logged in user.
- Last Accessed Date - The date/time when the file was last accessed.
- Item Name - Name of the value within the registry key.
Microsoft Office Recent Places Artifact
This artifact contains information related
to the recent directories of the files. The details you can view include:
- User Type - Type of the user.
- Path - The path to the file.
- Office Version - Office version.
- Office Program Name - Name of the program used to open the file.
- Located At - Full path to the value within the registry key.
- Live User ID - The unique identifier of the logged in user.
- Last Accessed Date - The date/time when the file was last accessed.
- Item Name - Name of the value within the registry key.
Microsoft Office Word Reading Locations Artifact
Microsoft Word allows users to
continue reading or editing a document starting at the last point they were working on by tracking the
positioning of the cursor in the document. This artifact contains information related to this feature. The
details you can view include:
- File Closed Date - The date/time when the file was last closed.
- Path - Full path to the file.
- Item Name - Name of the value within the registry key.
- Located At - Full path to the value within the registry key.
- Office Version - Office version.
- Position 1/Position 2 - Both indicates the positioning data used to place the cursor at a point in the document.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
