Investigating Microsoft Management Console (MMC) MRU
07/09/2022 Wednesday
Microsoft Management Console (MMC) creates, saves, and opens administrative tools in Windows operating systems. MMC makes custom administrative consoles for managing servers and clients. These administrative consoles are called snap-ins. Snap-ins allow users to administer computers, services, system components, and networks. Snap-ins can be saved in MMC for later use.
Digital Forensics Value of MMC MRU Artifact
When a management console is run on a system, the file name (with .msc extension) is stored in the cache and registry. In addition, custom MMCs created by users are also maintained in the registry. These artifacts are helpful when investigating system administrative actions and can help identify how users managed the system.
Location of MMC MRU Artifact
Microsoft Management Console MRU artifact is stored at the following location:
HKCU\Software\Microsoft\Microsoft Management Console\Recent File List
Analyzing MMC MRU Artifact with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract MMC MRU artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Microsoft Management Console MRU artifact:

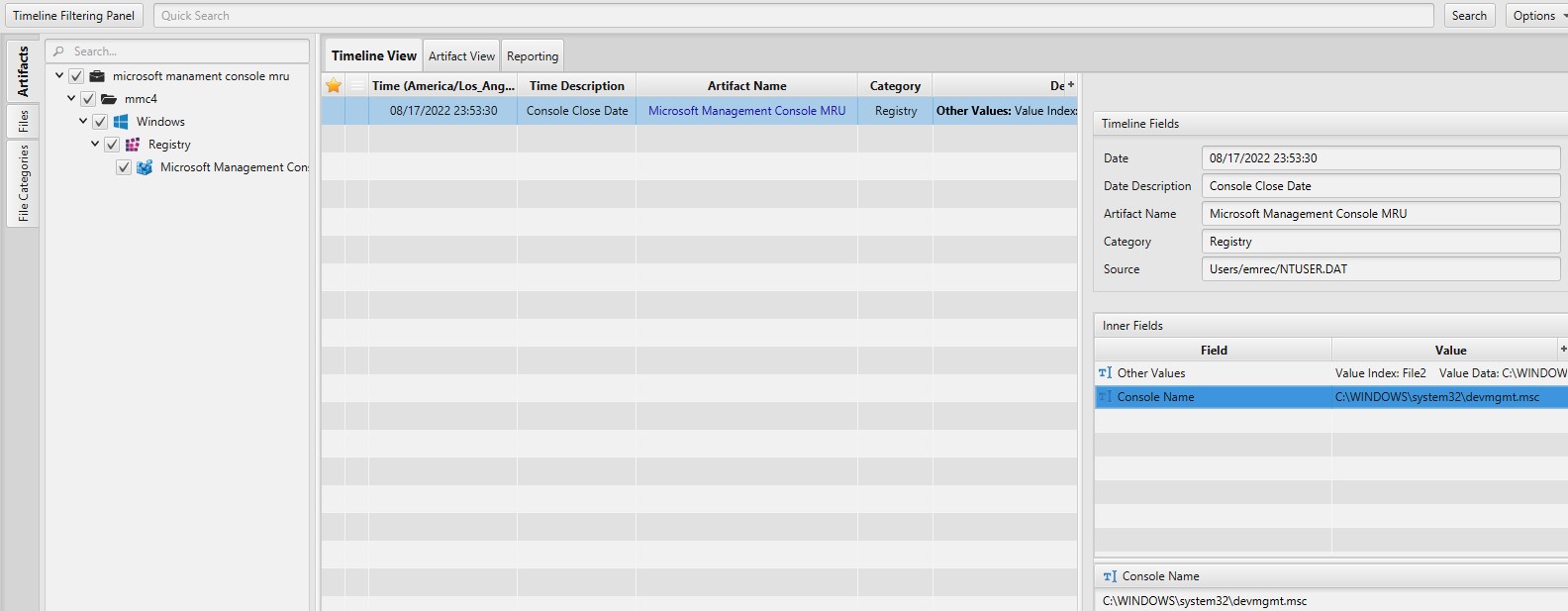
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of MMC MRU artifact in ArtiFast.
Microsoft Management Console MRU: This artifact shows the system's last opened MMC.
- Console Name - Console name.
- Close Date - Console closed date.
- Other Values - Other recent values.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
