Investigating Machine SID
18/07/2022 Monday
A security identifier (SID) is a unique alphanumeric number that identifies a security principal or a security group. Security principals can be a user account, a computer account, a thread, or a process. SID is generated by the system to identify a particular entity at the time it is created.
Digital Forensics Value of Machine SID Artifact
SIDs are unique within their scope (domain or local) and they are never reused. The operating system generates a SID that identifies a particular account or group at the time the account or group is created. No two accounts or groups on the computer ever share the same SID. Analyzing SIDs on a system helps investigators to uniquely identify accounts or groups created on the systems.
Location and structure of Machine SID Artifact
Machine SID is stored in a security database. The default location is Windows\System32\Config\SECURITY\SAM\Domains\Account registry key. SID consists of the following:
- The revision level of the SID structure.
- A 48-bit identifier authority value which identifies the authority that issued the SID.
- A variable number of subauthority or relative identifier (RID) values.
The combination of the identifier authority value and subauthority values ensures that no two SIDs will be the same. The standardized string notation for SIDs is S-R-I-S.
- “S”, identifies the strings series of digits as a SID,
- “R”, is the revision level,
- “I”, is the identifier-authority value,
- “S”, is the subauthority values.
Analyzing Machine SID Artifact with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract Machine SID artifact from Windows machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Machine SID artifact:
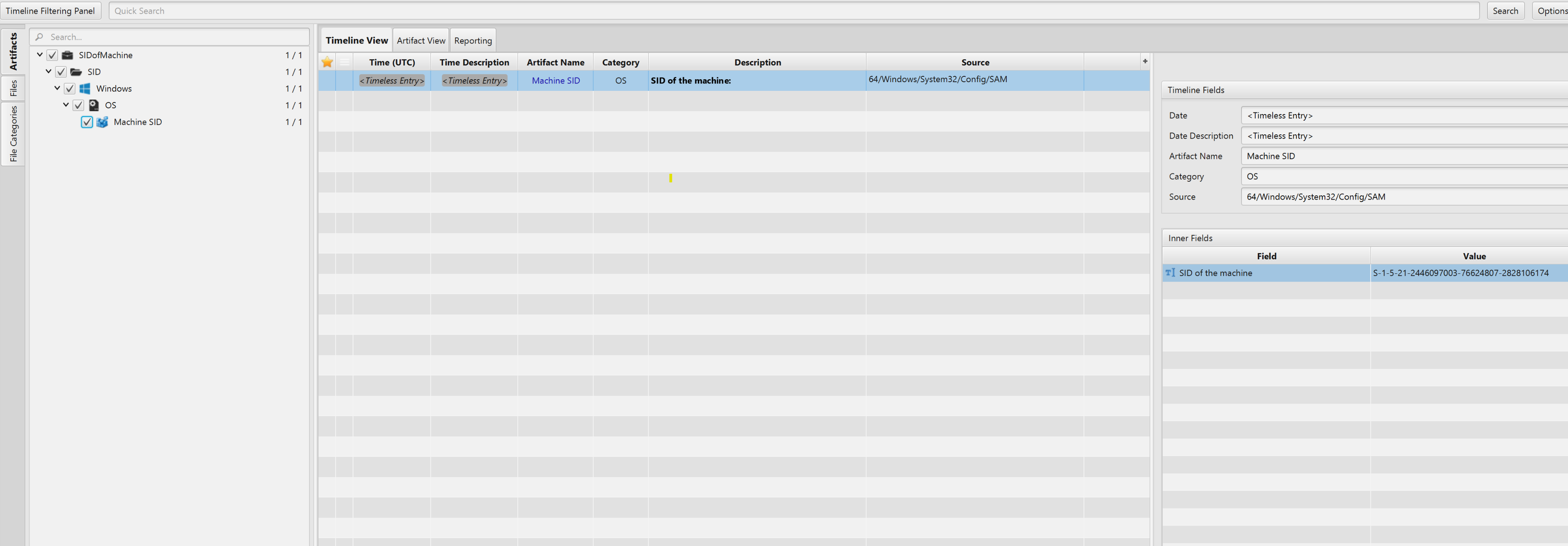
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of the Machine SID artifact in ArtiFast.
Machine SID Artifact
The artifact contains the SID value of an account or group. The details you can view include:
- SID of the machine - A security identifier (SID) is a unique value of variable length used to identify a trustee.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
