Investigating Link File
17/12/2021 Friday
Link Files are Windows shortcut files created automatically by the Windows operating system whenever a user accesses a local or remote file or document. These files, however, can also be created manually by the user. LNK files can point to executables or any other file on the system acting as a direct link to access the original file and they end with “.LNK” extension.

Digital Forensics Value of Link File Artifact
LNK files are excellent sources of evidentiary information during investigations. They typically contain
metadata about accessed files and documents, including the file name, size, the path to the target file,
timestamps (for the original file and the LNK file itself), volume and system information (including volume
name, serial number, NetBIOS name and MAC address), and network information (ex. network share path).
All of this information can be extremely valuable to investigators, especially, when attempting to gain a
better understanding of the suspect’s activity on the system such as program execution, file opening, as
well as malicious code execution. In addition, LNK files have proven to be helpful when investigating files
that may no longer exist on the system as the artifacts persist even after the source files are removed from
the system.
Location and Structure of Link File Artifact
The LNK shortcut files follow the Shell
Link Binary File Format [MS-SHLLINK]. These files are scattered throughout the file system;
however, they are found primary on the following locations:
Windows XP:
- C:\%USERPROFILE%\Recent
Windows 7 to 11:
- C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent
- C:\%USERPROFILE%\AppData\Roaming\Microsoft\Office\Recent
Analyzing Link File Artifact with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Link File artifact from Windows
machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Link File artifact:
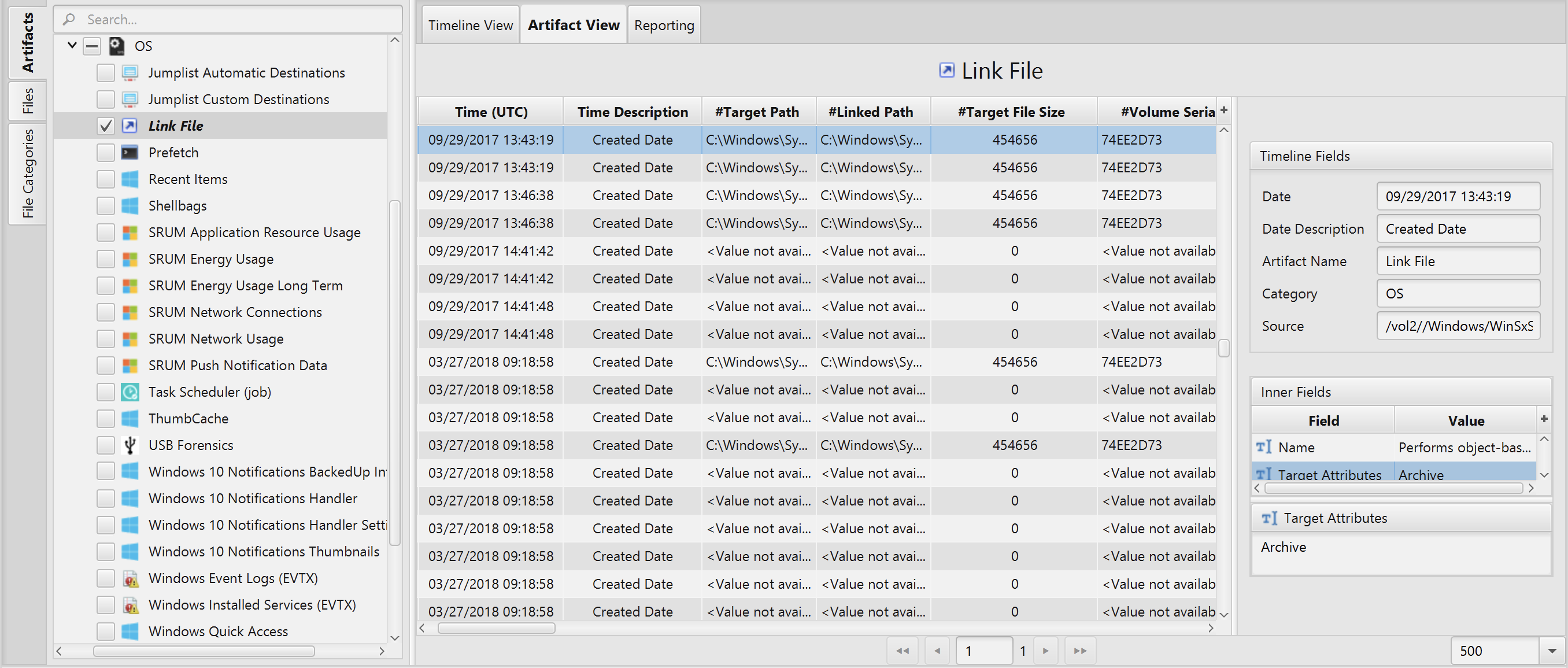
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a list of the details you can view using Link File artifact in ArtiFast Windows.
Link File Artifact
- Target File Created Date
- Target Path
- Linked Path
- Target File Size
- Volume Serial Number
- MAC Address
- Name
- Target File Last Modified Date
- Target File Last Accessed Date
- Show Command
- Volume Name
- Drive Type
- Working Directory
- NetBIOS Name
- Created Date
- Last Modified Date
- Last Accessed Date
- Arguments
- Environment Variable
- Target Attributes
- Relative Path
- Link File Size
- Icon Path
- CNRL Device Name
- CNRL Network Name
- CNRL Network Type
- Hotkey Combination
- Unclassified Data String
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
