Investigating Last Accessed Key
22/10/2021 Friday
All versions of Windows systems include a Registry Editor (regedit). This tool allows users to view the Windows registry and perform various functions within the registry such as creating, modifying and deleting keys, subkeys values and value data. The Last Accessed Key artifact contains the path to the last registry key accessed by the user which is recorded in the “LastKey” value within the “RegEdit” key.
Digital Forensics Value of Last Accessed Key
The information maintained in Last Accessed Key artifact can provide useful indications of user activity. This artifact can also be very useful during cases involving registry tampering.
Location of Last Accessed Key Artifact
Last Accessed Key artifact is stored in the NTUSER.dat registry hive at the following location:
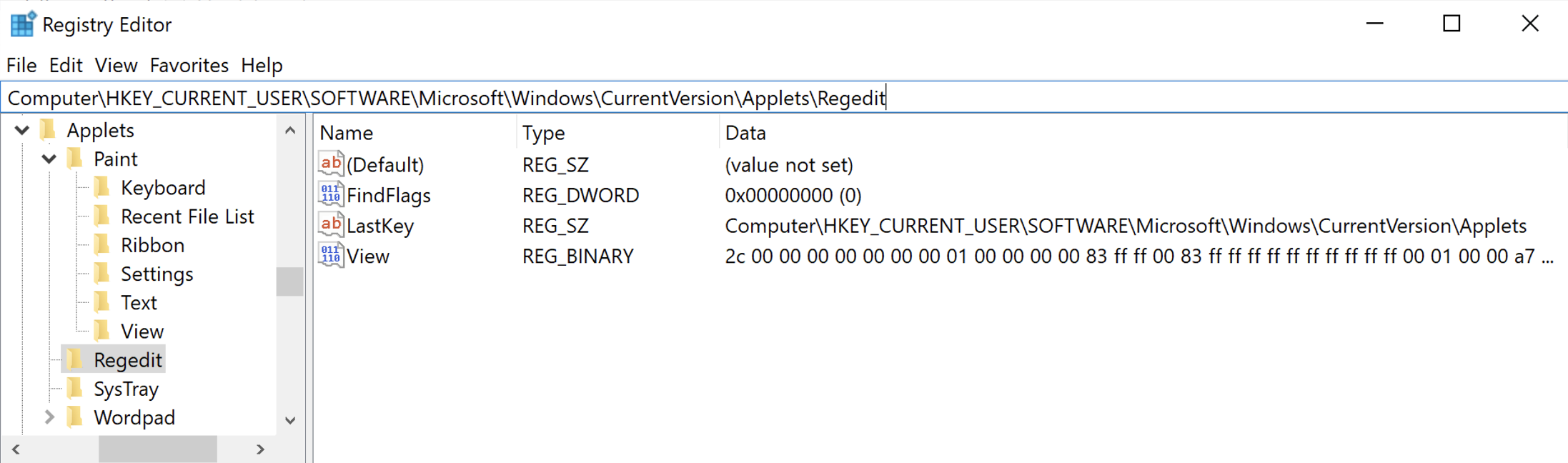
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Applets\RegEdit
Structure of Last Accessed Key Artifact
As seen in the figure below, the LastKey value within the RegEdit key stores the path to the last accessed
key in a string format.
Analyzing Last Accessed Key Artifact with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Last Accessed Key artifact from Windows
machines and what kind of digital forensics insight we can gain from the artifact.
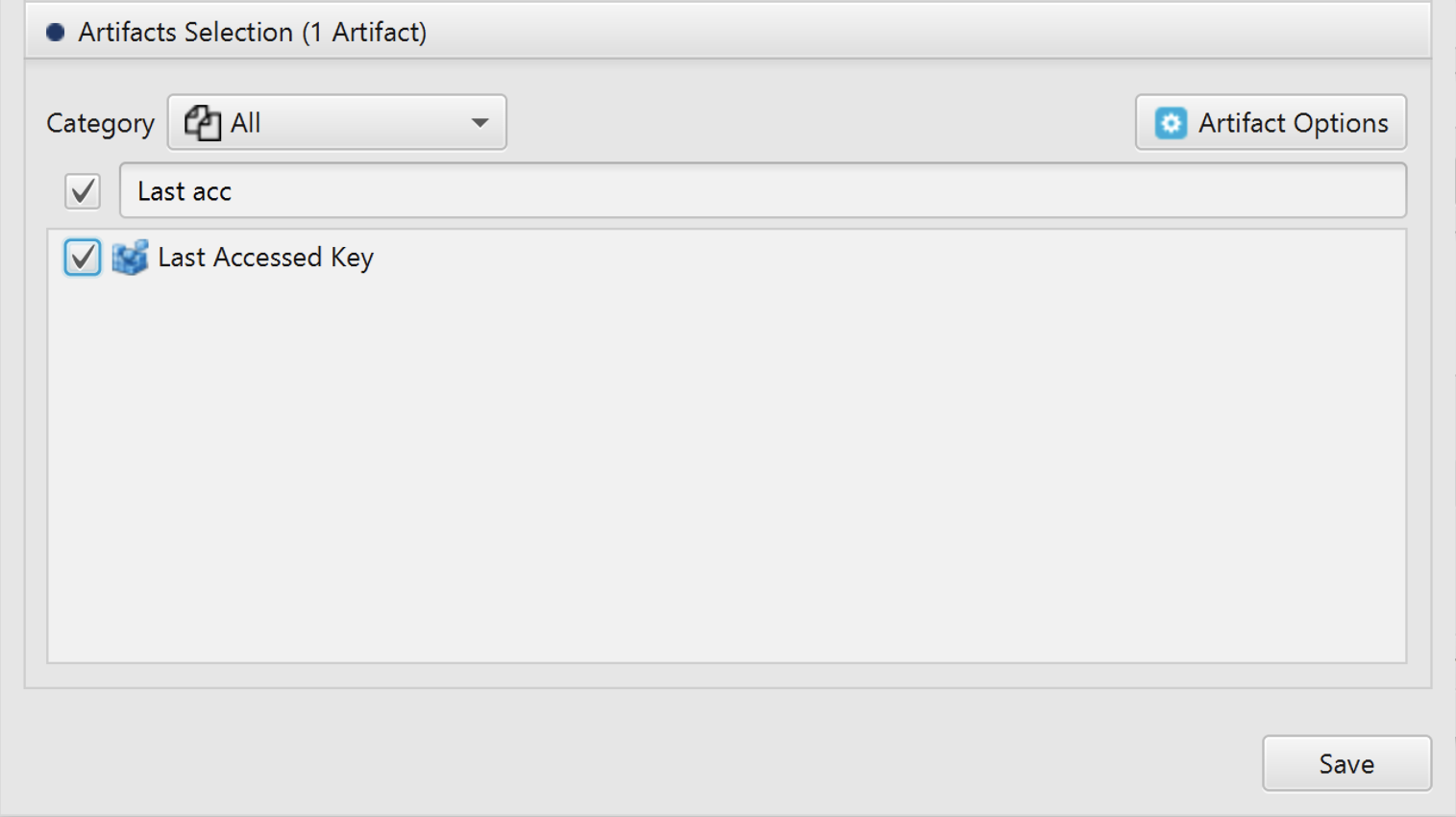
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Last Accessed Key Artifact:
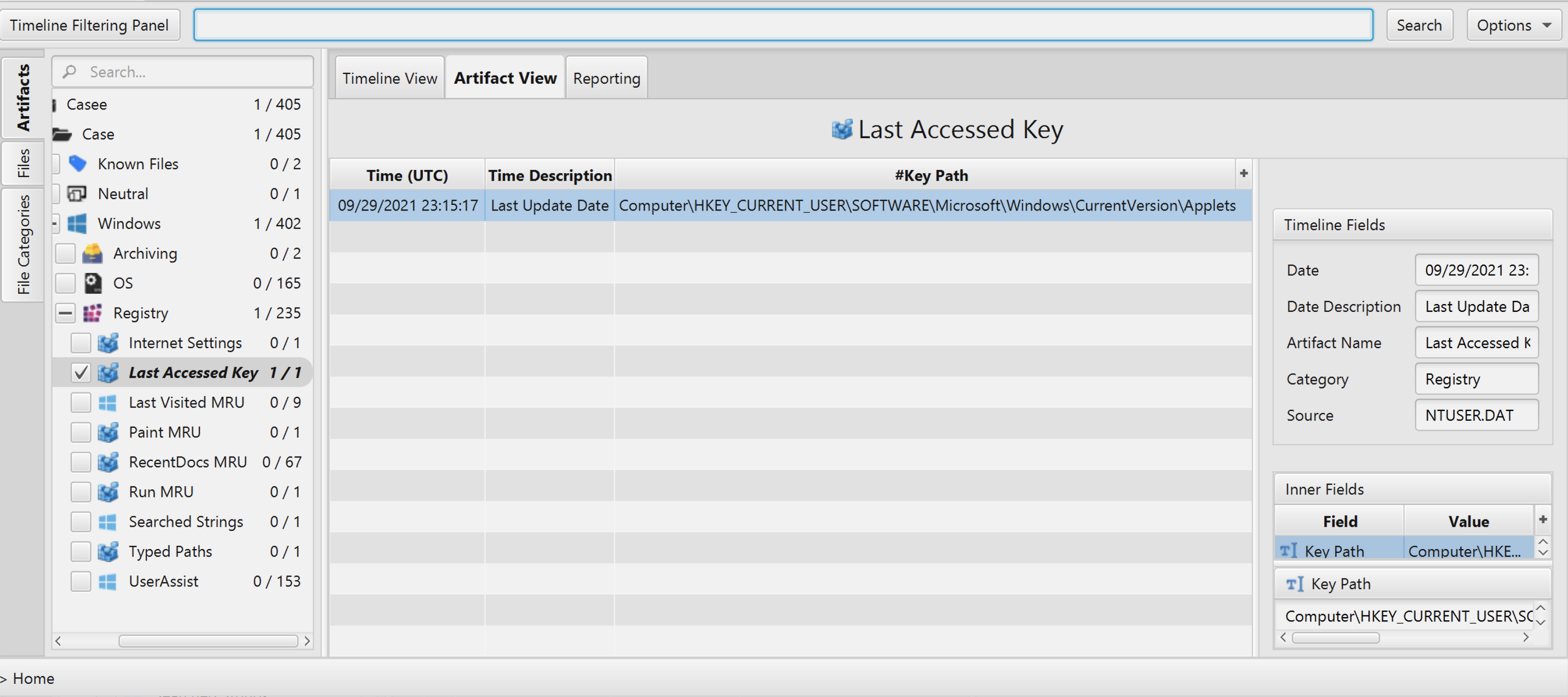
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a detailed description of Last Accessed Key artifact in ArtiFast Windows.
Last Accessed Key Artifact
- Key Path - Last accessed key path.
- Last Update - The date and time when the RegEdit key was last modified.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
