Investigating Jump Lists
10/12/2021 Friday
Jump Lists feature was first introduced with Windows 7 and continued in later versions of Windows systems including Windows 11. The feature is designed to provide the user with quick access to recently accessed application files and common tasks.
Digital Forensics Value of Jumplist Artifacts
The records maintained by Jump Lists are considered an important source of evidentiary information during investigations. The analysis of Jump List files can provide valuable information about users’ historic activity on the system such as file creation, access and modification. Examiners can utilize data extracted from Jump List files to construct a timeline of user activities. What makes this artifact more valuable is the fact that the information is maintained on the system long after the source file and application have ceased to exist on the system.
Location and Structure of Jumplist Artifacts
In Windows systems, two types of Jump Lists can be created:
- *.automaticDestinations-ms (autoDest) files in AutomaticDestinations subdirectory.
- *.customDestinations-ms (custDest) files in CustomDestinations subdirectory.
Each file consists of 16-digit hexadecimal number which is the AppID (Application Identifier) followed by automaticDestinations-ms or customDestinations-ms extension. Note that these files are hidden and navigating through Windows Explorer will not reveal them even if you turned on hidden items in Windows Explorer. They can be viewed by entering the full path in Windows Explorer address bar.
AutomaticDestinations:
The AutomaticDestinations Jump List files are located in the following directory:-
C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations
CustomDestinations:
The CustomDestinations Jump List files are located in the following directory:-
C:\%UserProfile%\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations
Analyzing Jumplist Artifacts with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Jumplist artifact from Windows
machines and what kind of digital forensics insight we can gain from the artifacts.
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Jumplist artifacts:
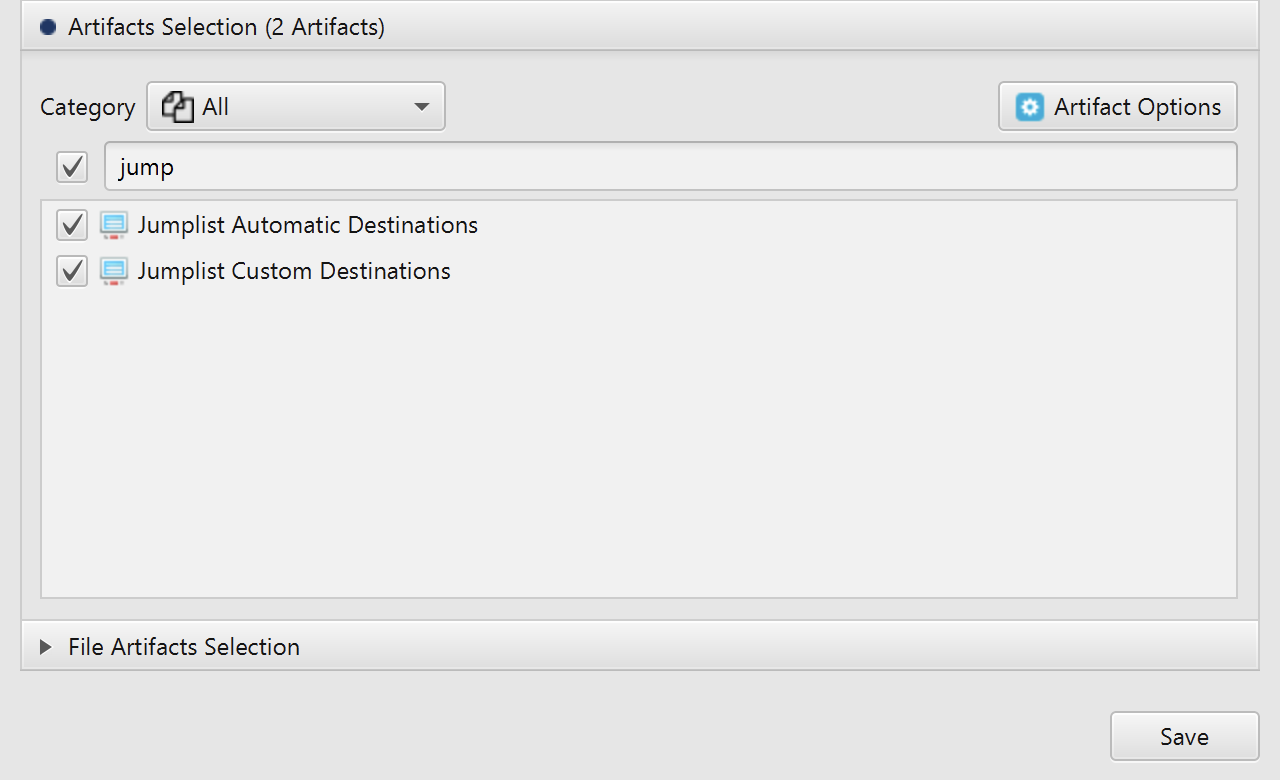
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a detailed description of Jumplist artifacts in ArtiFast Windows.
Jumplist Automatic Destinations Artifact
- Application ID - Application ID.
- Application Name - Application name.
- Common Path - Common path.
- Destination List Version - Destination list version.
- Drive Type - Drive type.
- Entry Accessed Date/Time - Modified Date/Time.
- Entry Created Date/Time - Created Date/Time.
- Entry Number - Entry number.
- Extra Blocks Present - Extra blocks present.
- File Attributes - File attributes.
- File Birth Droid - File birth droid.
- File Droid - File droid.
- File Size - File size.
- Header Flags - Header flags.
- Host Name - Host name.
- Interaction Count - Interaction count.
- Last Used Entry Number - Last used entry number.
- Local Path - Local path.
- MAC Address - MAC address.
- MRU - MRU.
- Path - Path.
- Pin Status - Whether the user pinned the file.
- Relative Path - Relative path.
- Source Accessed Date/Time - Source accessed Date/Time.
- Source Created Date/Time - Source created Date/Time.
- Source Modified Date/Time - Source modified Date/Time.
- Target Accessed Date/Time - Target accessed Date/Time.
- Target Created Date/Time - Target created Date/Time.
- Target Modified Date/Time - Target modified Date/Time.
- Tracker Created Date/Time - Tracker created Date/Time.
- Volume Birth Droid - Volume birth droid.
- Volume Droid - Volume droid.
- Volume Label - Volume label.
- Volume Serial Number - Volume serial number.
- Working Directory - Working directory.
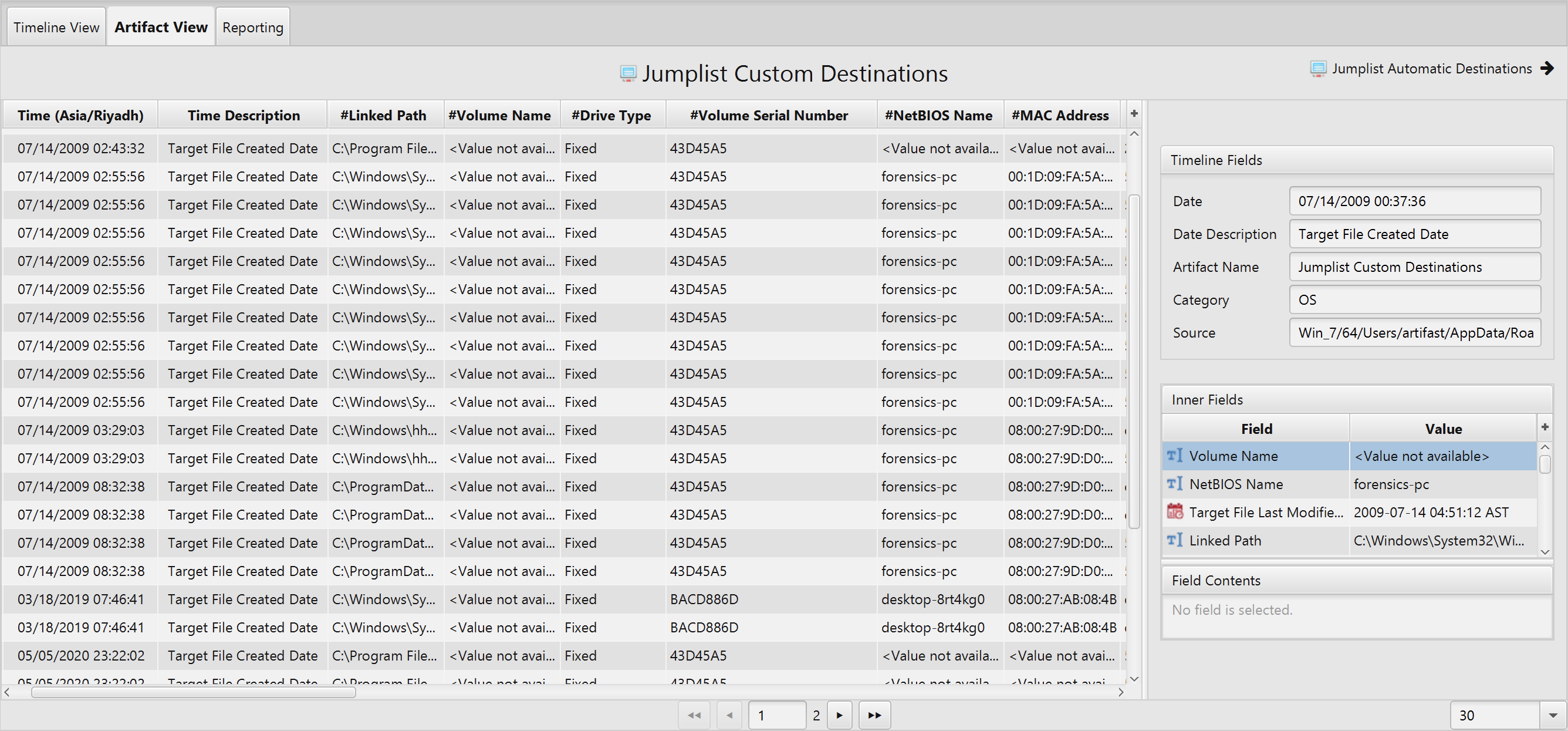
Jumplist Custom Destinations Artifact
- Created Date - Created date.
- Last Modified Date - Last modified date.
- Last Accessed Date - Last accessed date.
- Target File Size - Target file size.
- Arguments - Target attributes.
- Show Command - Show command.
- Target File Last Accessed Date - Target file last accessed date.
- Target File Created Date - Target file created date.
- Target File Last Modified Date - Target file last modified date.
- Target Attributes - Target attributes.
- Linked Pat - Linked path.
- Volume Name - Volume name.
- Drive Type - Drive type.
- Volume Serial Number - Volume serial number.
- NetBIOS Name - NetBIOS name.
- MAC Address - MAC address.
- Application ID - Application ID.
- Located At - Located at.
- Potential App Name - Potential app name.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
