Investigating iOS Gettr
25/07/2025 Friday
GETTR is a social media platform founded by Jason Miller, a former
advisor to Donald J. Trump. Launched in 2021, it was created as an
alternative to mainstream platforms like Twitter, emphasizing free
speech and minimal content moderation. GETTR aims to provide a space for
open discussion, particularly catering to users who feel censored or
restricted by traditional social media sites. The platform promotes
itself as a hub for political discourse, news sharing, and unrestricted
expression.
Digital Forensics Value of iOS Gettr
The digital forensics value of iOS Gettr lies in its potential to
provide critical evidence related to user activity, communications, and
content shared on the platform. As a social media app emphasizing free
speech, it may contain data relevant to investigations involving
cybercrime, harassment, extremism, or disinformation campaigns. Forensic
analysis can uncover user profiles, posts, messages, metadata, and
behavioral patterns, aiding legal and investigative processes. This
makes Gettr a valuable source of information for law enforcement and
cybersecurity professionals.
Location of iOS GETTR Artifacts
iOS Gettr artifacts can be found at the following location:
private/var/mobile/Containers/Data/Application/<App-GUID>/Documents/db_****.sqlite
Analyzing iOS Gettr Artifacts with ArtiFast
This section will discuss using ArtiFast to extract iOS Gettr artifacts
from iOS device files and what kind of digital forensics insights we can
gain from the artifacts.
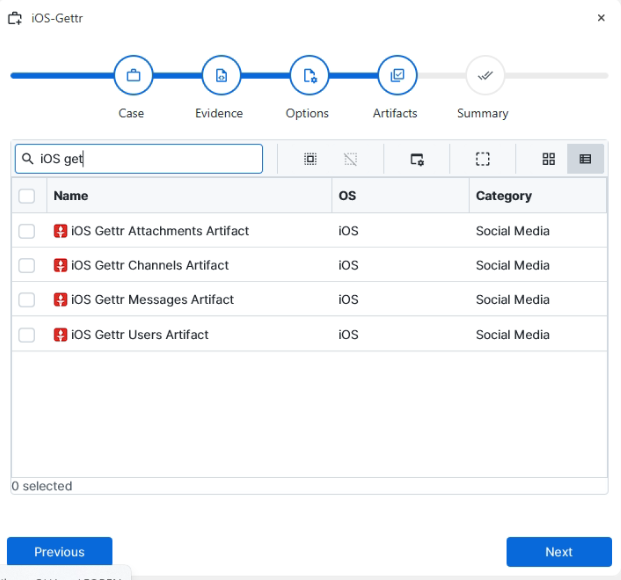
After you have created your case and added evidence for the
investigation, at the Artifact Selection phase, you can select iOS Gettr
artifacts:
×
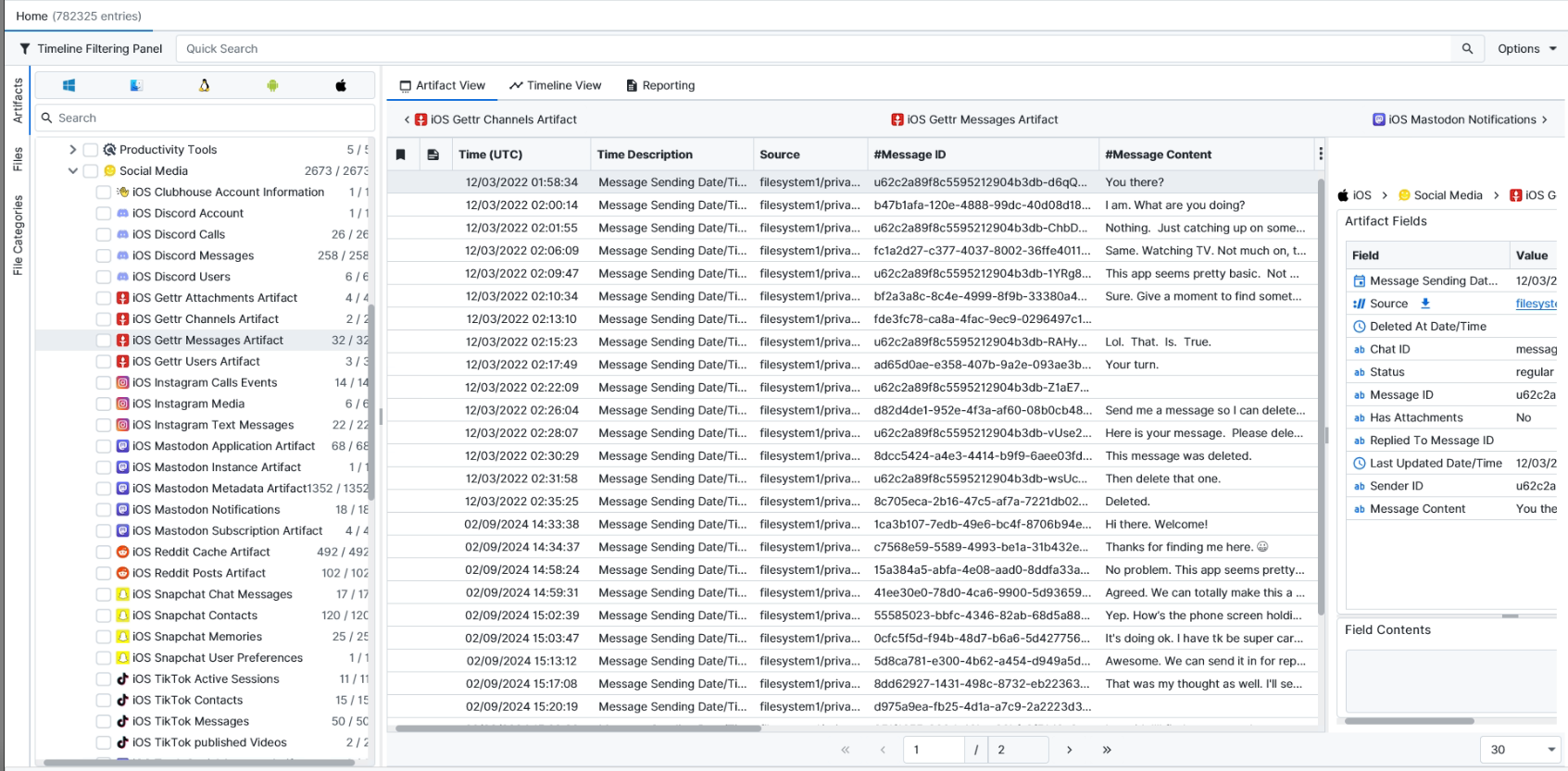
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of iOS Gettr artifacts in ArtiFast.
iOS Gettr Users
- User Name: The user name.
- User ID: The User identifier.
- Creation Date: The date and time the account was created.
- Is Verified: Indicates whether the account is verified or not.
- Profile Picture URL: The user profile picture’s URL.
- Last Active Date/Time: The last date and time the user was last active.
- Account Type: The account type.
iOS Gettr Messages
- Sending Date/Time (UTC): The message sending date and time in UTC.
- Deleted At Date/Time: The time and date when the message was deleted.
- Status: The status of this message.
- Has Attachments: Indicates whether the message has an attachment or not.
- Replied To Message ID: The ID of the replied-to message, if it exists.
- Last Update Date/Time: The last date and time the message was updated.
- Sender ID: The message sender ID.
- Message ID: The message identifier.
- Chat ID: The chat identifier.
- Message Content: The message body content.
iOS Gettr Channels
- Date/Time: The date and time the channel information was modified (UTC).
- Members Information: The information of the channel members.
- Creator ID: The channel creator user identifier.
- Number of Participants: The number of the channel participants.
- Channel Type: The channel type.
- Channel ID: The channel identifier.
- Last Sent Message Date/Time: The time and date when the last message was sent.
- Created Date/Time: The date and time the channel was created.
iOS Gettr Attachments
- Message ID: The ID of the replied-to message, if it exists.
- File Type: The attachment file type.
- File Size: The attachment file size.
- File Name: The attachment file name.
- File URL: The attachment file URL.
- MIME Type: The type of data stored in the attachment.
For more information or suggestions please contact: ekrma.elnour@forensafe.com
