Investigating Installed Programs
19/11/2021 Friday
The Windows Registry maintains a great deal of information regarding system configuration, user activity and so on. Installed Programs artifact is among the useful artifacts extracted from the registry hives. The artifact contains details about the applications installed on the system.
Digital Forensics Value of Installed Programs Artifact
Installed Programs artifact retain information such as the name of the installed application, version, size, publisher, date when the application was last installed or updated, location of the application's executable and many other details related to the applications installed on the system. Retrieving such information may have a significant impact on forensic examinations.
Location of Installed Programs Artifact
Installed Programs artifact is extracted from the SOFTWARE registry hive at the following locations:
- Microsoft\Windows\CurrentVersion\Uninstall
- WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall
The NTUSER.DAT hive also stores information related to the applications installed on the system at:
- SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
Structure of Installed Programs Artifact
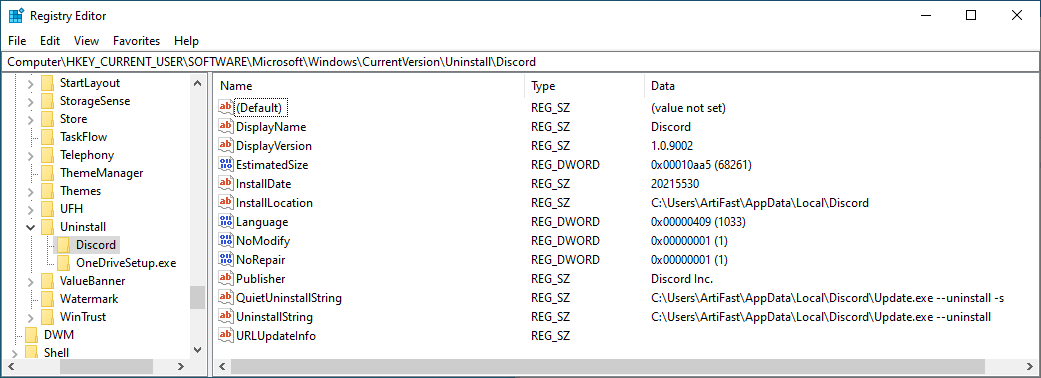
The Uninstall key contains information related to the applications installed on the system. As demonstrated
in the figure below, each application installed has its own key. The values within each subkey contains
detailed information about that application such as the name of the installed application, version, size,
and so on.
Analyzing Installed Programs Artifact with ArtiFast Windows
This section discusses how to use ArtiFast Windows to analyze Installed Programs artifact from Windows
machines and what kind of digital forensics insight we can gain from the artifact.
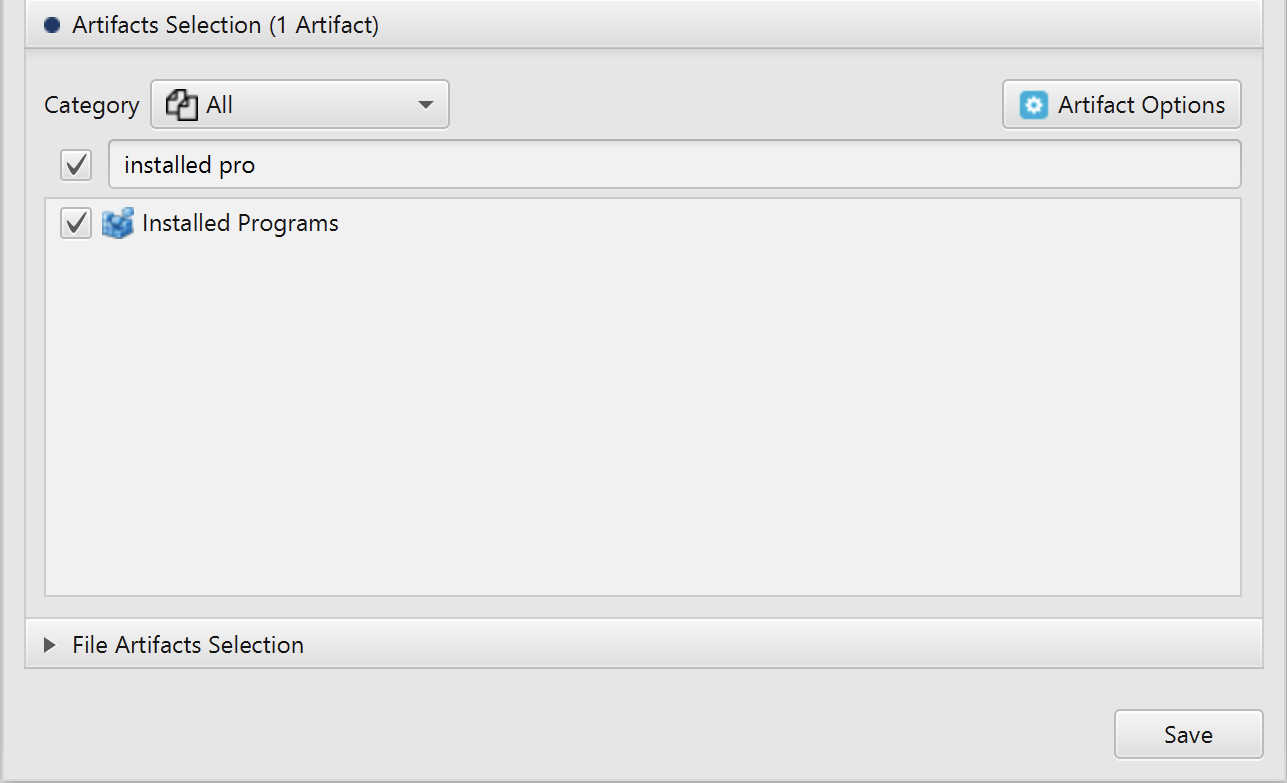
After you have created your case and added evidence for the investigation, at the Artifacts Selection phase,
you can select Installed Programs artifact:
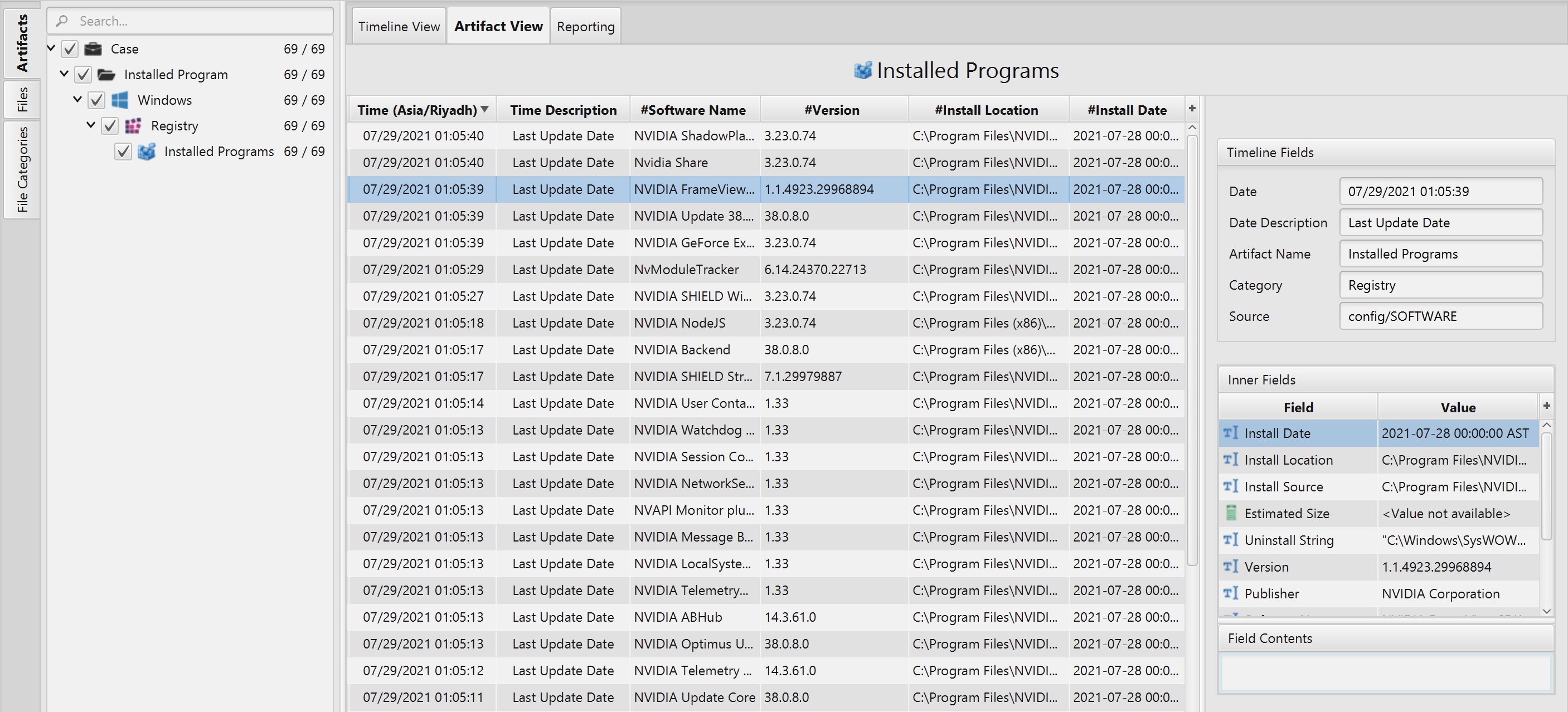
Once ArtiFast parser plugins complete processing artifacts for analysis, it can be reviewed via “Artifact View” or “Timeline View”, with indexing, filtering, and searching capabilities. Below is a detailed description of Installed Programs artifact in ArtiFast Windows.
Installed Programs Artifact
This artifact contains information related to the
applications installed on a system. The details you can view include:
- Last Update - Last Update Date.
- Software Name - Installed software name.
- Version - Installed software version.
- Install Location - Path to installed program.
- Install Date - Last install or update date.
- Publisher - Software publisher name.
- Estimated Size - Software estimated size.
- Install Source - Path to install source.
- Modify Path - Path to modify installation.
- Display Icon - Software display icon location.
- Uninstall String - Uninstall command path.
- Help Link - Software help link.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
