Using Artifast Suite for Incident Response Investigations
19/09/2025 Friday
When conducting incident response investigations, one of the first challenges is how to collect and process forensic evidence efficiently without overwhelming analysts with unnecessary data. Triage packages created with tools such as CyLR or Velociraptor Offline Collector strike a balance between speed and coverage. These packages typically contain the majority of artifacts relevant in incident response scenarios, including Windows event logs, registry hives, scheduled tasks, prefetch files, and browser history. Unlike full disk images, triage collections cannot be used for file carving or recovery of deleted files. However, in the majority of incident response cases, such capabilities are not required.
A key advantage of triage packages is speed. Parsing a triage archive in Artifast Suite is generally around five times faster than processing a full disk image. This reduction in time is particularly valuable when dozens of systems must be analyzed in parallel during an investigation. At present, Artifast does not support multiple images per case, meaning each system requires its own case. While this may initially appear to be a limitation, it also contributes to keeping investigations organized and focused.
When creating a new case in Artifast Suite, it is advisable to change the default timezone. By default, Artifast displays results in the timezone of the analyst’s device, which can lead to inconsistencies when comparing results across multiple systems. Using UTC provides a consistent baseline across all investigations.
Once the image is loaded, the next step is file processing configuration. For triage images, options such as hash calculation, encrypted file detection, or file carving are typically unnecessary. These are more relevant for full forensic disk investigations. Because triage archives contain only the files and artifacts of interest, enabling these options adds processing time without delivering significant additional value.
The following page allows for artifact selection. Artifast Suite supports selective artifact processing, but as artifact-to-file matching is extremely fast, selecting all available artifacts is generally the most efficient approach to ensure no relevant evidence is overlooked. Analysts who require a more focused dataset may select specific artifacts manually, depending on the case.
Processing time depends on the size of the logs contained in the triage package. On average, parsing a Windows triage image requires between thirty and forty-five minutes, with larger collections—particularly those containing extensive event logs—taking longer. Once parsing is complete, results are displayed chronologically. Reversing the order to display the most recent events first often highlights the final attacker activity before detection. This adjustment can be made in the timeline view by changing the sorting order. Increasing the number of displayed entries per page to five hundred is also recommended, as this helps maintain context by reducing the need to switch between pages.
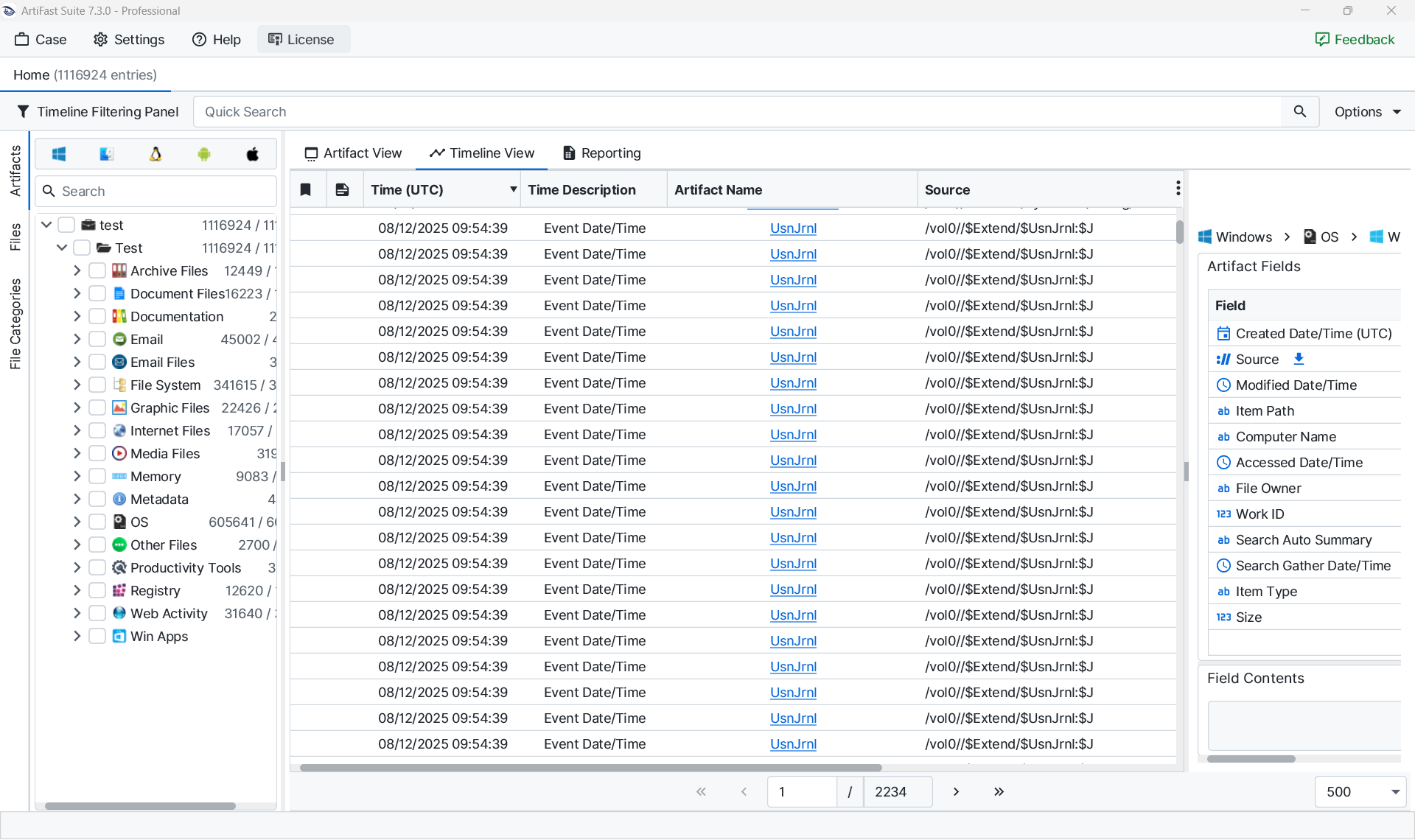
Working with Artifact View
The Artifact View is the primary interface for detailed analysis. Reviewing activities artifact by artifact provides a structured workflow. The Timeline Filtering Panel is particularly valuable for narrowing results to specific timeframes, for example, the known incident window. This significantly improves focus during investigations.
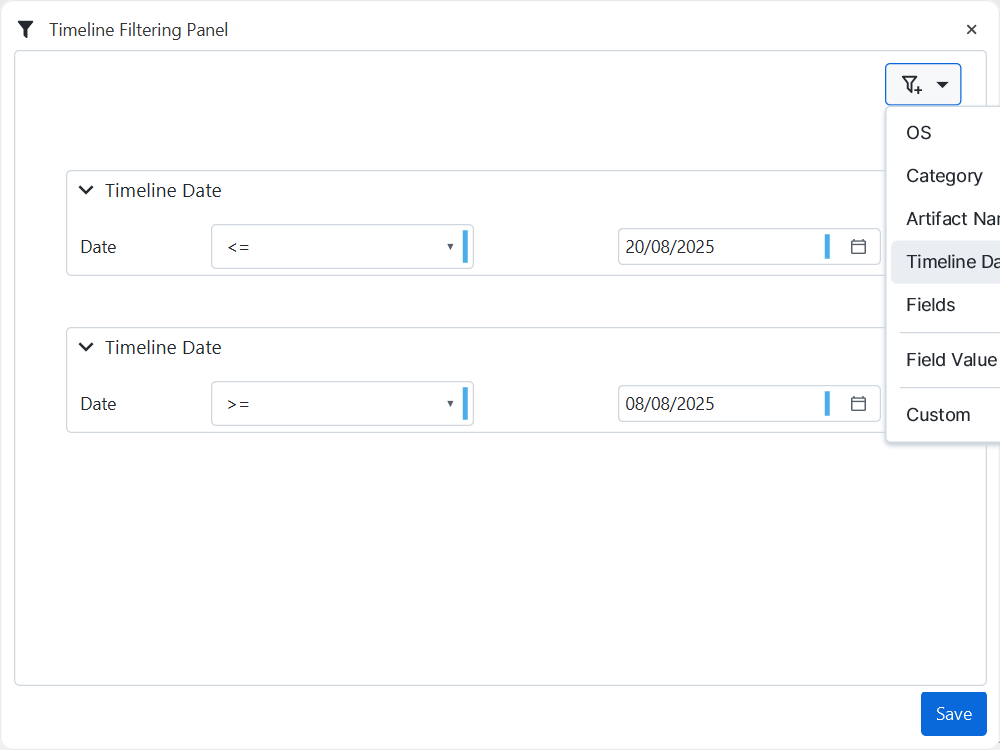
Expanding all artifacts in the left-hand panel and reviewing their contents systematically ensures comprehensive coverage. Suspicious or unusual items can be bookmarked for further attention.
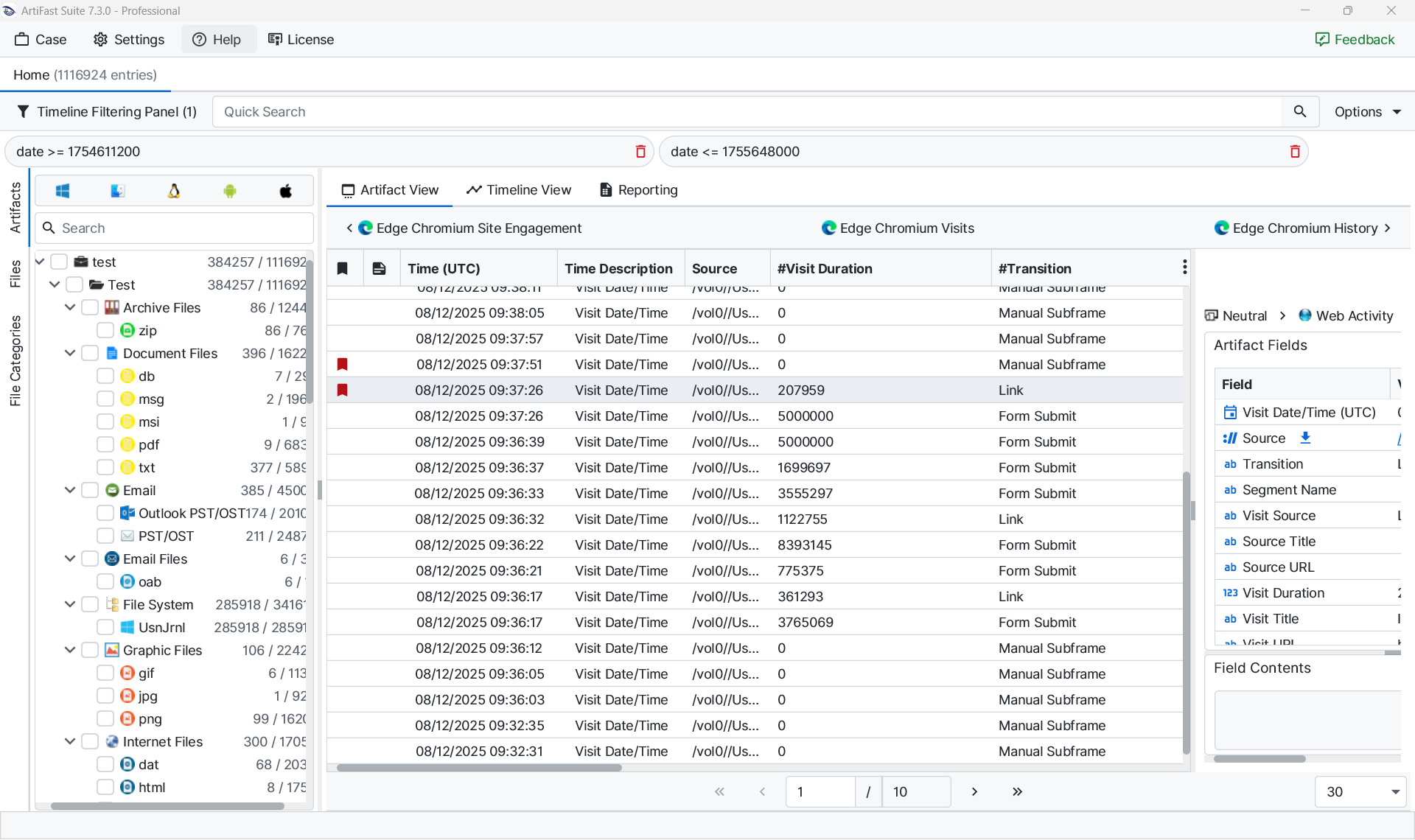
Windows event logs, however, frequently contain hundreds of thousands of entries, making manual review impractical. In these cases, custom filters are essential. Artifast Suite supports the creation of reusable filters tailored to attacker activities. For example, the following query isolates login activity:
(artifact_id = 10100302 AND (#"Event ID" = '4624' OR #"Event ID" = '4625' OR #"Event ID" = '4634'))
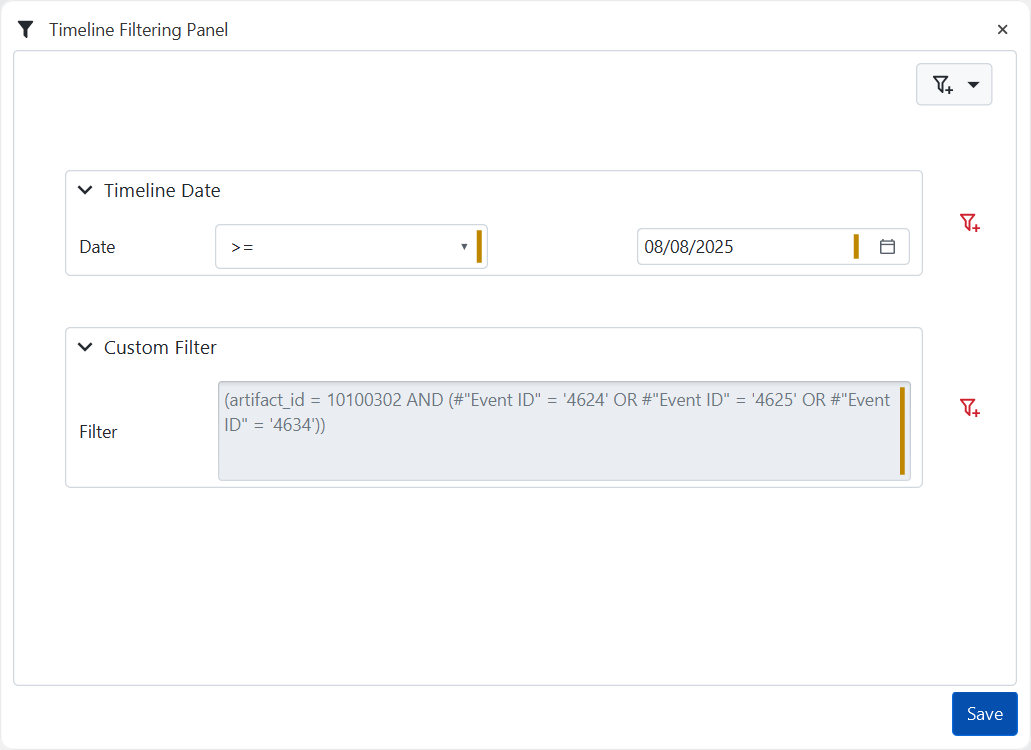
Expanding all artifacts in the left-hand panel and reviewing their contents systematically ensures comprehensive coverage. Suspicious or unusual items can be bookmarked for further attention.
Custom Filters for Windows Event Logs
Windows event logs are among the richest but also most complex artifacts. Because of the high volume of entries, custom filters are critical to narrowing the dataset to attacker-relevant activities. A set of reusable queries has proven effective across most cases:
- Login activity (successful logons, failed logons, logoffs):
(artifact_id = 10100302 AND (#"Event ID" = '4624' OR #"Event ID" = '4625' OR #"Event ID" = '4634')) - Explicit credential use (event ID 4648):
(artifact_id = 10100302 AND #"Event ID" = '4648') - SMB server activity:
(artifact_id = 10100302 AND #"Channel" LIKE '%SMBServer%') - SMB client activity:
(artifact_id = 10100302 AND #"Channel" LIKE '%SMBClient%') - RDP client activity:
(artifact_id = 10100302 AND #"Channel" LIKE '%RDPClient%') - Local Session Manager activity:
(artifact_id = 10100302 AND #"Channel" LIKE '%LocalSessionManager%') - Windows Defender detections (event IDs 1116 and 1117):
(artifact_id = 10100302 AND #"Event ID" = '1116' AND #"Provider Name" = 'Microsoft-Windows-Windows Defender') OR (artifact_id = 10100302 AND #"Event ID" = '1117' AND #"Provider Name" = 'Microsoft-Windows-Windows Defender')
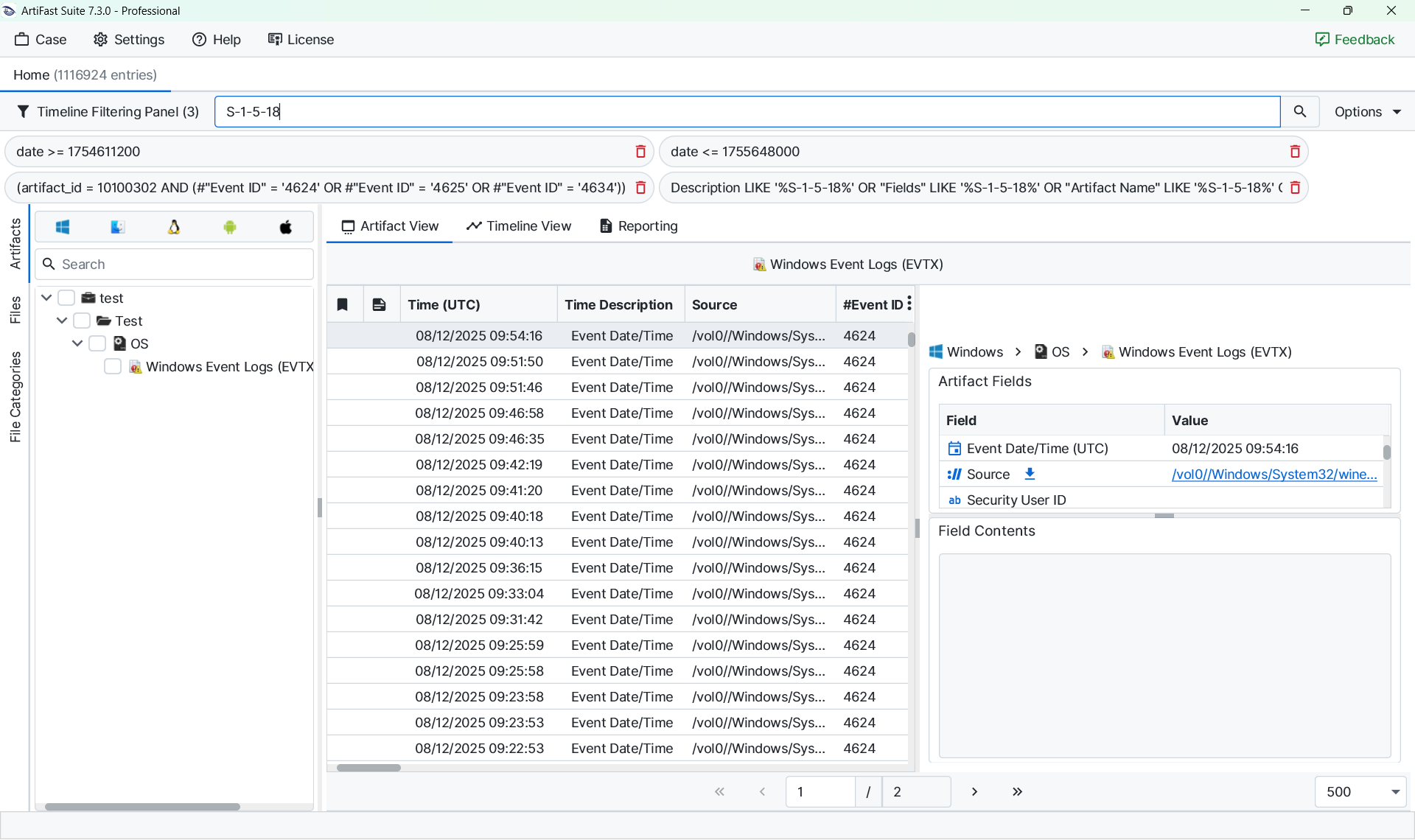
Applying these filters reduces an overwhelming dataset to a manageable set of entries with a high probability of attacker relevance. Quick Search or Quick Time Filters can then be used to build additional context around specific events.
Pivoting with Quick Time Filters
Once suspicious activity has been identified, it is important to review surrounding activity for context. The Quick Time Filters feature facilitates this by displaying other artifacts occurring within the same minute. This makes it easier to determine whether a login event was followed by command execution, process creation, or network activity.
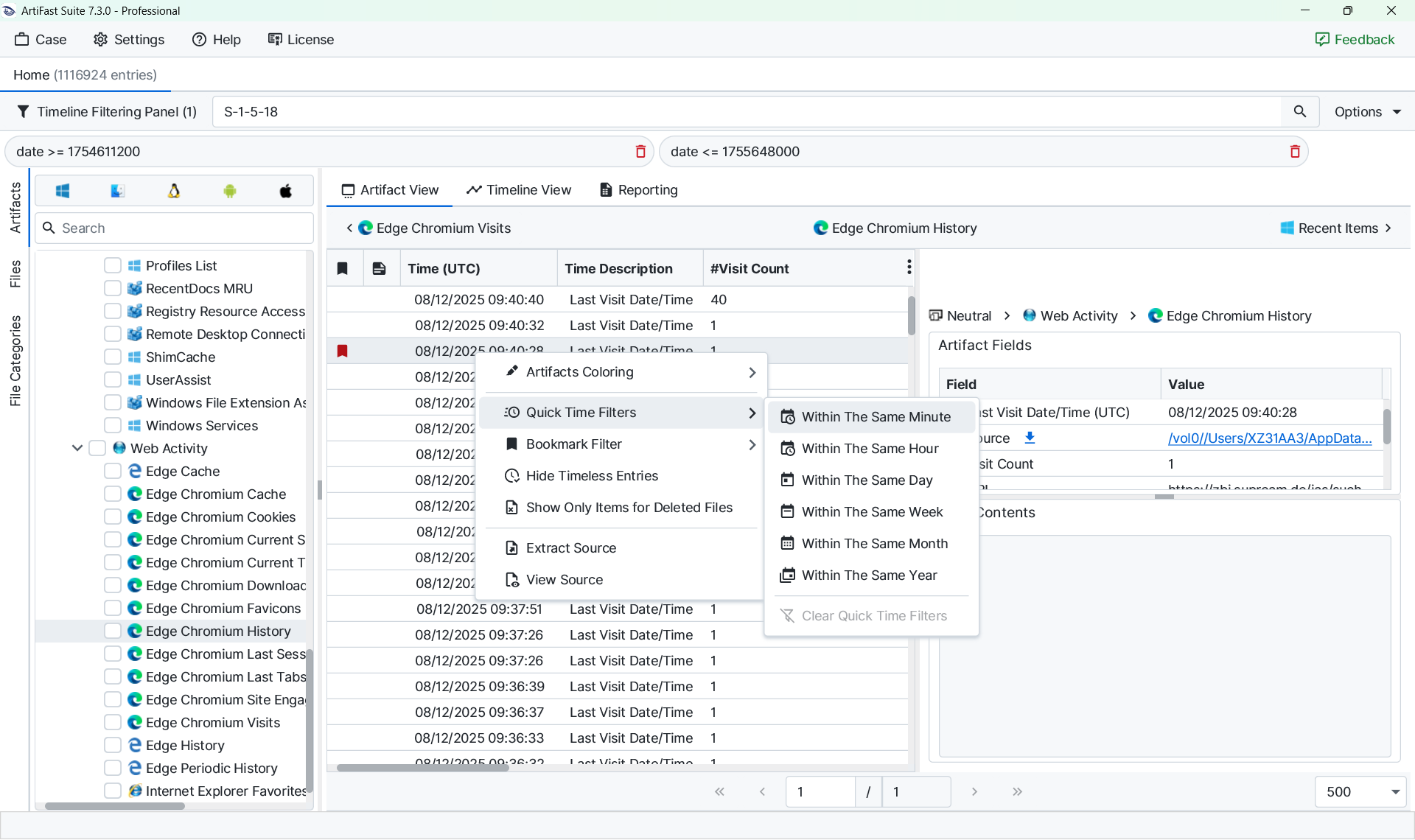
After identifying relevant events, bookmarks can be used to build a focused dataset. By applying a bookmark filter, the view is reduced to suspicious activities only. Switching back to the timeline view then provides a concise overview of attacker activity.
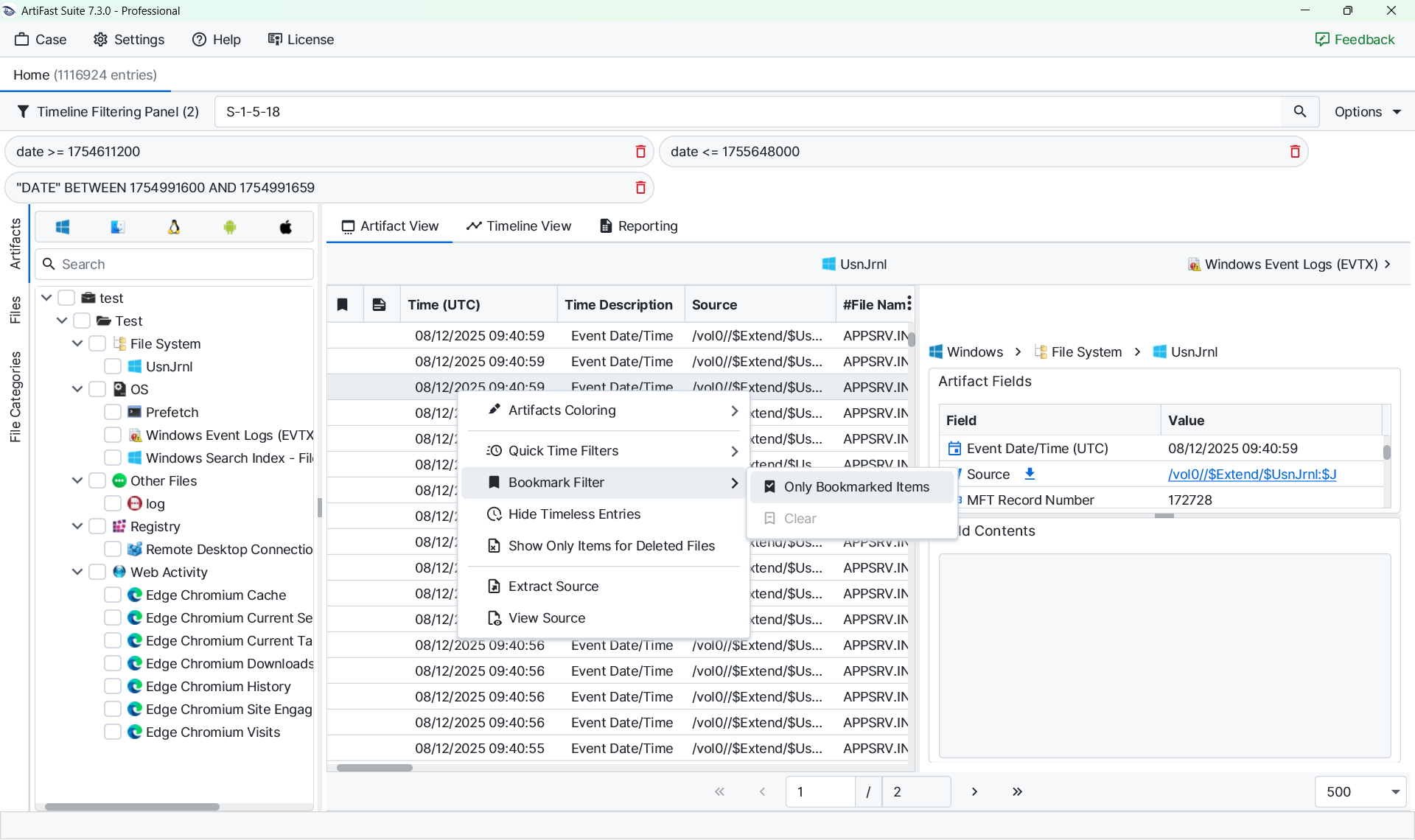
Investigations are iterative, and systems are often revisited as new indicators of compromise emerge. Building custom query templates simplifies this process. For example, if a service account such as SVC_SQL is identified as abused for RDP logins and credential dumping, the following query can be used on previously analyzed systems:
(artifact_id = 10100302 AND #"Event Data" LIKE '%SVC_SQL%' AND (#"Event ID" = '4624' OR #"Event ID" = '4625' OR #"Event ID" = '4634'))
Exporting and Reporting
Exporting results is a critical step for integrating Artifast findings into broader investigations. A common workflow involves filtering for bookmarked items, exporting the timeline into CSV format, and using Python scripts to normalize the data into a unified investigation timeline.
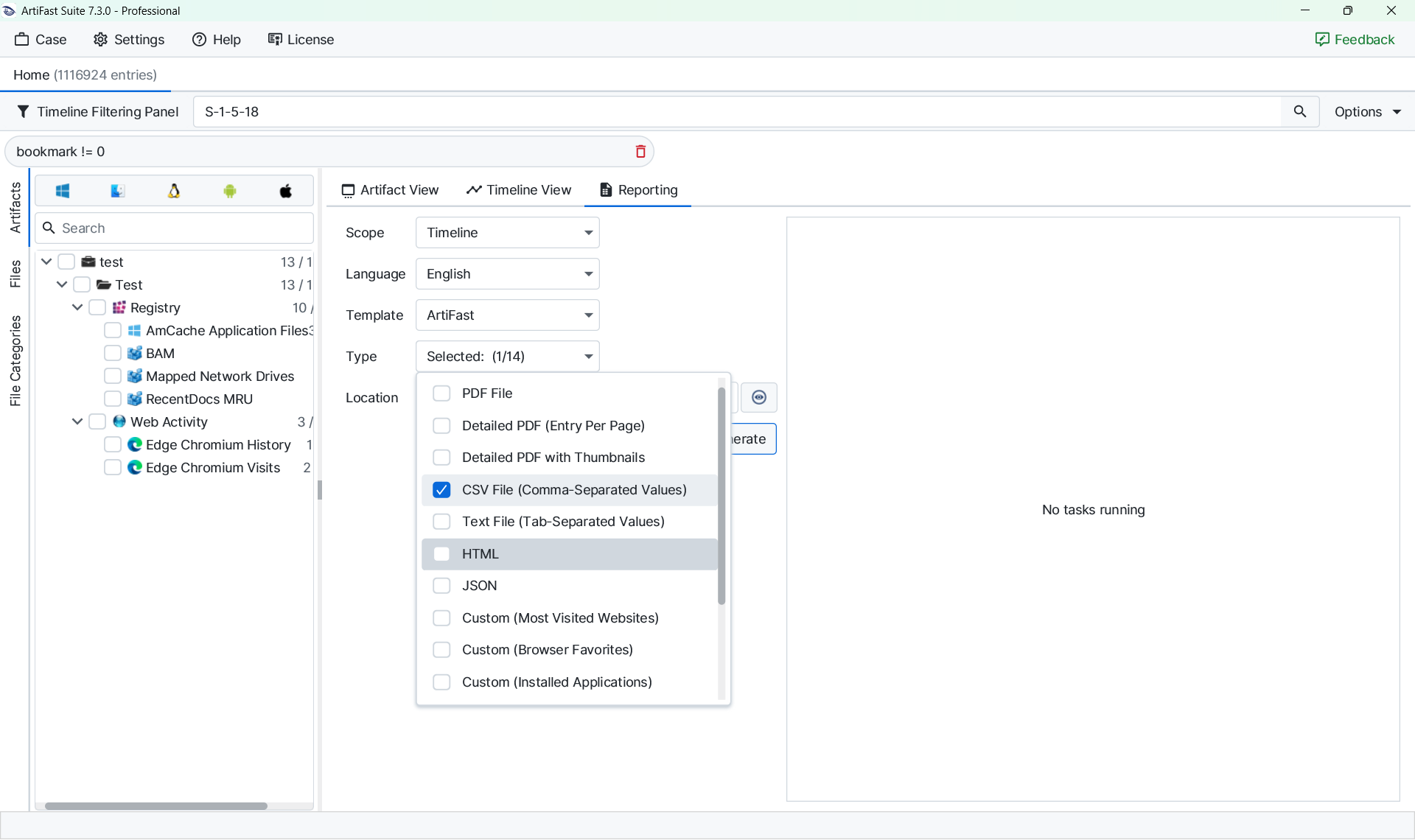
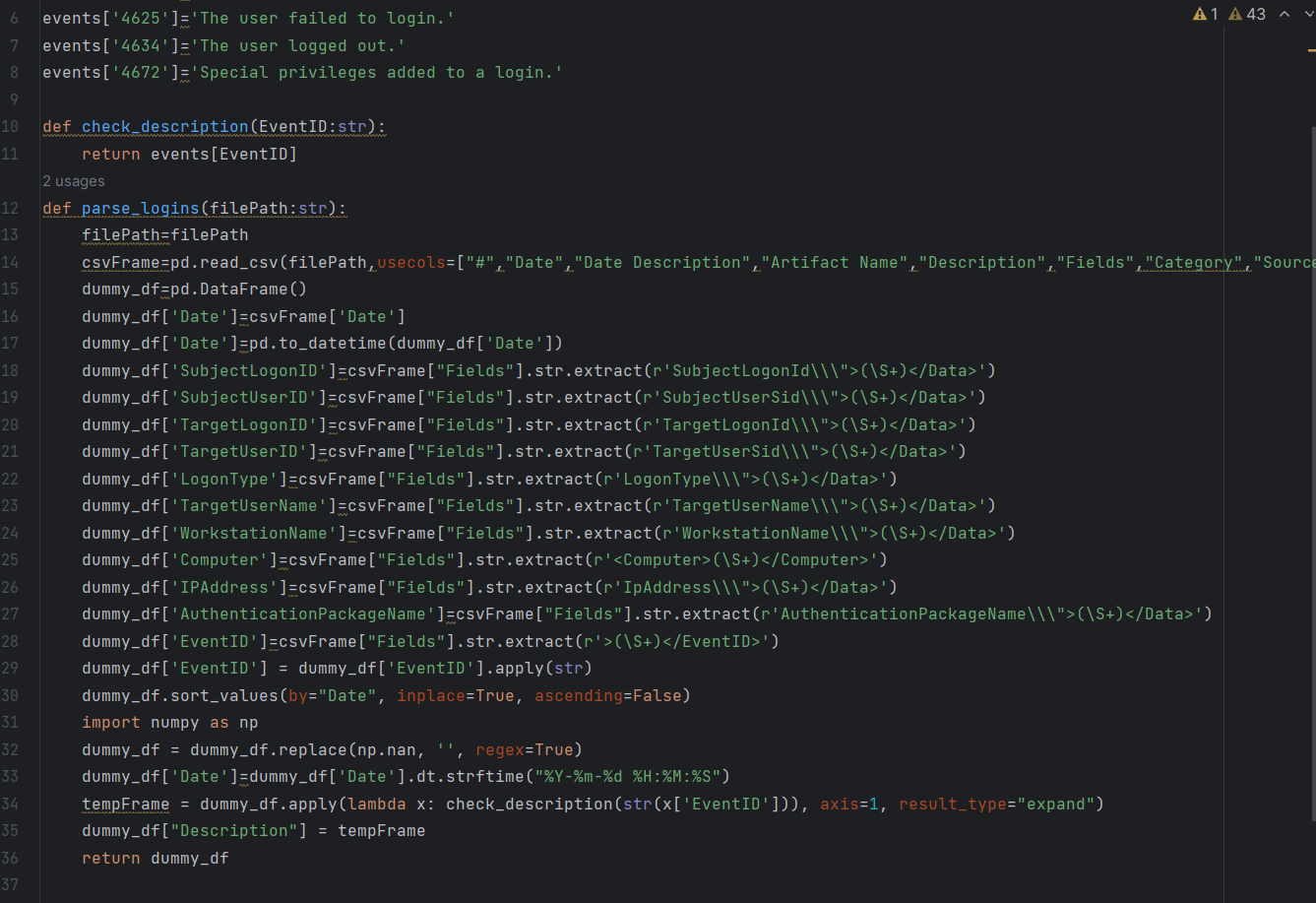
Artifast also supports artifact-based exports, which are useful when extracting specific fields. For example, filtering Windows event logs for login activity, exporting to CSV, and parsing with a script can transform technical fields such as usernames, logon types, and source addresses into clear, plain-language summaries. This makes reporting more accessible to non-technical stakeholders.
Conclusion
By combining triage collection, consistent case setup, custom filters, bookmarks, and export automation, Artifast Suite enables highly efficient incident response investigations. Large volumes of data can be distilled into concise timelines of attacker activity supported by clear evidence. Once a reusable library of queries and filters has been established, analysis and reporting become significantly faster and more consistent across cases.
