Investigating iOS Threema
17/05/2024 Friday
Threema is an open-source end-to-end encrypted instant messaging application and does not require a phone number or any other personally identifiable information. It anonymizes users to some extent. Users can make voice and video calls, and send multimedia, locations, voice messages, and files in addition to text messaging.
Digital Forensics Value of iOS Threema
Messaging application in mobile phones is a rich source of information when it comes to digital forensics investigation. That’s because those applications hold data related to the user’s messaging history along with media attachments and call logs. Threema as an open-source end-to-end encrypted instant messaging application can be a valuable source of information. Threema encrypts all communications end-to-end, including group messages, photos, videos, files, and voice calls. Threema includes its app-specific encryption based on AES-256 to protect stored messages and media.
Location of iOS Threema App Artifacts
iOS Threema App artifact can be found at the following location:
/private/var/mobile/Containers/Data/Application/<App_GUID>/ThreemaData.sqlite
Analyzing iOS Threema Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract iOS Threema artifact from iOS device's files and what kind of digital forensics insights we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select iOS Threema artifact:
×
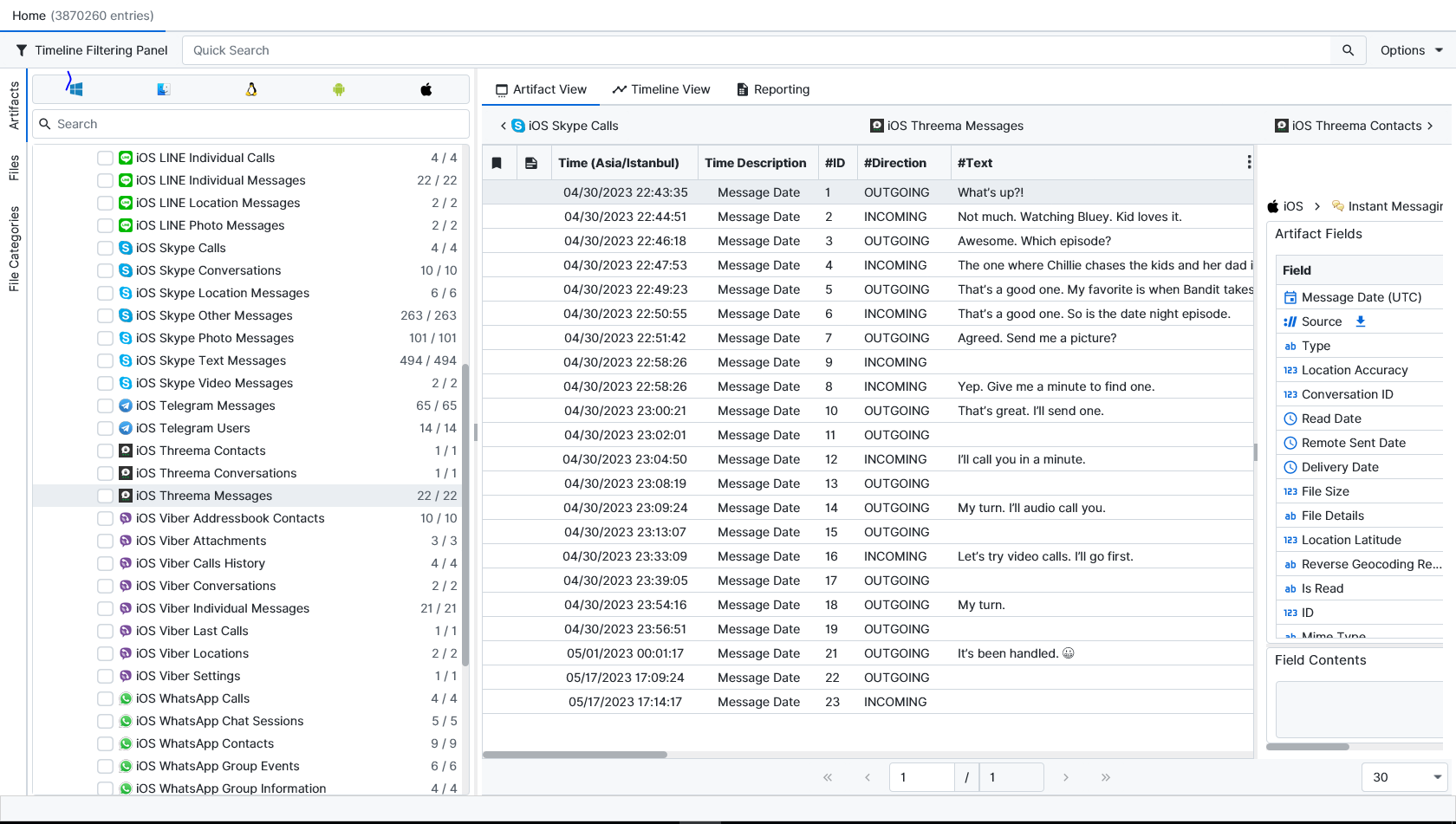
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of iOS Threema App artifact in ArtiFast.
iOS Threema Contacts
- Time: Profile picture update time.
- Public Key: Contact’s public key.
- First Name: The contact’s first name.
- Last Name: The contact’s last name.
- Public Nickname: The contact’s public nickname.
- Is Hidden: Indicates whether the contact is hidden or not.
- Contact ID: The contact’s ID.
- Identity: The contact’s identity.
- Verification Level: Verification level.
iOS Threema Messages
- Time: Message date and time.
- Type: Message type (Text, File, or Call).
- Location Accuracy: The location accuracy.
- Conversation ID: Conversation ID.
- Read Date: The time and date the message was read.
- Remote Sent Date: The time and date the message was sent.
- Delivery Date: The time and date the message was delivered.
- File Size: File size.
- File Name: File name.
- File Details: File details.
- Location Latitude: Location latitude.
- Location Longitude: Location longitude.
- Reverse Geocoding Result: Reverse geocoding results.
- Is Read: Indicates whether the message was read or not.
- ID: Message ID.
- Mime Type: Mime type.
- Text: Message body.
- Is Delivered: Indicates whether the message was delivered or not.
- Arguments: Arguments.
- Direction: Message direction (Incoming, outgoing).
iOS Threema Conversations
- Contact ID: Contact ID.
- Unread Message Count: Unread message count.
- Is Marked: Indicates whether the conversation is marked or not.
- ID: Conversation ID.
- Last Message ID: Last message ID.
- Group Name: Group name.
For more information or suggestions please contact: ekrma.elnour@forensafe.com
