Investigating FileZilla
20/10/2022 Thursday
FileZilla was initially released in 2001 and it is very common among IT community. It is a free open-source, cross-platform file transfer protocol (FTP) application. FileZilla has client and server versions. The client version support connections to FTP and FTPS and SFTP servers while the server version establishes FTP server on the installed platform.
Digital Forensics Value of FileZilla
After installing FileZilla, server connection details and user configurations are stored in XML files. By analyzing FileZilla artifacts, we can collect valuable information about how the user used FileZilla, details about client connected servers, and files transferred between client and server.
Location and Structure of FileZilla Artifacts
FileZilla artifacts including username, password and file transfer queue are stored in XML files at the following location:
C:\Users\[UserProfile]\AppData\Roaming\FileZilla
Analyzing Windows FileZilla Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract FileZilla artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifacts.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select FileZilla artifacts:
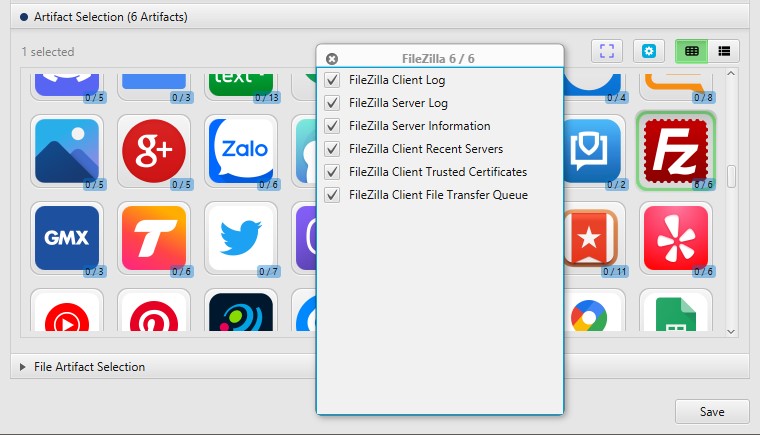
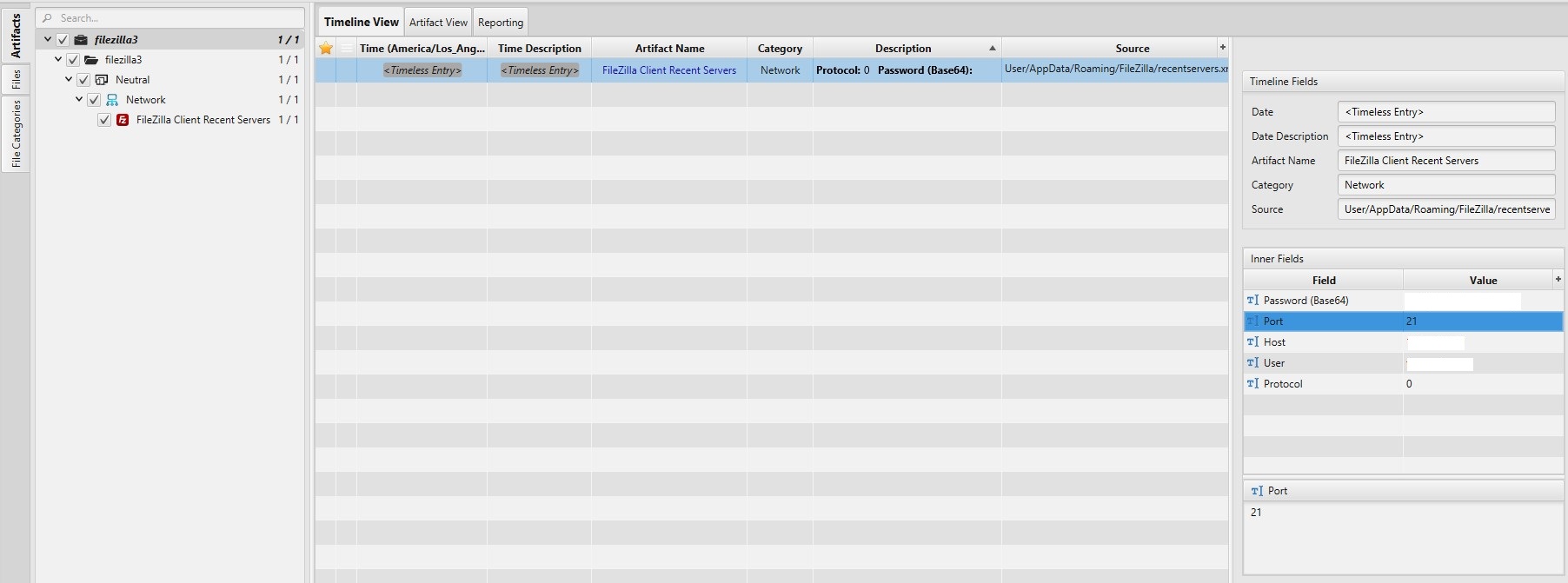
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of FileZilla artifacts in ArtiFast.
FileZilla Client Log Artifact:
- Command Argument - Command argument which is used by the FileZilla client application.
- Connection ID - Connection identification number.
- Process ID - Process identification number.
- Action Type - Action type.
- Action Date - Action date.
FileZilla Server Log Artifact:
- Command Argument - Command argument sent from client to server.
- Initiator IP - FTP connection initiator IP.
- Login Name - Login name for the FTP server.
- Action Date - Action date.
FileZilla Server Information Artifact:
- Name - Server name.
- Host - The host IP or domain name.
- Port - Name of the file being in the queue.
- Password - The client’s password for the server.
- Fingerprint - The fingerprint of the server.
- Last Connected Server - The (domain or IP) and port of the server.
FileZilla Client Recent Servers Artifact:
- Host - IP address of the FTP server.
- Port - Port used by the connection.
- User - Username.
- Password (Base64) - Password in base64 encoding.
- Protocol - Connection protocol.
FileZilla Client Trusted Certificates Artifact:
- Host - IP address of the FTP server.
- Port - Port used by the connection.
- Activation Time - Certificate activation time.
- Expiration Time - Certificate expiration time.
- FTP Session Resumption
FileZilla Client File Transfer Queue Artifact:
- File ID - Unique identification number for the file being transferred.
- Server ID - Unique identification number for the FTP server.
- File Name - Name of the file for transfer.
- Size - Size in bytes.
- Host - IP address of the FTP server.
- Port - Port used by the connection.
- User - Username.
- Password - Password in base64 encoding.
- Local Path - Local directory path of the file being transferred.
- Remote Path - Transfer location of the local file at the remote server.
For more information or suggestions please contact: ummulkulthum.wambai@forensafe.com
