Investigating File Extensions Associations
04/11/2022 Friday
File associations are registry settings in Windows that determine what application to use to open a file of a specified type. Users or applications can set associations for file types so that when the file is opened, a command gets triggered by Windows. For example, when a user double-clicks a text “.txt” file, Notepad.exe will launch. Windows has preset default file associations; however, users can change and customize the associations according to their needs.
Digital Forensics Value of File Extensions Associations
File Associations that are different from the defaults can provide details about how the system was used. During investigations, we can use the associations to give details on which applications were installed on the system and which extensions were related to these installed applications. That information helps prove that the user installed and configured a certain application.
Location and Structure of File Extensions Associations
The following registry locations contain File Extension Associations' details:
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts
HKLM\Software\Classes
Analyzing File Extensions Associations Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract file extension associations artifacts from Windows machines and what kind of digital forensics insight we can gain from the artifacts
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select File Extension Associations artifacts:
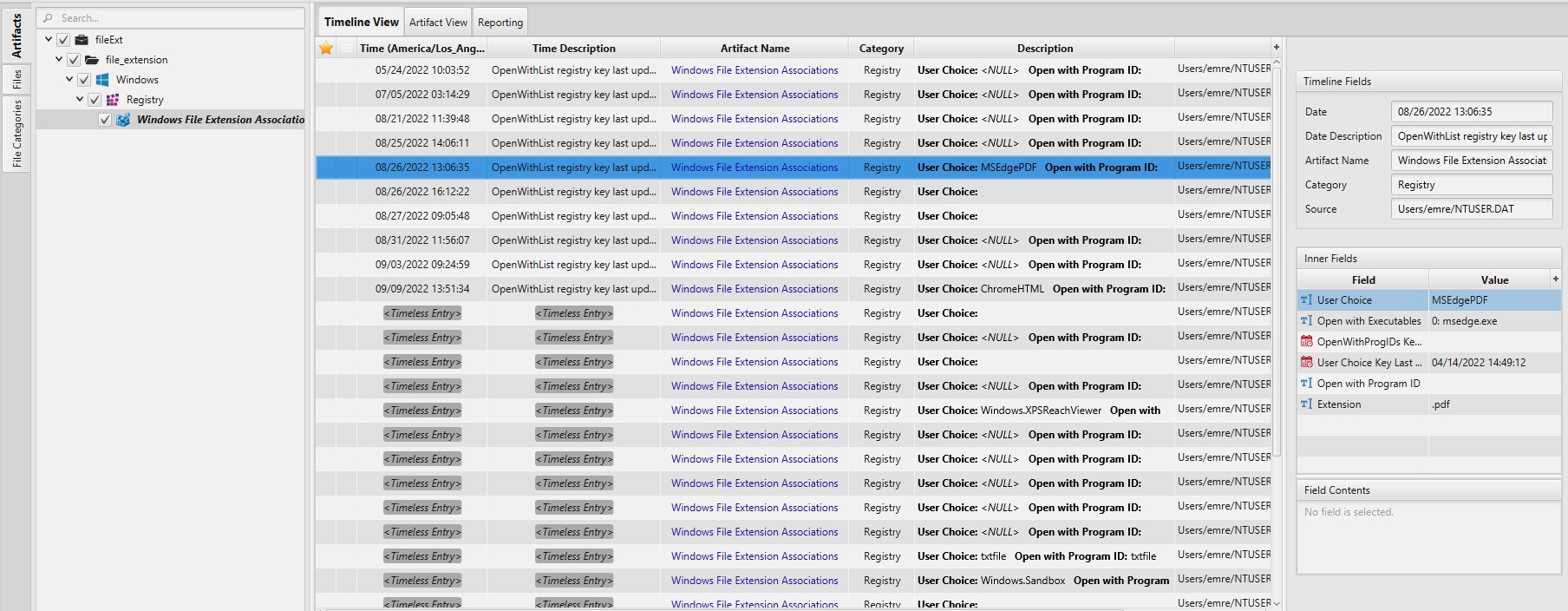
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of File Extension Associations artifacts in ArtiFast.
Windows File Extension Associations Artifact:
- Extension - Extension of the file.
- Open with Executables - The program(s) that was used to open the file extension ranked by the order of execution.
- Open with Program ID - Program ID associated with the extension.
- User Choice - The program chosen by the user for opening the file.
- OpenWithList Key Last Write Date/Time - OpenWithList registry key last update date and time.
- OpenWithProgIDs Key Last Write Date/Time - OpenWithProgIDs registry key last update date and time.
- User Choice Key Last Write Date/Time - User choice registry key last update date and time.
Windows File Extension Associations Default Artifact:
- File Type - The file type that triggers the associated command to be executed.
- File Path - A path to the program that is run when a file of the specified file type is opened.
- File Name - The name of the program that is run when a file of the specified file type is opened.
- Command - The command that is executed.
- Default - The default command that is executed.
- Registry Key Last Write Date/Time - Registry Key Last Write Date/Time.
For more information or suggestions please contact: asmaa.elkhatib@forensafe.com
