Solving Magnet Virtual Summit - Windows Server CTF Using ArtiFast
12/05/2023 Friday
In this blog post, we will be solving the Magnet Virtual Summit Windows Server CTF created by Magnet Forensics. Below is the solution to the challenge, solved using ArtiFast Suite.
Artifacts Covered in this Challenge:
- Registry Artifacts → System Information,Network Interfaces, Installed Programs, User Accounts and Timezone Information.
- OS Artifacts → Windows Event Logs .
- Web Activity Artifacts → Chrome Web Browser.
Q&As:
1. Maybe you can get the Team to help you Viewer this?
What non-standard email service has the user used previously?
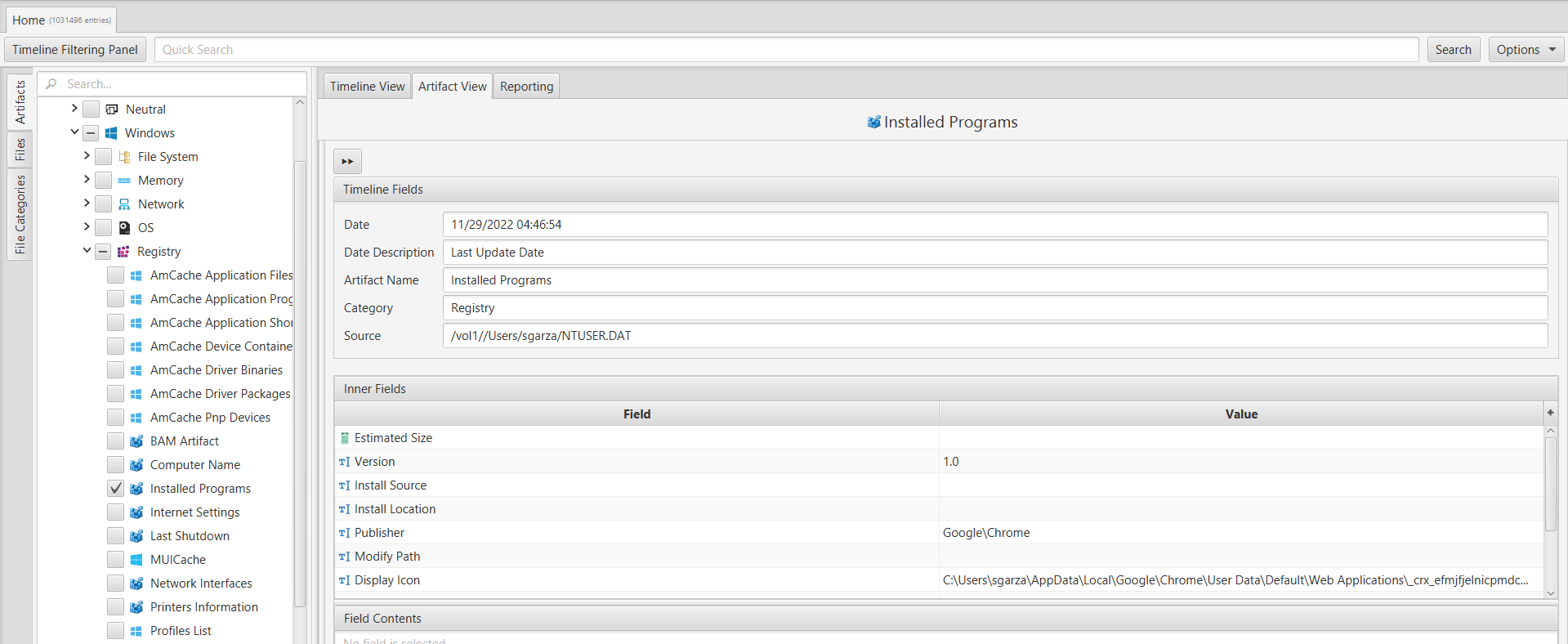
To identify the program installed on the system, we searched for installed programs using ArtiFast's registry artifacts. We specifically looked into the "Installed Programs" artifact under the "Registry" category, and found that the user had installed "Chrome Remote Desktop".
2. Remember to turn back the clocks in November!
What is the system timezone?
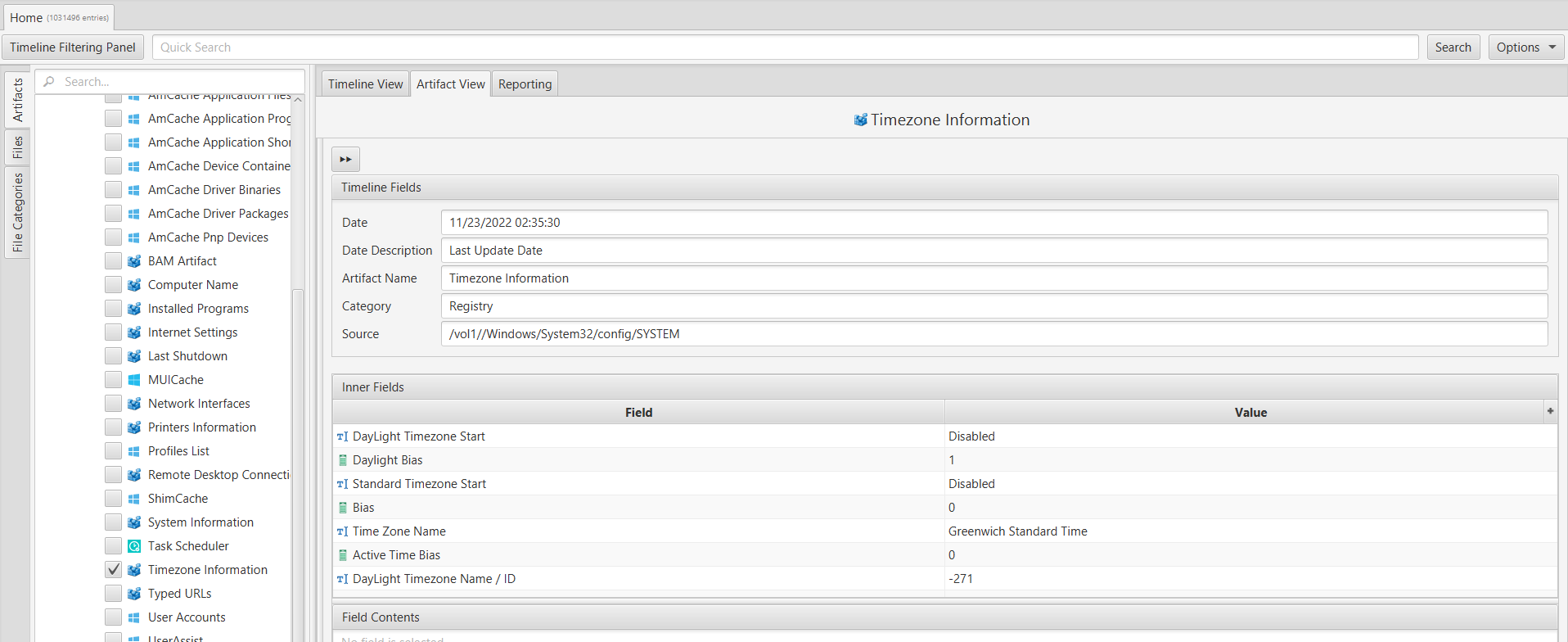
To answer this question, we examined the "Timezone Information" artifact within ArtiFast's "Registry" category. From this artifact, we determined that the time zone recorded on the system is "Greenwich Standard Time."
3. I think I'm going to have a (National) Expresso toDay!
TWhat was the date and time on the system when the user account with a password hint was created? (YYYY-MM-DD HH:MM:SS)
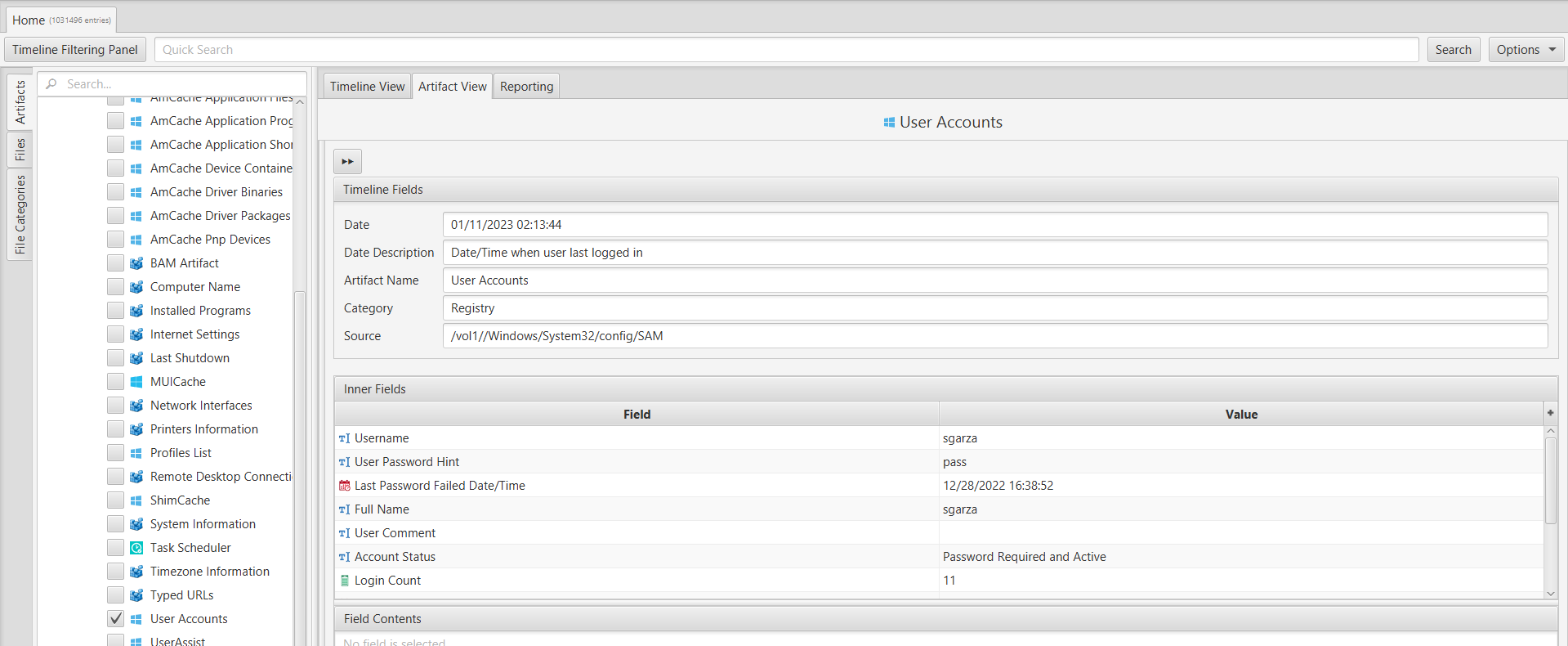
To address this question, we can utilize ArtiFast's "User Accounts" artifact within the "Registry" category.
By examining this artifact, we discovered that the username associated with the account is "Sgarza."
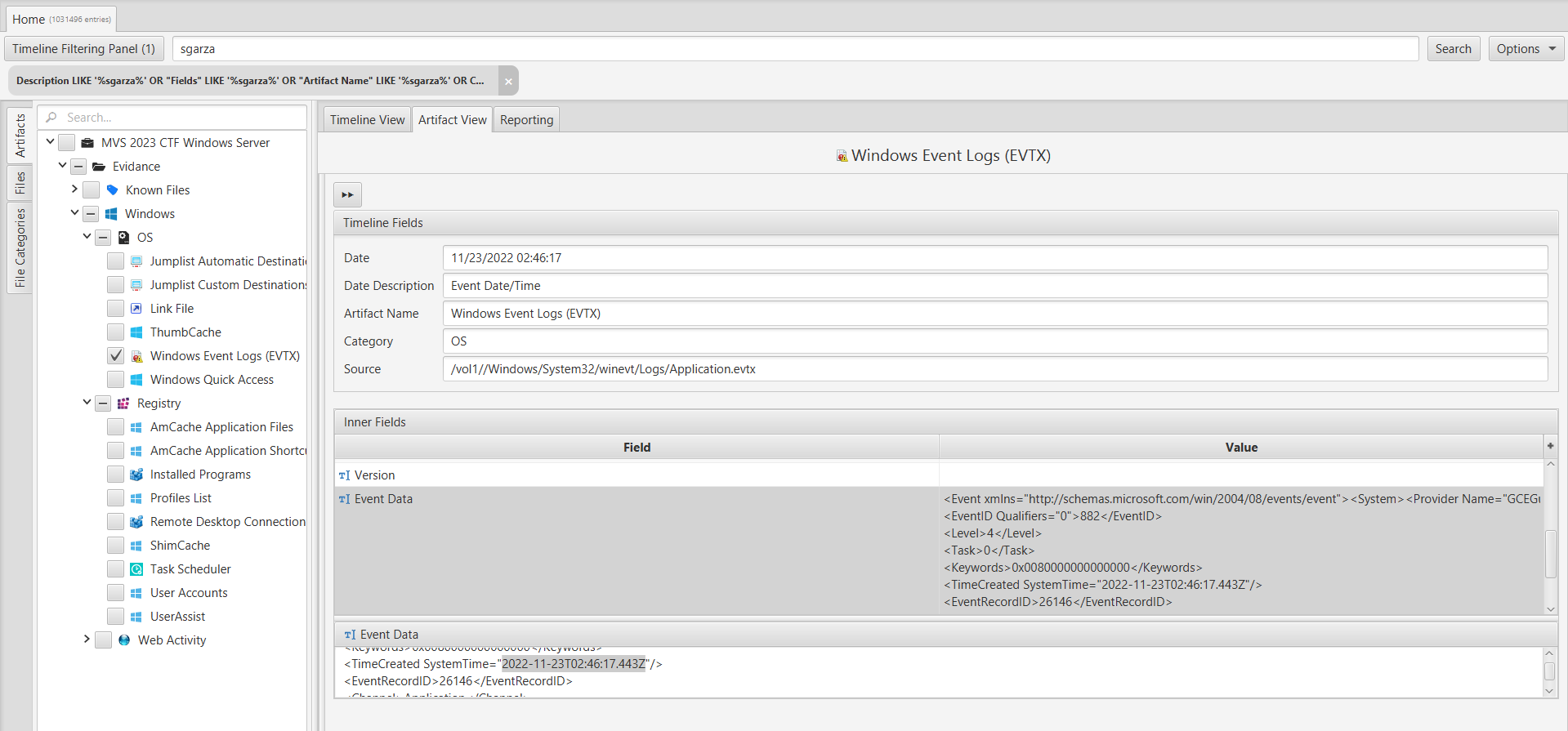
To determine the creation time of this username, we employed ArtiFast's search feature to look for this specific username within the "Windows Event Logs (EVTX)" artifact, located in the "OS" category.
The result is “2022-11-23T02:46:17.443Z".
4. WHAT? I CANT HEAR YOU OVER THE FANS!
What is the operating system edition?
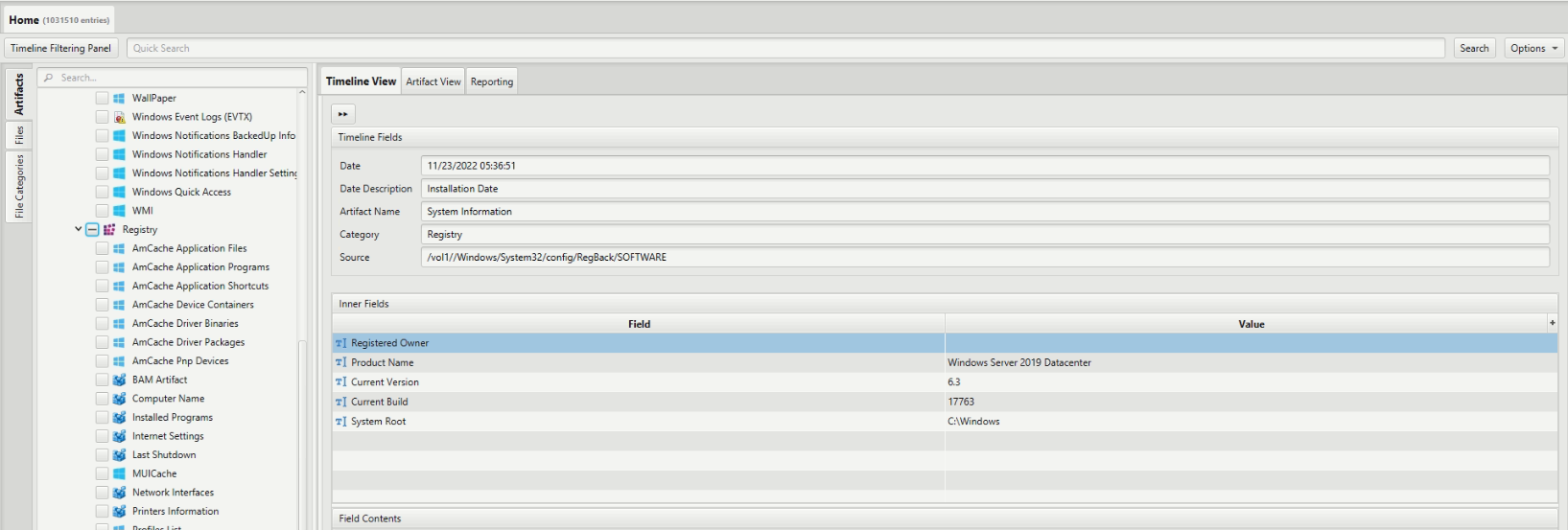
To find this information easily, we can refer to the "System Information" artifact within ArtiFast. By examining this artifact, we can determine that the operating system recorded is Windows Server 2019 Datacenter.
5. Which email did I use for this again?
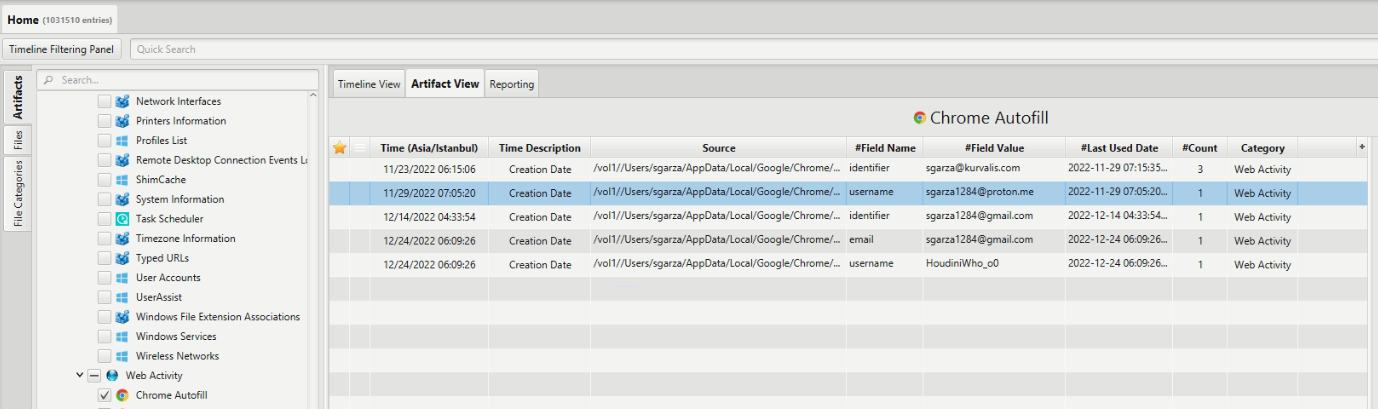
Not including their work account or gmail, what other email address did the primary user of the system have?
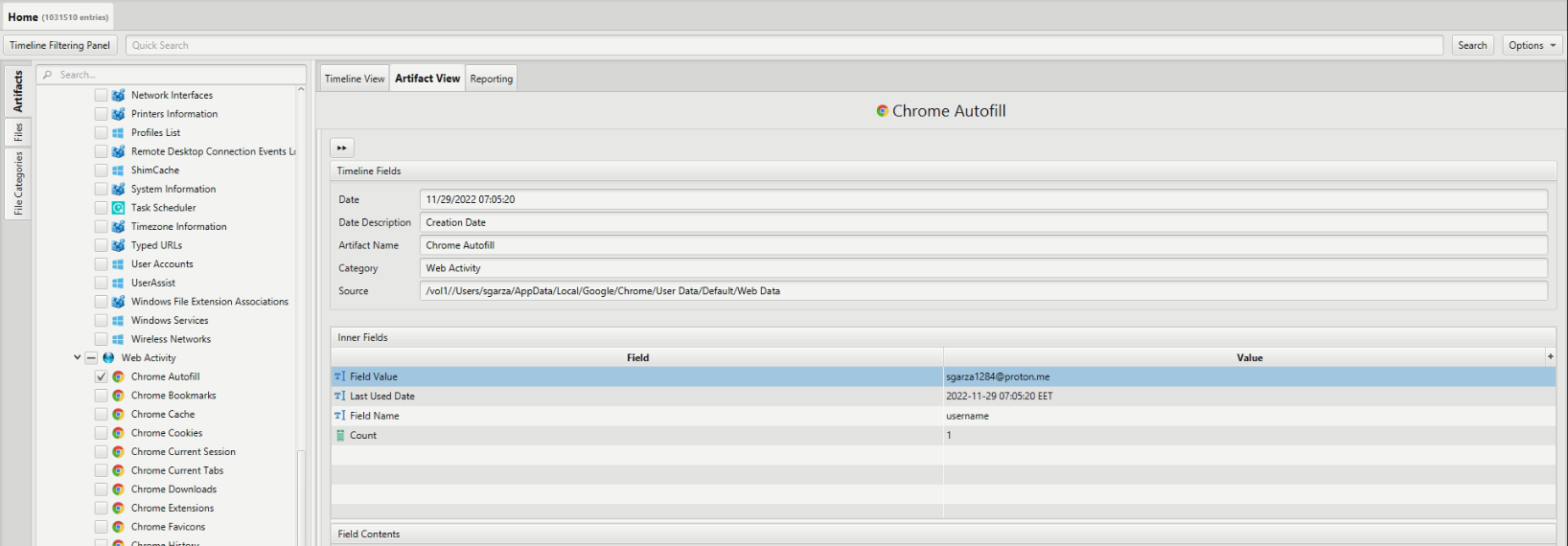
As we are looking for an email we check ArtiFast’s “Chrome Autofill” artifact there we found 3 emails work “sgarza@kurvalis.com” and personal “sgarza1284@gmail.com” and a protonmail email “sgarza1284@proton.me” which is the answer.
6. Can I sync these on my mobile device?
What is the name for the bookmark item added on December 11, 2022 at 2:04:54 AM (local system time)?
To determine the appropriate bookmarks related to the specific date mentioned in the question, we examined ArtiFast's "Chrome Bookmarks" artifact.
From this artifact, we identified two options: "Mobile Bookmarks" and "Other Bookmarks," both of which were added on December 11, 2022, at 2:04:54 AM.
Considering the question's mention of bookmarks being synced from a mobile device, the correct answer would be "Mobile Bookmarks."
7. I lost Control of my Services and broke all the Tcpipconnections. This is the last time I'm going to use random Parameters I don't understand!
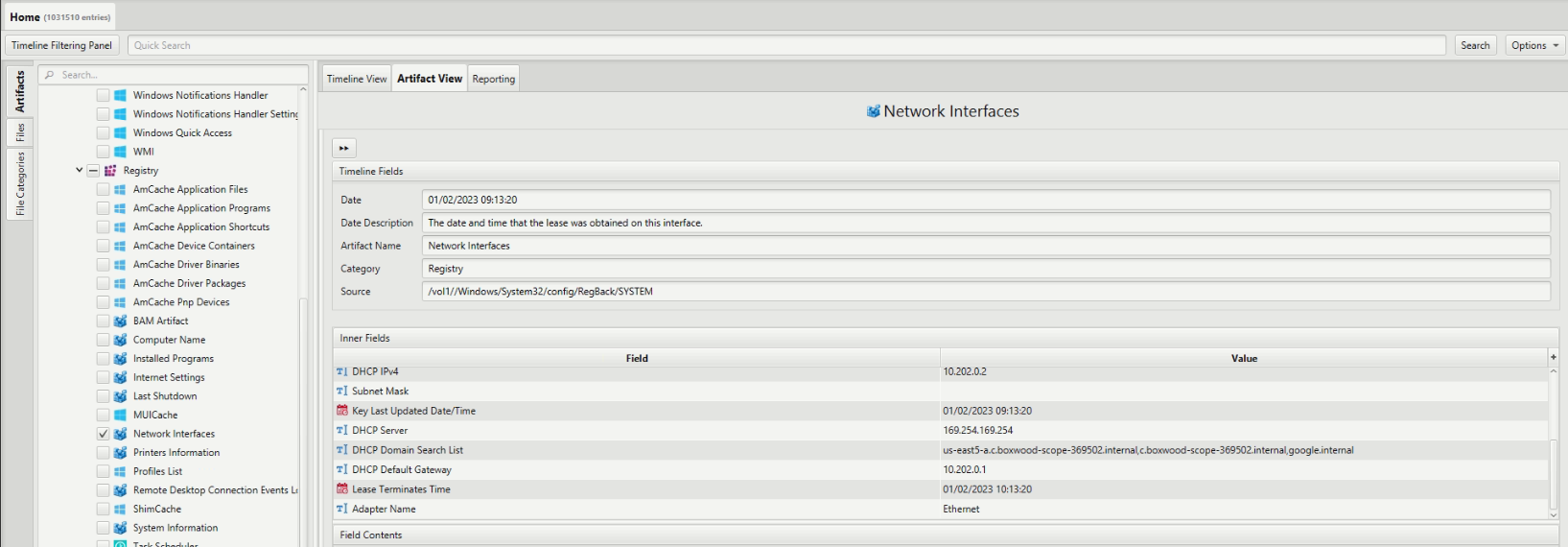
What was the second domain in the search list provided by the DHCP server?
To find the answer, we examined ArtiFast's "Network Interfaces" artifact within the "Registry" category. From this artifact, we discovered that the DHCP search list includes the following domains: "us-east5-a.c.boxwood-scope-369502.internal," "c.boxwood-scope-369502.internal," and "google.internal." Therefore, the answer to the question is "c.boxwood-scope-369502.internal"."
8. i'm tired of Googling about the Cloud - time to learn about PowerShell modules instead.
What is the GUID of the PowerShell module found on the system?
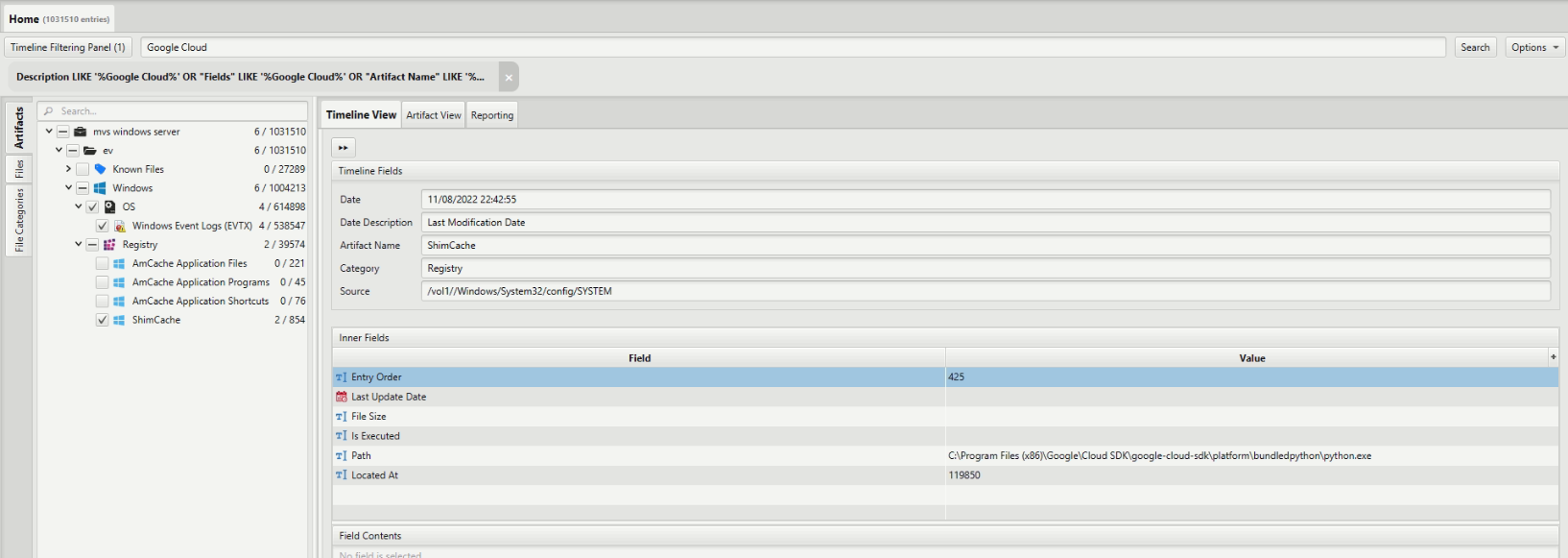
During our search for the term "Google Cloud" we came across a reference to the Google Cloud SDK in the "ShimCache" artifact. The program's base path was identified as "C:\Program Files (x86)\Google\Cloud SDK."
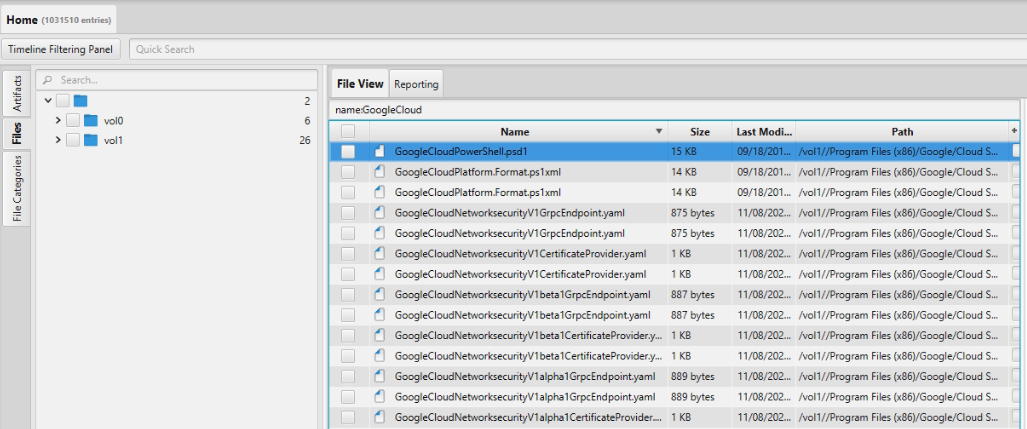
To dive deeper, we utilized ArtiFast's built-in file system viewer to navigate through the specified path.Our objective was to locate the term "GoogleCloud."
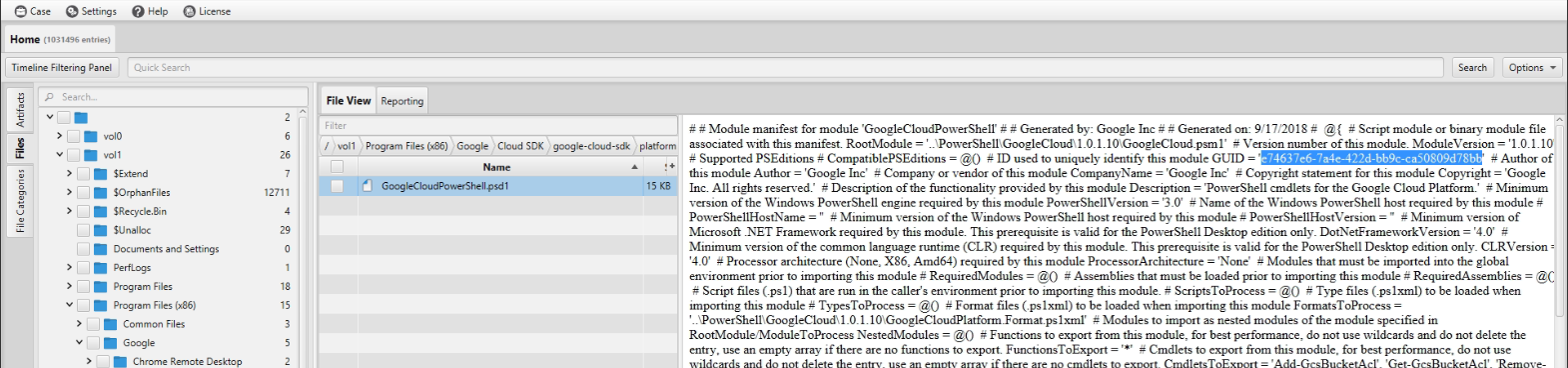
Eventually, we discovered a PSD1 file named "GoogleCloudPowerShell" in the following location: C:\Program Files (x86)\Google\Cloud SDK\google-cloud-sdk\platform\GoogleCloudPowerShell\GoogleCloud.psd1
Furthermore, with the assistance of ArtiFast's file viewer, we were able to identify a GUID associated with the file: e74637e6-7a4e-422d-bb9c-ca50809d78bb.
×
For more information or suggestions please contact: amro.alshadfan@forensafe.com
