Solving Magnet Virtual Summit - Windows 11 CTF Using ArtiFast
12/05/2023 Friday
In this blog post, we will be solving the Magnet Virtual Summit Windows 11 CTF created by Magnet Forensics. Below is the solution to the challenge, solved using ArtiFast Suite.
Artifacts Covered in this Challenge:
- Registry Artifacts → System Information, Installed Programs, User Accounts and Remote Desktop Connection Events Log.
- OS Artifacts → PowerShell, Windows Event Log and Prefetch.
- Web Activity Artifacts → Chrome Web Browser.
Q&As:
1. Gmail? Outlook? Yeah, right.
What non-standard email service has the user used previously?
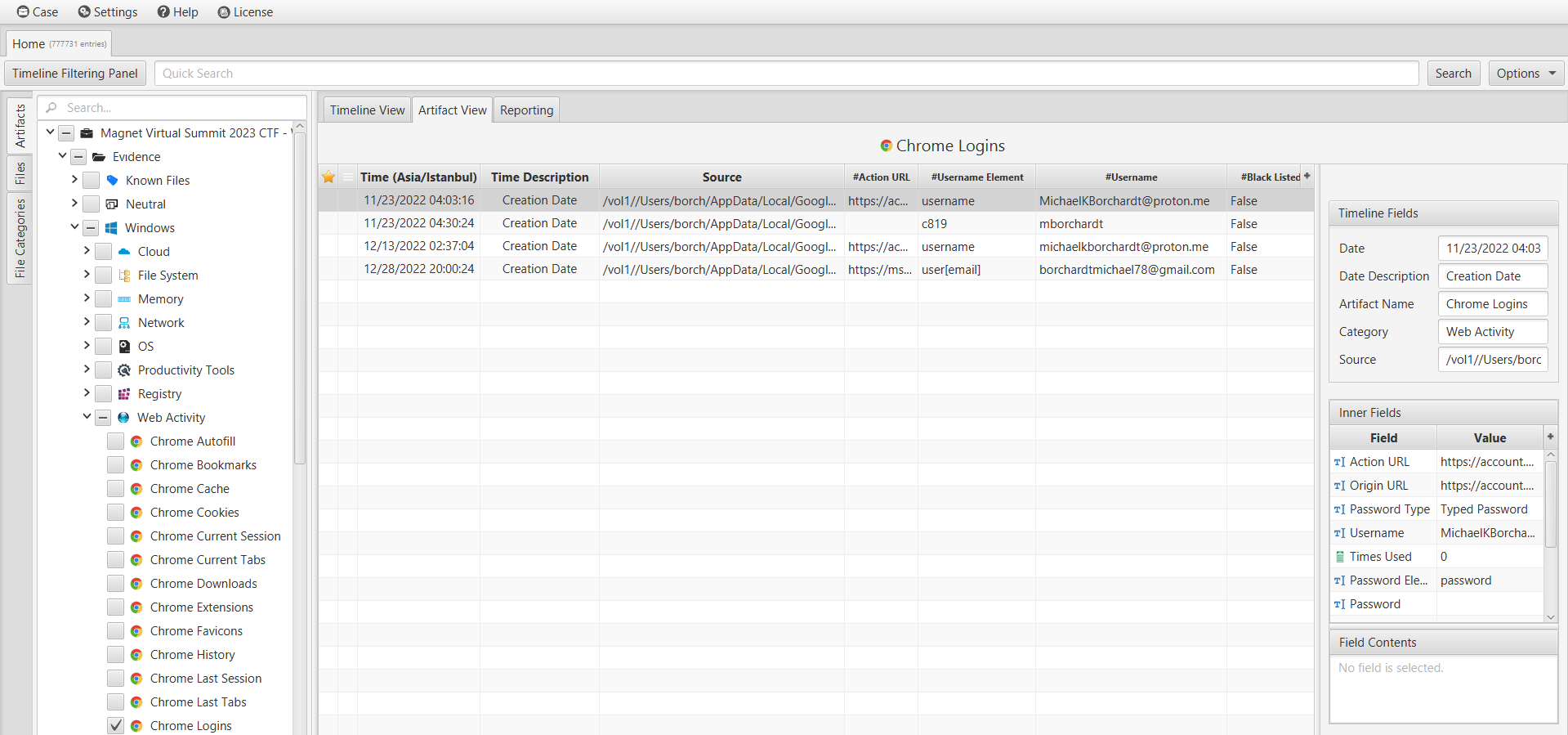
We are searching for an unconventional email service that the user utilized, excluding mainstream providers like Gmail, Hotmail, and Yahoo. To investigate, we examined the user's web activity using ArtiFast's "Web Activity" category. By analyzing the "Chrome Logins" artifact, we discovered that the user employed the proton.me (ProtonMail) service for their emails. MichaelKBorchardt@proton.me is the answer
2. Two different versions, twice the emulation power! Makes sense to me!
The user installed and ran a mobile device emulation program on their system. Which 2 versions of this software did the user install? (Format: SoftwareName V1/V2)
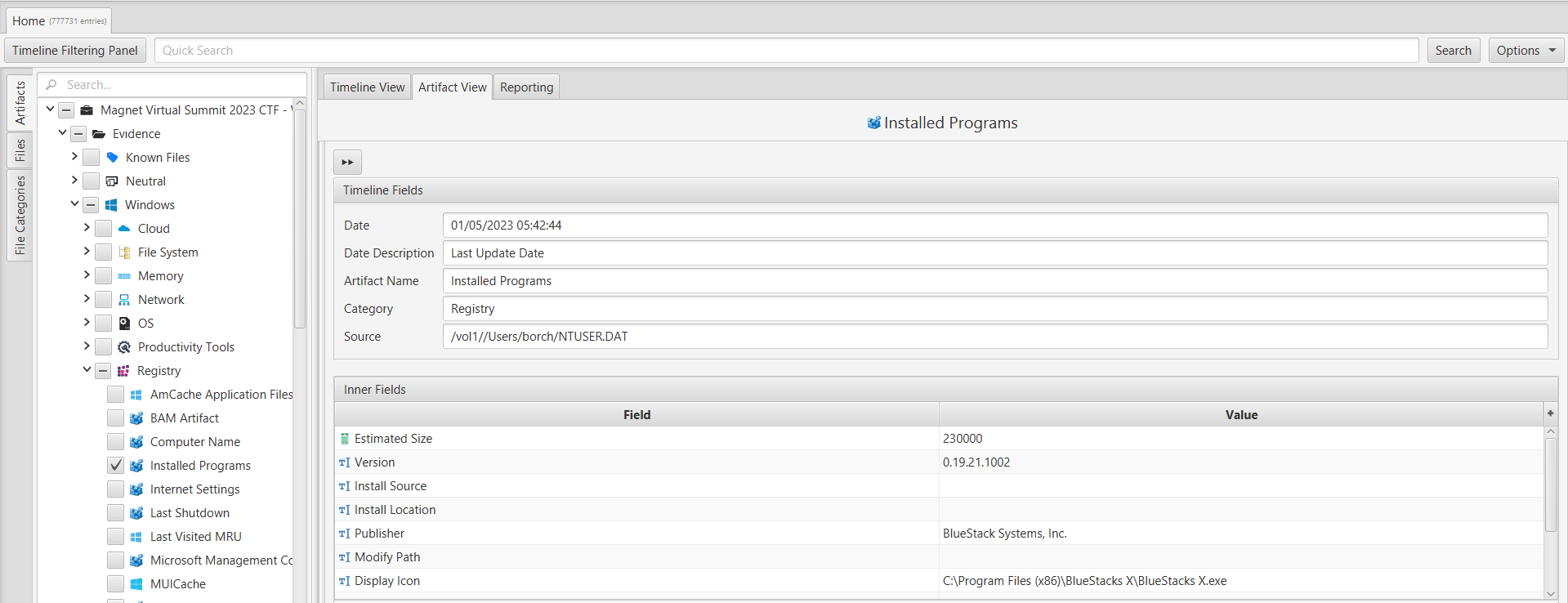
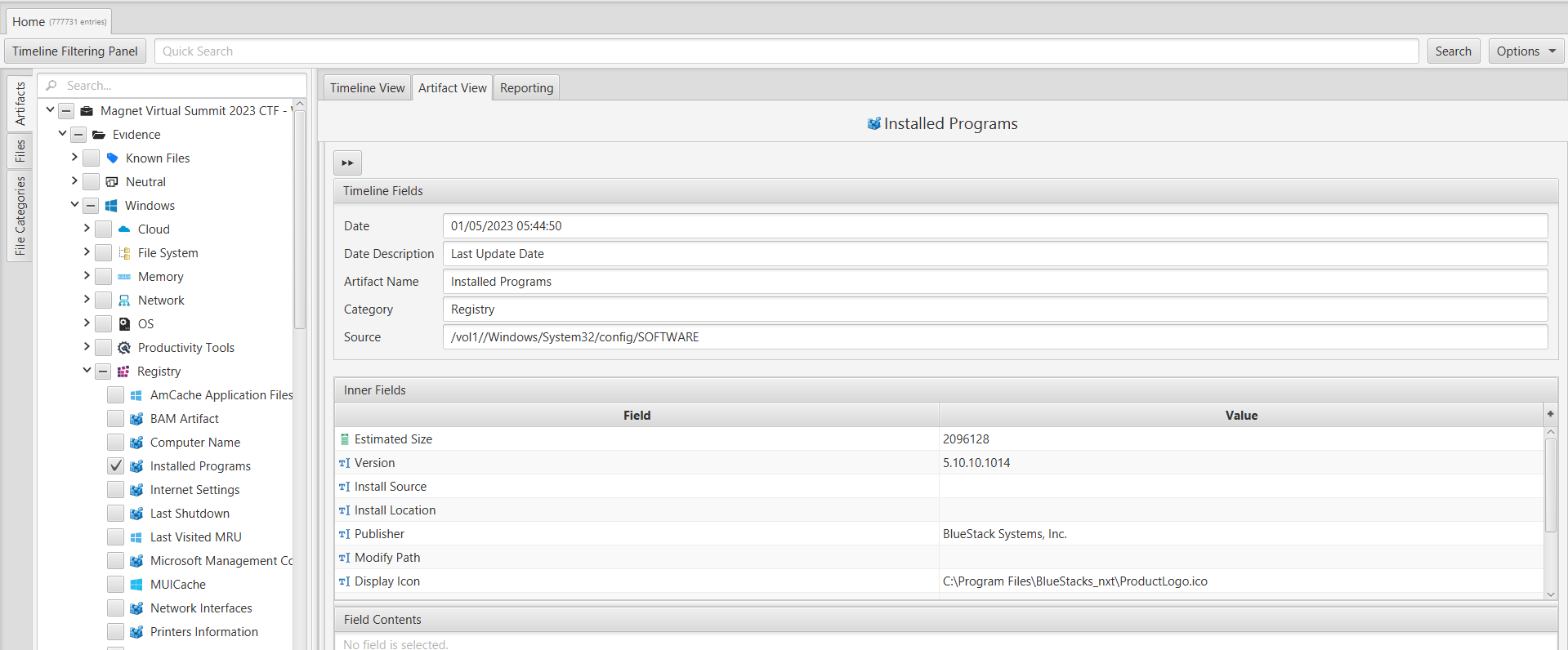
In order to identify a program that was installed on the system, we examined the registry artifacts since typically installed programs are stored there. Using ArtiFast, we explored the "Registry" category and specifically investigated the "Installed Programs" artifact. Our analysis revealed that the user had installed BlueStacks5 and BlueStacks X.
3. LITEning fast write speeds!
The user's system is equipped with a 256GB NVMe SSD. What is the make and model of this drive?
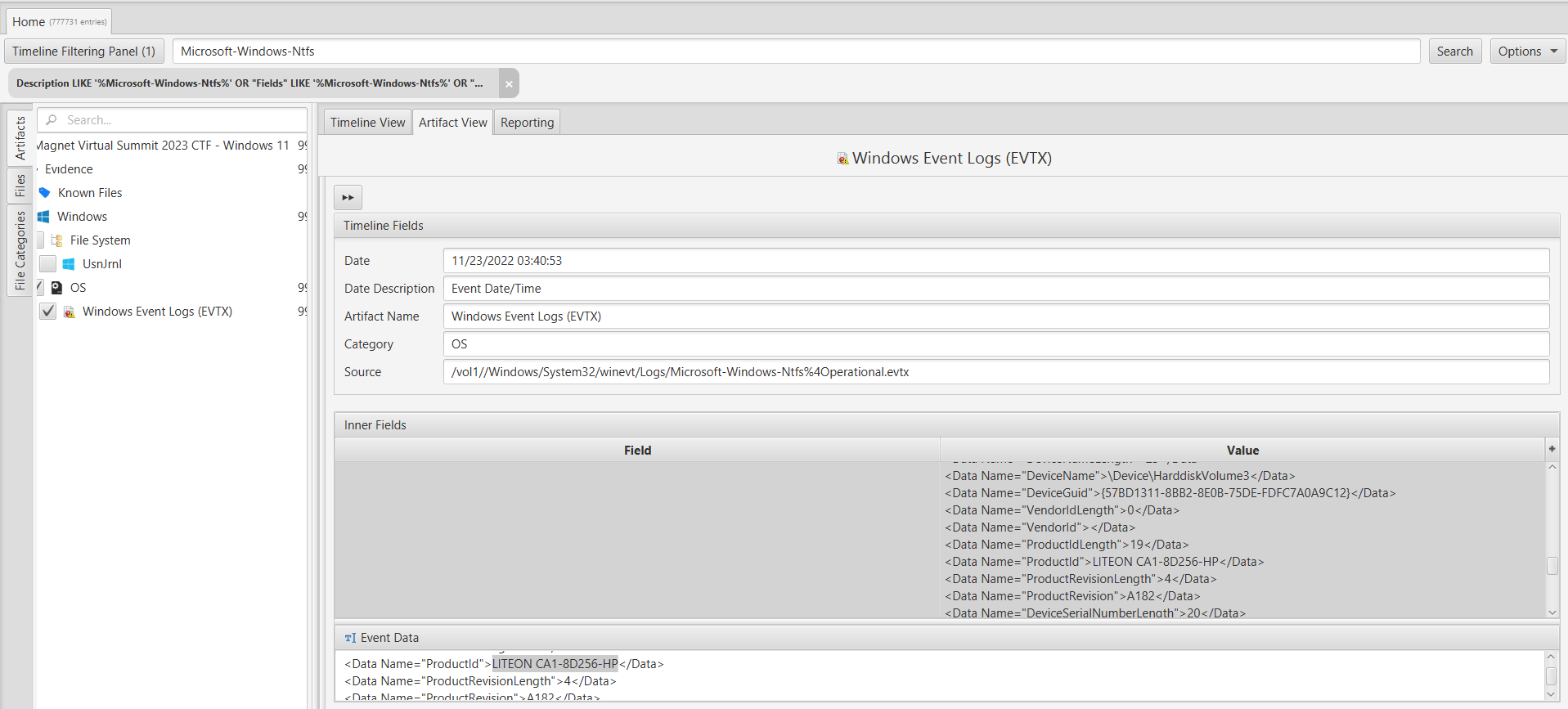
To address this question, we relied on the "Windows Event Logs" artifact within the "OS" category. By utilizing our filter, we searched for the results specifically within the "Microsoft-Windows-Ntfs%4Operational.evtx" log. Within this log, we examined the "LITEON CA1-8D256-HP" entry, which provided us with the model number "LITEON CA1-8D256-HP."
4. Really...? Plaintext...?
The user frequently accesses a Chrome Remote Desktop virtual machine. What password is used to log into this VM?
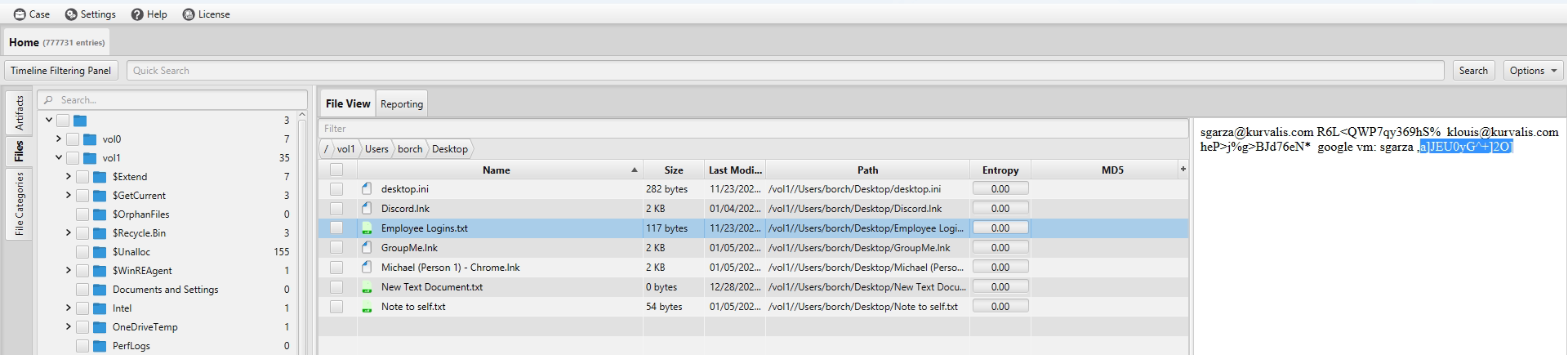
To address this question, we utilized ArtiFast's built-in filesystem viewer to navigate through the filesystem. During this exploration, we discovered a text file named "Employee Logins.txt" located on the desktop of the user named "borch." By using ArtiFast's built-in file viewer, we examined the contents of this file and found the password to be ",a]JEU0yG^+]2O]". It is worth noting that the user has a pattern of saving their credentials in pairs, separated as seen in the first two lines of the file. We selected this password specifically because it corresponds to a Google virtual machine (VM).
5. Why was 6 afraid of 7? Because 7 can unarchive virtual drives!
Within the past 2 years, a popular unarchiving program gained the ability to unarchive VHDX virtual disk images. What version of the program was this upgrade implemented?
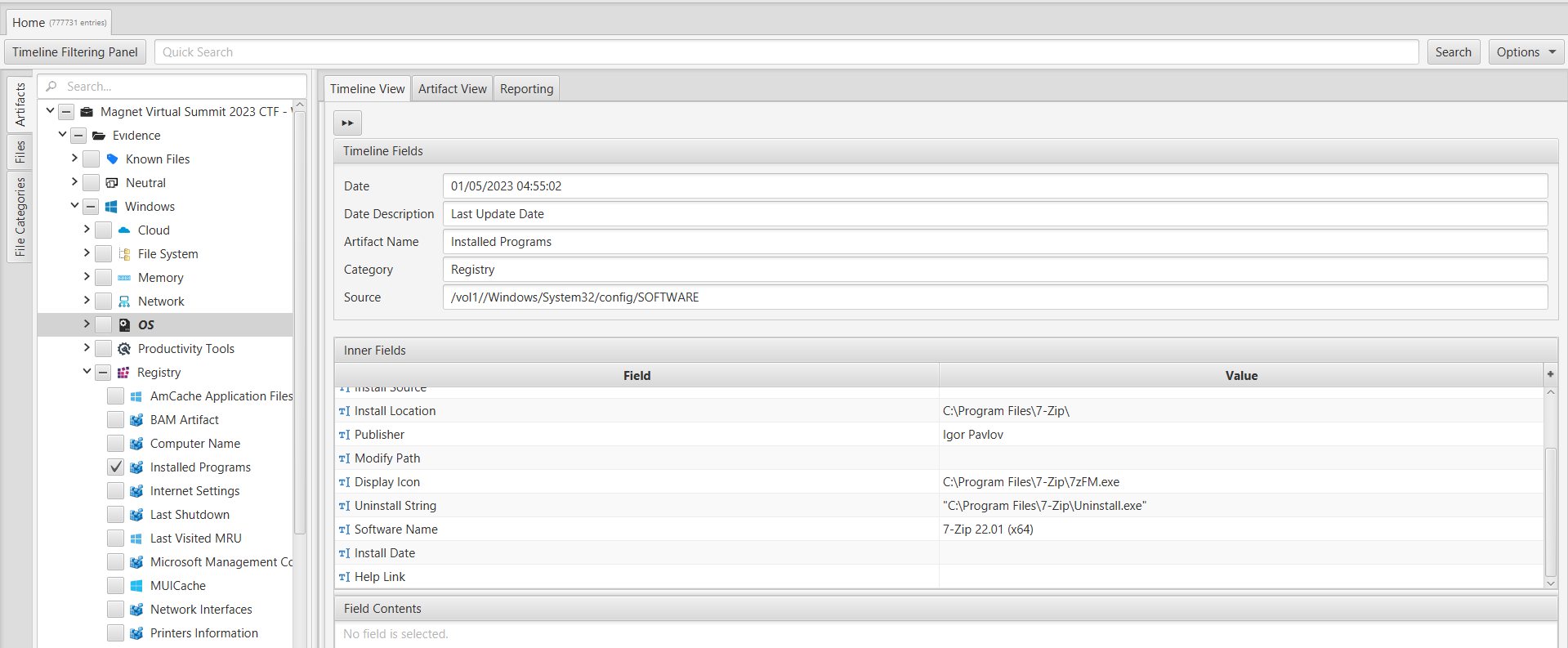
Returning to the "Installed Programs" artifact within ArtiFast's "Registry" category, we discovered that the sole unarchiving program installed on the system is 7-Zip V22.01. Further research conducted on the internet confirms that 7-Zip introduced VHDX support in version 21.07.
6. We're not in Kansas anymore...
The user has established an RDP connection to one destination more than any other. What is the Geolocation of this destination? (Format: City, ST)
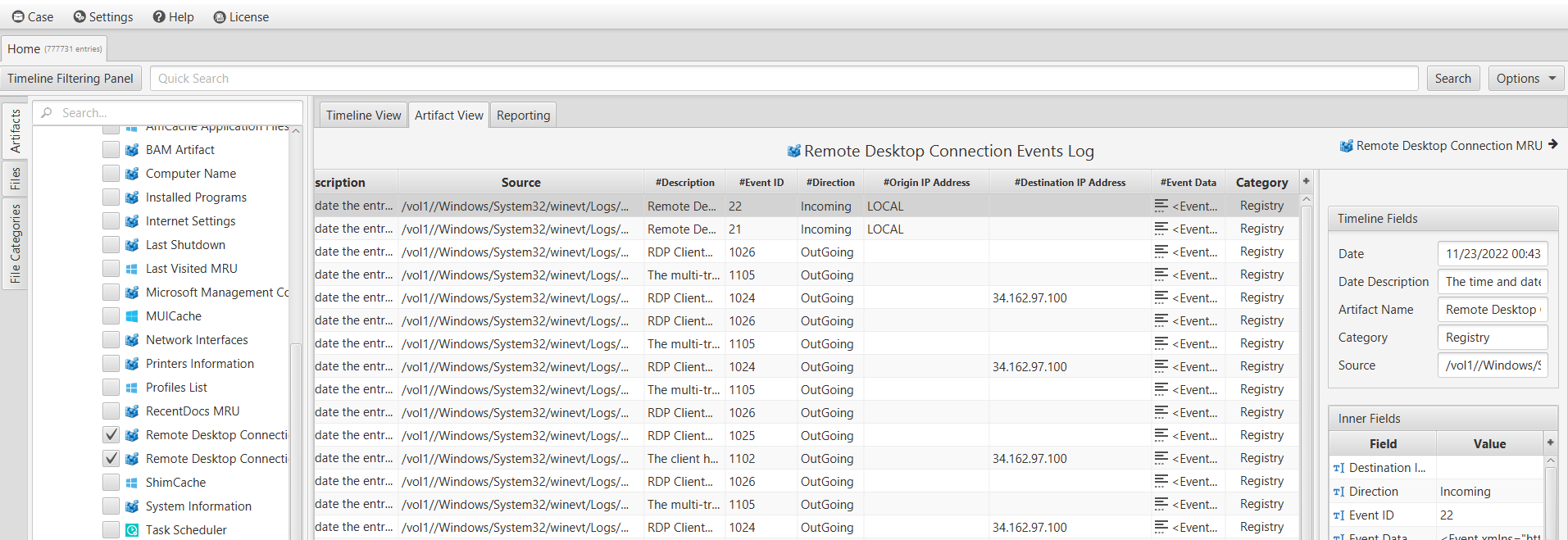
By examining ArtiFast's "Remote Desktop Connection Events Log" artifact within the "Registry" category, we were able to identify RDP connection events performed by the user, along with their event details. Among these events, the most frequently accessed destination IP address was 34.162.97.100. By conducting a geolocation lookup on this IP address using one of the IP geolocation websites, we determined that it corresponds to Columbus, Ohio.

7. Make sure to keep some tabs on that System Admin from Southern California
The user visited the Mastodon page of one user more than any others on the platform. What is the full legal name of the user Michael visited?
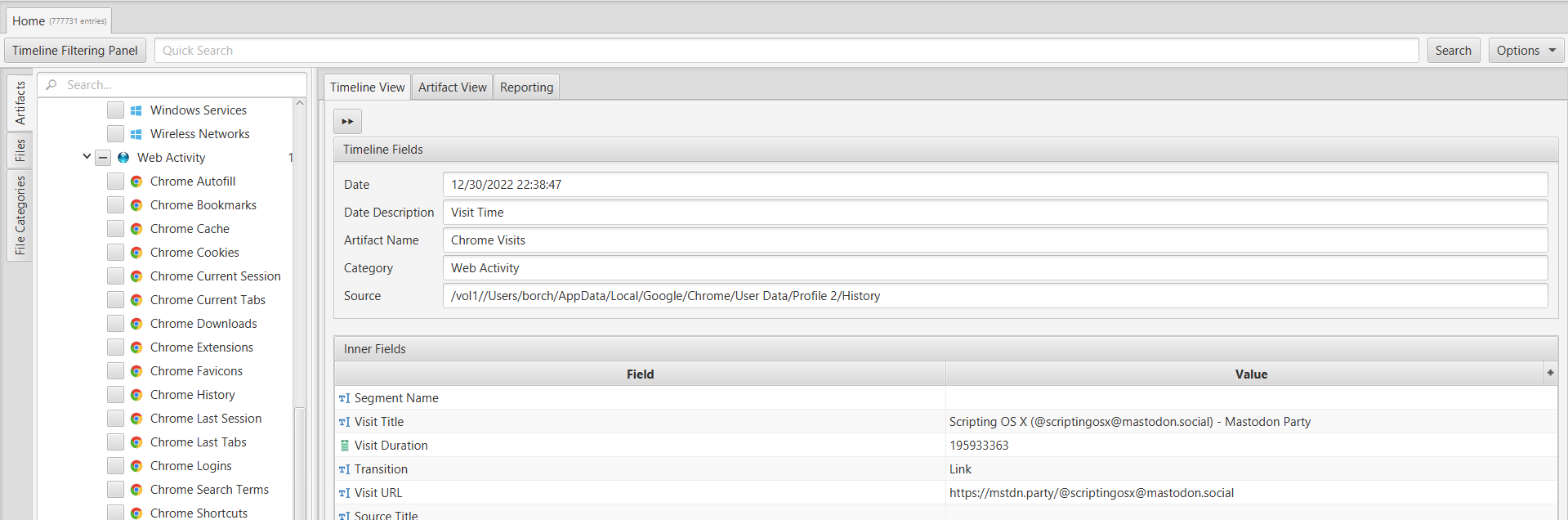
In order to address this question, we utilized ArtiFast's search feature to look for the keyword "Mastodon" and examined the results. By analyzing the "Chrome Visits" artifact within the "Web Activity" category, we discovered that the user frequently visited a profile named "scriptingosx@mastodon.social". By visiting the associated website URL, we were able to determine that the name of the user is Armin Briegel.
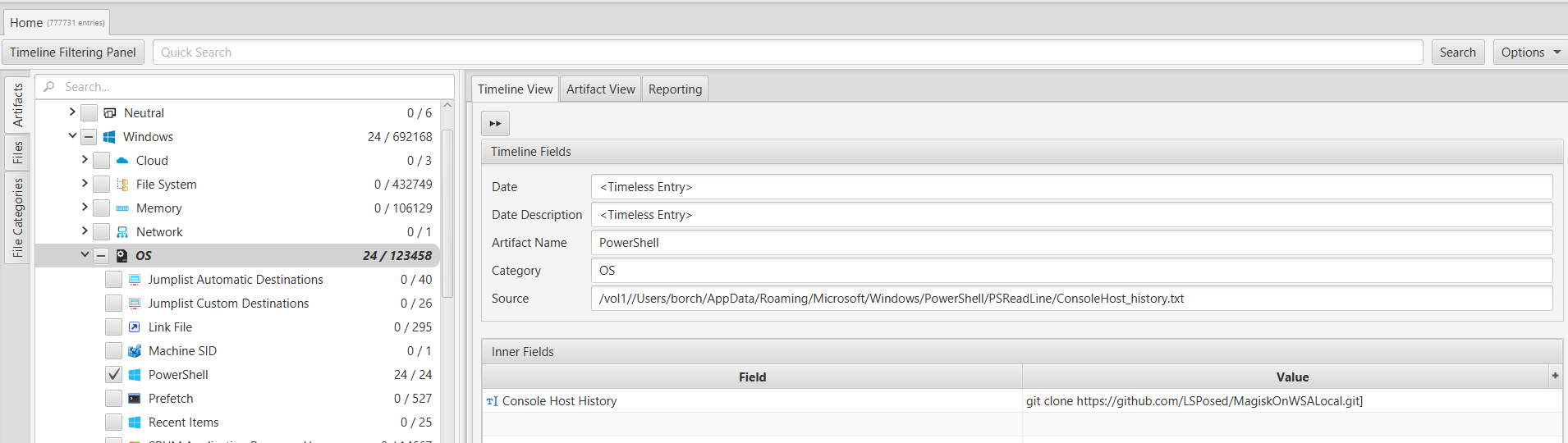
8. We have a History of attracting some sizeable donors with our projects
Michael used PowerShell to clone a particular GitHub utility. What is the account name of one of this repo's most prominent sponsors?
To find the GitHub repository that was accessed using PowerShell, we examined the PowerShell history using ArtiFast's "PowerShell" artifact within the "OS" category. From the artifact, we observed that a git command was executed for the repository at https://github.com/LSPosed/MagiskOnWSALocal. By visiting this GitHub repository, we discovered that the prominent sponsor associated with it is "yujincheng08".
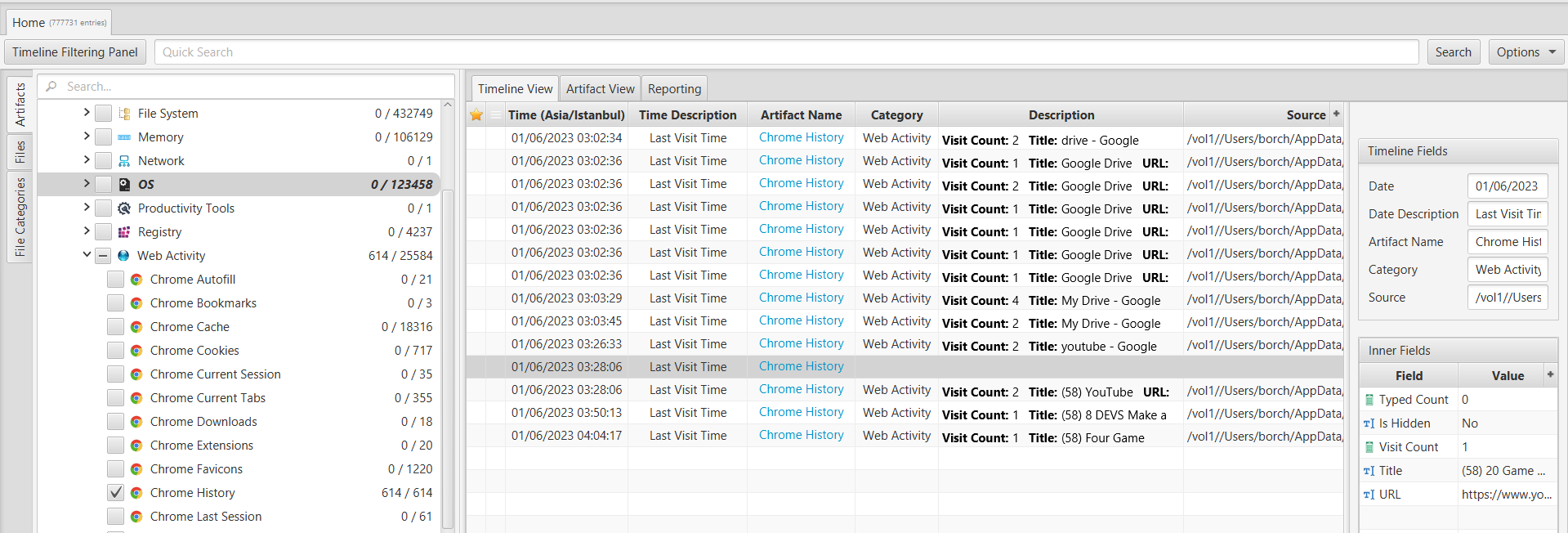
9. Scratch that Itch.io
The user viewed a YouTube video by the creator BenBonk surrounding video game developers. Within this video, how many developers were involved with the project?
To locate a specific YouTube video, we utilized ArtiFast's search feature to simplify our task. Among the search results, we found a few YouTube links within the "Chrome History" artifact. After visiting each of the links, we discovered that one of them was a video by BenBonk titled "20 Game Developers Made This Game." Therefore, the answer to the question is 20.
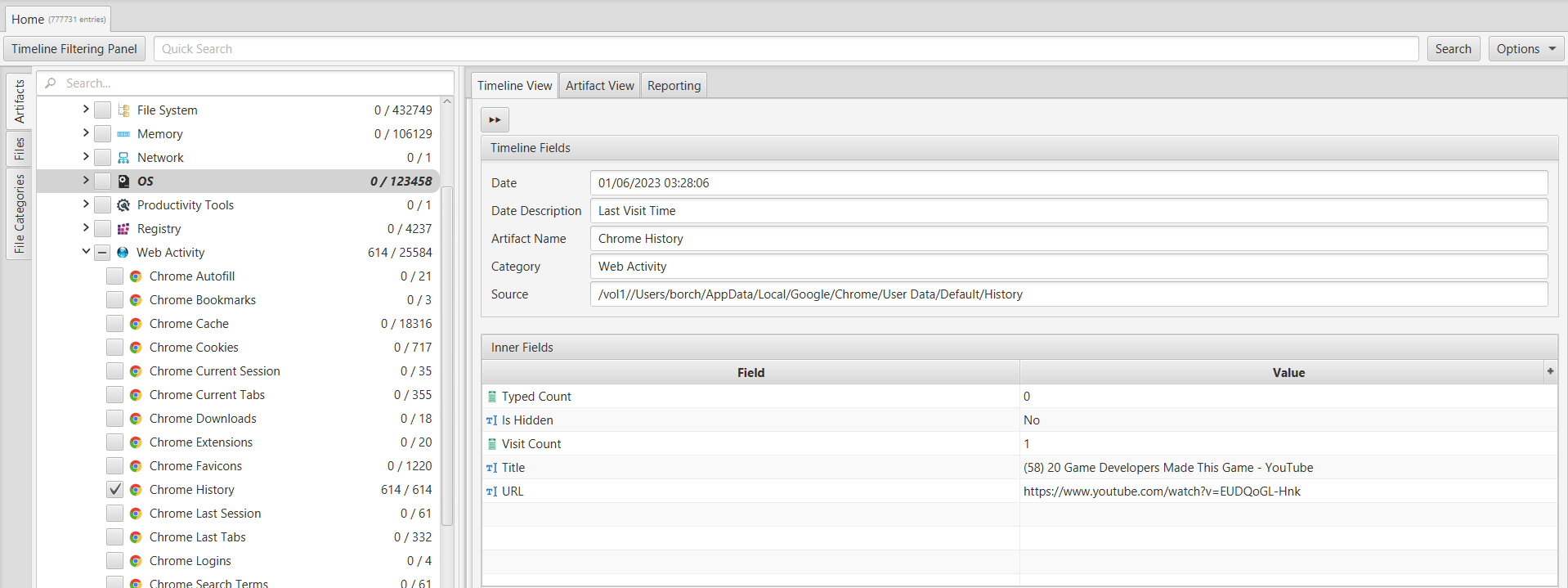
10. The breakfast bell is ringing.
The user has been doing some research lately on fast food items. What is, according to some experts, the unhealthiest food item of the bunch?
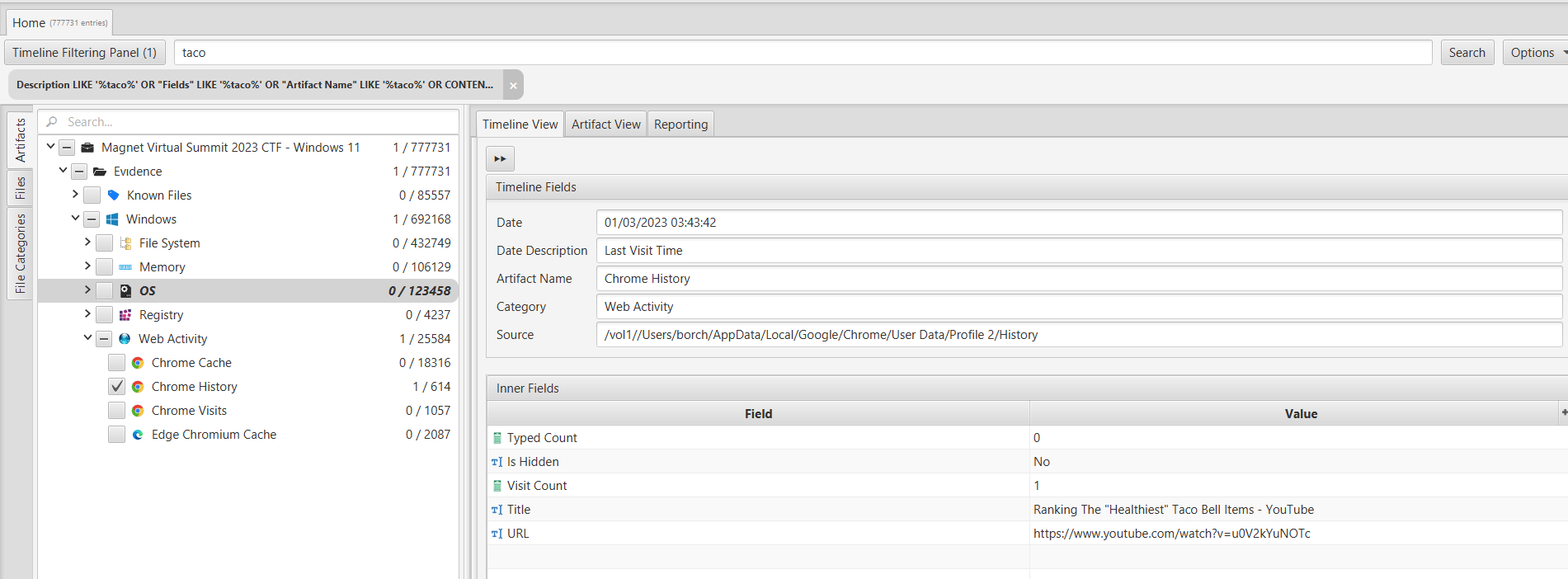
To search for search history, we relied on the "Chrome History" artifact. Considering the mention of a "bell" and the context of a fast food item, we focused on Taco Bell as a potential fast food chain. Utilizing ArtiFast's keyword search feature, we discovered that the user had opened a YouTube video titled "Ranking The 'Healthiest' Taco Bell Items." According to this video, the unhealthiest food item among the options discussed is the "breakfast crunchwrap sausage supreme."
11. Oh Deer...I think we're lost
Michael lives just a mile south of a beautiful body of water. What is the name of this body of water?
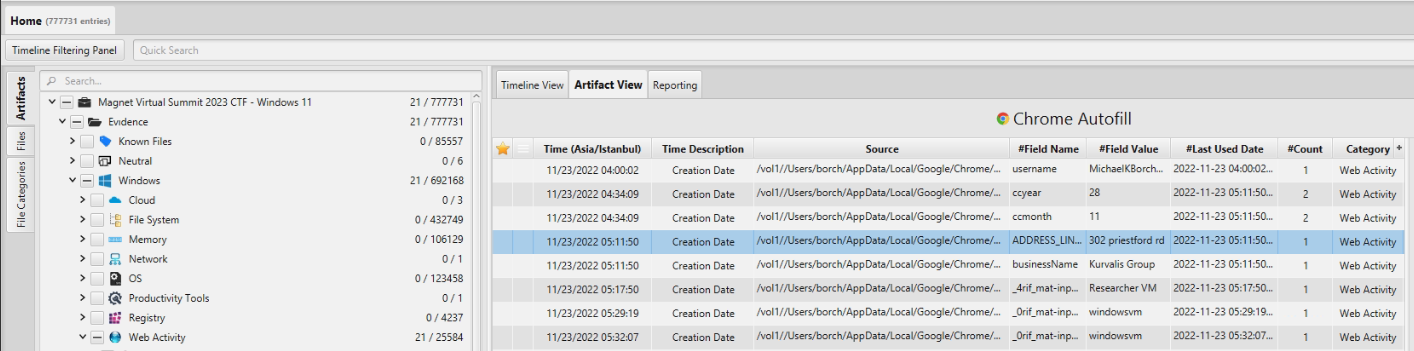
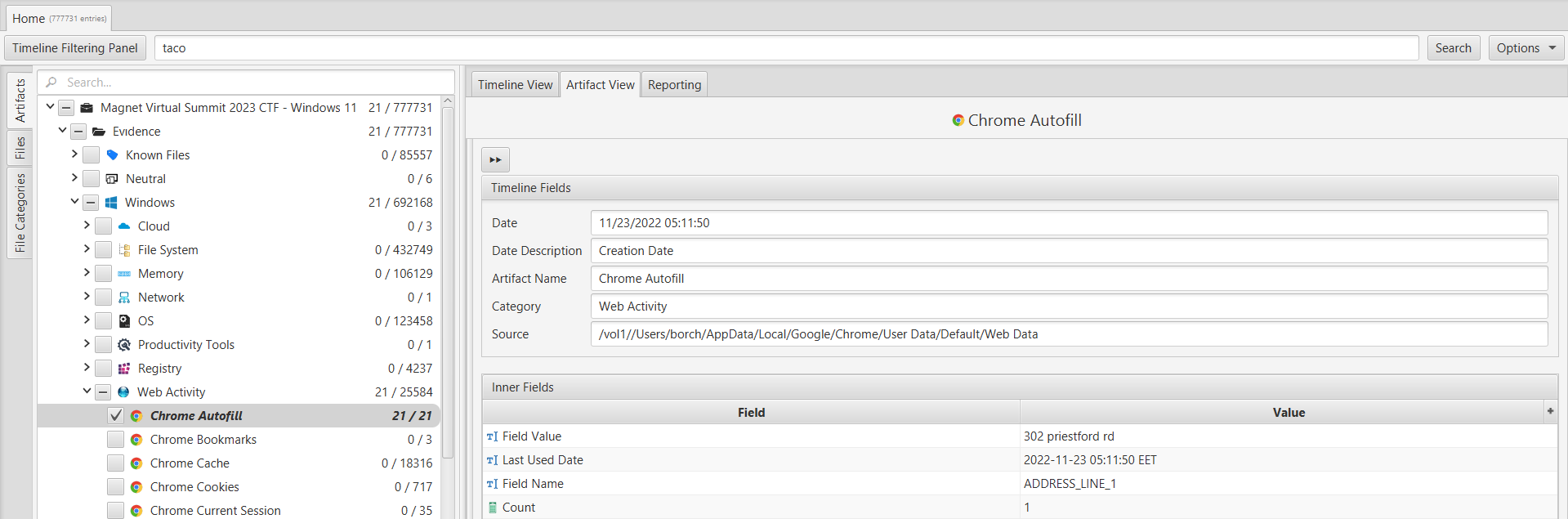
To address this question, we examined the user's address by exploring the autofill data in the Chrome browser using ArtiFast's "Chrome Autofill" artifact. From this artifact, we discovered an address saved in the Chrome autofill as "302 Priestford Rd." By searching for this address on a map, we found that it is located on the same street as a body of water called "Deer Creek."
12. Gotta Git going fast with some Accelerated emulation!
In order to emulate an Android device, the user required some specialized management tools. What Android port is used by default with these services?
Upon revisiting the "Installed Programs" artifact within ArtiFast, we identified a program named "WSA PaCMan." This program serves as a management tool for Android devices on Windows. Notably, the default port used by WSA PaCMan is 58526.
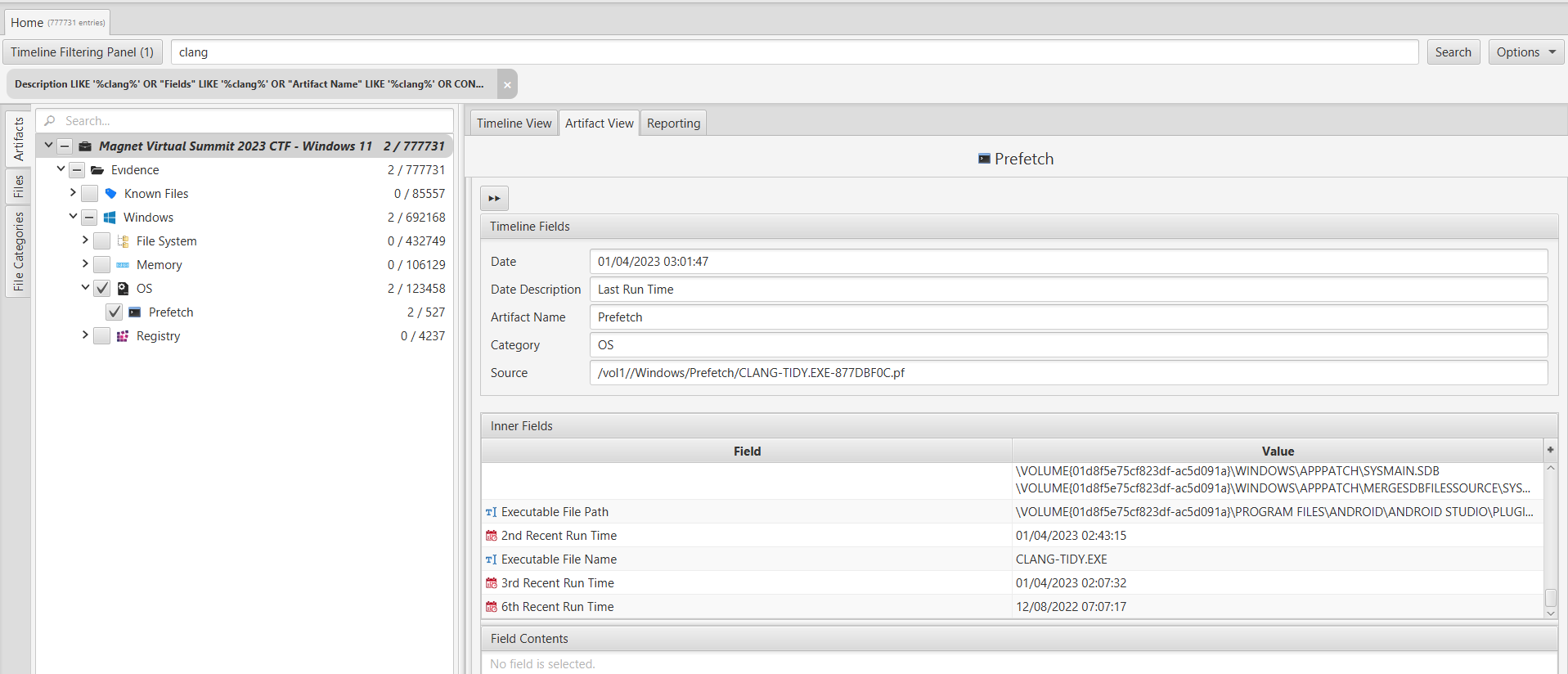
13. PCA - Program Clang Assistant?
Michael lives just a mile south of a beautiful body of water. What is the name of this body of water?
To address this question, we utilized ArtiFast's search feature to search for the term "clang." The search results revealed the presence of an Android Studio plugin called "Clang." In further investigation related to PCA (Program Compatibility Assistant), we discovered a file named "%systempartition%\Windows\appcompat\pca\PcaGeneralDb0.txt." Within this file, we found that the exit code for "Clang" is listed as "0xc0000135”.

×
For more information or suggestions please contact: amro.alshadfan@forensafe.com
