Injector Challenge Using the Full Version of ArtiFast Windows
15/07/2021 Thursday
In this blog post, we will be solving another challenge designed by Cyber Defenders using the full version of ArtiFast Windows. In this case, an attacker has compromised an organization’s web server through their website. The purpose of this challenge is to analyze the image provided and specify how the breach occurred and to identify the actions/commands performed by the attacker (scenario). Below is the solution to the challenge, solved using ArtiFast.
OS Information
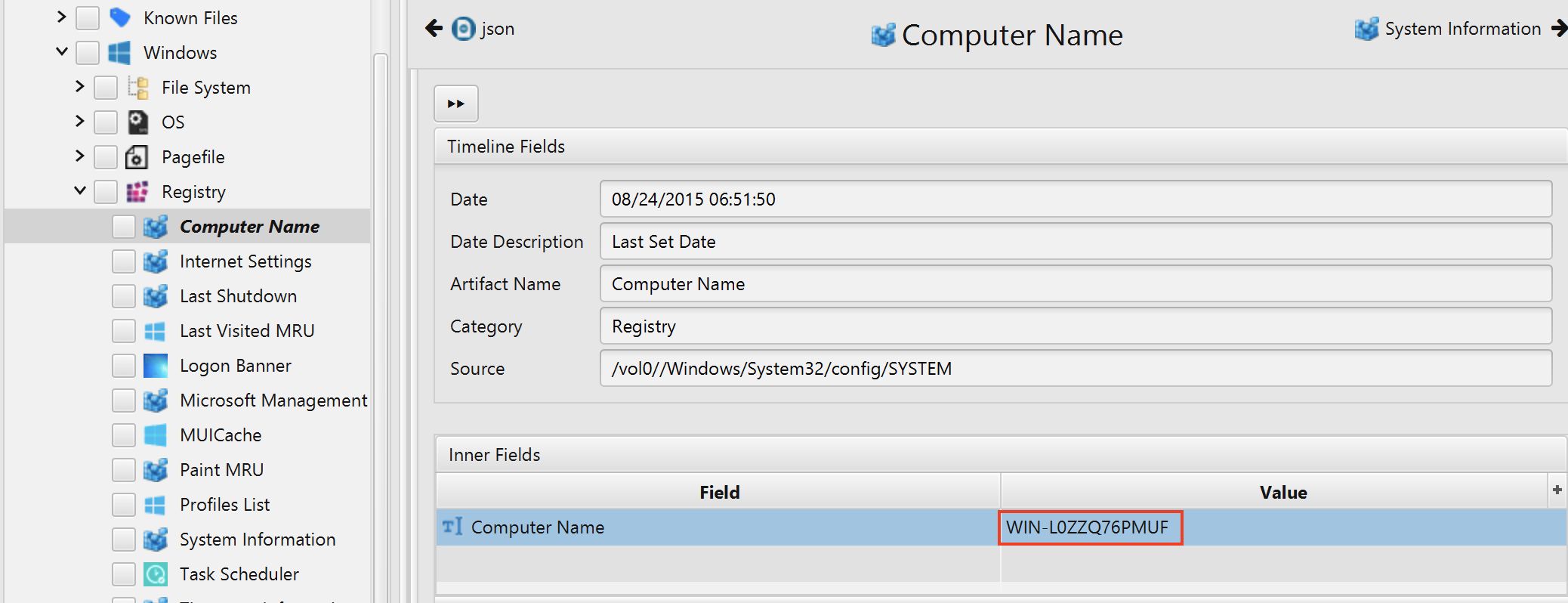
1. What is the computer's name?
The answer can be found in Computer Name artifact under the Registry category. The computer name is WIN-L0ZZQ76PMUF
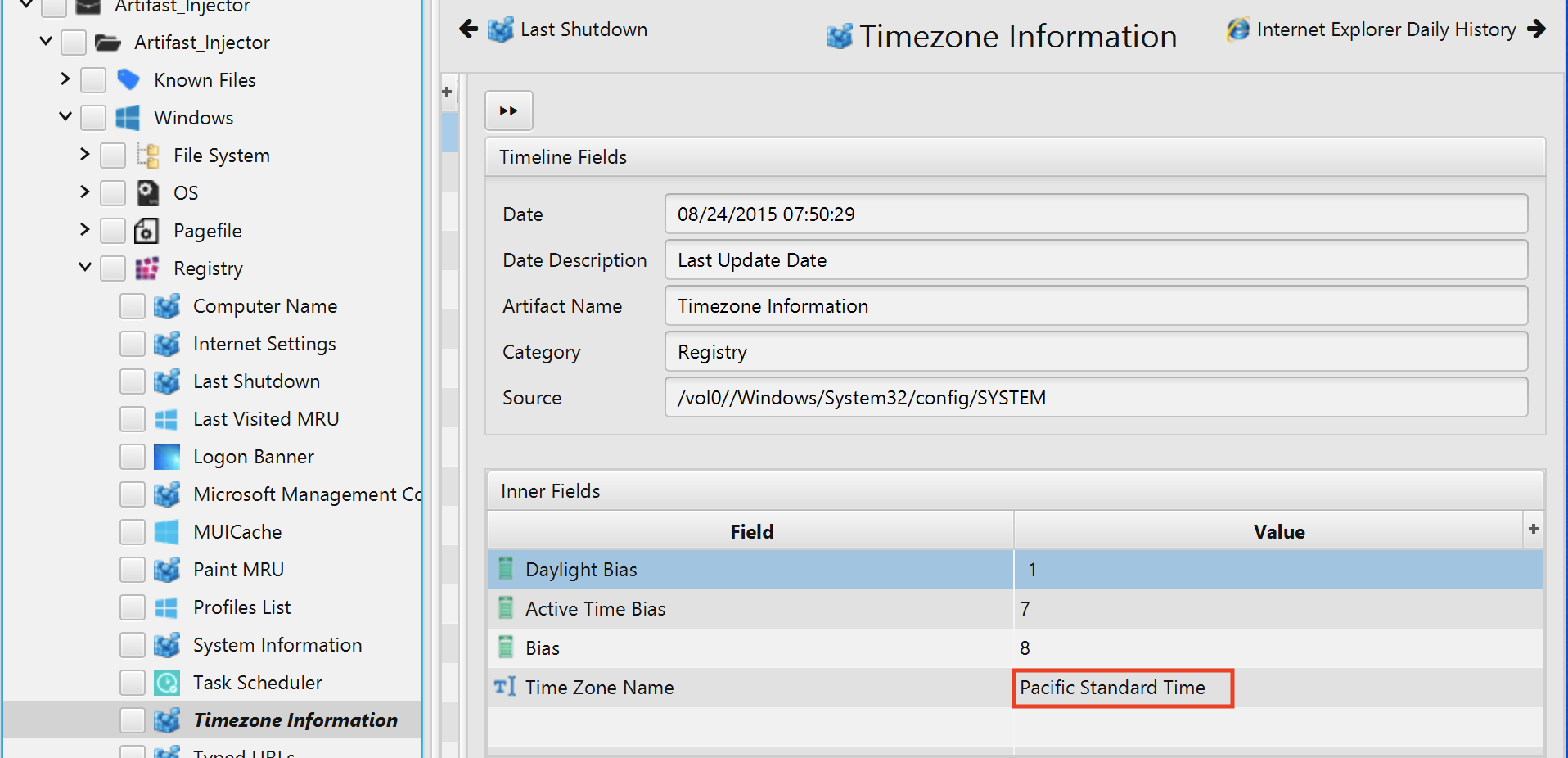
2. What is the Timezone of the compromised machine? UTC+0 (no-space)
The answer can be found in Timezone Information artifact under the Registry category. The computer timezone is UTC-7.
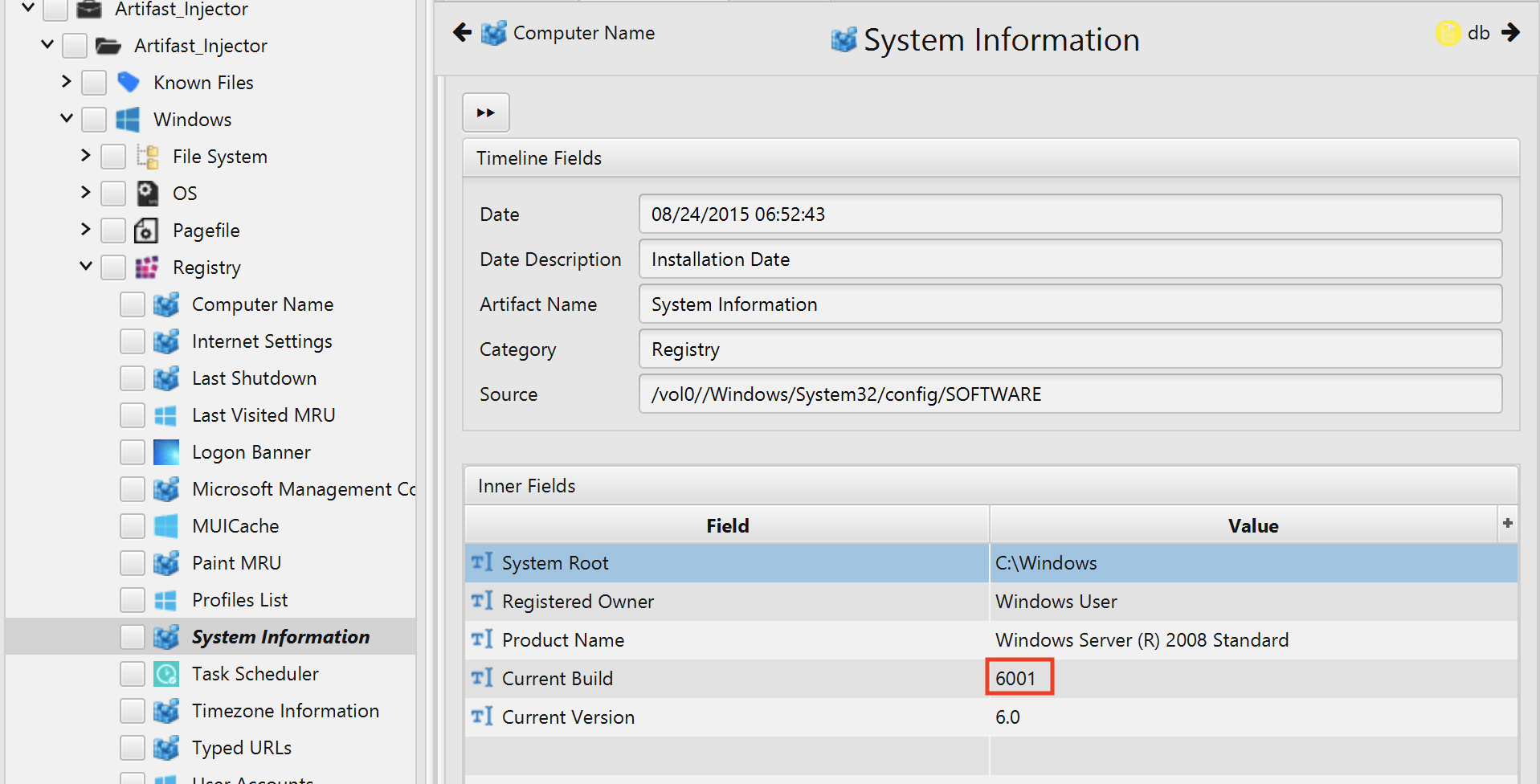
3. What is the OS build number?
The answer can be found in System Information artifact under the Registry category. The current build is 6001.
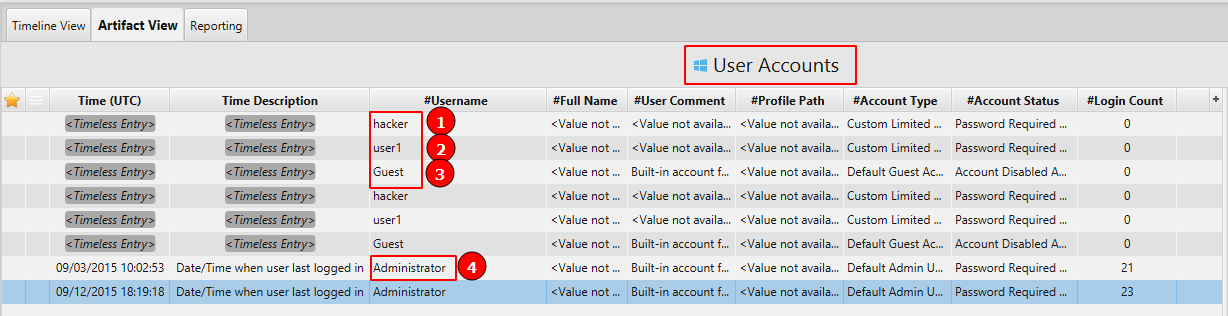
4. How many users are on the compromised machine?
The answer can be found in User Accounts artifact under the Registry category. There are 4 users on the compromised machine.
Web Server Information
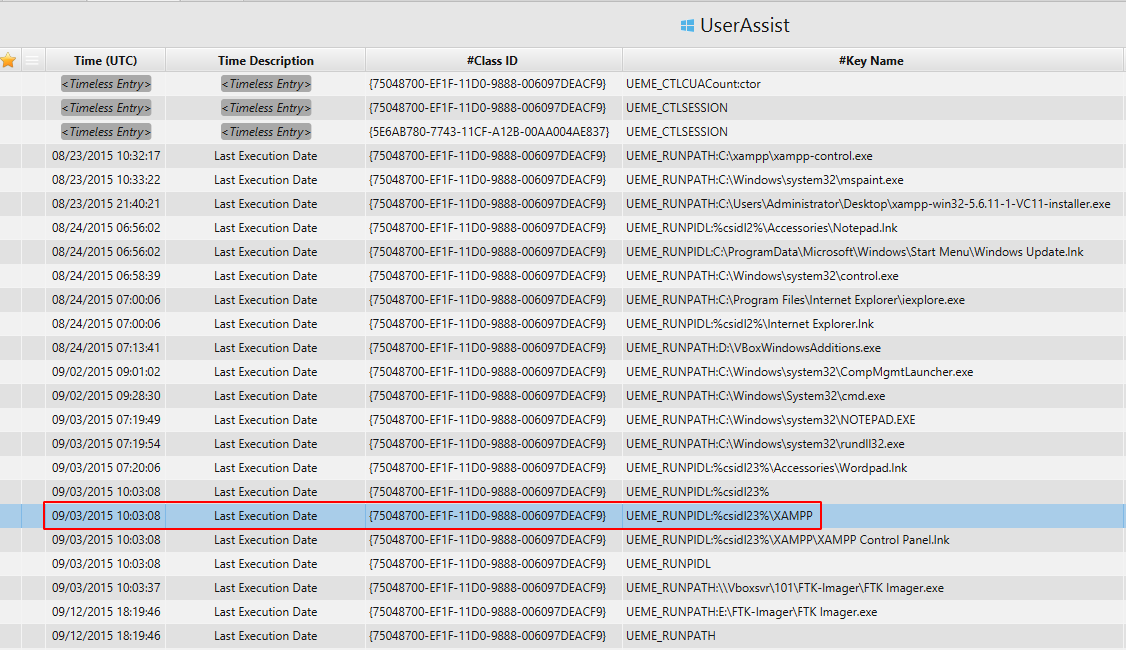
1. What is the webserver package installed on the machine?
The answer can be found in UserAssist artifact under the Registry category. XAMPP package was installed on the machine.
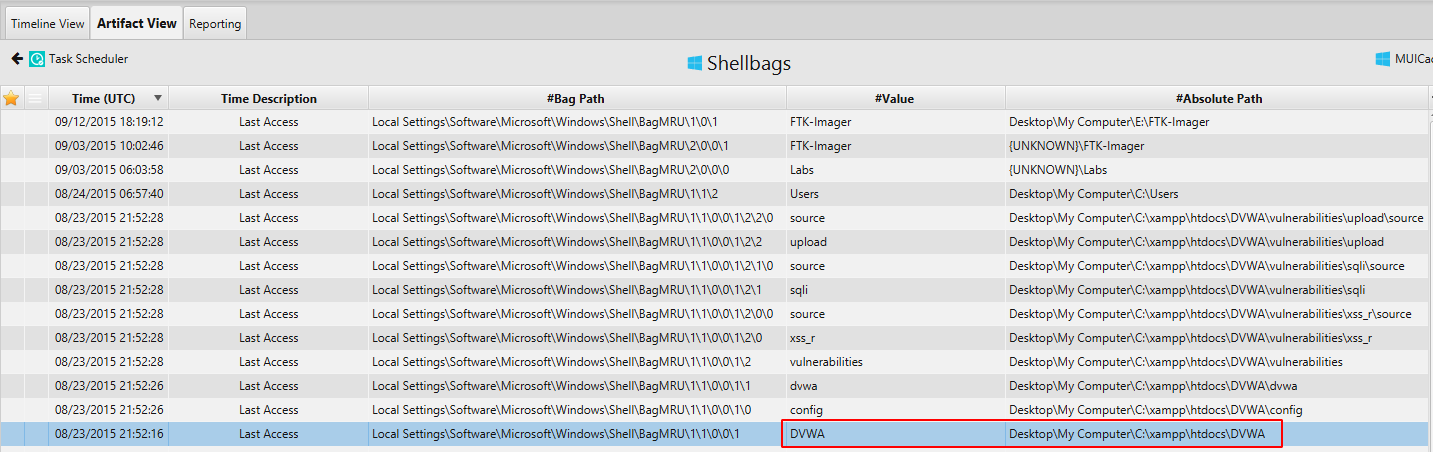
2. What is the name of the vulnerable web app installed on the webserver?
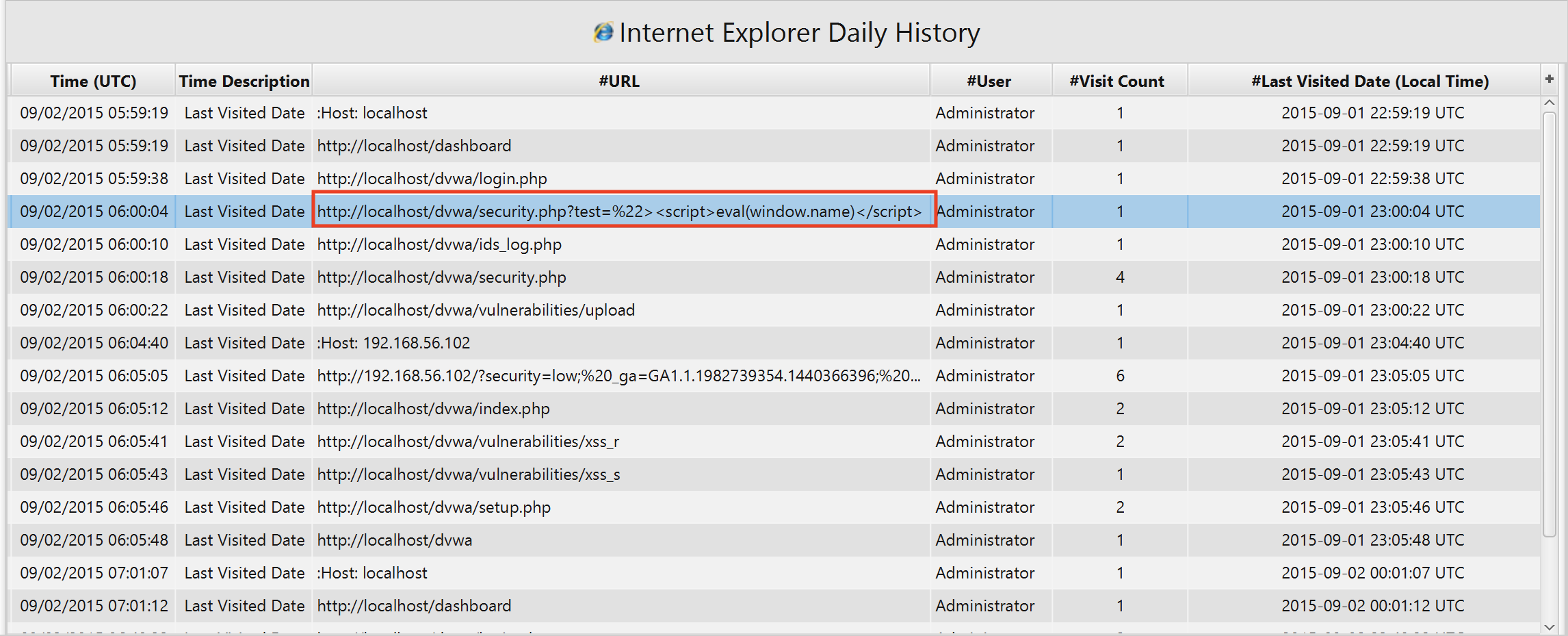
There are multiple ways to figure out the vulnerable web app installed on the webserver. Either through Shellbags artifact under the Registry category or through Internet Explorer Daily History artifact under the Web Activity category.
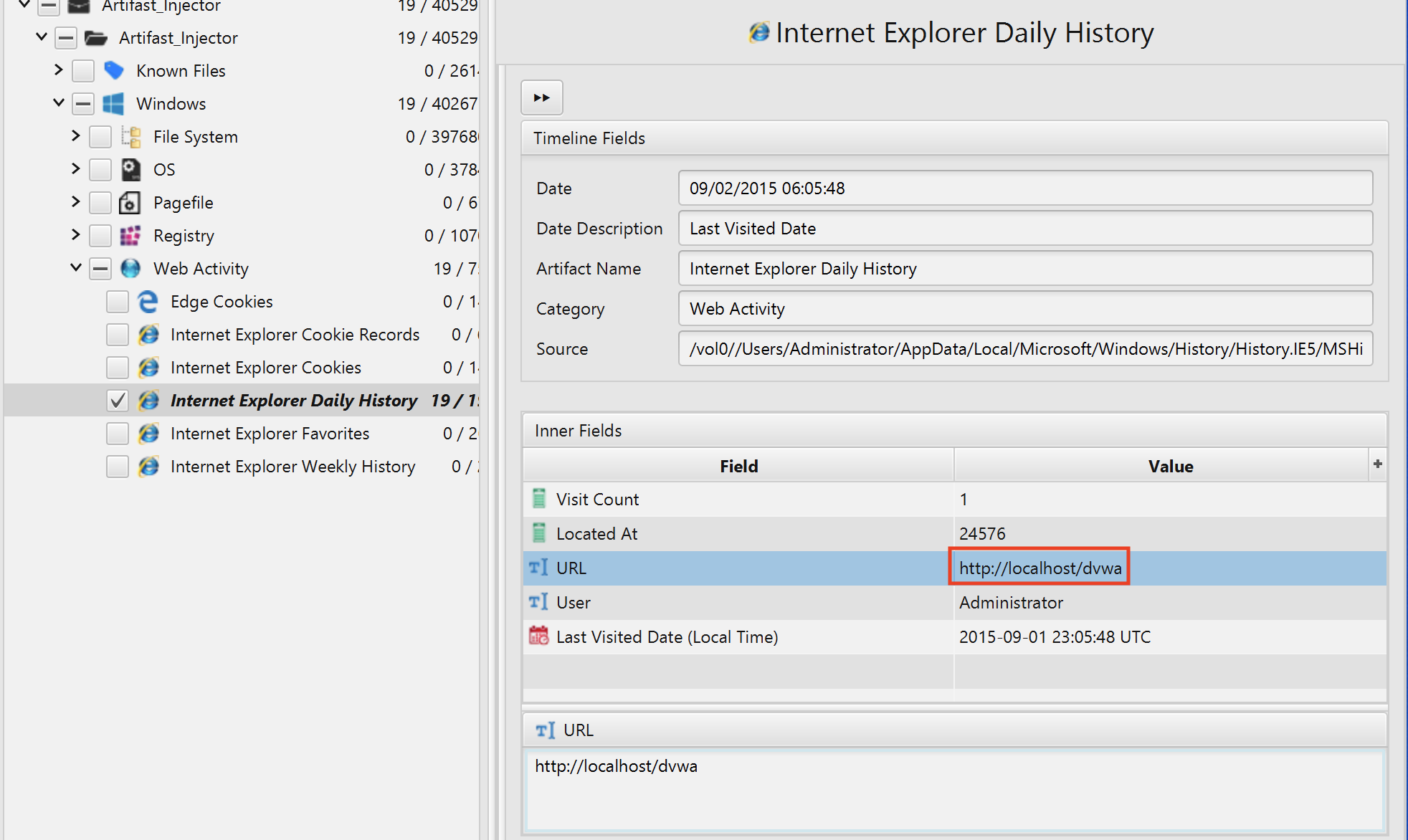
3. what is the first vulnerability that attacker exploit?
The answer can also be found in Internet Explorer Daily History artifact under the Web Activity category.
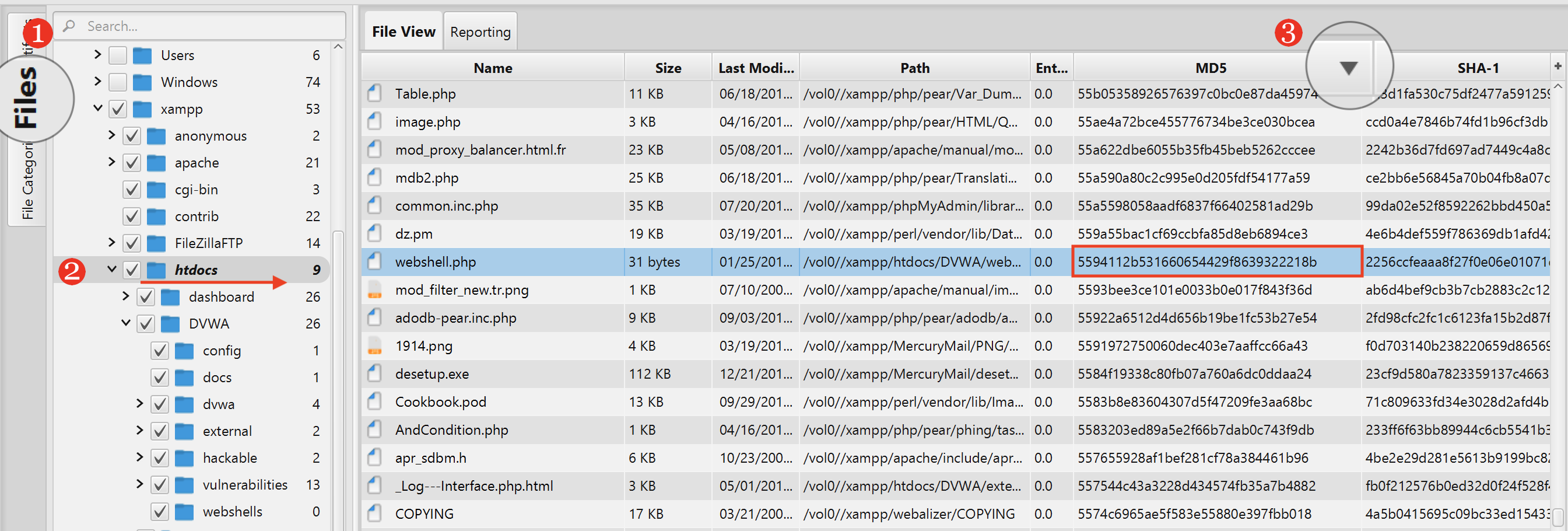
4. The MD5 hash value of one of uploaded shell by attacker
The answer can be found by following the steps below:
- Switch to files view.
- Navigate to htdocs folder.
- Sort the MD5 column by clicking on it.