Hunter Challenge Using the Full Version of ArtiFast Windows
31/05/2021 Monday
In this blog post, we will be solving a challenge designed by Cyber Defenders using the full version of ArtiFast Windows. In this case, the SOC team detected an illegal port scanning activity coming from a disgruntled employee's system who might be getting help from an outsider (full scenario). The purpose of this challenge is to analyze the image provided and confirm or deny the theory claimed. Below is the solution to the challenge, solved using the full version of ArtiFast.
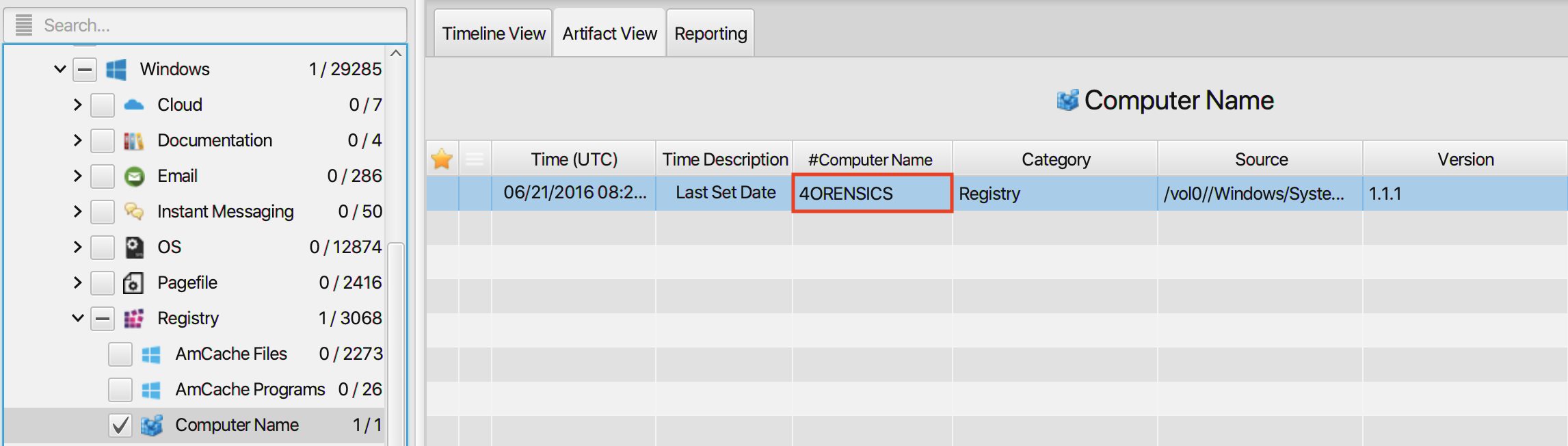
1. What is the computer name of the suspect machine?
The answer can be found in Computer Name artifact under the
Registry category. The computer name is 4ORENSICS .
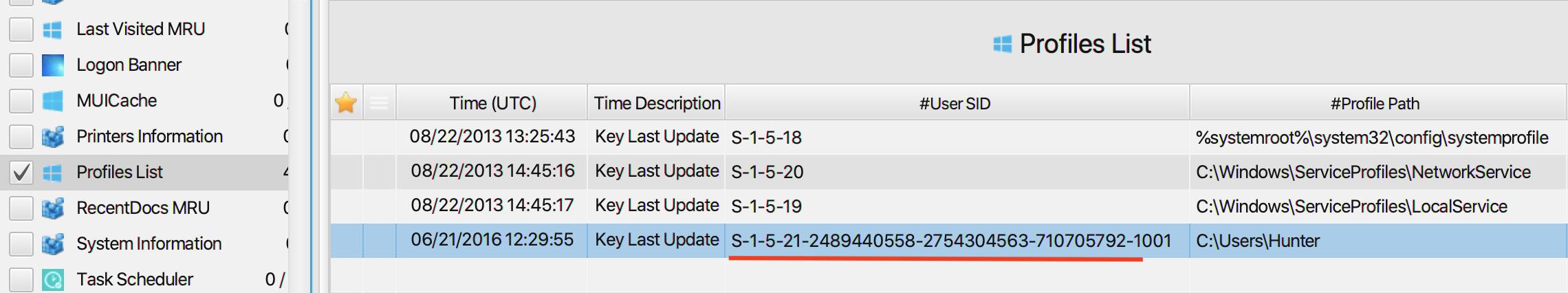
2. What is the computer SID?
The answer can be found in Profiles List artifact under the
Registry category. The computer SID is
S-1-5-21-2489440558-2754304563-710705792.
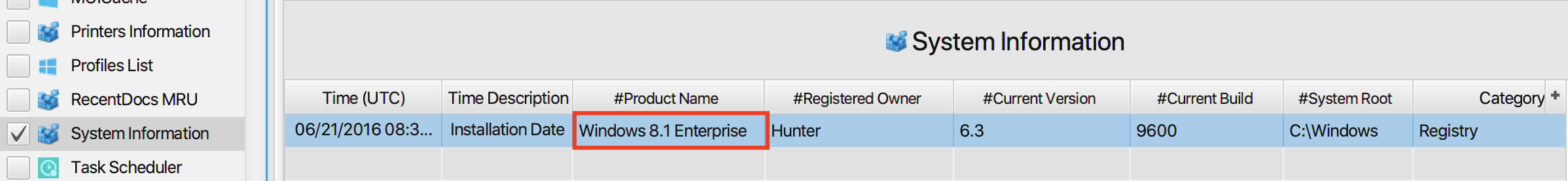
3. What is the Operating System (OS) version?
The answer can be found in System Information artifact under the
Registry category. The operating system version is
Windows 8.1 Enterprise.
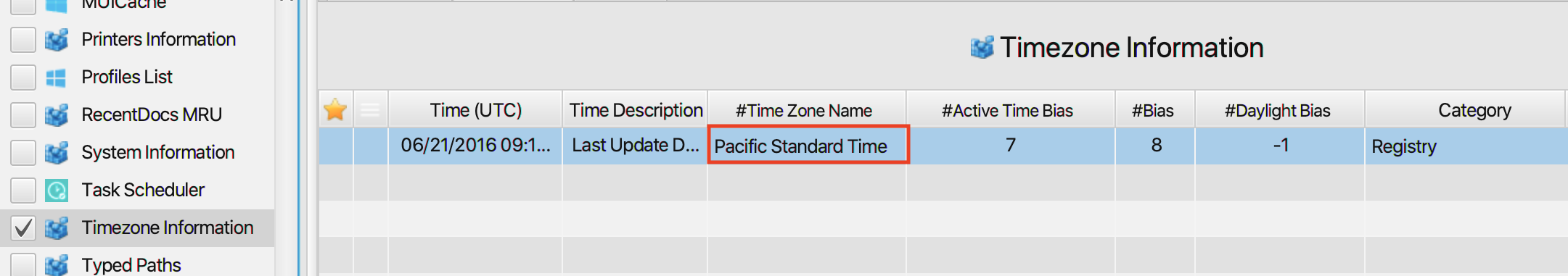
4. What was the computer timezone?
The answer can be found in Timezone Information artifact under
the Registry category. The computer timezone is UTC-07:00.
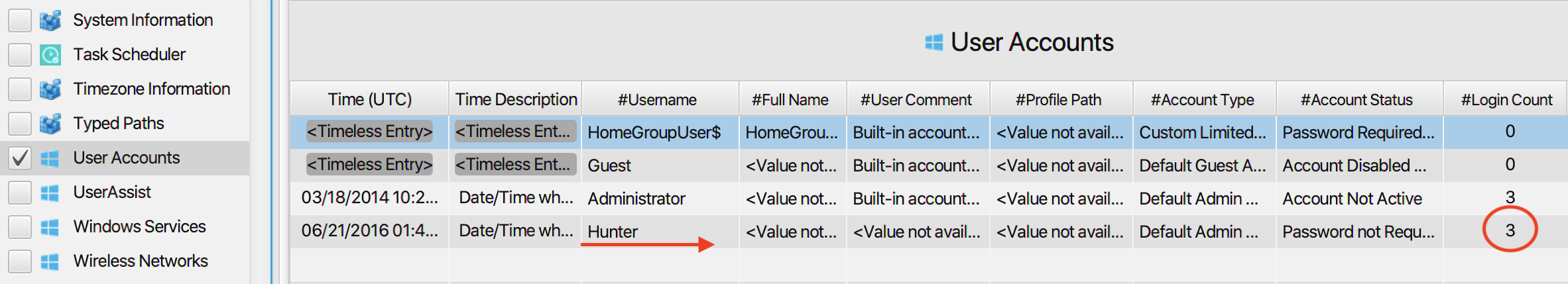
5. How many times did this user log on to the computer?
The answer can be found in User Accounts artifact under the
Registry category. The user Hunter logged in to the computer
3 times .
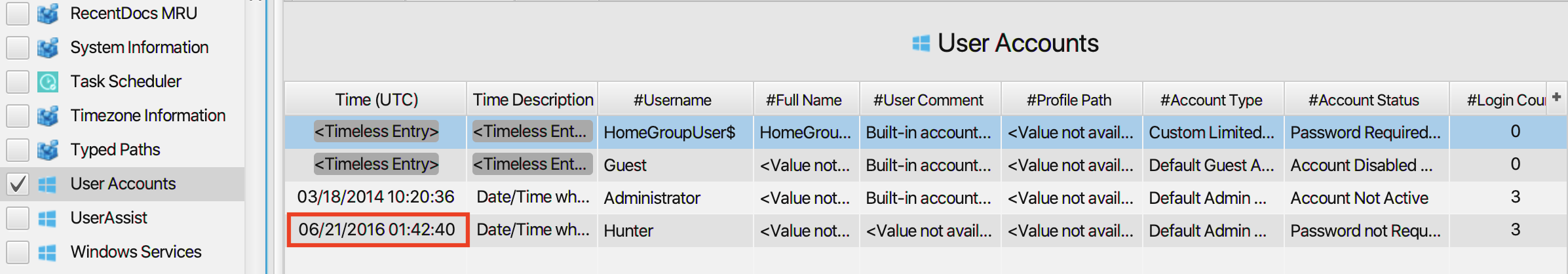
6. When was the last login time for the discovered account?
The answer can also be found in User Accounts artifact under the
Registry category. The last login time for the user Hunter is at
2016-06-21 01:42:40.
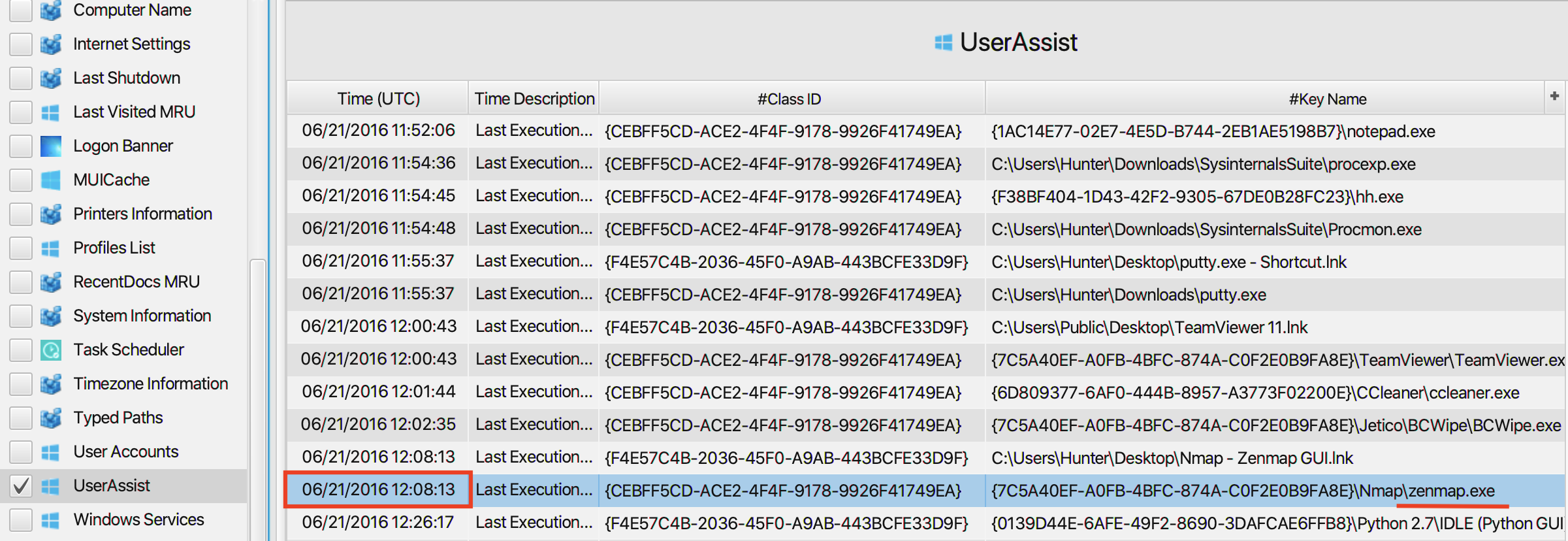
7. There was a “Network Scanner” running on this computer, what was it? And when was the last time the suspect used it?
The answer can be found in UserAssist artifact under the Registry
category. As can be seen in the picture below, zenmap was running
on the computer and the last time the suspect used it was at
2016-06-21 12:08:13.
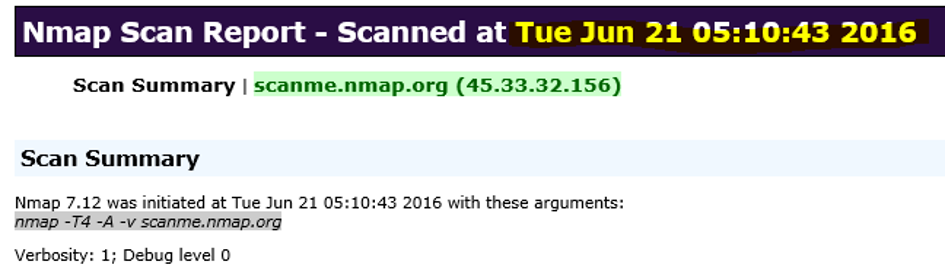
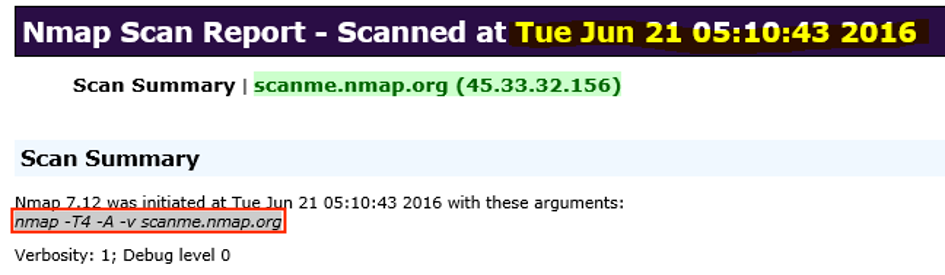
8. When did the port scan start and end?
The answer can be found within nmapscan.xml file which is located on
Hunter’s desktop.
To access nmapscan.xml file, switch to file view and then, navigate to
the file. By right clicking on any file, you can view it as text, image,
audio, video or pdf depending on the type of the file. The file will
open on the window in the rightmost side of the screen and you can
extract and save these files.
9. How many ports were scanned?
The answer can also be found in nmapscan.xml file. The user
Hunter used the command nmap -T4 -A -v scanme.nmap.org which
means that 1000 ports were scanned.
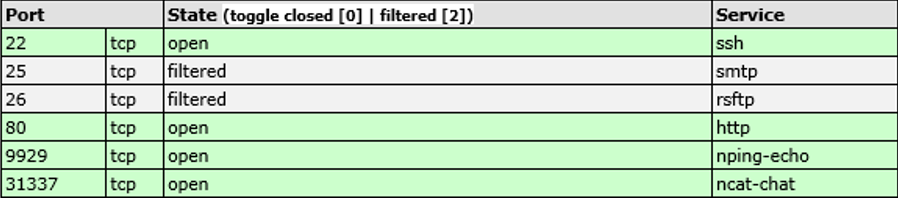
10. What ports were found "open"?
The answer can also be found in nmapscan.xml file. As can be
seen in the picture below, the ports
22, 25, 26, 80, 9929 and 31337 were found open.
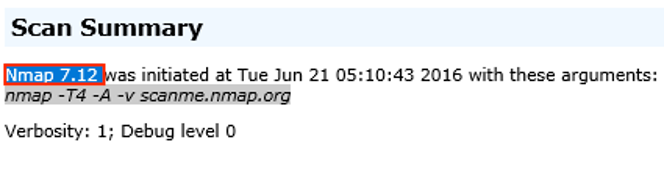
11. What was the version of the network scanner running on this computer?
The answer can also be found in nmapscan.xml file. As can be
seen in the picture below, the version of the network scanner running on
the computer is (7.12).
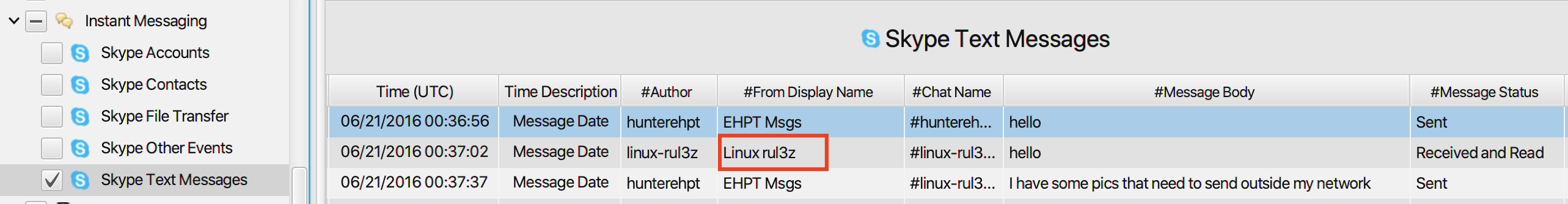
12. The employee engaged in a Skype conversation with someone. What is the skype username of the other party?
The answer can be found in Skype Text Messages artifact under
Instant Messaging category. The employee exchanged several
messages with a user named Linux rul3z.
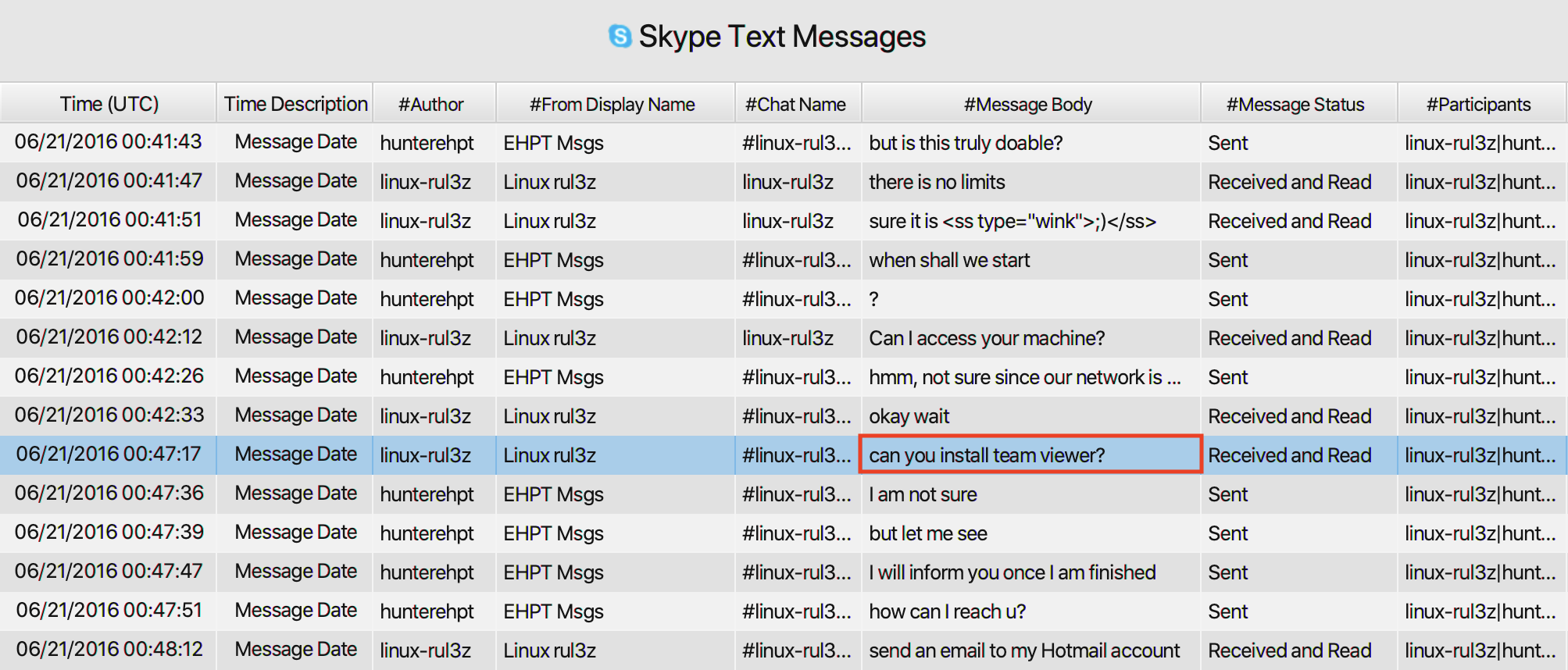
13. What is the name of the application both parties agreed to use to exfiltrate data and provide remote access for the external attacker in their Skype conversation? And when did the suspect run it?
The answer can also be found in Skype Text Messages artifact.
As can be seen in the picture below, the employee and the external
attacker agreed on using Team Viewer.
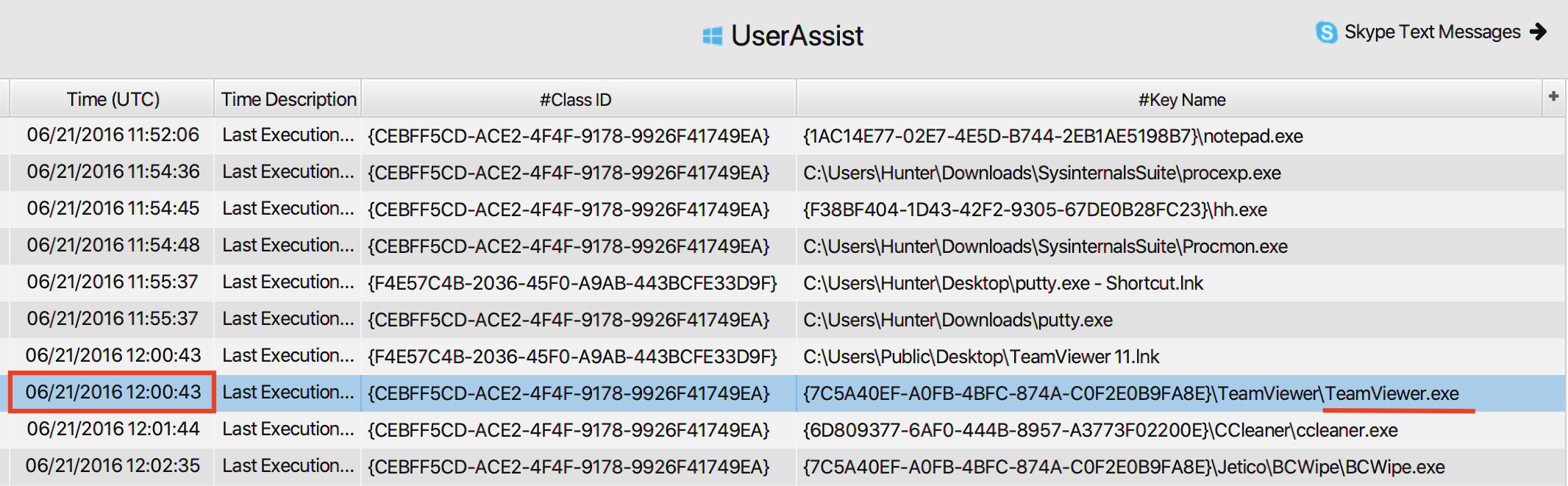
For the second part of the question, the answer can be found in
UserAssist artifact under the Registry category. As can
be seen in the picture below, the suspect ran Team Viewer at
2016-06-21 12:00:43.
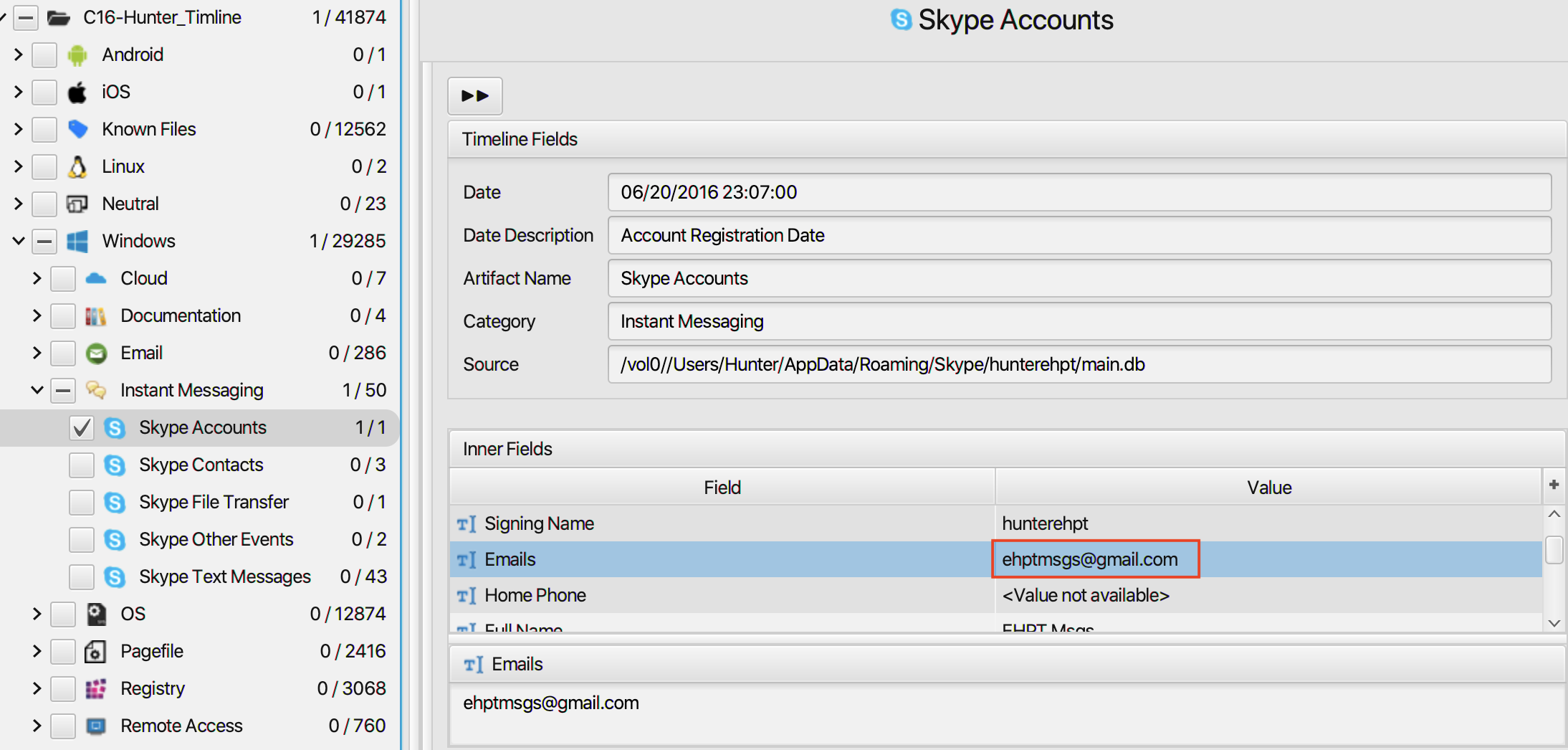
14. What is the Gmail email address of the suspect employee?
The answer can be found in Skype Accounts artifact under
Instant Messaging category. The email address of the suspect
employee is ehptmsgs@gmail.com .
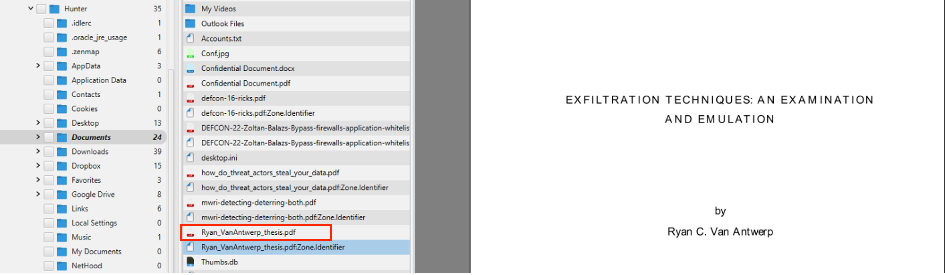
15. The user Documents' directory contained a PDF file discussing data exfiltration techniques. What is the name of the file?
To find the file, switch to file view and then, navigate to the
documents' directory. You can view all the pdf files by right clicking
on any of them. As can be seen in the picture below, the name of the
file discussing data exfiltration techniques is
Ryan_VanAntwerp_thesis.pdf.
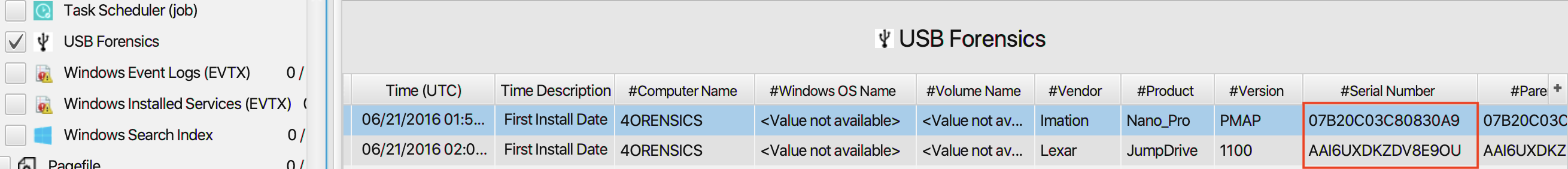
16. What are the serial numbers of the two identified USB storage?
The answer can be found in USB Forensics artifact under
OS category. The serial numbers of the two identified USB
storage are 07B20C03C80830A9 and AAI6UXDKZDV8E9OU.
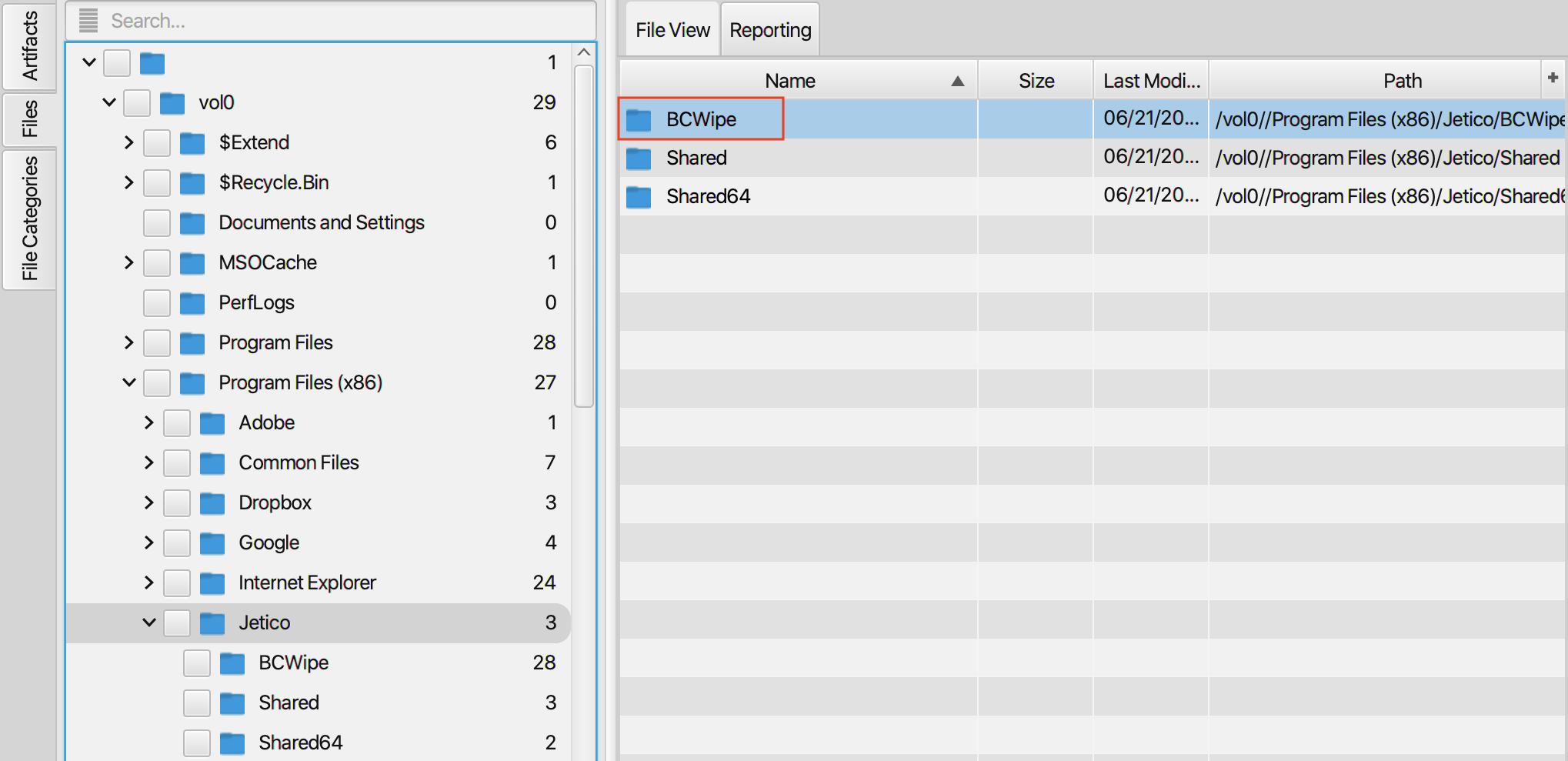
17. One of the installed applications is a file shredder. What is the name of the application?
To find the application, switch to file view and then, navigate to
program file (x86). As can be seen in the picture below, the name of the
application is Jetico BCWipe.
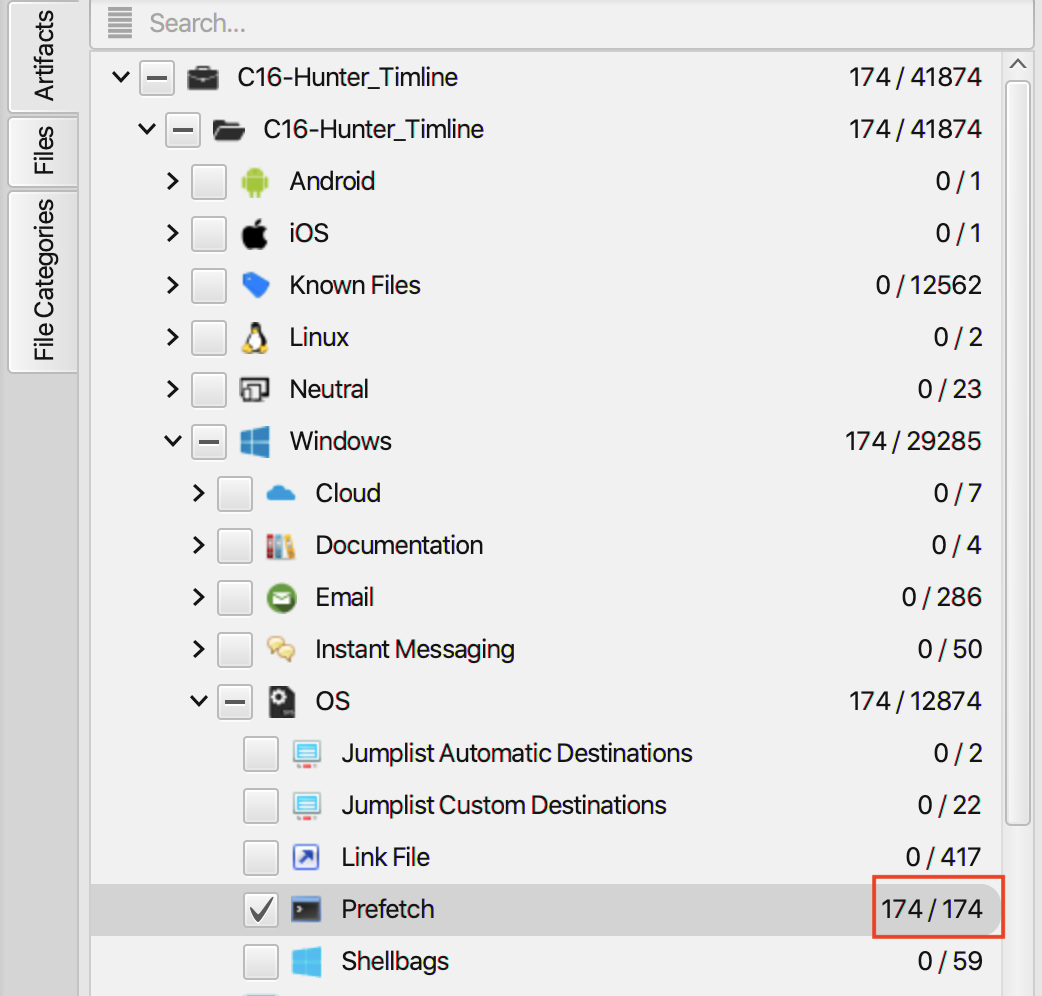
18. How many prefetch files were discovered on the system?
As can be seen in the picture below, the number of prefetch files
that were discovered on the system is (174).
19. How many times was the file shredder application executed?
The answer can be found in Prefetch artifact under
OS category. The file shredder application was executed
5 times.
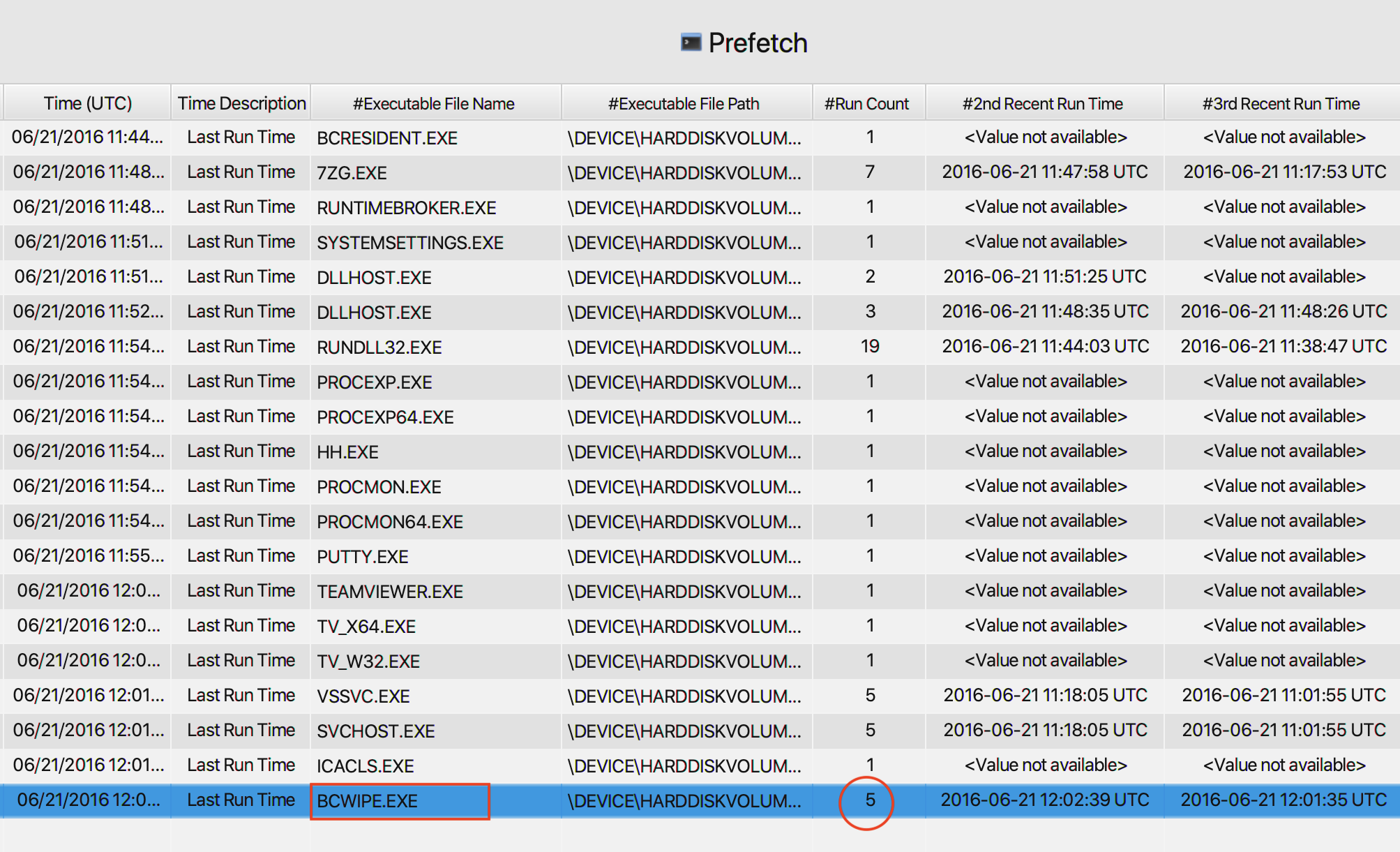
20. Using prefetch, determine when was the last time ZENMAP.EXE-56B17C4C.pf was executed?
As can be seen in the picture below, ZENMAP.EXE-56B17C4C.pf was
last executed on June 21, 2016 at 12:08:13 PM.
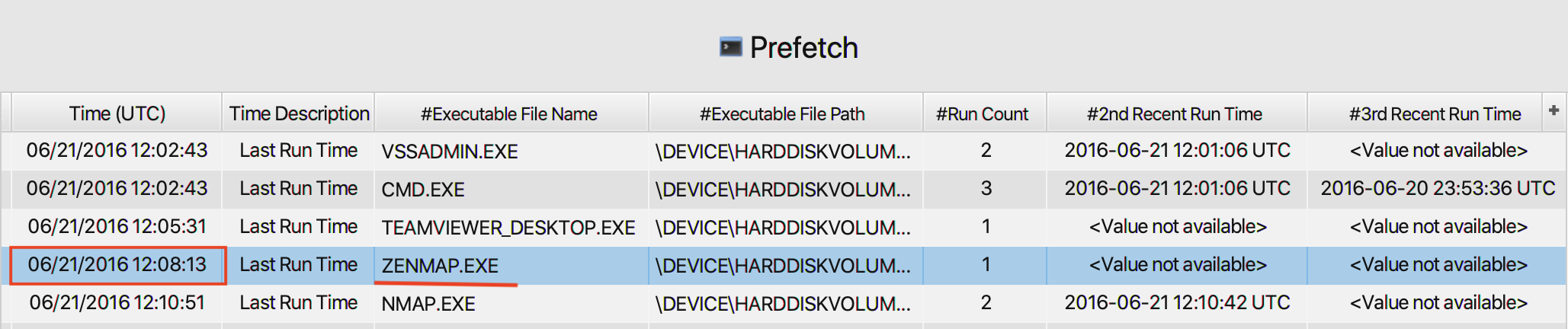
21. The suspect employee tried to exfiltrate data by sending it as an email attachment. What is the name of the suspected attachment?
The answer can be found in Outlook PST/OST artifact under
Email category. As can be seen in the picture below, the name
of the attachment is Pictures.7z.
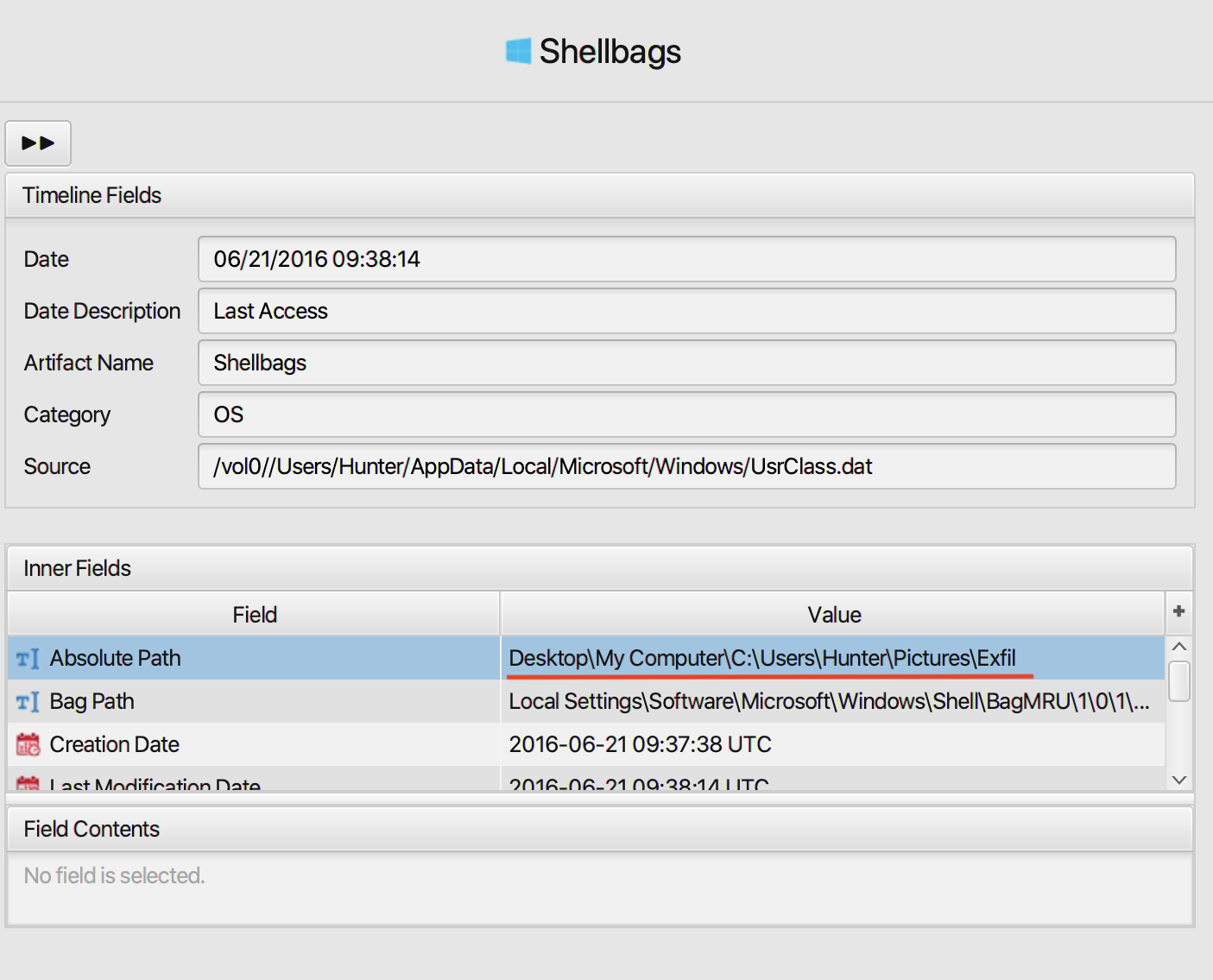
22. Shellbags shows that the employee created a folder to include all the data he will exfiltrate. What is the full path of that folder?
As indicated in the question, the answer can be found in
Shellbags
artifact under OS category. The full path to the folder is
C:\Users\Hunter\Pictures\Exfil