Data Leak Challenge Using the Full Version of ArtiFast Windows
23/02/2021 Tuesday
National Institute of Standards and Technology (NIST) provides DFIR challenges to help people learn about various types of challenges and the techniques that can be used to solve them. This challenge provides the following scenario. It is a data leakage case where we are required to find evidence of the offense and any data that the suspect might have generated. Below is the solution to the challenge, solved using the full version of ArtiFast.
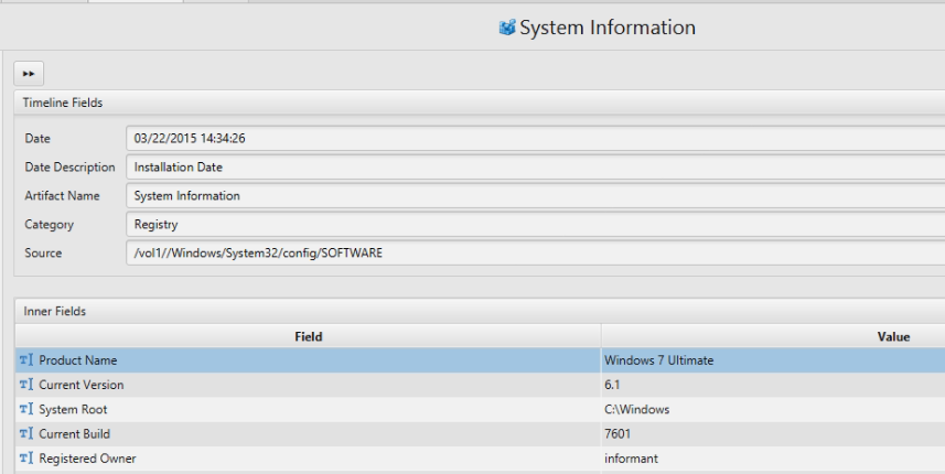
1. Explain installed OS information in detail.
The answer can be found in System Information Artifact.
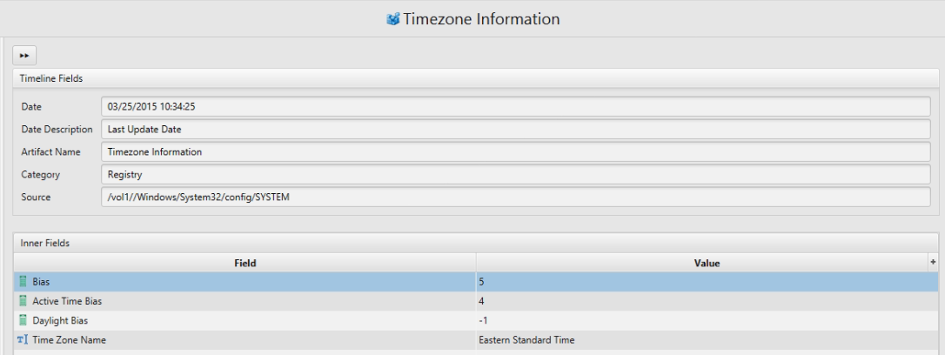
2. What is the timezone setting?
Answer: Eastern Time (US & Canada)(UTC-05:00)
The answer can be found in Timezone artifact.
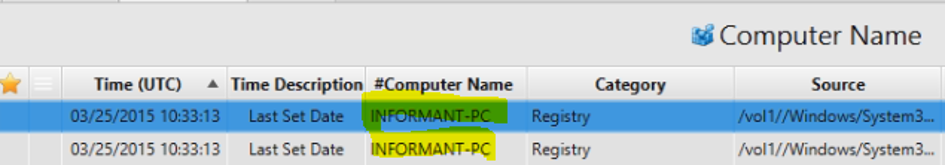
3. What is the computer name?
Answer: INFORMANT-PC
The answer can be found in Computer Name Artifact.
4. List all accounts in OS except the system accounts: Administrator, Guest, systemprofile and LocalService?
Answer: informant, admin11, ITechTeam, and Temporary.
The answer can be found in User Accounts Artifact.
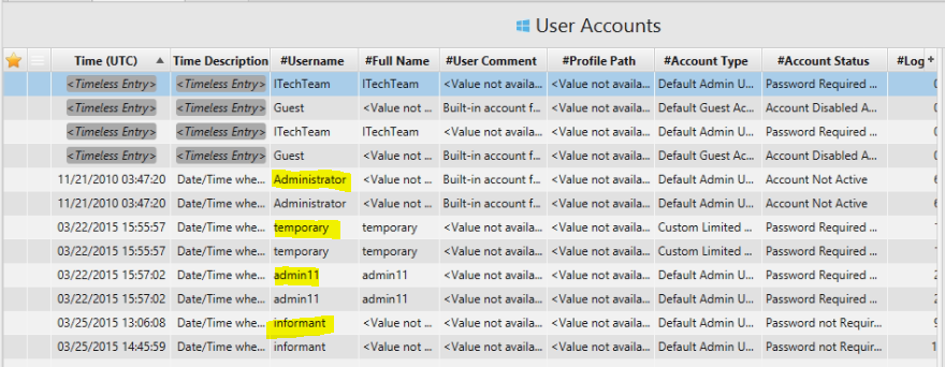
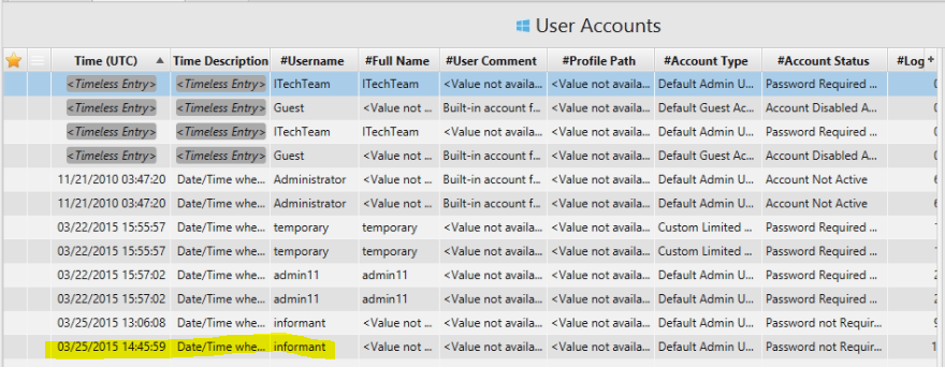
5. Who was the last user to logon into PC?
Answer: informant.
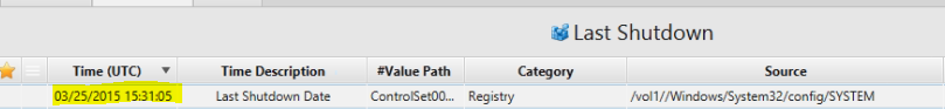
6. When was the last recorded shutdown date/time?
Answer: 2015-03-25 11:31:05 (Eastern Time + DST).
The answer can be found in Last Shutdown Artifact.
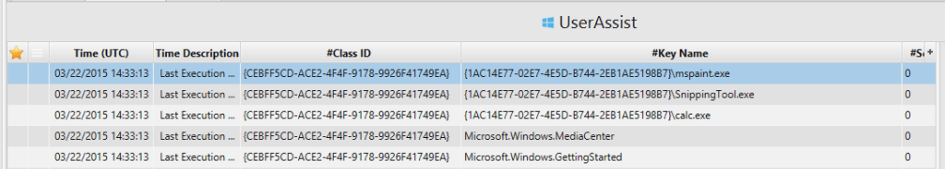
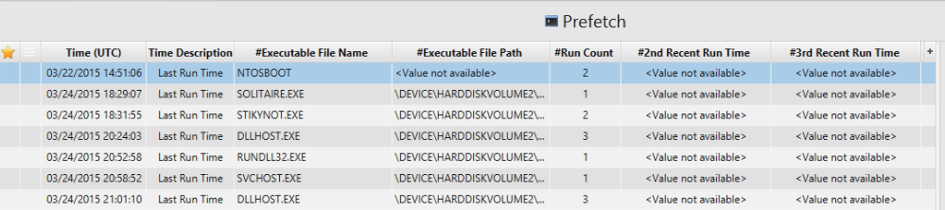
7. List application execution logs.
It is a huge list of execution files but we can take a screenshoots of
prefech and userassit artifacts.
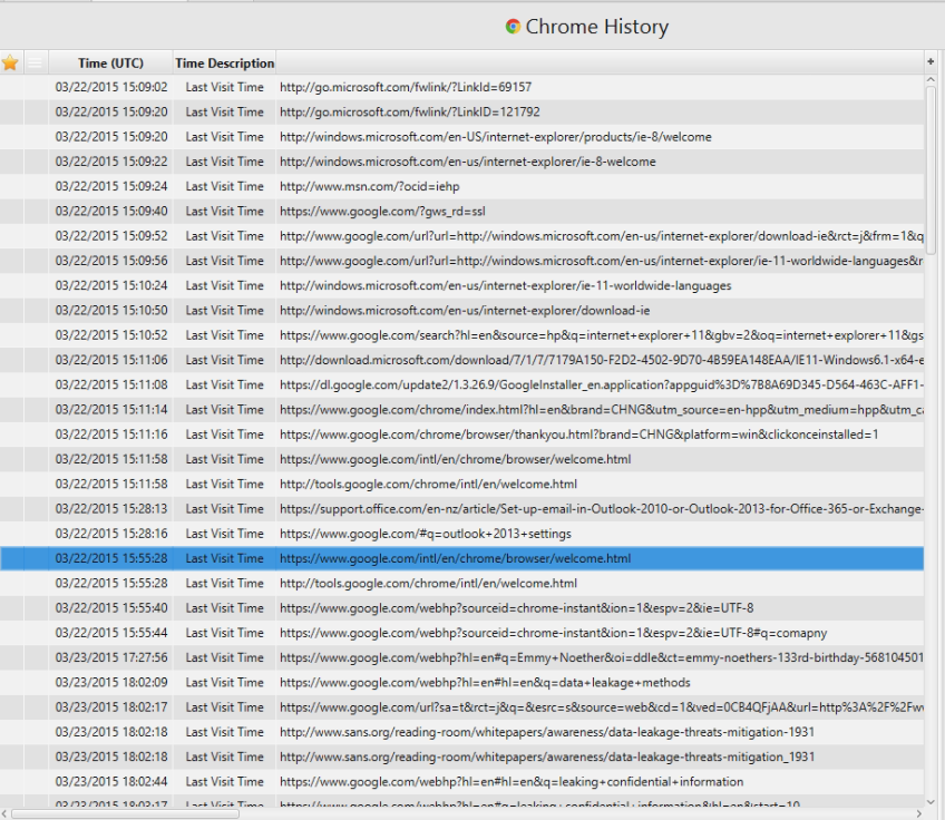
8. What websites were the suspect accessing?
We can check chrome history.
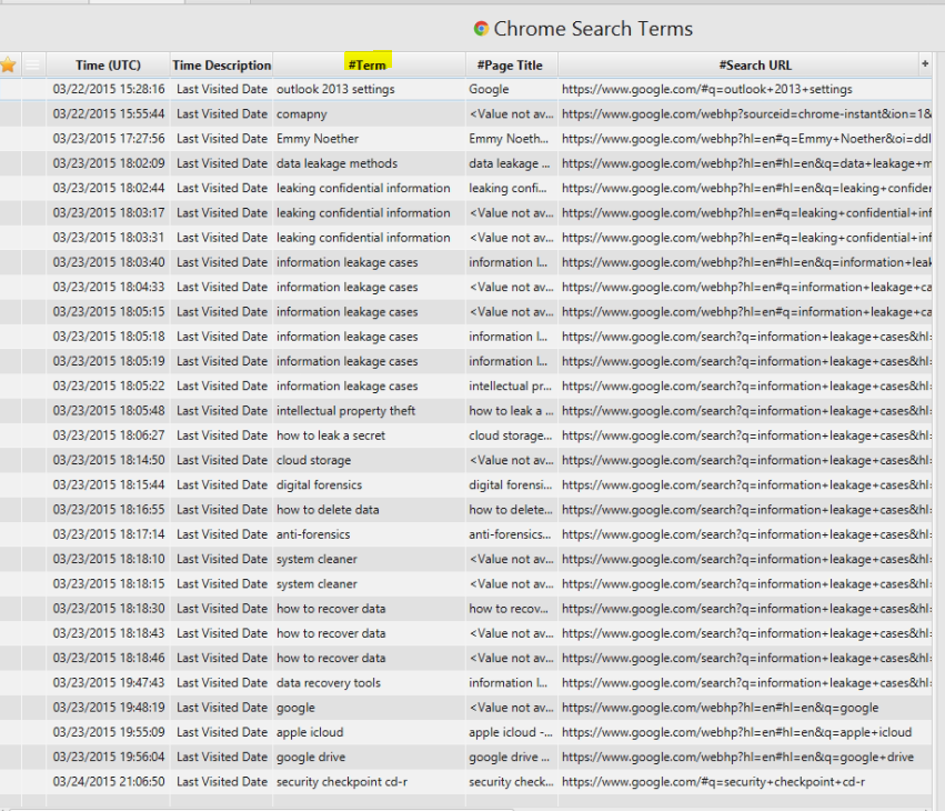
9. List all search keywords using web browsers.
Here I have used Chrome Search Terms artifact to list the keywords.
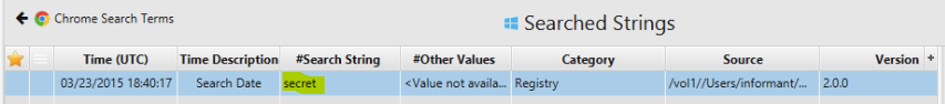
10. List all user keywords at the search bar in Windows Explorer.
The answer can be found in the Search Strings artifact.
11. Where is the e-mail file located?
Answer:
C:\Users\informant\AppData\Local\Microsoft\Outlook\iaman.informant@nist.gov.ost
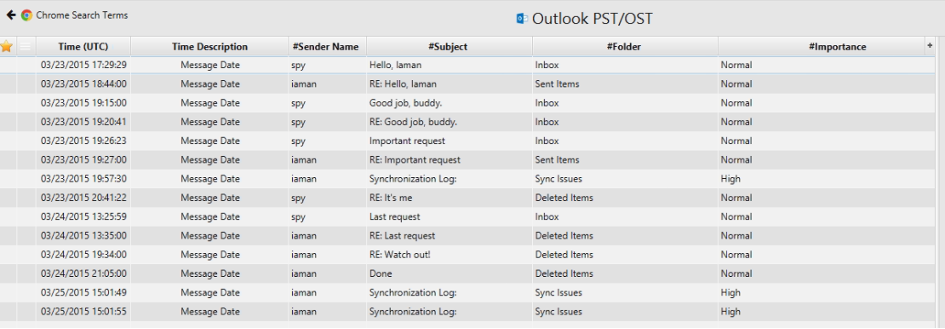
12. List all e-mails of the suspect. If possible, identify deleted e-mails.
The answer can be found in Outlook/OST artifact.
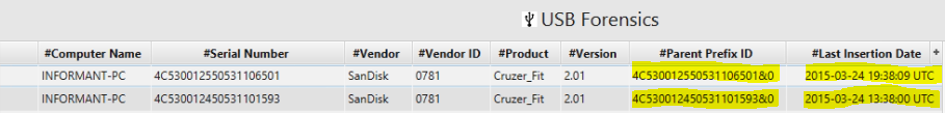
13. List external storage devices attached to PC.
The answer can be found in USB Artifact.
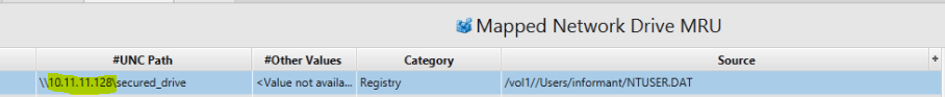
14. What is the IP address of company's shared network drive?
Artifact: Mapped Network Drive MRU.
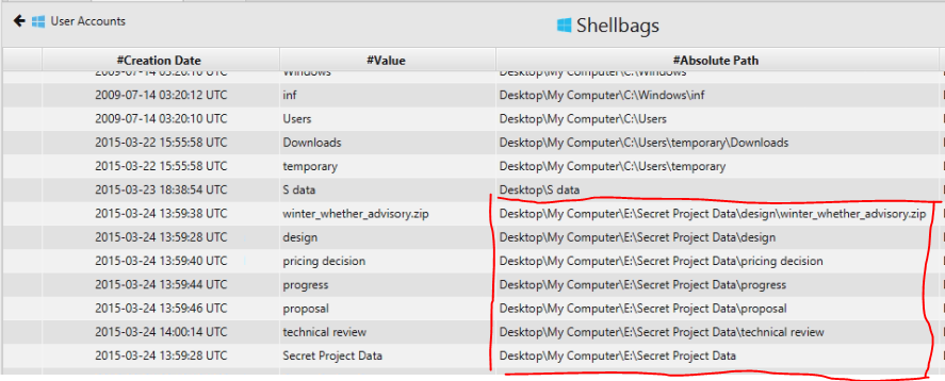
15. List all directories that were traversed in 'RM#2'.
Answer: Shellbags.
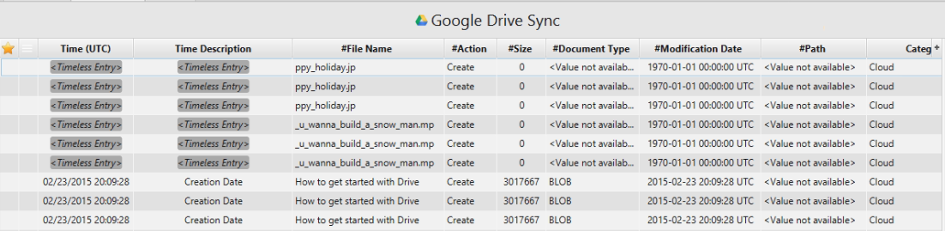
16. What files were deleted from Google Drive?
Artifact: Google Drive Sync.
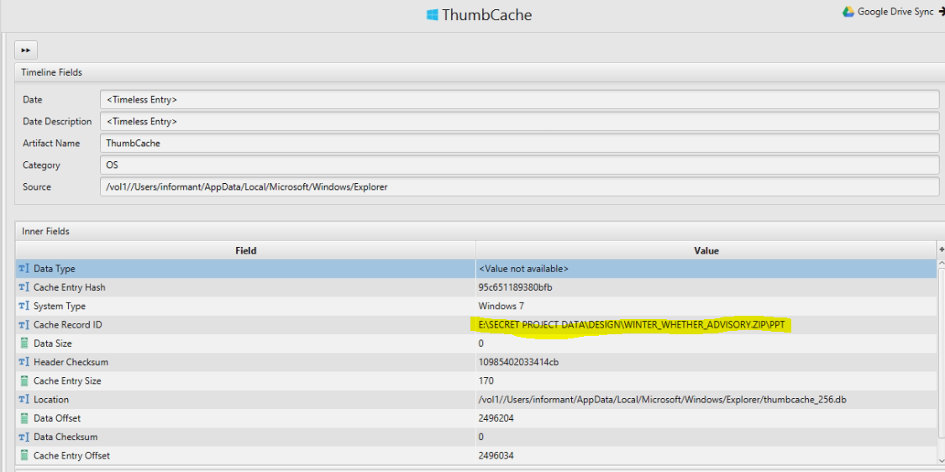
17. Identify traces related to confidential files stored in Thumbcache.
Artifact: Thumbcache.
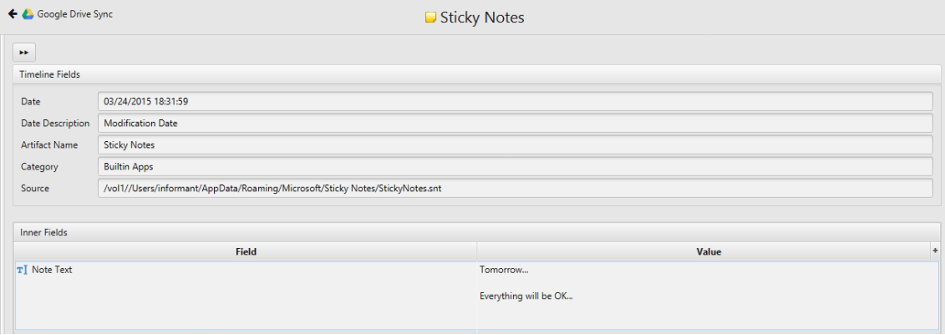
18. Identify notes stored in the Sticky Note file.
Artifact: Sticky notes Artifact.
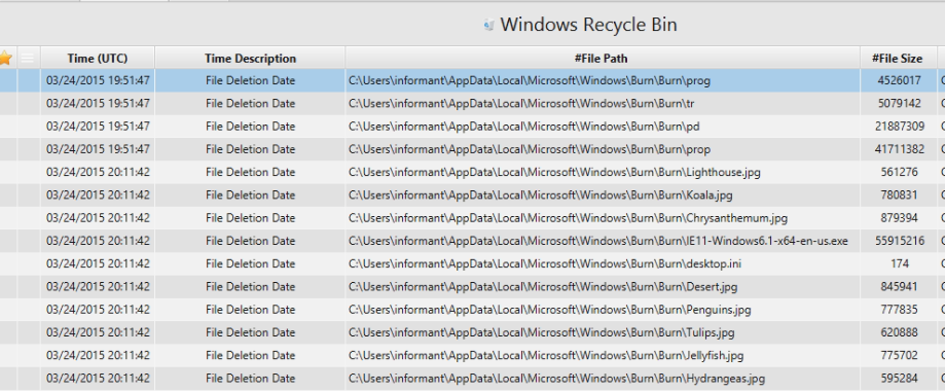
19. Examine 'Recycle Bin' data in PC.
Artifact: Recycle Bin Artifact.