BelkaCTF #6: Bogus Bill
16/01/2026 Friday
Belkasoft’s BelkaCTF 6 (Bogus Bill) ran from Apr 5 to 7, 2024, for 48 hours, following a “Bogus Bill” money-moving storyline across iOS and Windows evidences. This challenge will be solved with ArtiFast Suite (Full Version).
Artifacts Covered in this Challenge:
- Apple Accounts
- iOS Contacts
- iOS Telegram Users
- iOS Telegram Messages
- iOS Uber Places
- Windows User Accounts
- Windows Notifications
- iOS SplitWise Notifications
- Apple Notes
- Edge Chromium History
- Apple Spotlight
- Apple Known Wi-Fi Networks
- iOS SplitWise Notifications
- Link File
- Apple Biome Notifications
- iOS Installed Applications
Ident (Baby)
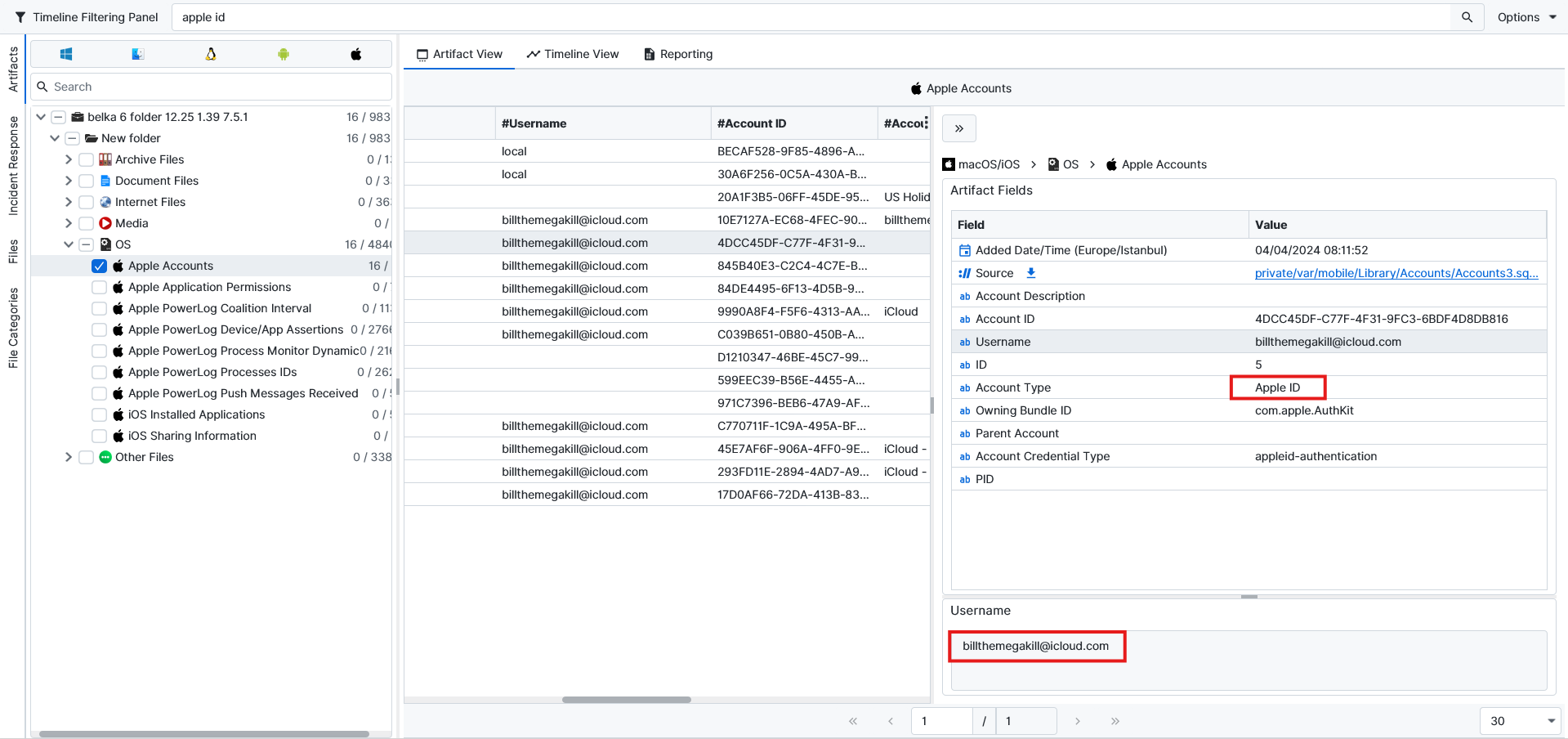
Q: What is the Apple ID used on the imaged iPhone?
billthemegakill@icloud.com.We can find the Apple ID of the iPhone by accessing the Apple Accounts artifact under the Username attribute. We can see that the Account type is Apple ID with the username used on it.
Namedrop (Baby)
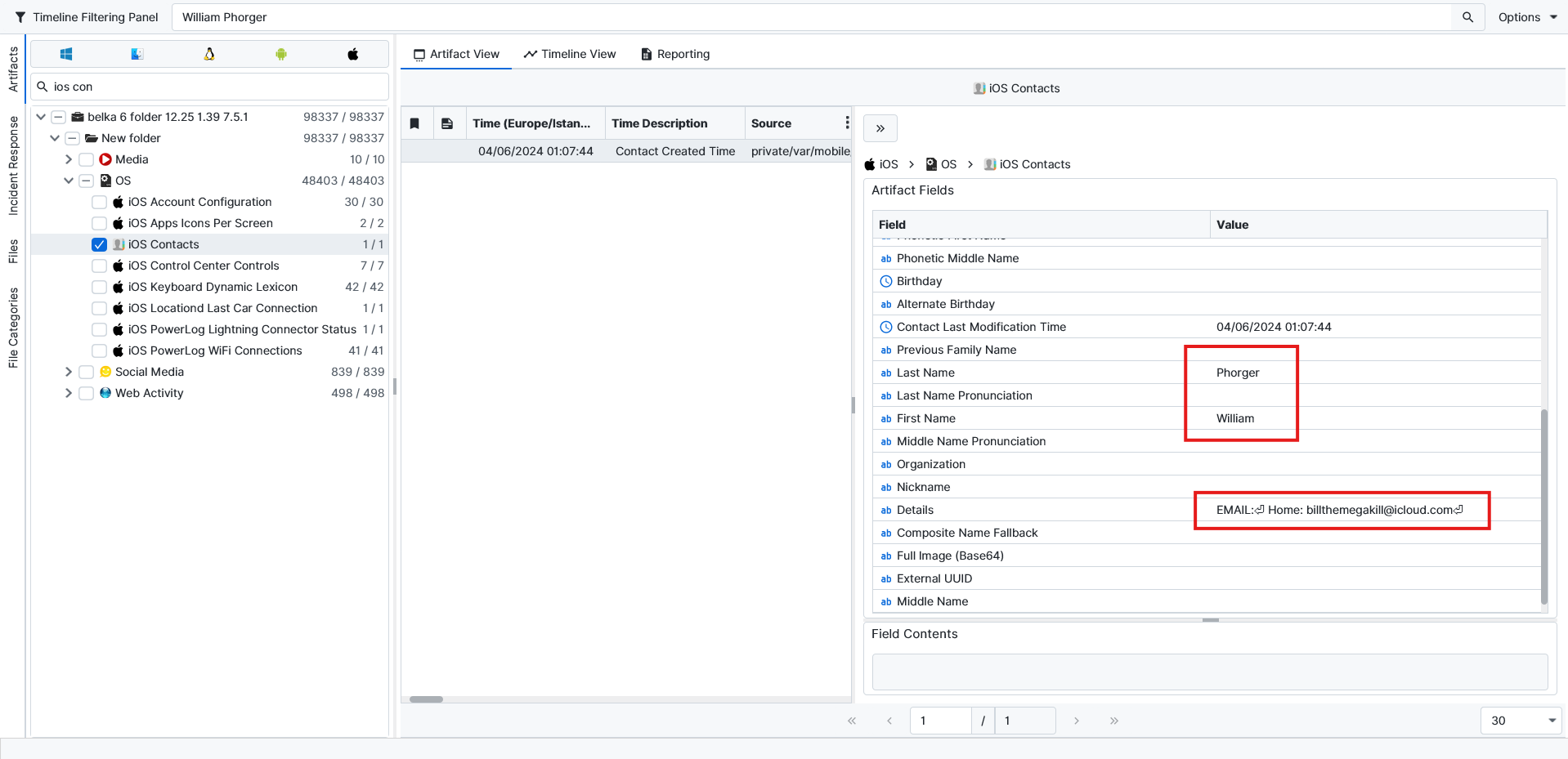
Question: What is the iPhone owner's full name? Flag format: First name Last name
William Phorger.If we filter all the results with the Apple ID we found from the previous question, which is billthemegakill@icloud.com we get contact info inside the iOS Contacts. The username is provided under this artifact.
Conspirators (Warmup)
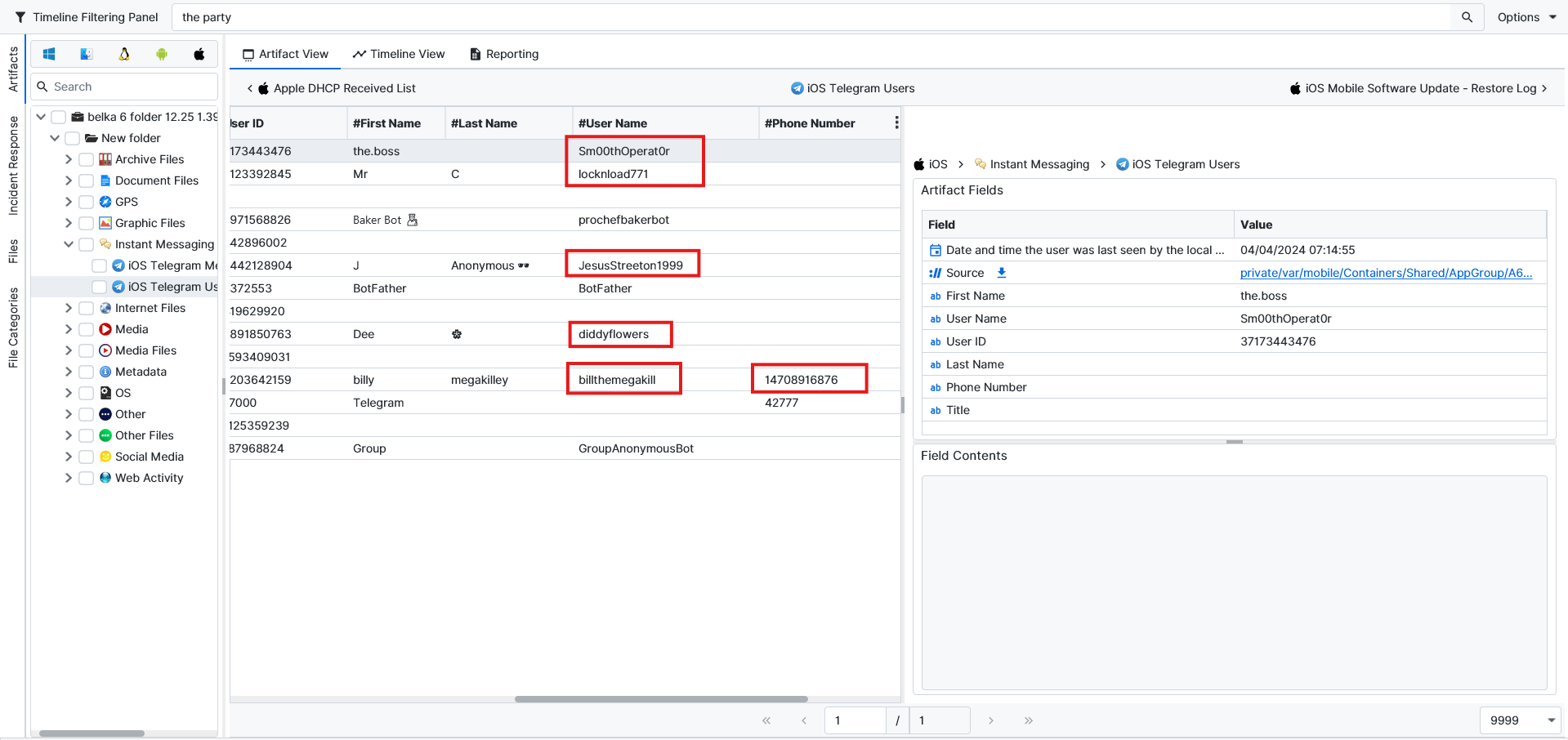
Question: Which Telegram accounts did the owner discuss shady stuff with? Flag format: @username, @username, @username, ...
@Sm00thOperat0r, @locknload771, @JesusStreeton1999, @diddyflowers.When we checked the chats in Telegram, we noticed a group that was discussing shady stuff in it. The group is called the party. If we take all the usernames that are in this group, we get the answer to our question.
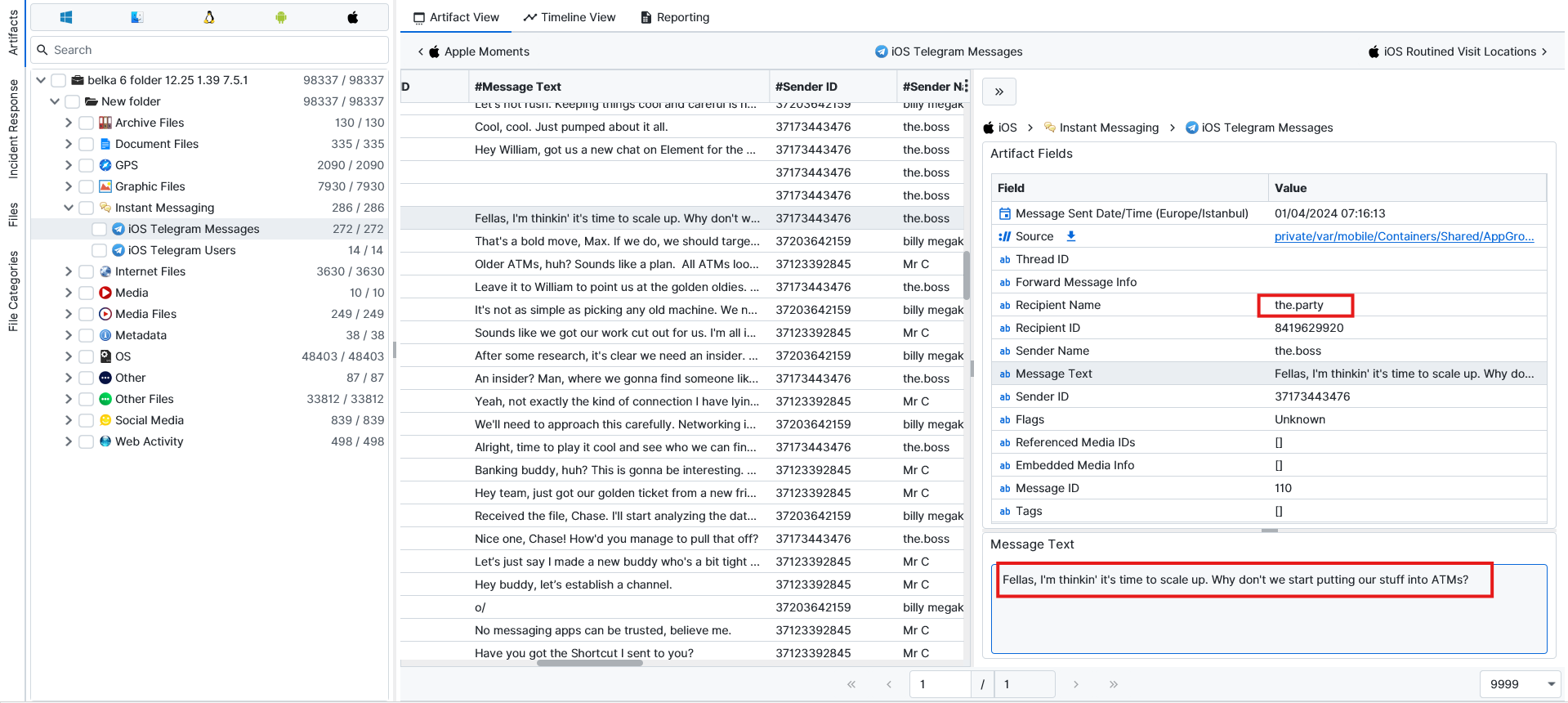
So, we filter the chats to only show messages in the party group. We notice 5 usernames in this group.
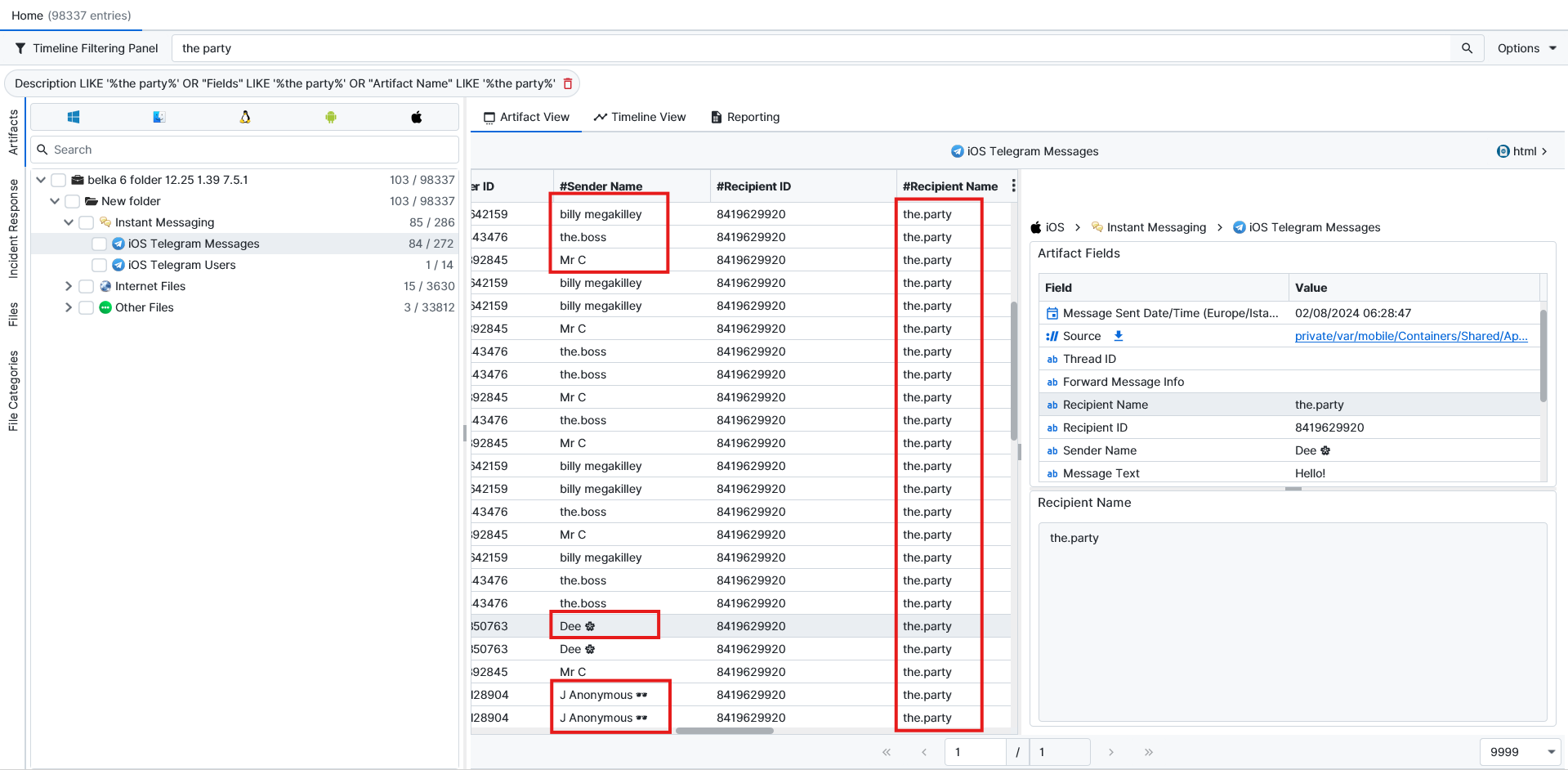
Out of 5 usernames, there is one username that is for the user themselves. This can be identified by phone number. The user is billthemegakill, and the rest are the people who were talking on the group chat.
Visit (Tricky)
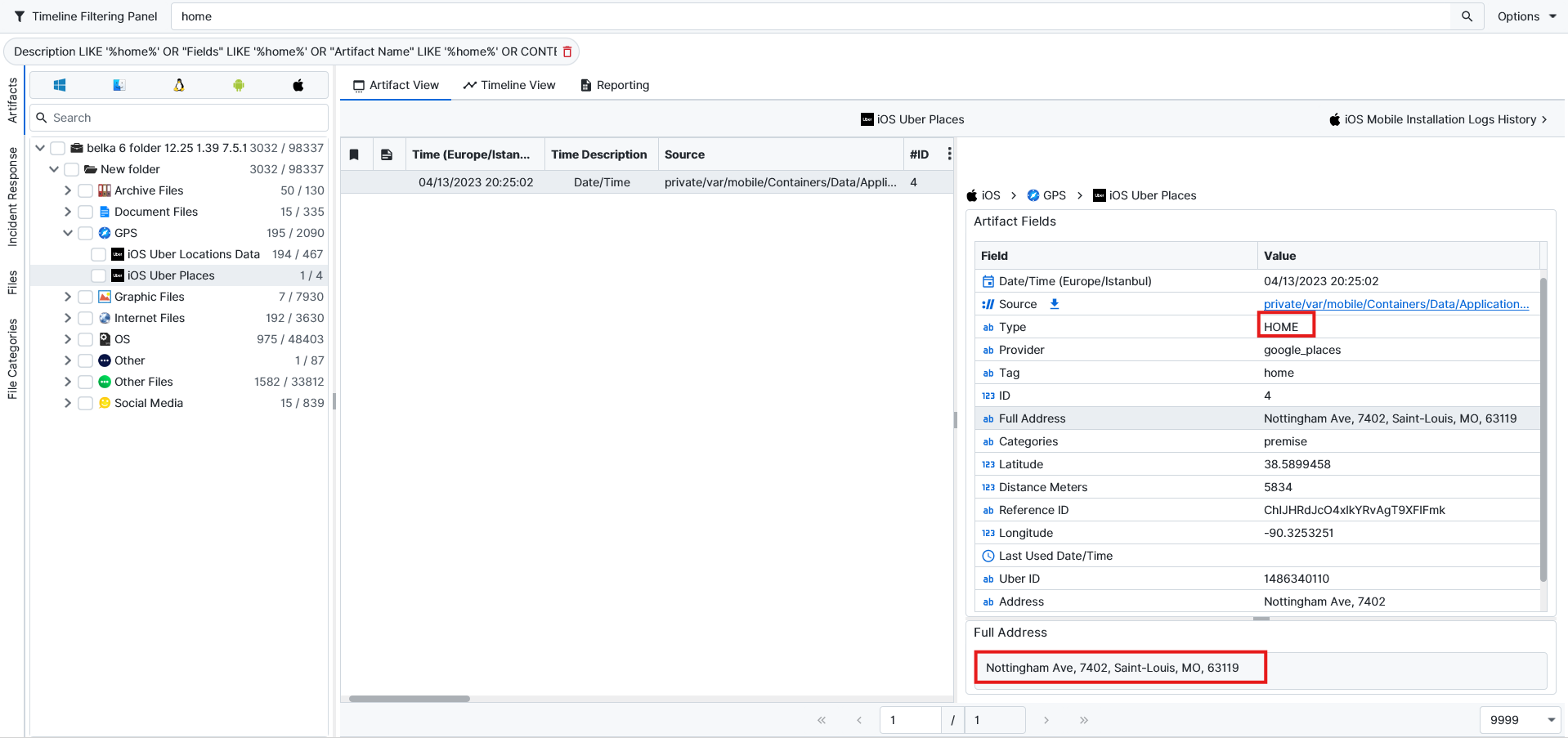
Question: Where does William live? Flag format: latitude, longitude—or just click the map
Nottingham Ave, 7402, Saint-Louis, MO, 63119.To find this, I searched for the word Home on ArtiFast and checked the results. On the iOS Uber Places, there is an address with a home tag on it.
Username (Baby)
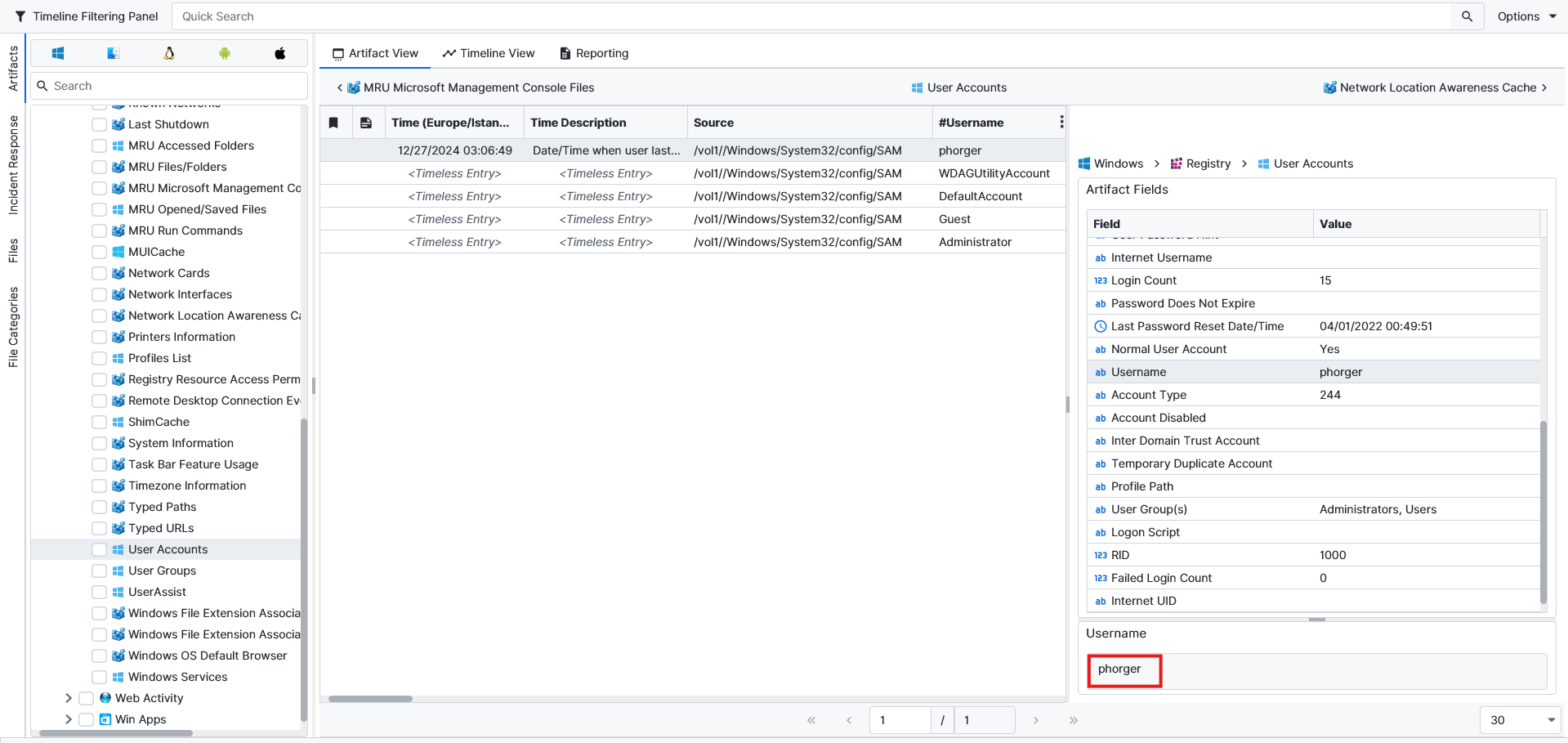
Question: What is the username of the laptop user?
Phorger.The challenge provided us with two pieces of evidence to complete this case. For this question, we need our second piece of evidence. The answer can be found under the User Accounts artifact, which shows the User accounts on the machine.
April Paycheck (Warmup)
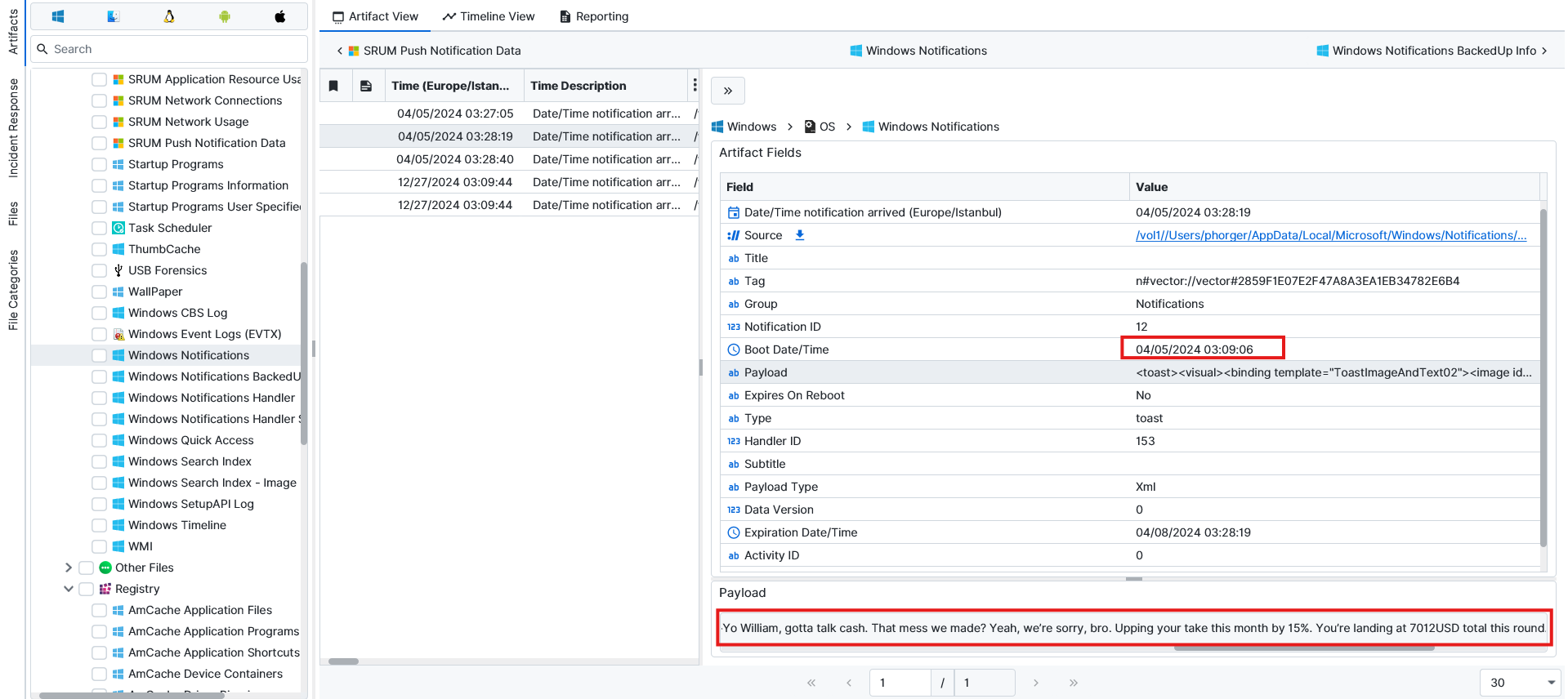
Question: What is the amount of William’s first take in April?
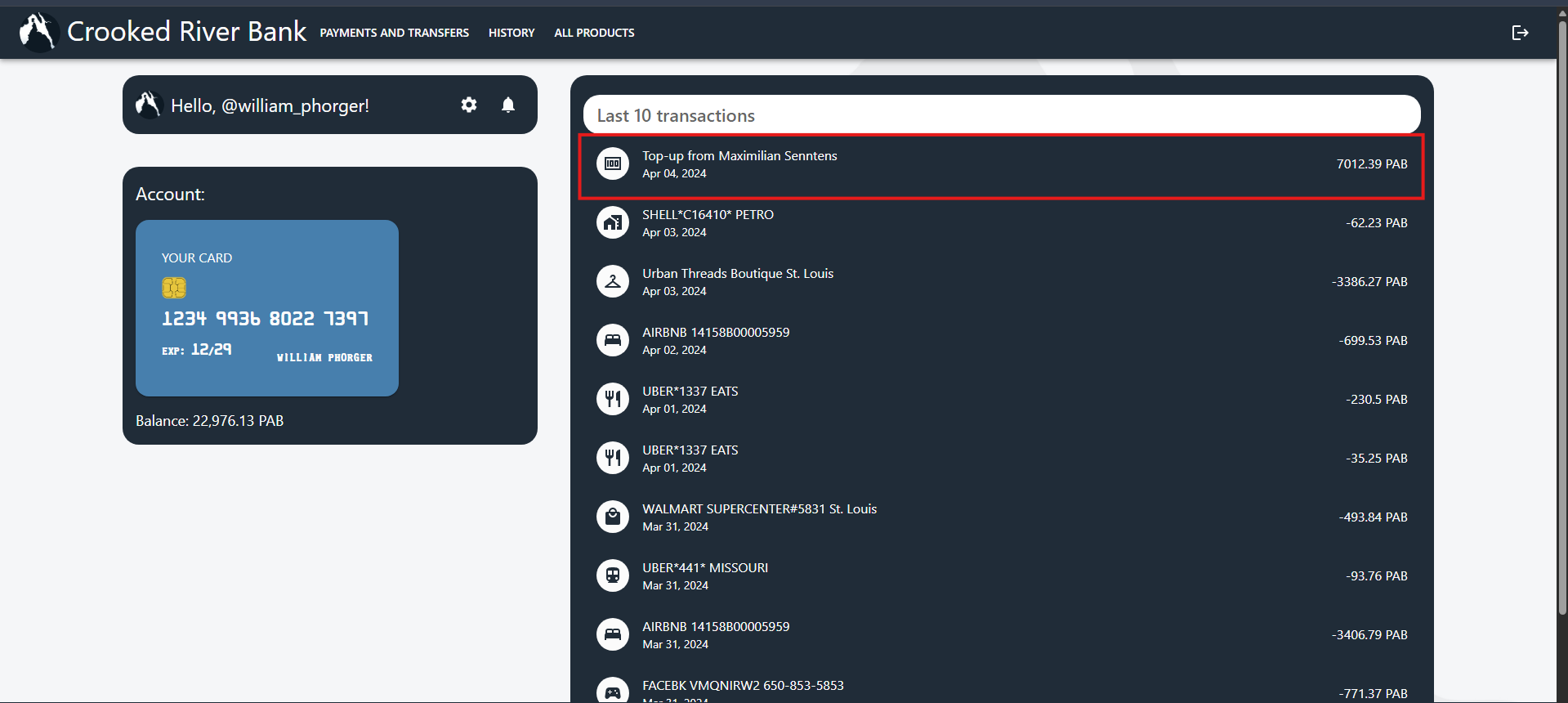
7012. Under the Windows Notifications, there is a message that was received in April. “Yo William, gotta talk cash. That mess we made? Yeah, we’re sorry, bro. Upping your take this month by 15%. You’re landing at 7012USD total this round." From this, we can determine how much he will receive, but there is another way to confirm it.
After searching for a while, I found a PNG with the name Capture2.PNG. This picture shows a bank account and credit card details. Let’s try to log in to the bank’s website.
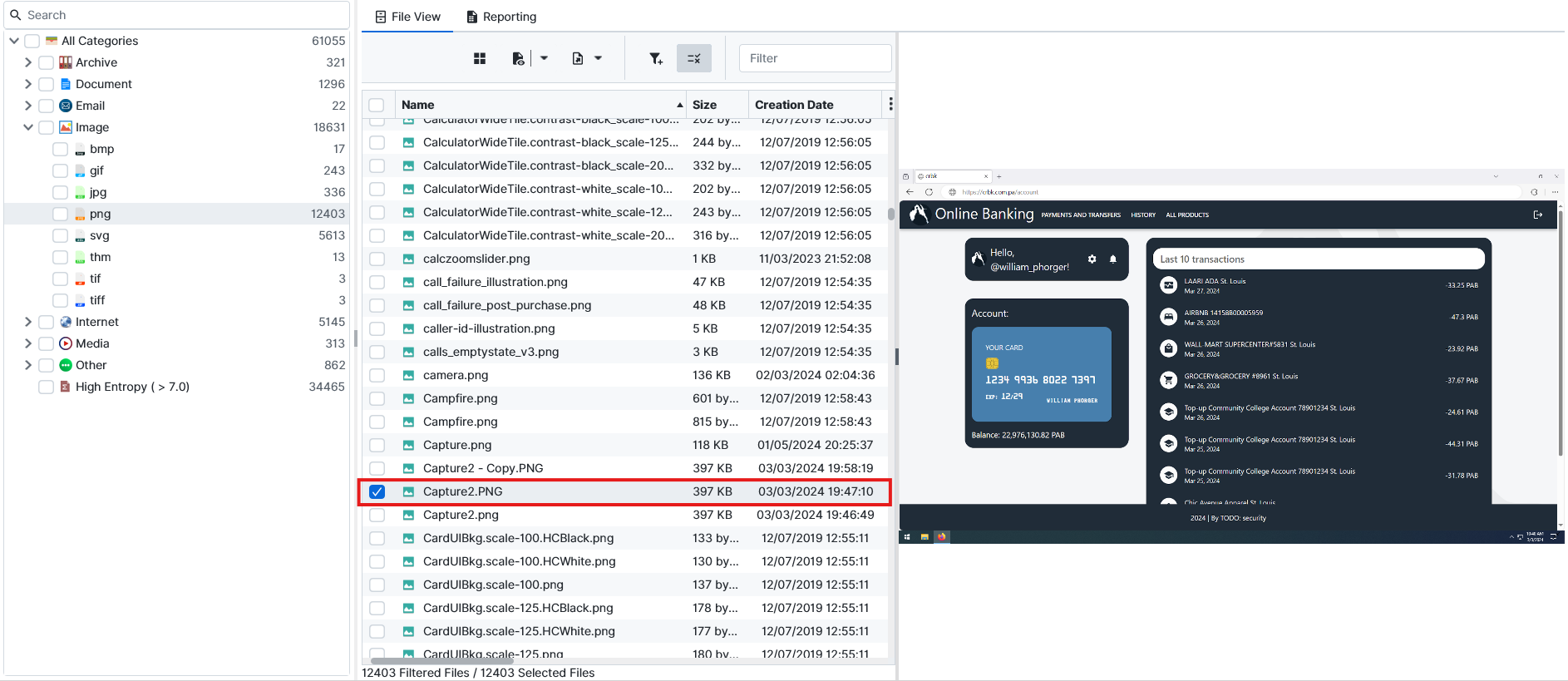
From the picture, we can see the website, but it wasn’t working. After changing and trying different variations, we get a link that actually works. https://crbk.org
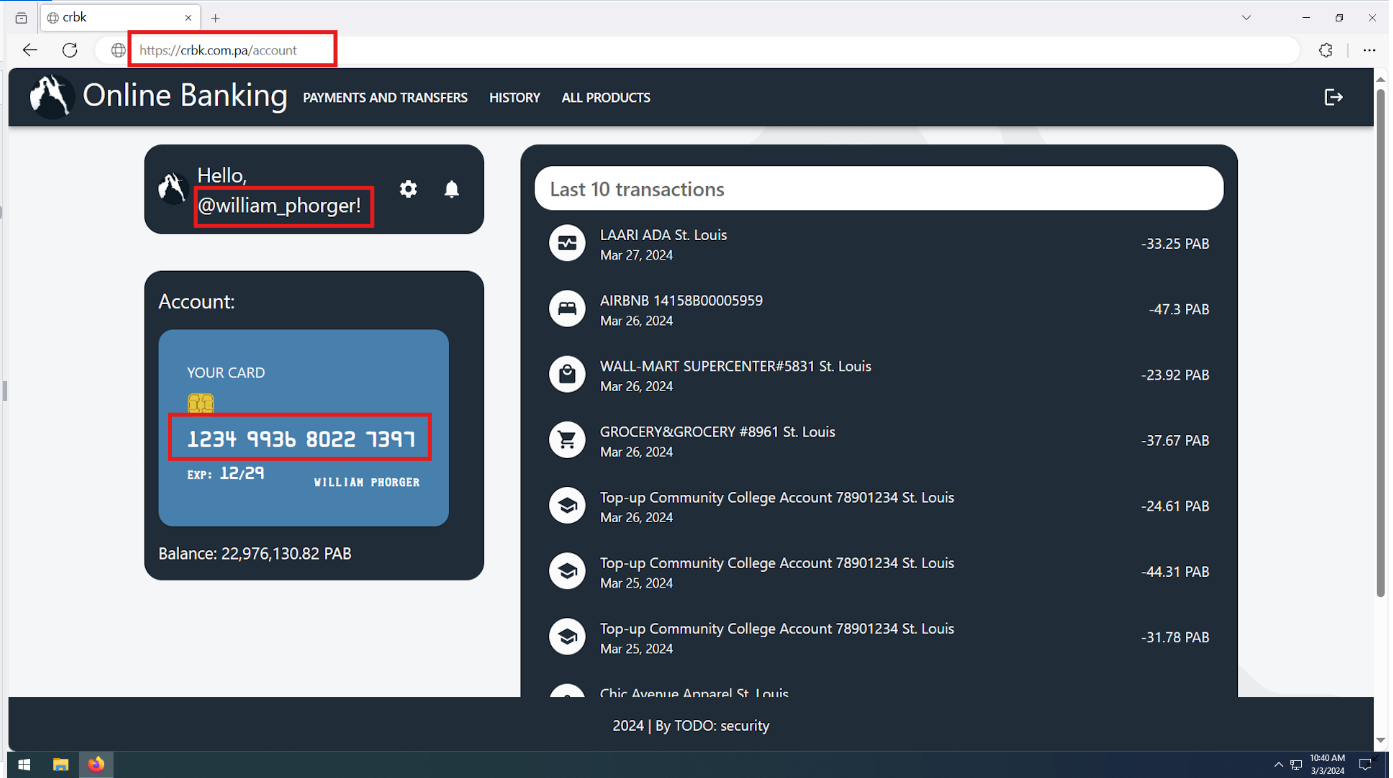
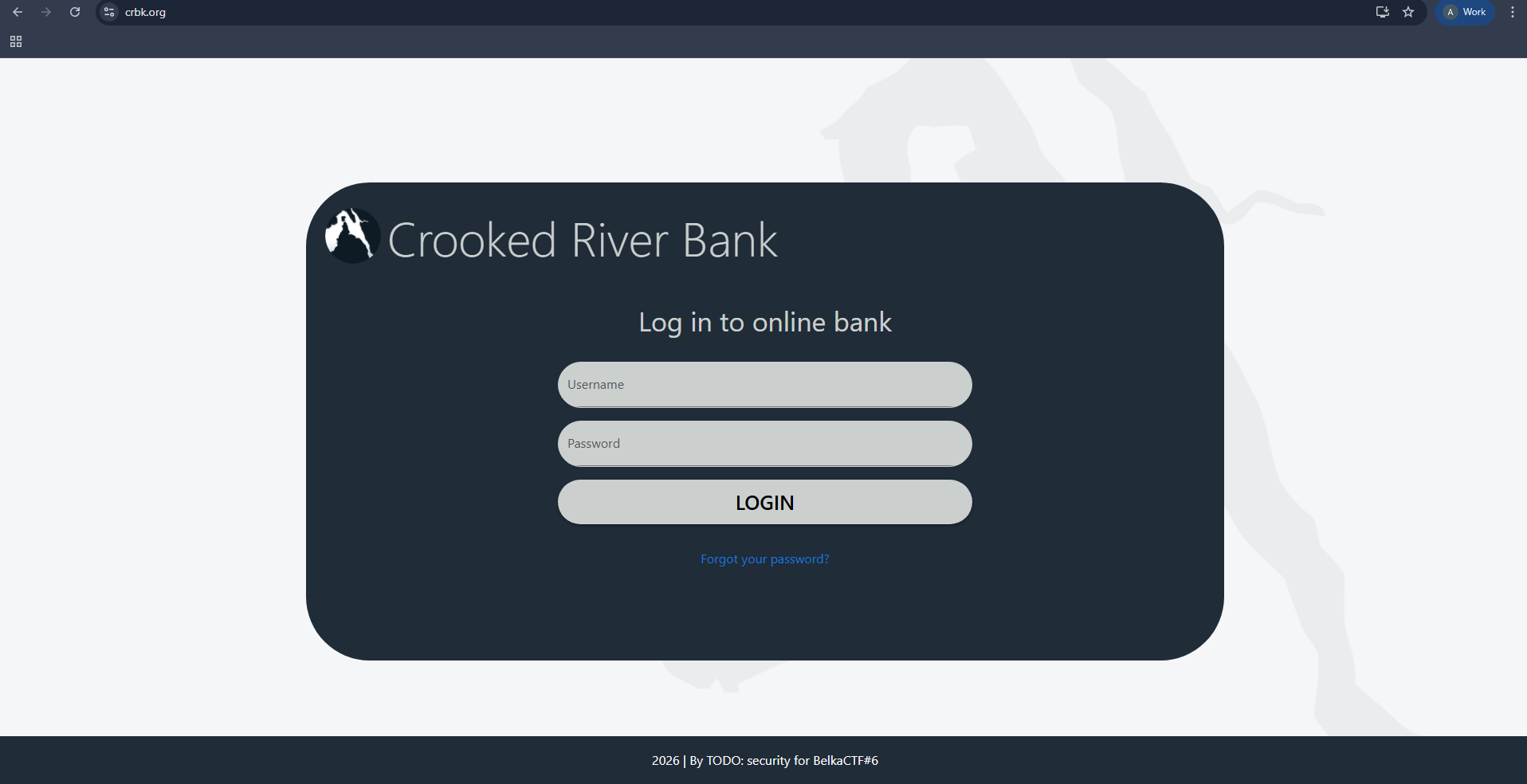
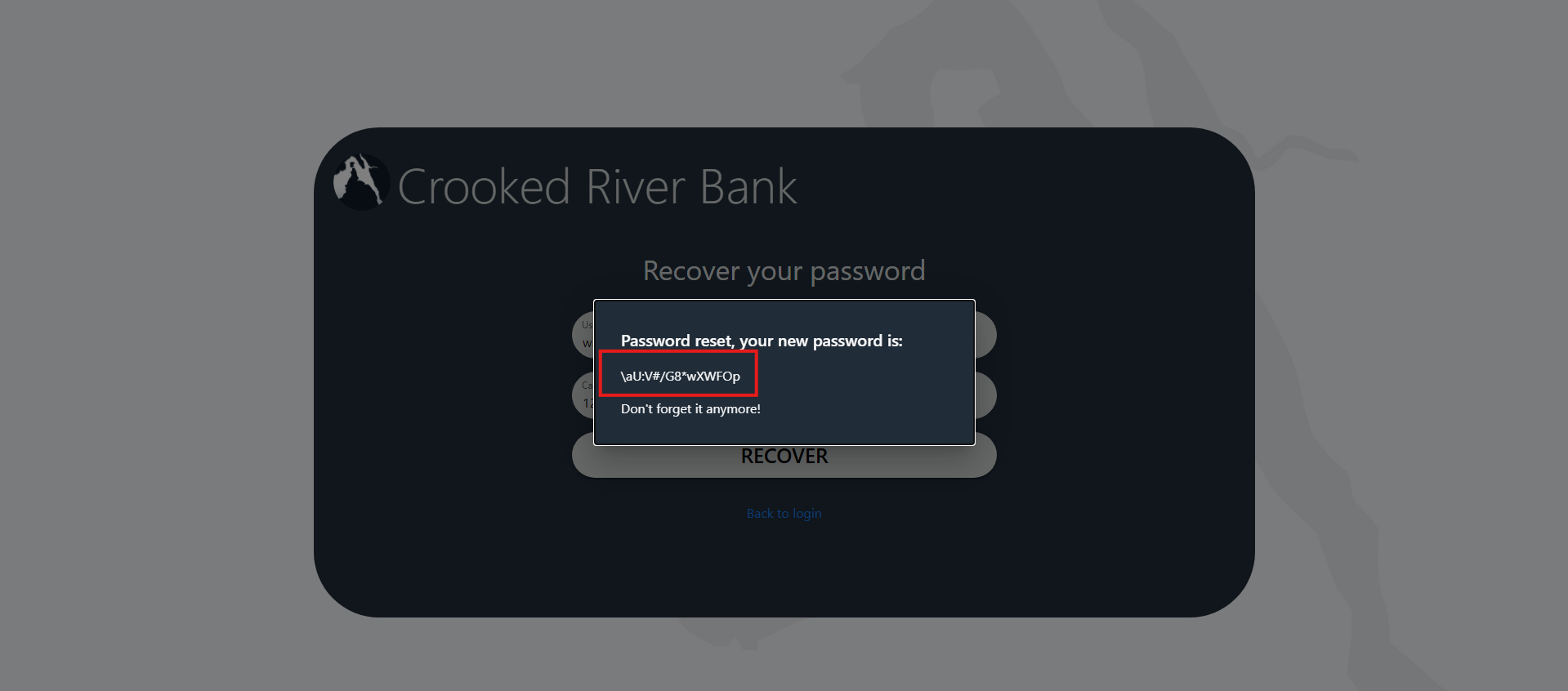
We know the username from the previous image, william_phorger, but not the password, so let’s try to choose forgot password option.
There we go. We have the username and the card number, which is 1234993680227397.
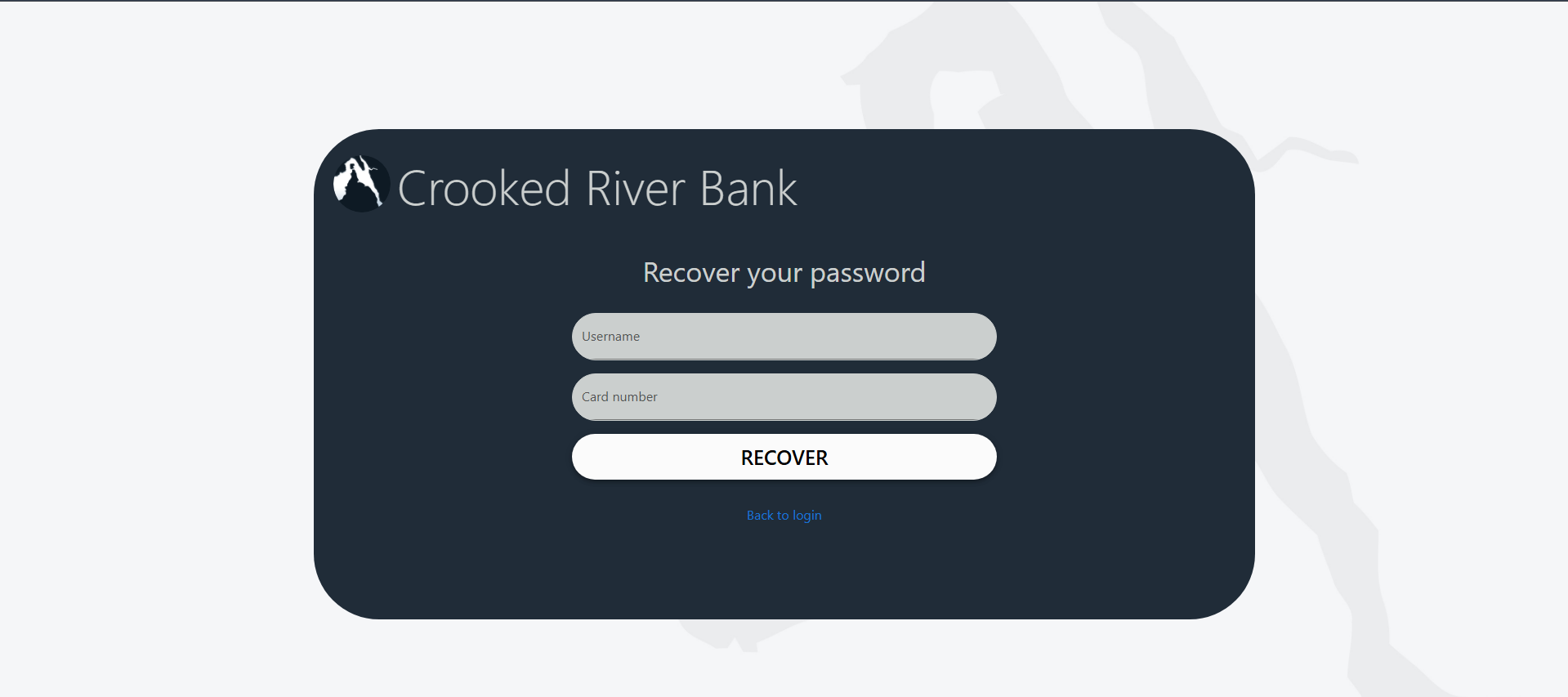
We got a new password to try to log in with. From there, we could see the transaction that was done in April, and it confirms our first guess.
Party (Tricky)
Question: Where did the gang go to celebrate their success together in March? Flag format: latitude, longitude—or just click the map
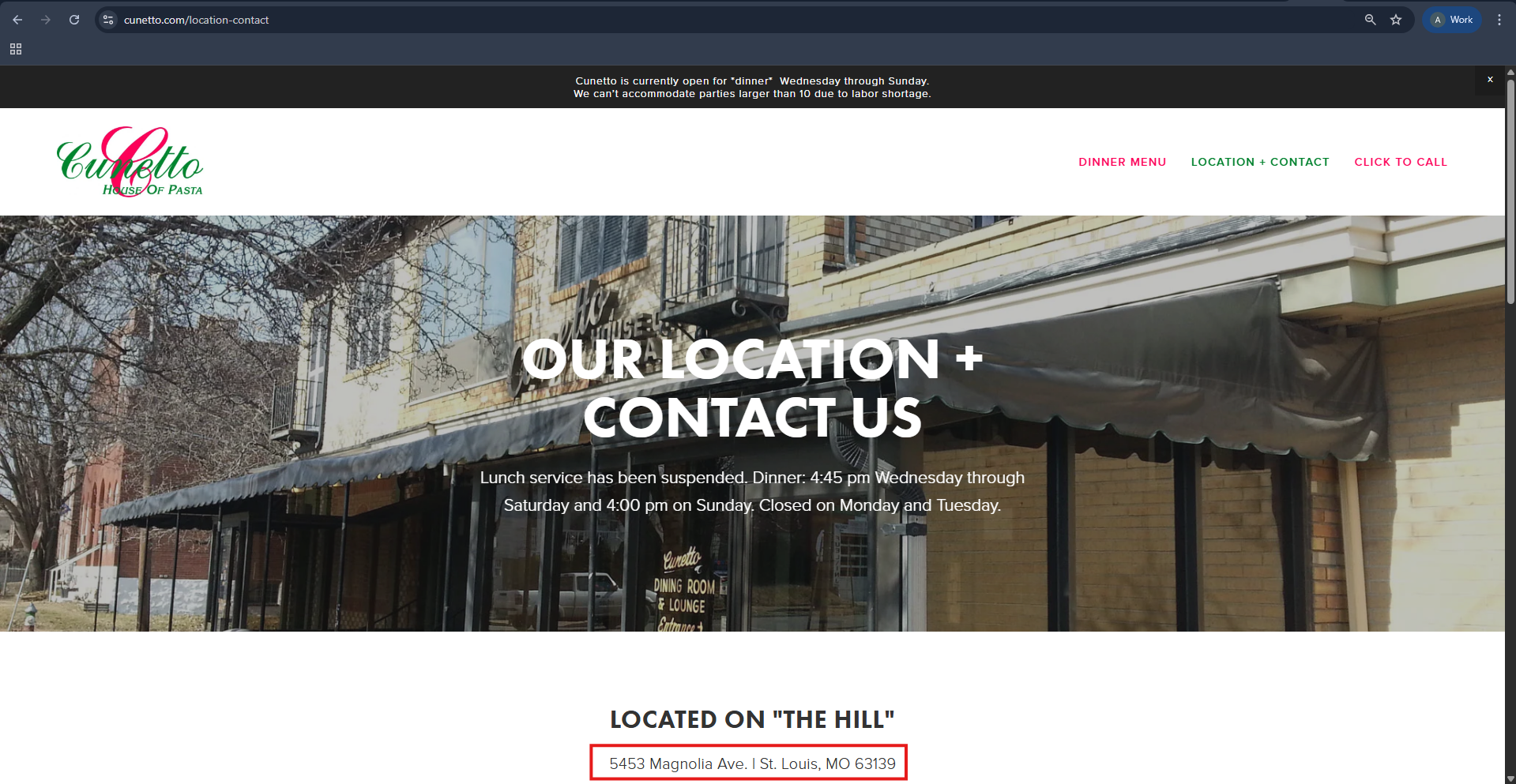
5453 Magnolia Ave, St. Louis.To answer this question, I had to go back to the iOS evidence and read the group chat again. There is a message about them doing a celebration. A couple of hours earlier, they also had a meal, and now we know they use the Splitwise app to split the amount of money they owe each other.
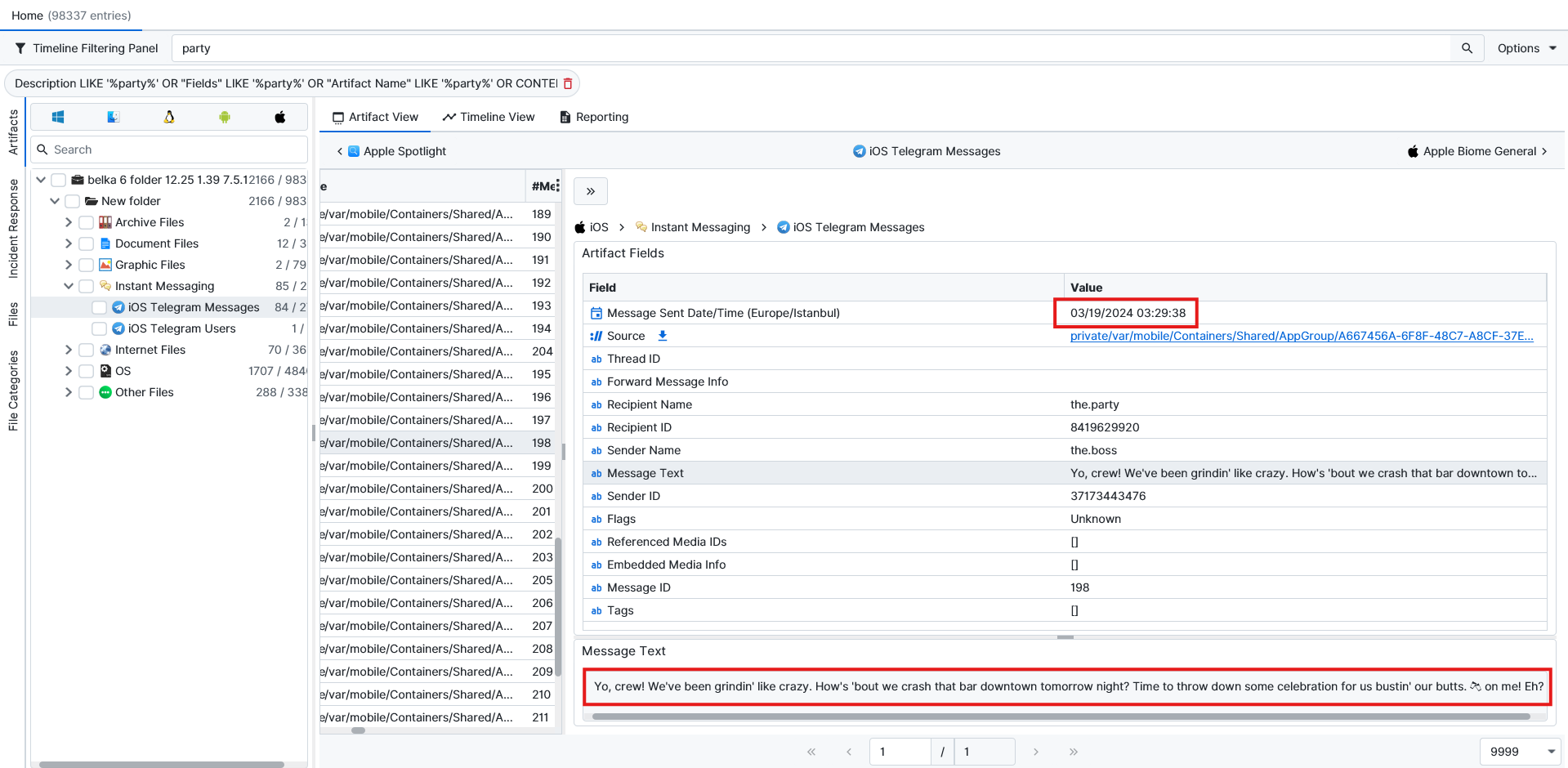
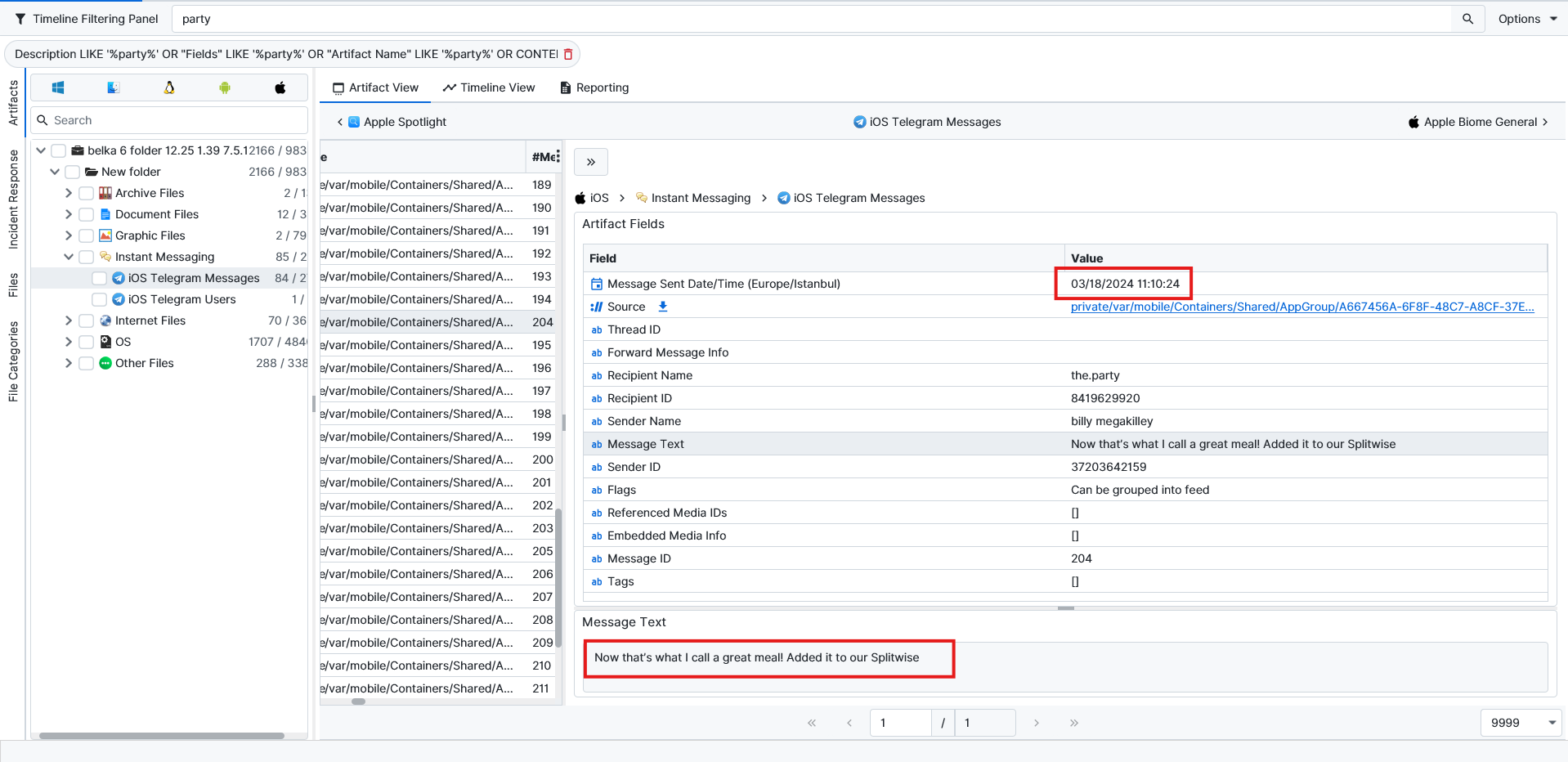
Since they had plans for the day after, it should’ve been on 20th March. ArtiFast has Splitwise artifacts to help us find the answer to this question. We can see that on the exact date, there is a charge of 790 dollars with the title of “Get-together at Cunetto”.
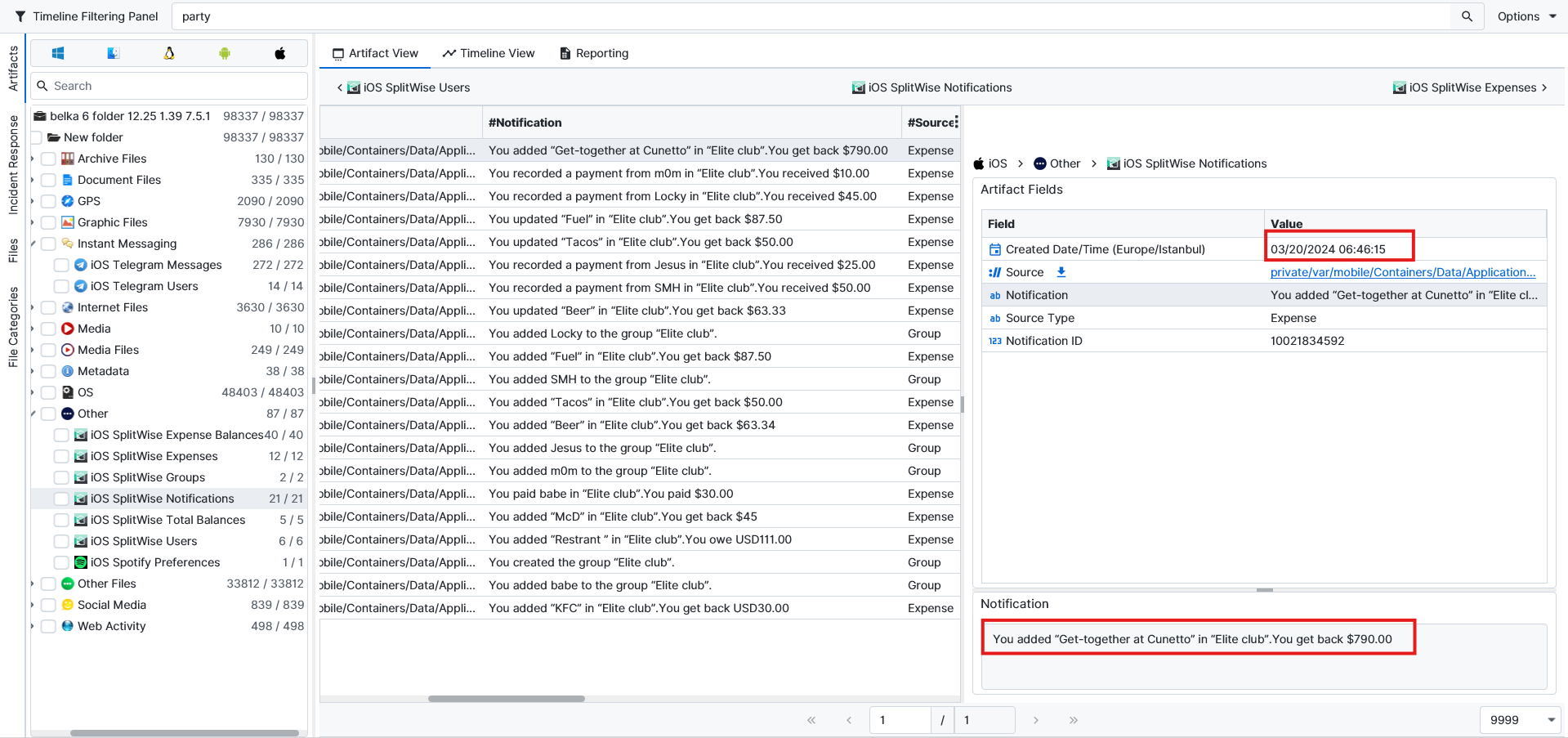
If we search for the name of the place, we can find its location on the internet.
Crypto (Warmup)
Question: Which file does the guy keep his encrypted container in? Flag format: full path, e.g. C:\VeraCrypt\MyContainer.vc
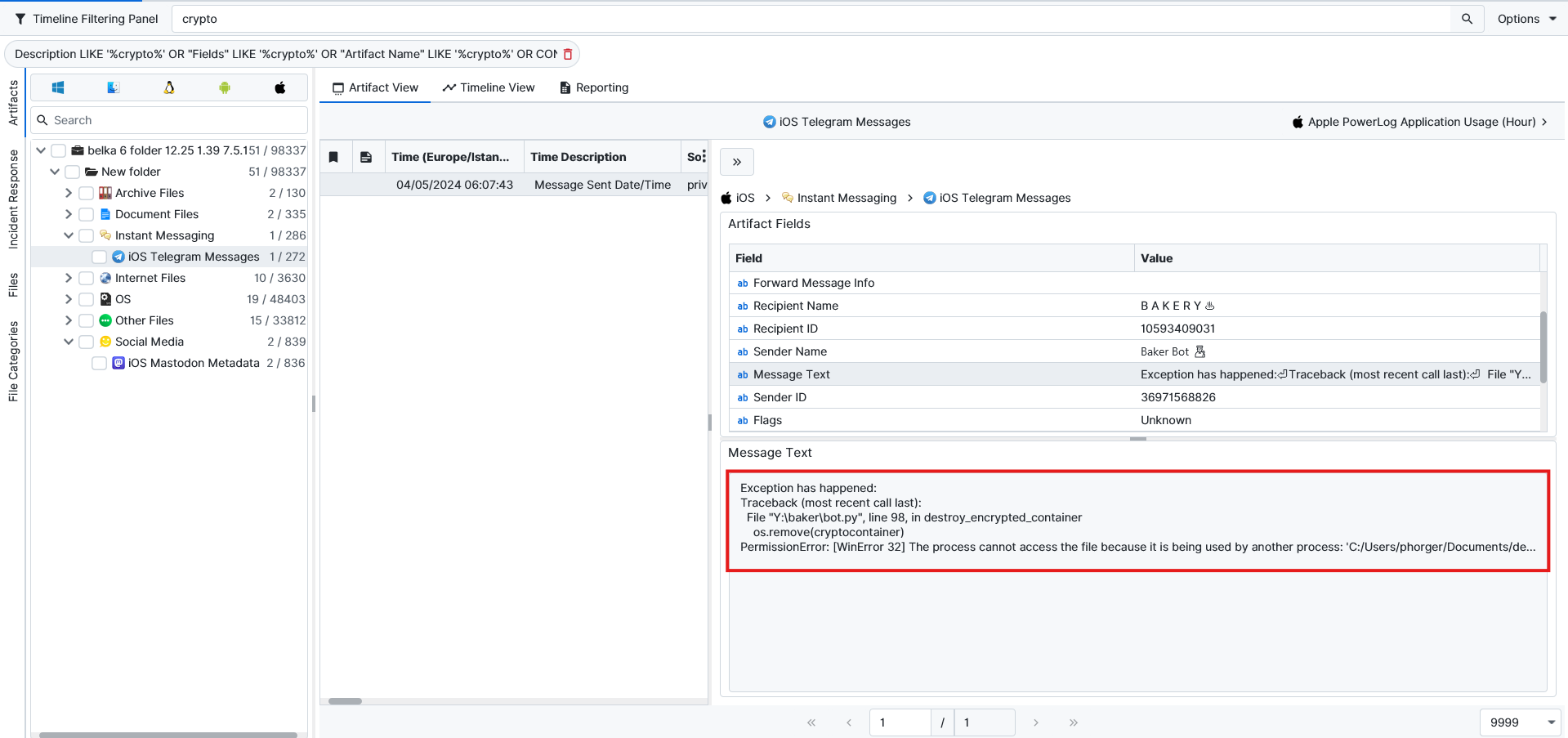
C:\Users\phorger\Documents\desktop.ini:vault.vhdx. I did not know where to start with this question. I just searched for Crypto to see if I could find something. After the filtering, I found one telegram message from a telegram bot with an error message “ [WinError 32] The process cannot access the file because it is being used by another process: 'C:/Users/phorger/Documents/de…”. This could mean something, so I switched back to Windows Evidence to go to the exact path.
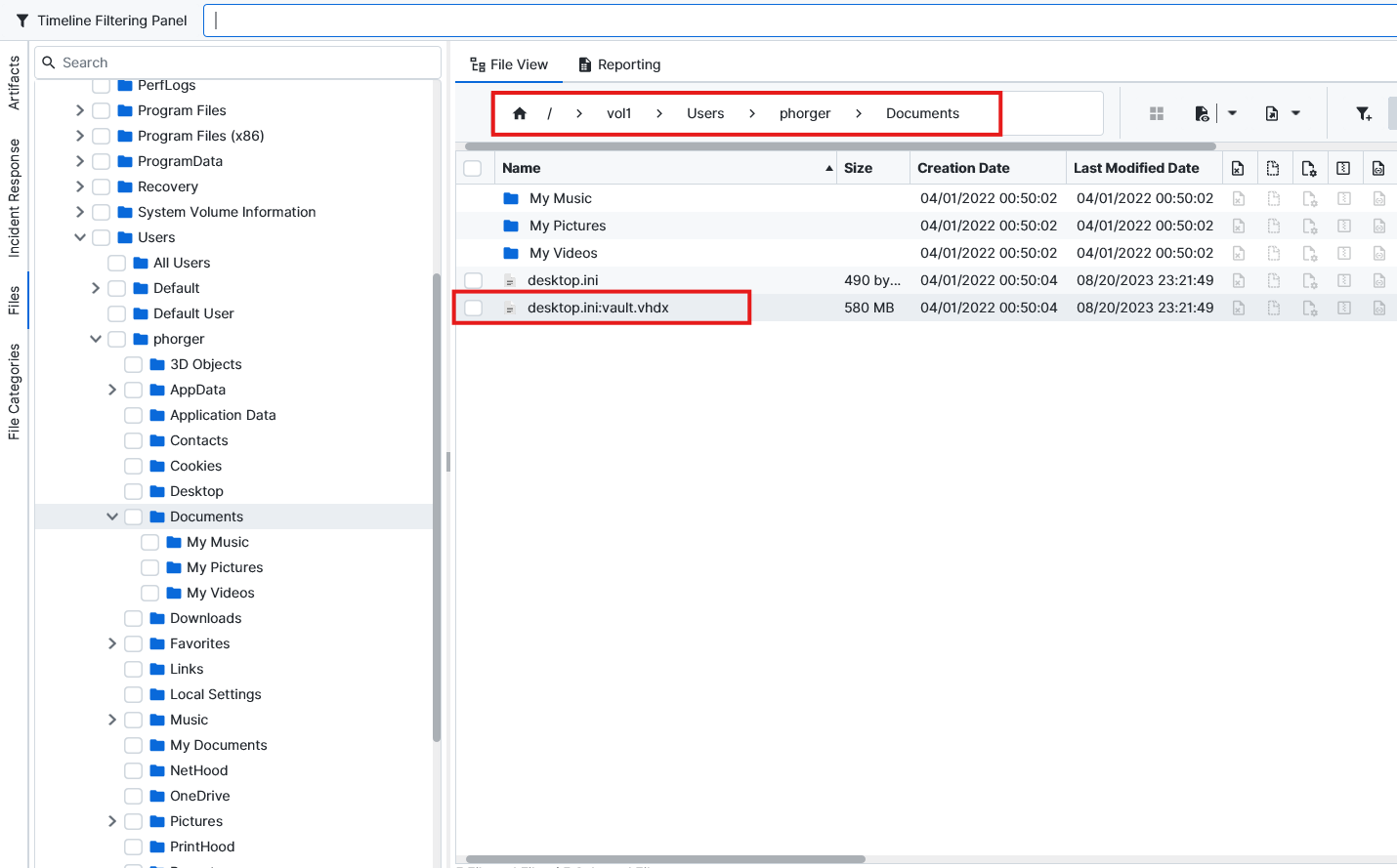
On this path, I found a VHDX file. The name also looks suspicious since it has a vault word in it. So this must be it.
Luxury (Warmup)
Question:Which luxurious item did Phorger put his laundered money into? Flag format: full name incl. any codes, e.g. Bugatti Chiron BG744
Rolex Submariner Date ref 126619LB.Let’s try to check inside the vault that we found in the previous question. Unfortunately, since it’s encrypted, we need to find the keys first. Let’s try to search for the word BitLocker on both evidence and see if we can find something.
And there it is. We find it inside the Apple Notes artifact. Now that we have the key for it let’s mount
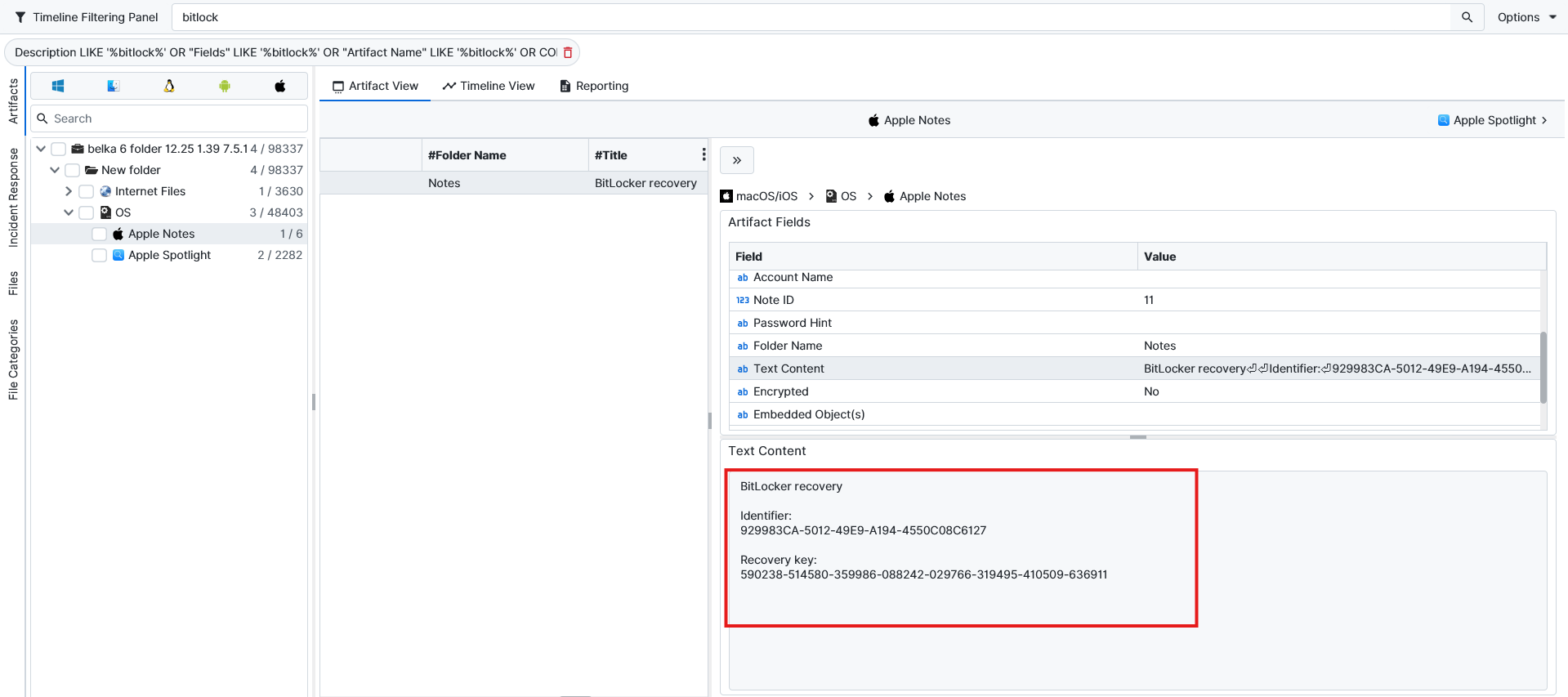
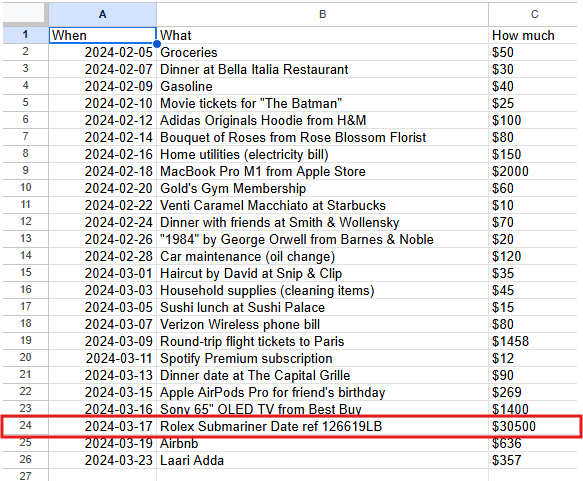
After opening the mounted drive, we see a file called spending.xlsx. When we take a look at it, we see a list of items he has purchased. The answer should be Rolex Submariner Date ref 126619LB since it’s the most expensive item.
Vacation (Tricky)
Question: Which concert were Phorger and his girlfriend planning to attend in May? Format: artist, venue, city, e.g. Taylor Swift, Friends Arena, Stockholm
Eric Clapton, Accor Arena, Paris.First, I searched for a vacation to see if I could find something on evidence. The only result I found that could be interesting is the chat between the @diddyflowers user about deleting everything about their May plan.
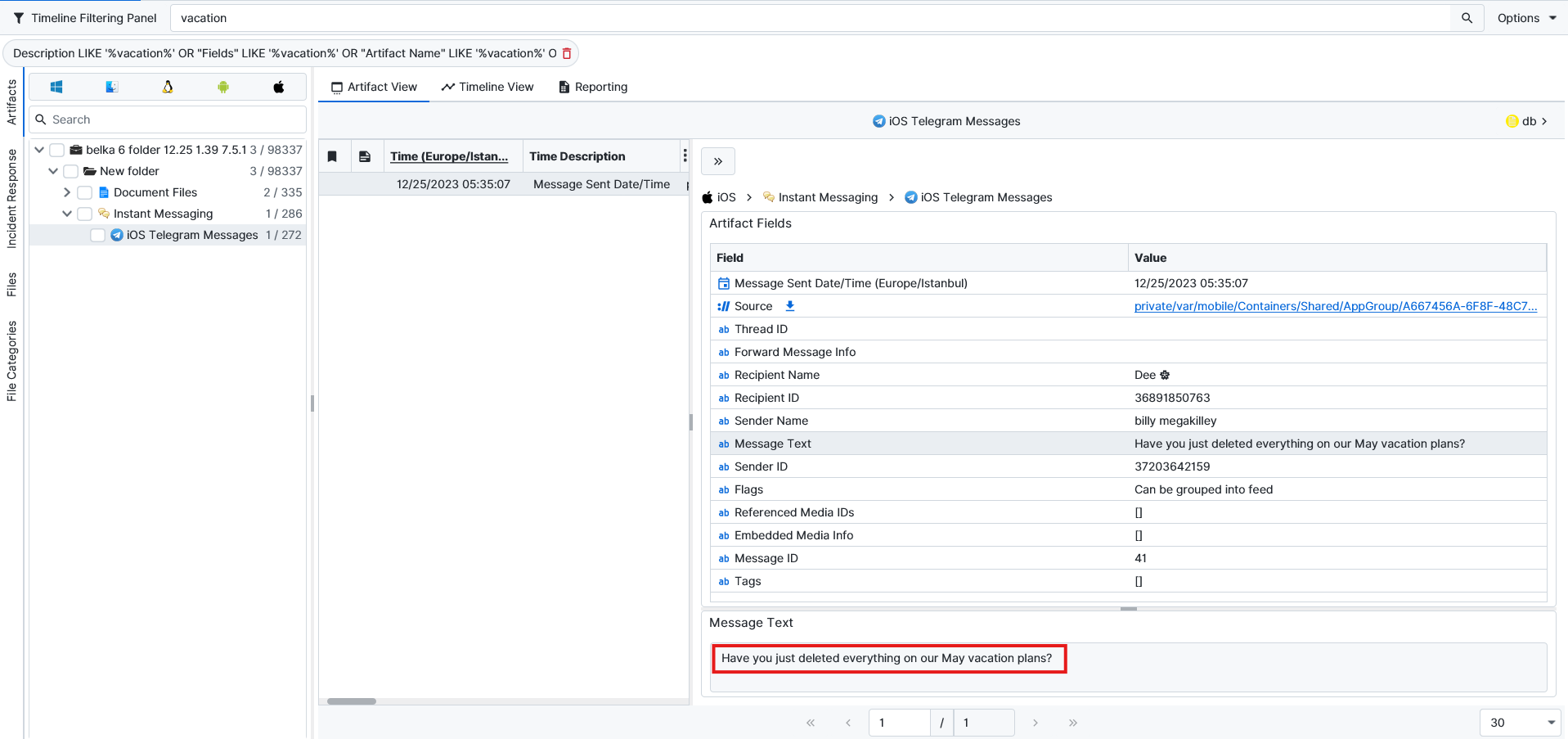
After searching a bit more, I noticed from web history that they also had conversations on the Telegram web version. So I tried to find the cache folder to see if there was anything left there.
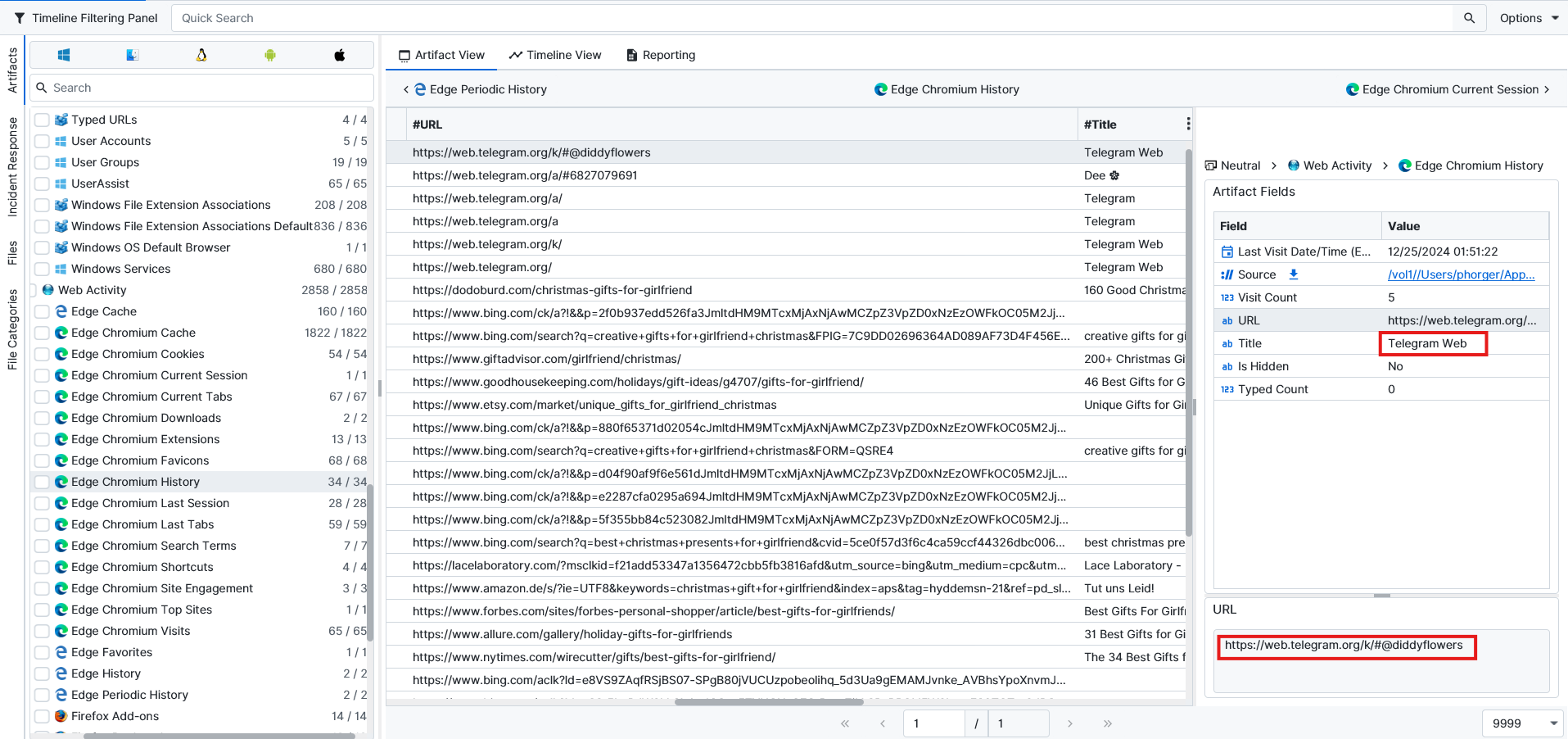
I found that it’s stored at C:\Users\phorger\AppData\Local\Microsoft\Edge\User Data\Default\Service Worker\CacheStorage. I searched more and found the cache files, then exported them to analyze more using Chromecacheview tool.
There were some pictures among all the files. After I exported them and checked them one by one, we found our answer. The Eric Clapton concert in Paris.

Illustrator (Warmup)
Question: What's the name of the person who designed the print template for the bills? Flag format: First name Last name
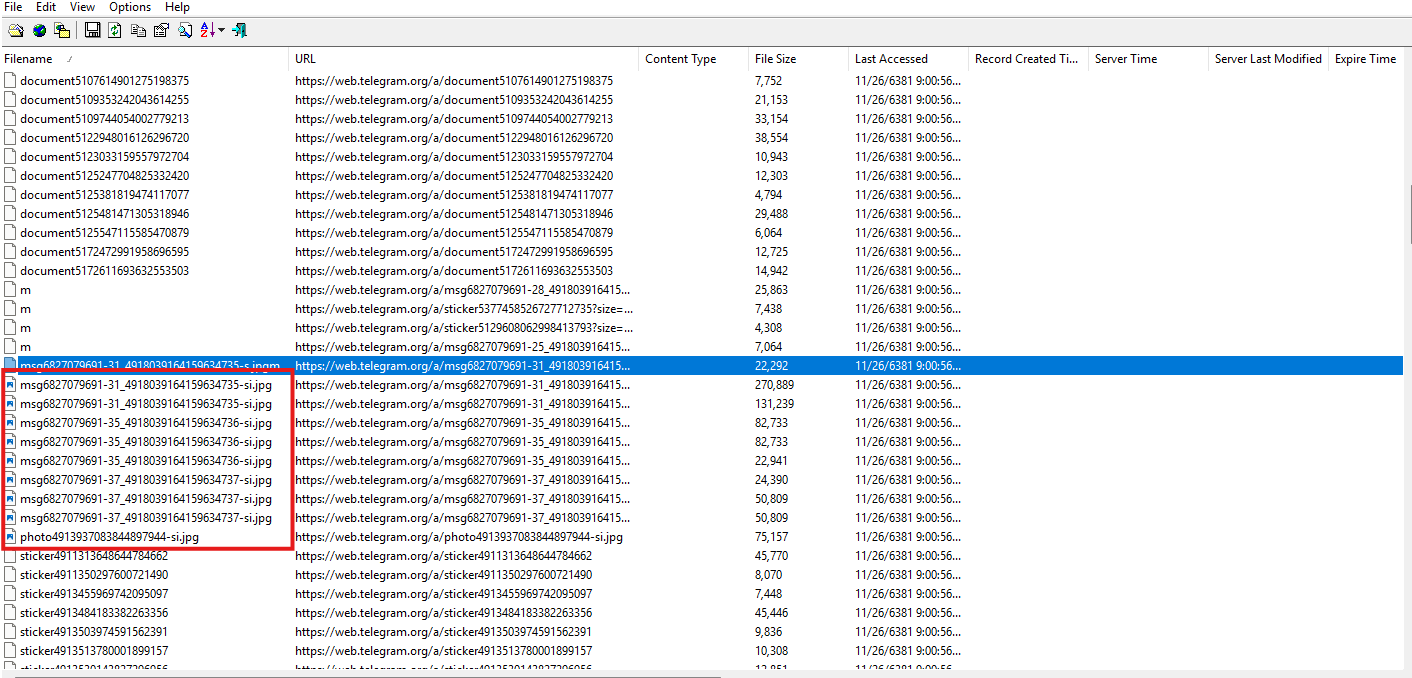
Drew Linesworth .When we search for design in the beginning, we get to see who the designer is. It’s someone called Drew, or known as diddyflowers, who is also the girlfriend of our user.
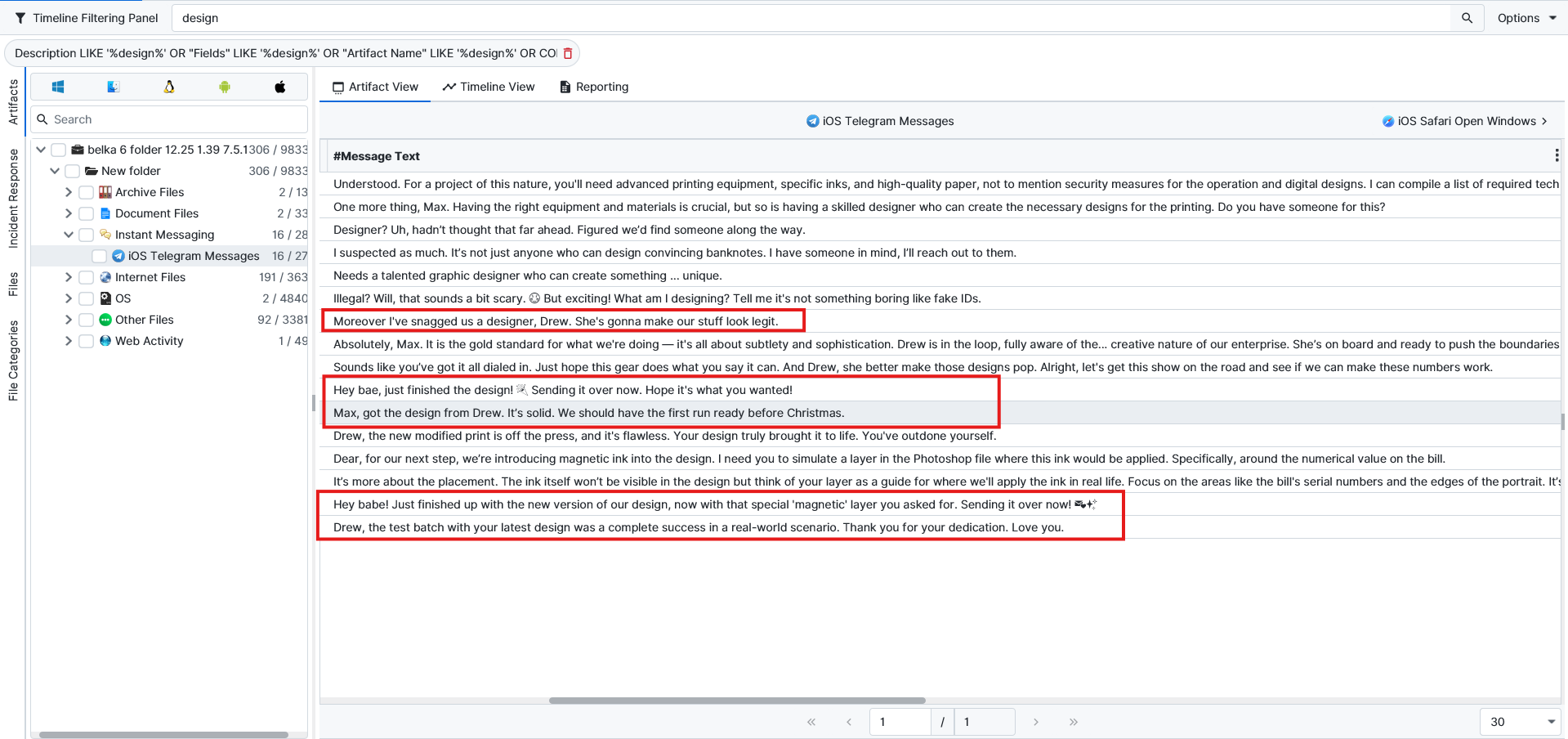
She said that she was sending the design over Telegram. From the telegram, we could see that the file name is Test Run.psd. Then I searched all over the evidence to find it; however, there was no sign of it.
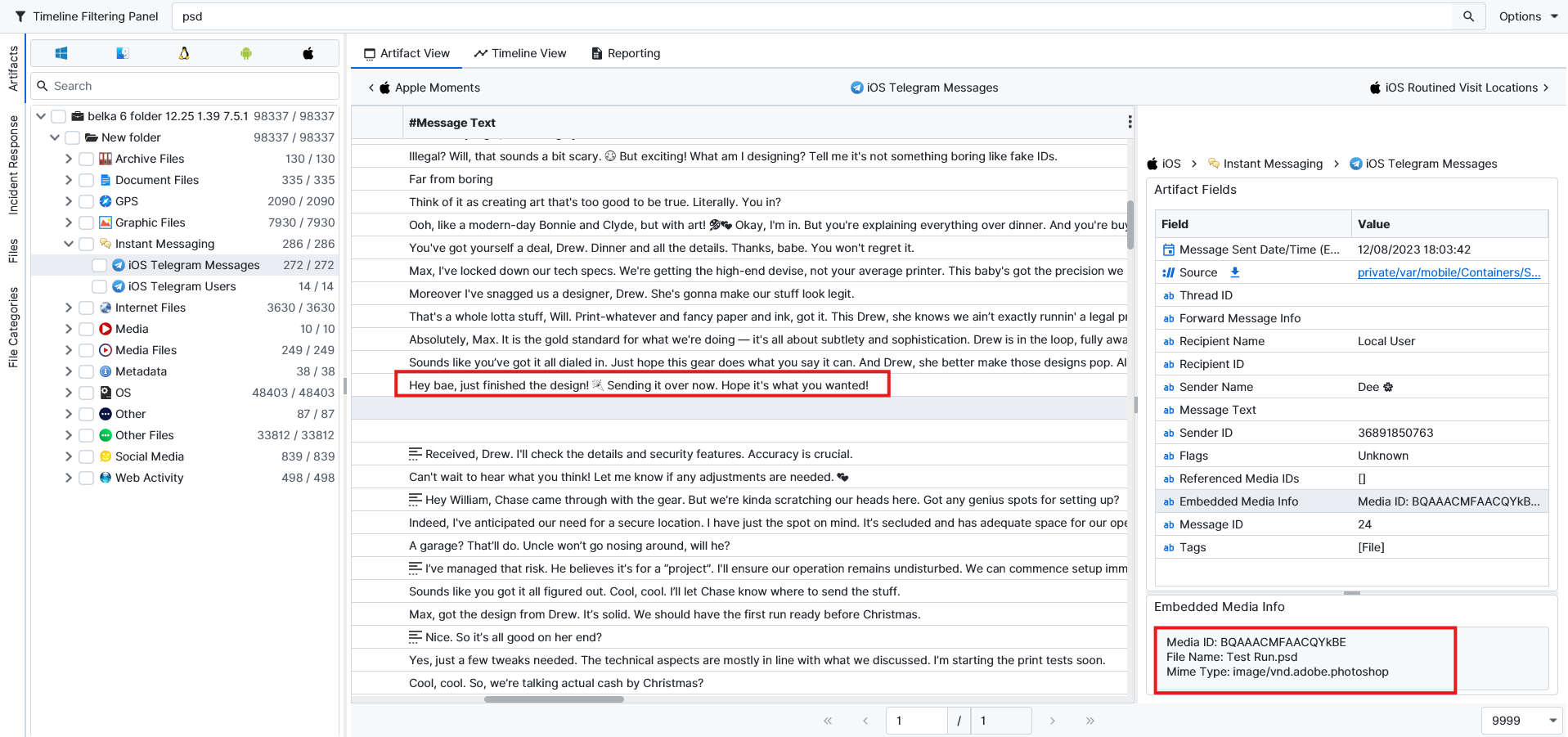
So I tried to look for it on the mounted drive. There was a PSD file inside the drive located at I:\baker\presets\1.psd
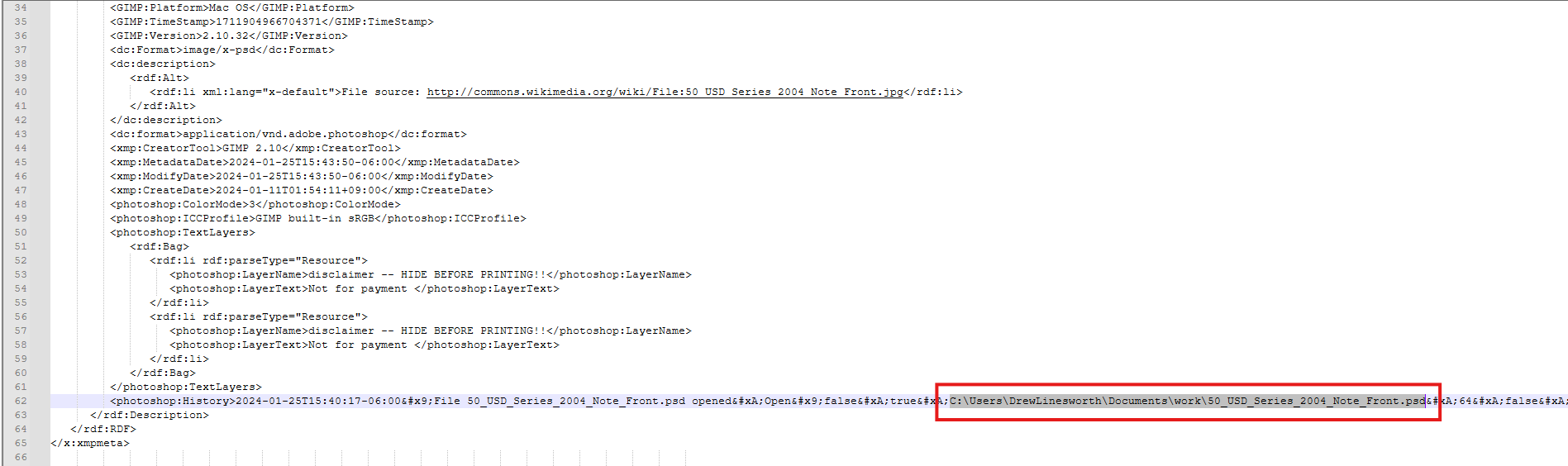
From the information inside the 1.psd, we can see that it is designed for money, and the designer is Drew Linesworth
Homebrew Lab (Tricky)
Question: Where is the makeshift lab where they printed the cash located? Flag format: full address, e.g. 314 S Main St, Kirksville, MO
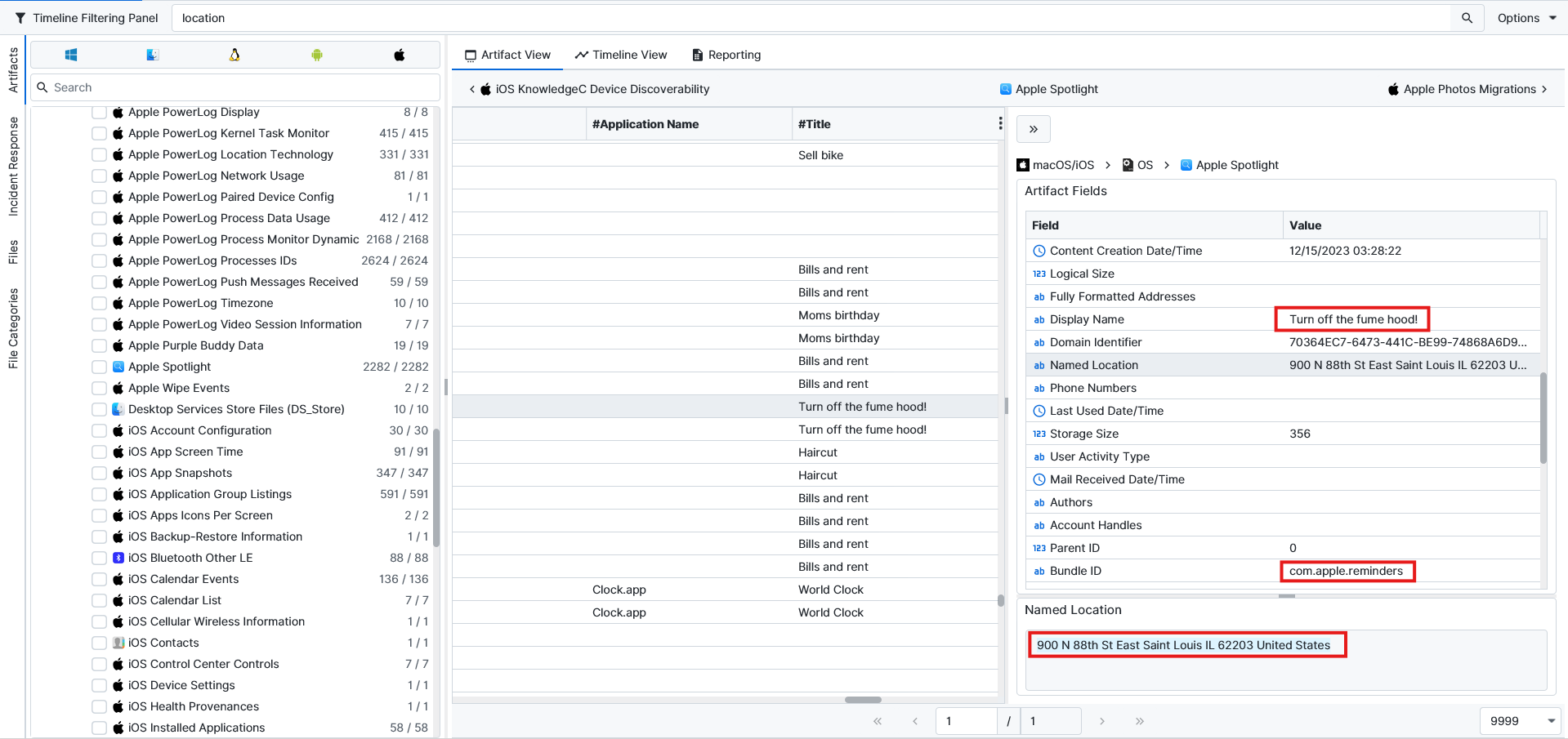
900 N 88th St, East St Louis, IL.To find the answer to this question, I looked at all the location info to see if there were any hints there. While searching, I found an interesting clue about reminders inside the Apple Spotlight artifact. A reminder was set to “Turn off the Fume hood”. Fume hoods are used in chemical operations and are not found in every place. There is a location attached to the reminder, which is our answer.
Largest Batch (Warmup)
Question: What is the precise moment their largest printing batch was completed? Provide exact timestamp in a common format, e.g. 2023-07-17 17:07:07 UTC
02.04.2024 22:44:30 UTC. Inside the mounted drive, there is a Python script called bot.py. When we open it we can see that it is the source code of the Telegram bot that was being used for baking money.
Seems like the number of the cakes is the amount of money, and when it finishes the operation successfully, it gives a message saying “They're hot and steaming fresh out the oven, enjoy 😋”.
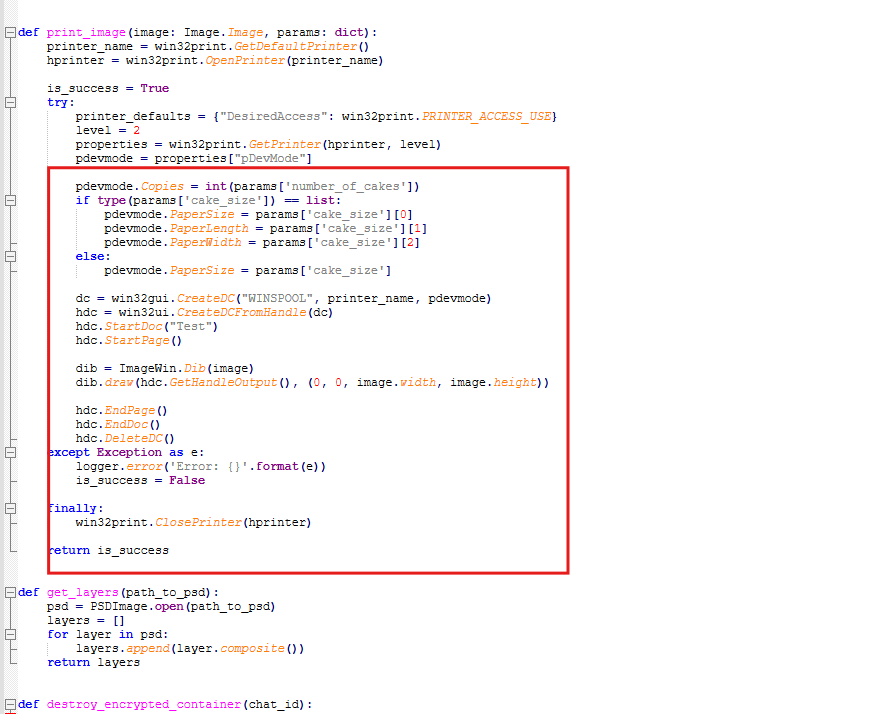
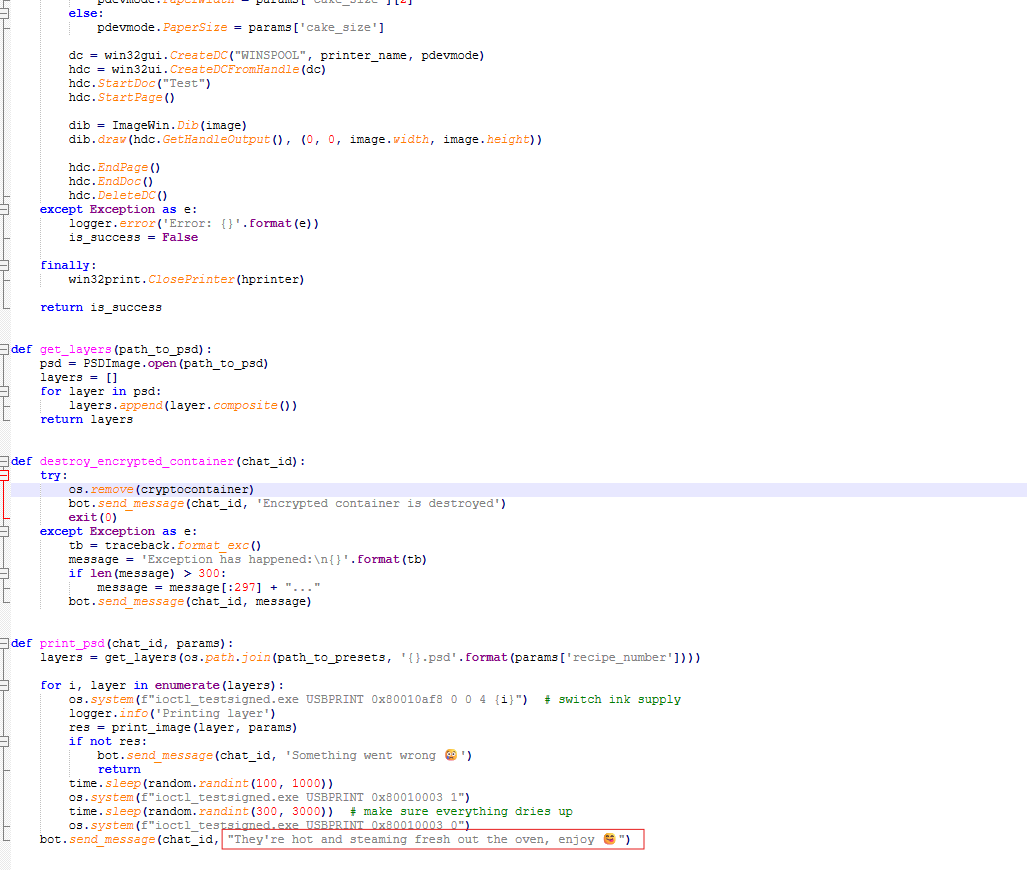
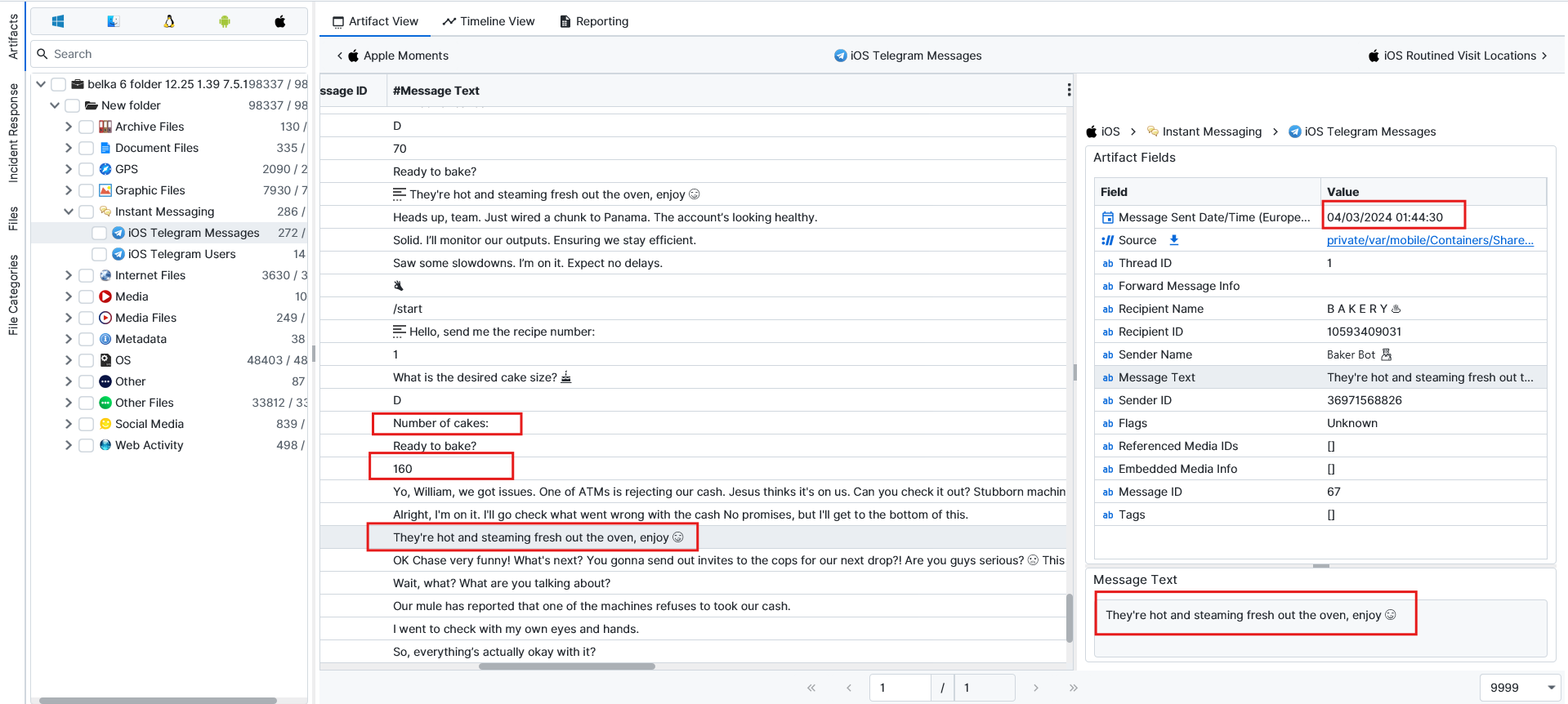
Now, if we go back to the telegram messages, we can see the highest number given for the number of cakes is 160, which was done successfully. The time is 04/03/2024 01:44:30 (Europe/Istanbul) or 02/04/2024 22:44:30 UTC
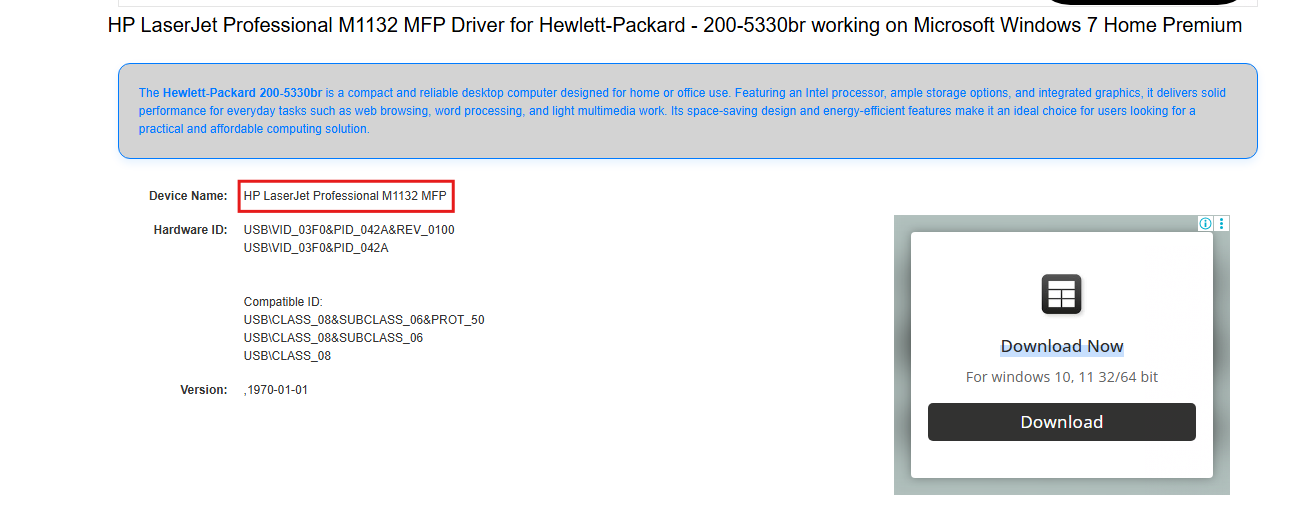
Device (Tricky)
Question: What's the printer model they used to print money? For example, Canon Color imageCLASS MF656Cdw
HP LaserJet Professional M1132 MFP.To find the answer to this question, we can check the USB Forensics artifact. From there, we can see the devices connected to our evidence machine.
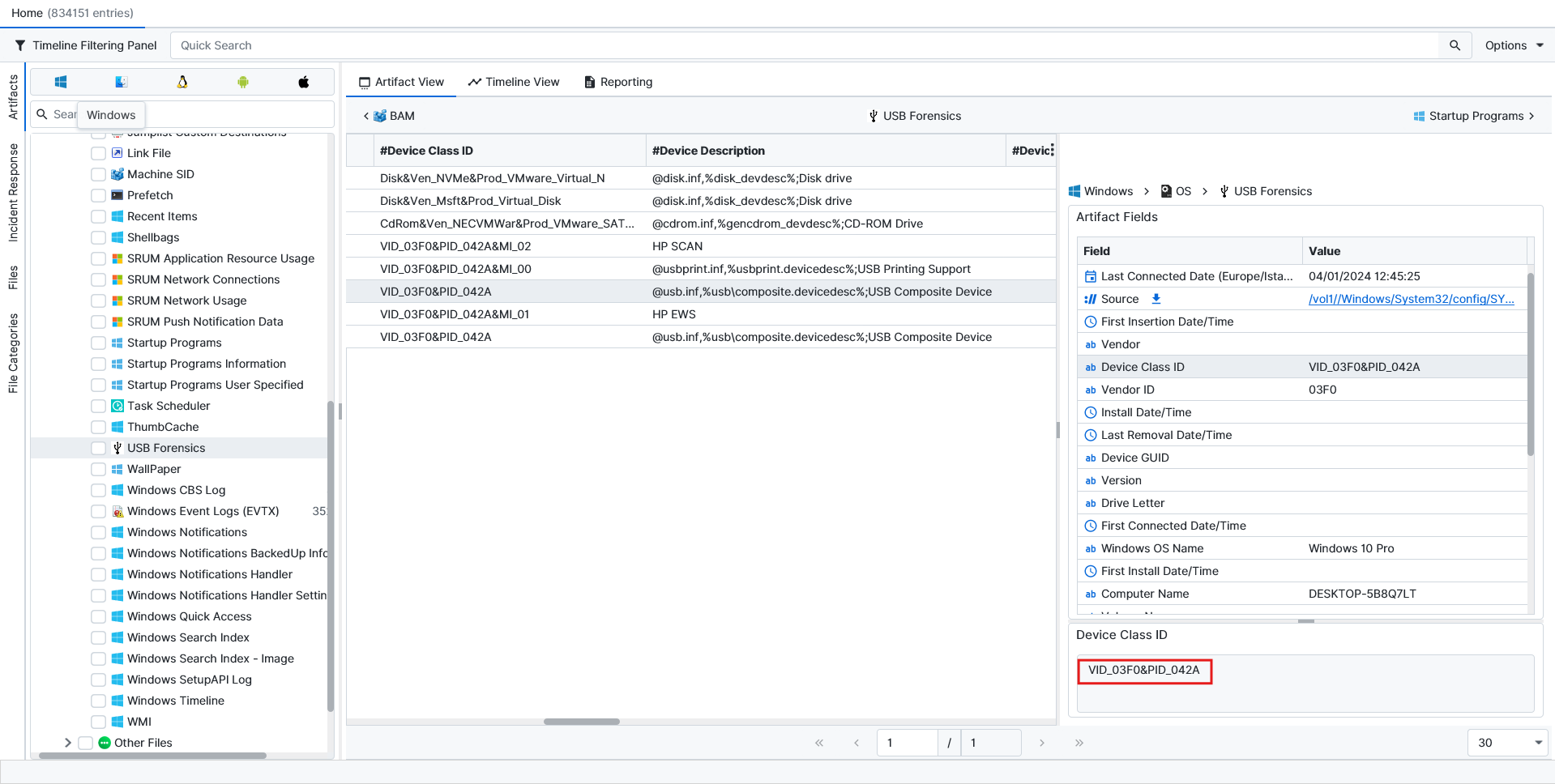
If we search for the device ID on the internet, we get the model for the printer.
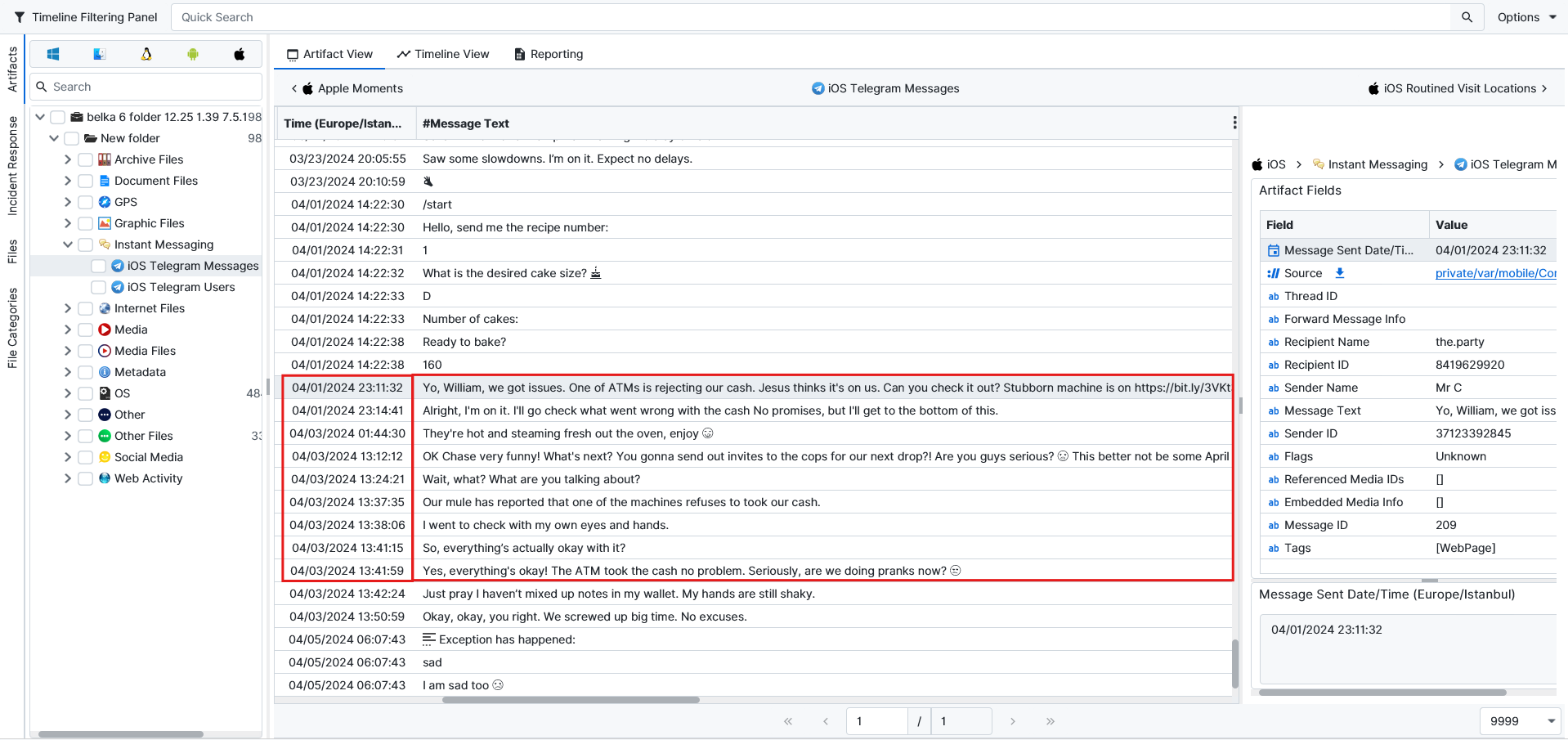
Night Shift (Tricky)
Question: Which ATM did Phorger test his bills on recently? Flag format: bank and street name, e.g. Chase ATM on S Main St
Regions Bank ATM on Delmar Blvd. The Telegram messages indicate that an ATM rejected the counterfeit money, after which Phorger was asked to test it. The date was 04/01/2024 23:11:32 (Europe/Istanbul), and in the following messages, Phorger confirms that he tested it on 04/03/2024 13:41:59 (Europe/Istanbul).
If we check what has happened in between these times, we can see that there is a WiFi connection from Apple Known Wi-Fi Networks.
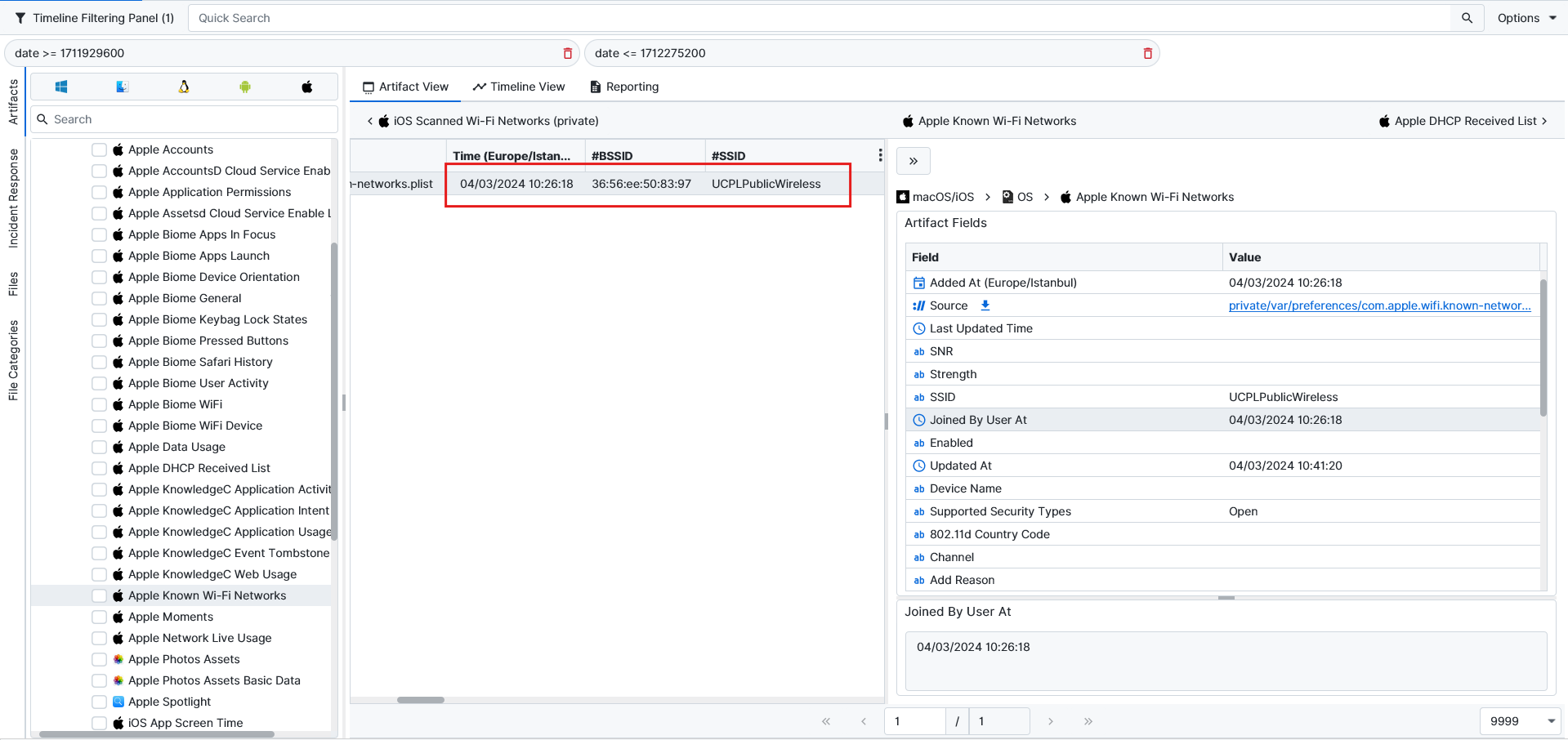
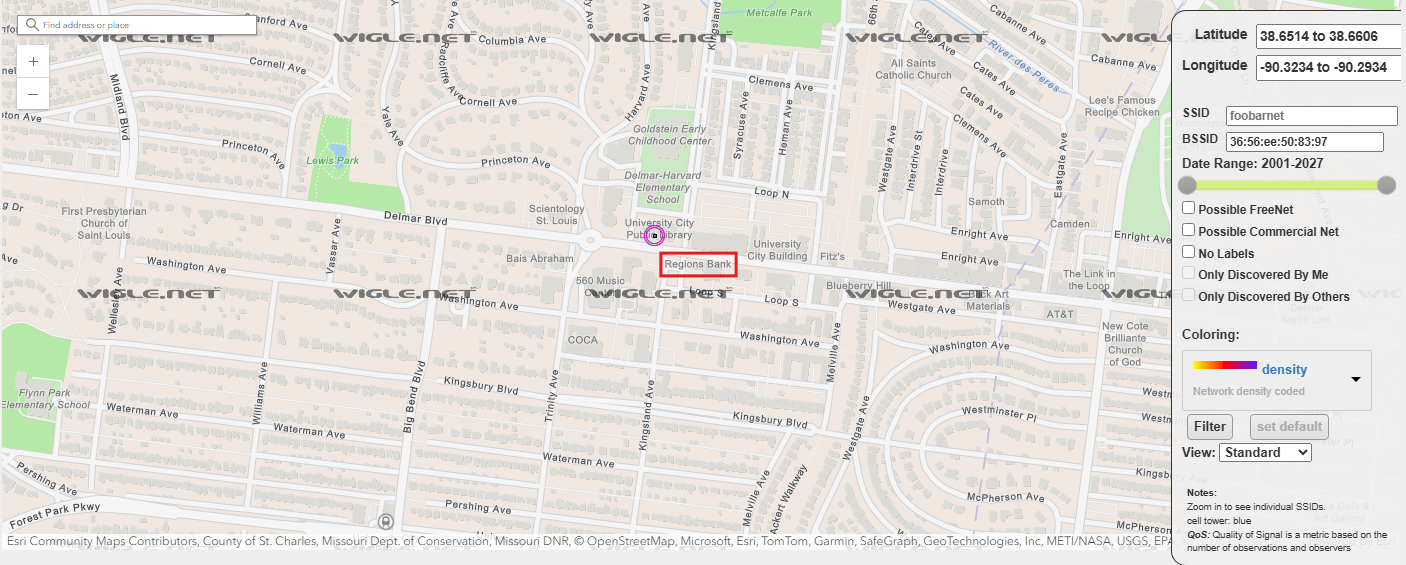
By searching the BSSID of the network, we can navigate and find the location. It’s the University City Public Library. When we check more, we see there is only one bank close to the Wi-Fi, and that is Regions Bank ATM on Delmar Blvd
Mole (Hard)
Question: Who leaked the technical data on the bill validator to the gang? Flag format: First name Last name
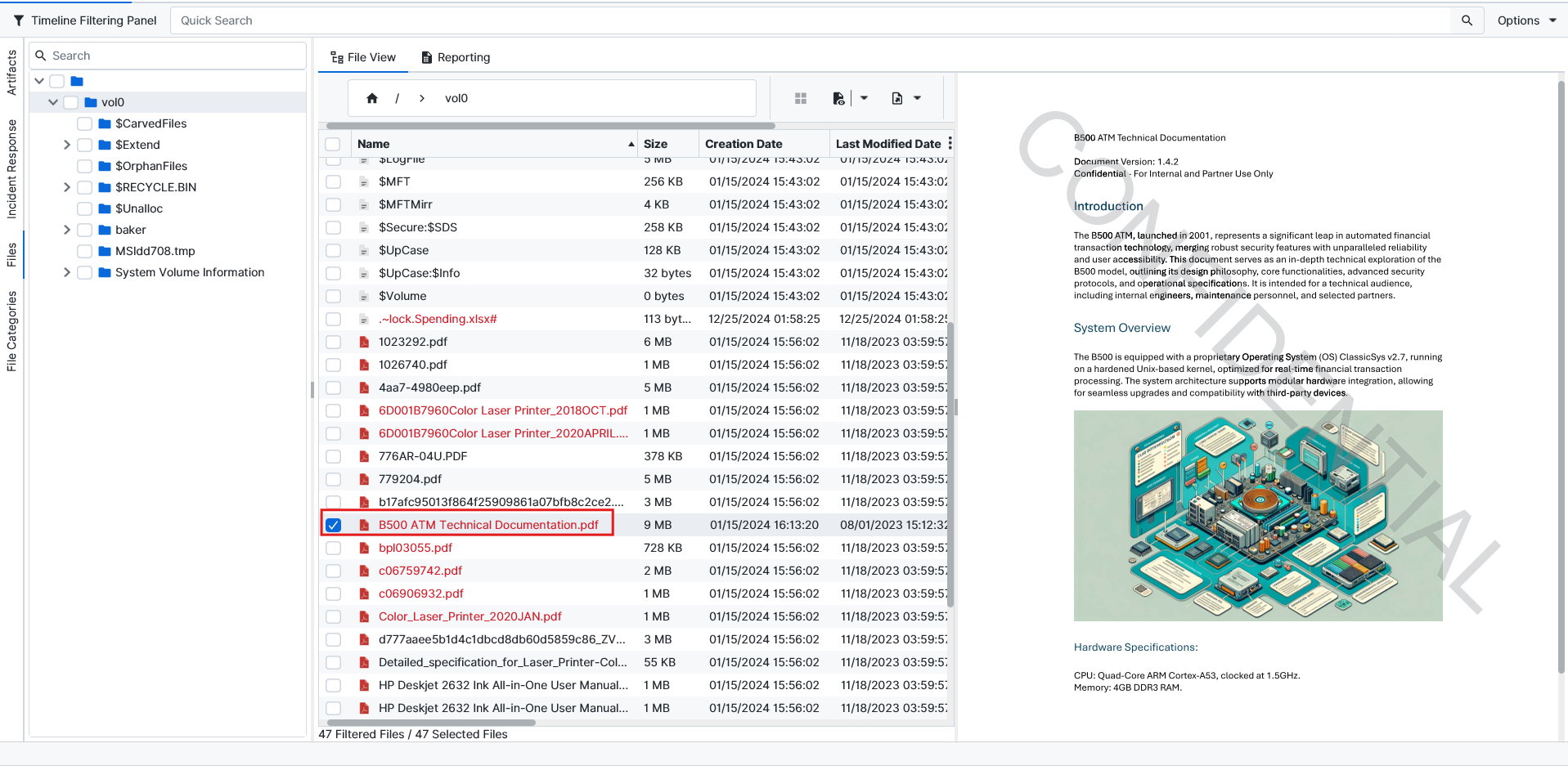
Kenneth Lee. I started this question by searching for anything related to technical documents. On my search, I came across a LNK file located at Y:\B500 ATM Technical Documentation.pdf. This must be the vhdx evidence we mounted earlier. However, when I go to the mounted drive, there is no document with this name. The file was likely deleted. Using ArtiFast’s file carving managed to bring this document back
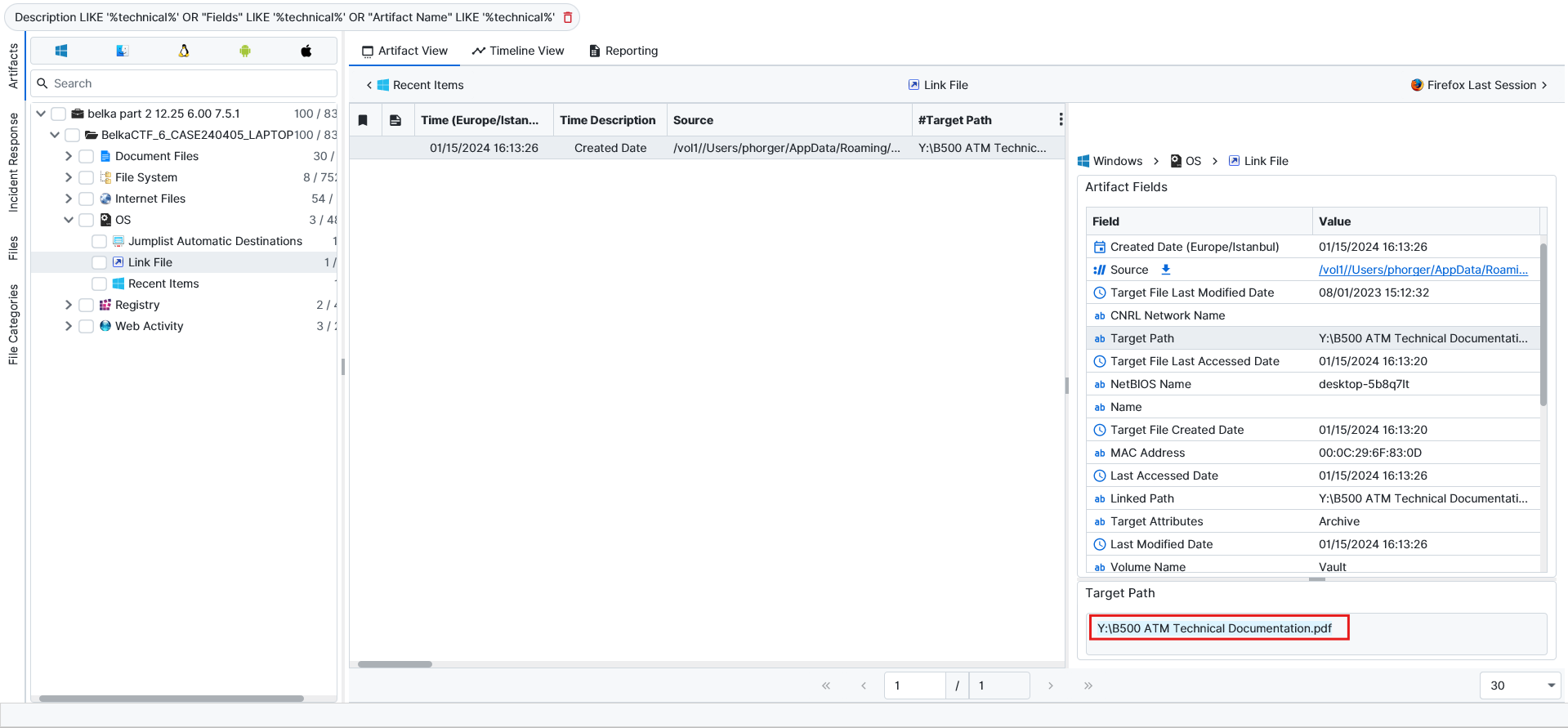
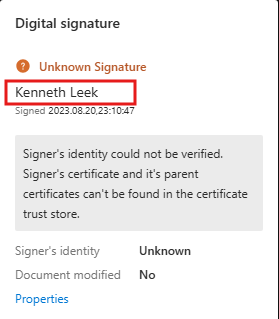
The document was digitally signed. We managed to find the name from the digital signature.
Financial institution (Hard)
Question: Which offshore financial institution did the gang bank with? Provide its SWIFT code.
CRVBPA2P. In the iOS Telegram Messages, there is a conversation between user Mr C or @locknload771 and Billy Megakilley or the local user. After they mention using a shortcut, the messages start to be encrypted. From shortcuts, they must have meant Apple Shortcuts.
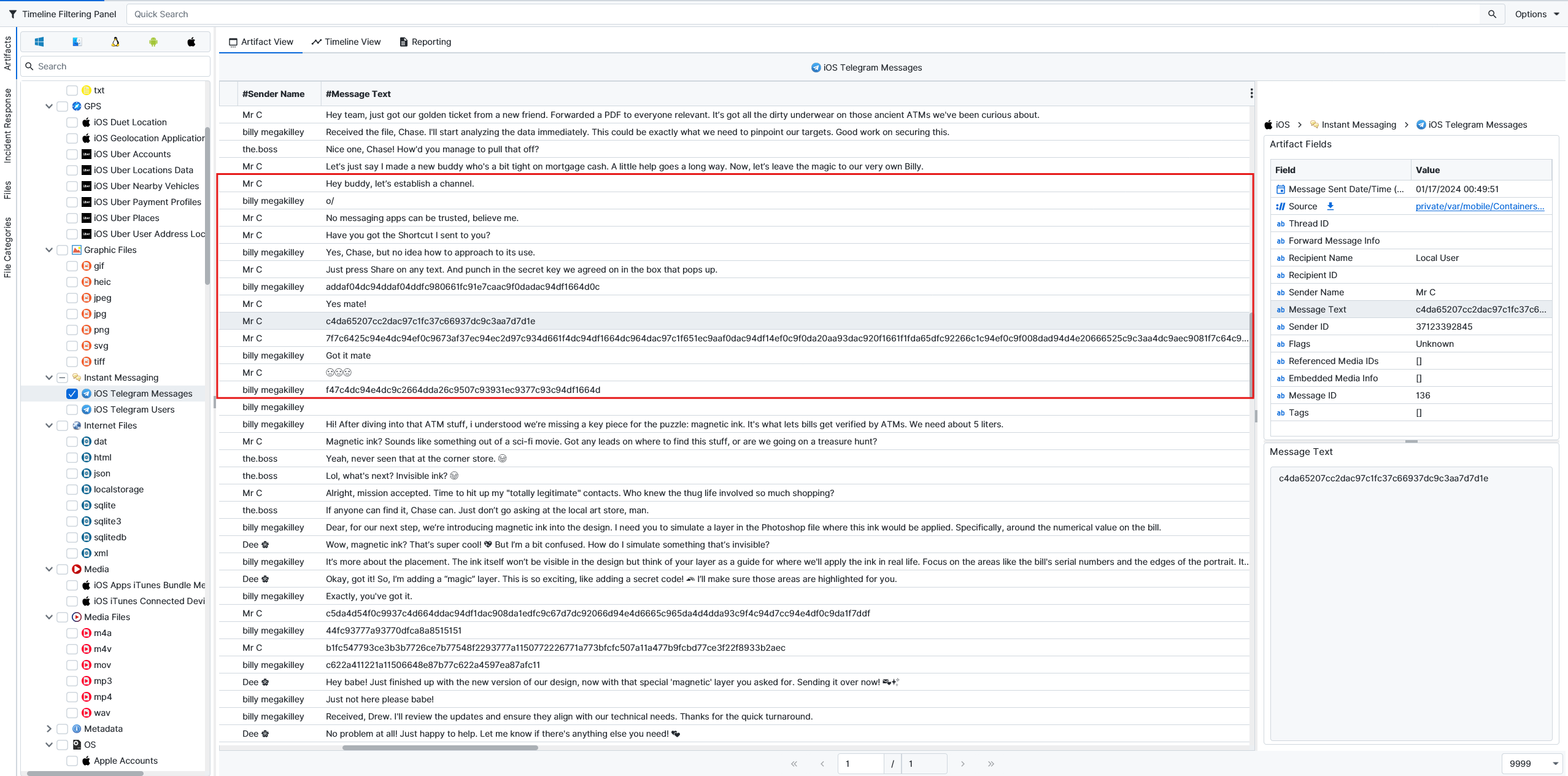
If we search for Shortcuts, we can see from the Apple Biome Notifications artifact that there are 2 shortcuts with names of SecuEncrypt and SecuDecrypt that have been used.
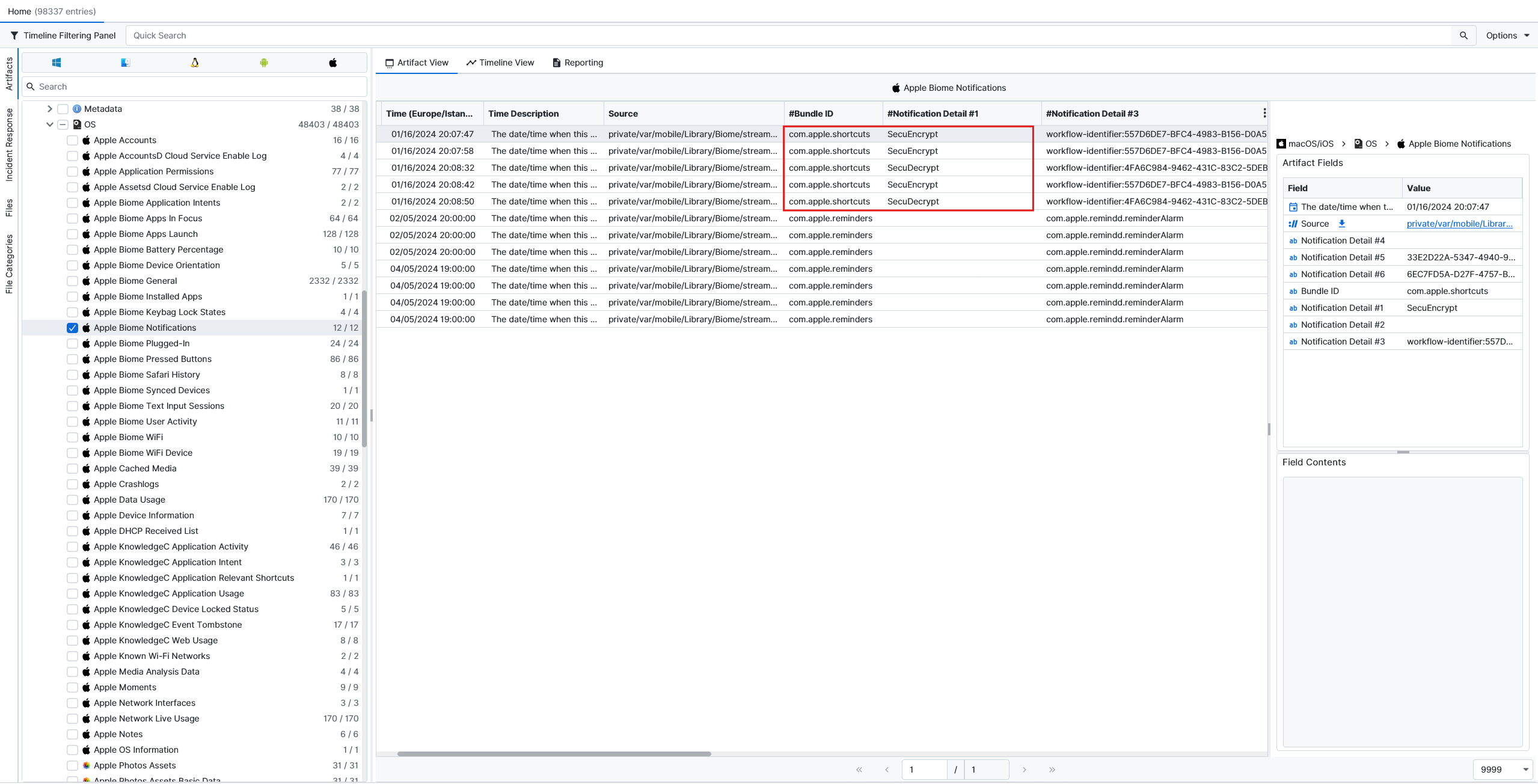
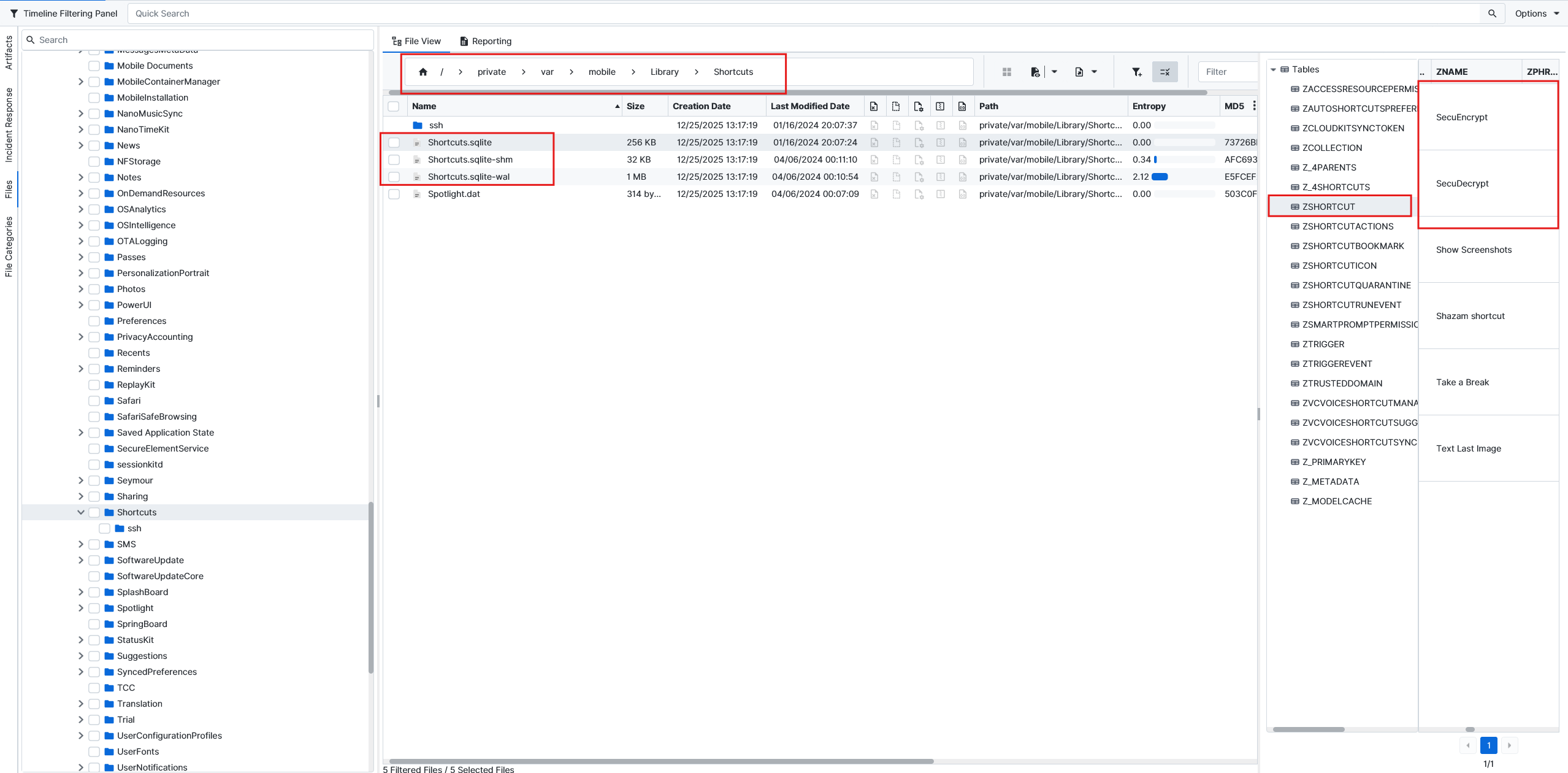
After checking the database related to shortcuts located at private\var\mobile\Library\Shortcuts, we can see the SecuEncrypt and SecuDecrypt shortcuts inside the ZSHORTCUT table using the ArtiFasts Database viewer.
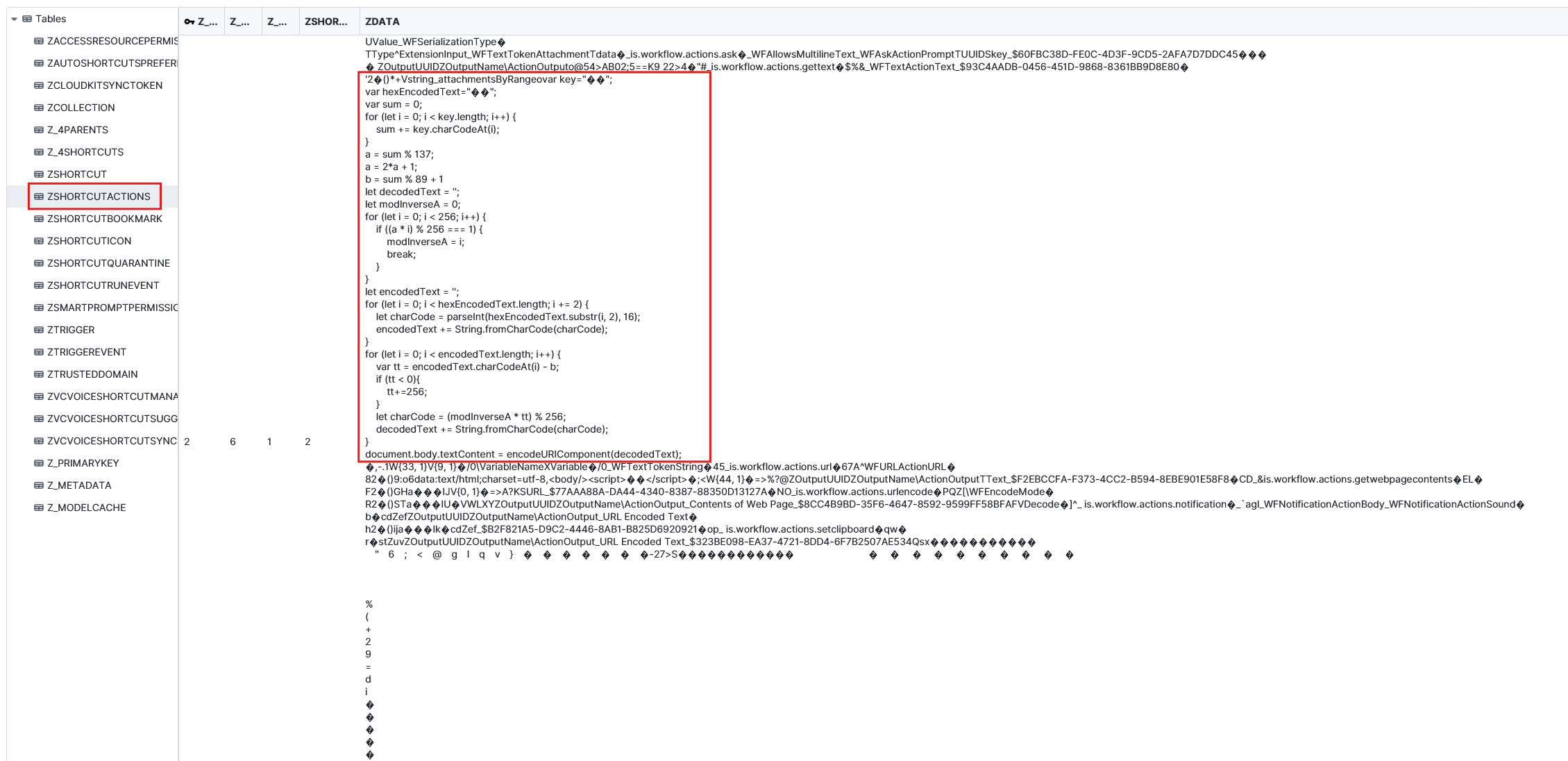
If we look further, we can find the command the shortcuts are using inside the ZSHORTCUTACTIONS table. From the commands The first code encrypts. It takes the message (inputText) and a secret key, turns the key into two numbers a and b, then for each byte does cipher = (a * plain + b) mod 256, and finally outputs the result as a hex string. The second code decrypts. It takes the hex ciphertext and the same key, recomputes a and b, finds invA (the modular inverse of a mod 256), converts hex back to bytes, then reverses the math: plain = invA * (cipher − b) mod 256. To decrypt a message, we need either the original key (to compute a,b) or the correct (a,b) values. Since we don’t have the key, the “brute force option” in this challenge works because the key is only used to produce two small parameters: a = 2*(sum % 137) + 1 → only 137 possible a values (odd numbers) b = (sum % 89) + 1 → only 89 possible b values So instead of brute-forcing the whole key string, you brute-force the (a, b) pair.
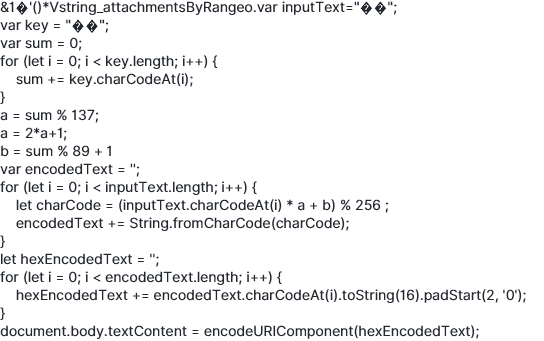
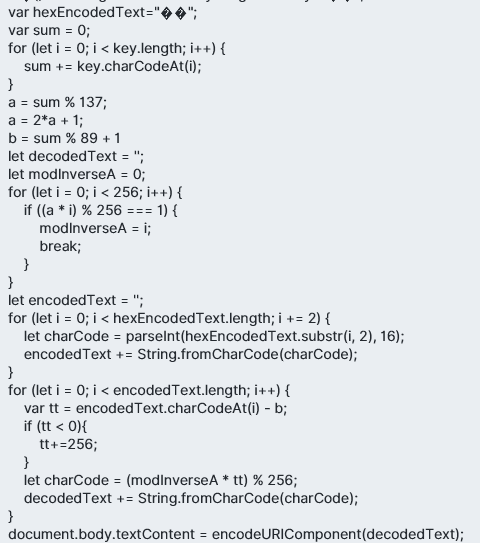
const cipherHex = "addaf04dc94ddaf04ddfc980661fc91e7caac9f0dadac94df1664d0c";
function attemptDecrypt() {
for (let x = 0; x < 137; x++) {
for (let shift = 1; shift <= 89; shift++) {
const coeff = 2 * x + 1;
// Compute modular inverse of coeff modulo 256
let invCoeff = 0;
for (let k = 0; k < 256; k++) {
if ((coeff * k) % 256 === 1) {
invCoeff = k;
break;
}
}
// Convert hex to binary string
let binaryStr = '';
for (let pos = 0; pos < cipherHex.length; pos += 2) {
const byteVal = parseInt(cipherHex.slice(pos, pos + 2), 16);
binaryStr += String.fromCharCode(byteVal);
}
// Apply decryption: inverse * (byte - shift) mod 256
let result = '';
for (let j = 0; j < binaryStr.length; j++) {
let shifted = binaryStr.charCodeAt(j) - shift;
if (shifted < 0) shifted += 256;
const decryptedByte = (invCoeff * shifted) % 256;
result += String.fromCharCode(decryptedByte);
}
// Check if result is printable ASCII
if (/^[\x20-\x7F]+$/.test(result)) {
console.log(result);
}
}
}
}
attemptDecrypt();
After decrypting the texts, we got some good information. Some of the texts are; “Test test. Can you see that?” “Got it mate! Sorry for that” “Now tell me, what ink am I looking for exactly?” “Now, it is VERY important that we only use this secure channel. Max is skeptical, but I know what I'm talking about. You will thank me later.” “Let's rotate the key. Add capital letter G to its end.” “Got it boss…” “This one is for you personally. Bank Name: Crooked River Bank. Account Name: Consulting Services Inc. Account Number: 9876543210. SWIFT Code: CRVBPA2P. Bank Address: 50 Offshore Blvd, Panama City, Panama” Here is our answer for Swift code.
Statement (Hard)
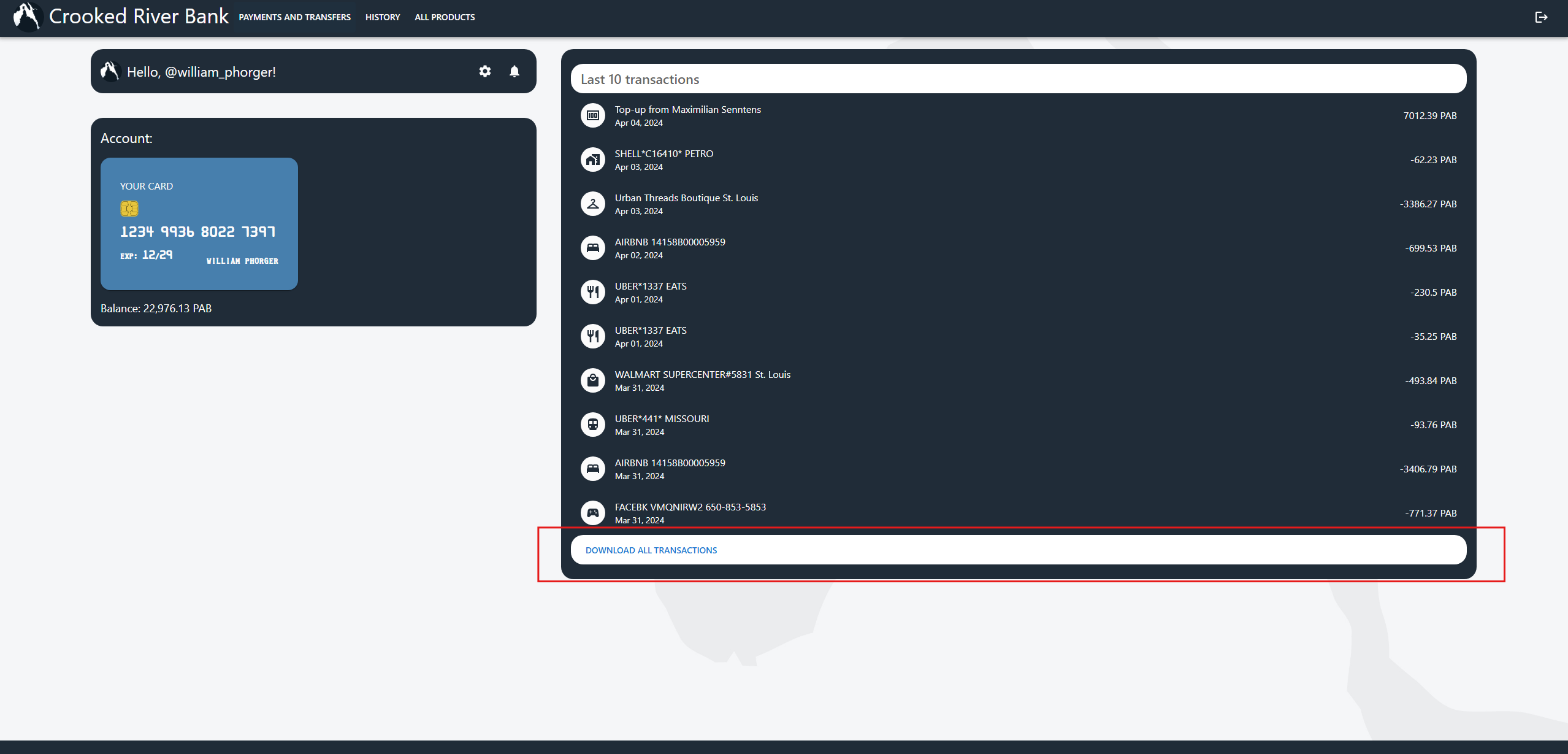
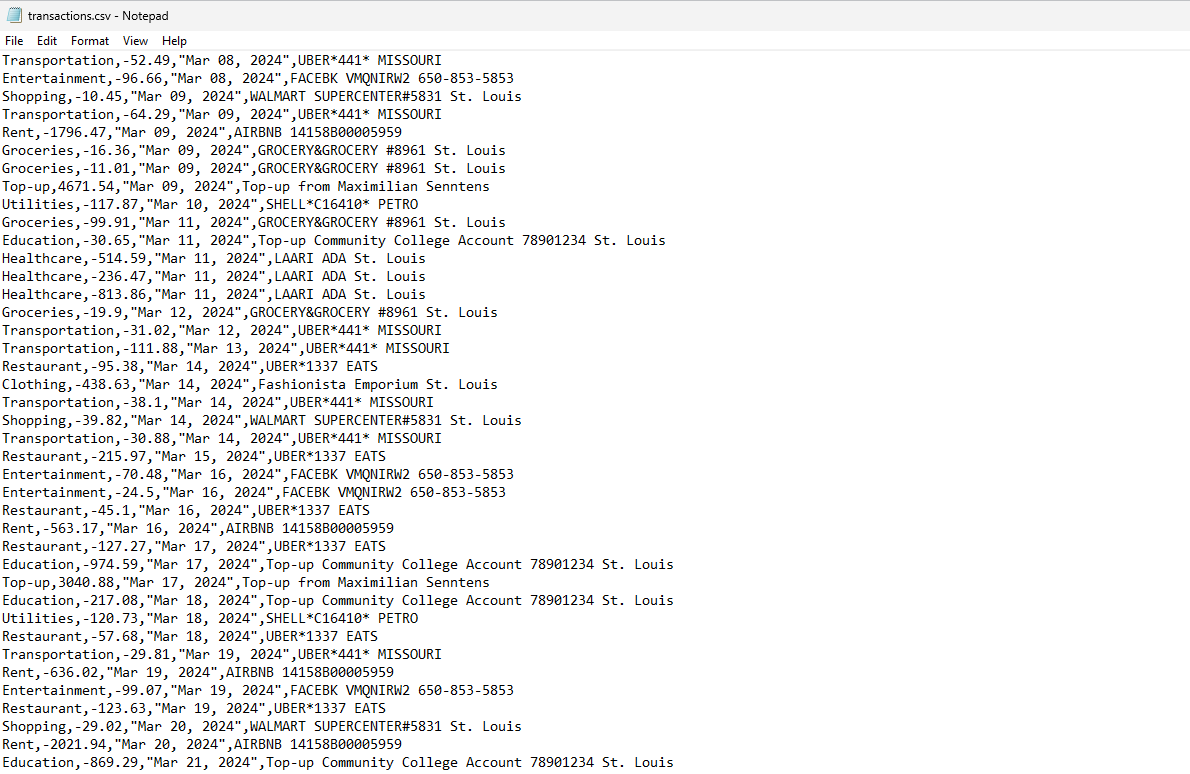
Question: Paste Phorger's entire bank statement here, containing all his offshore transactions.
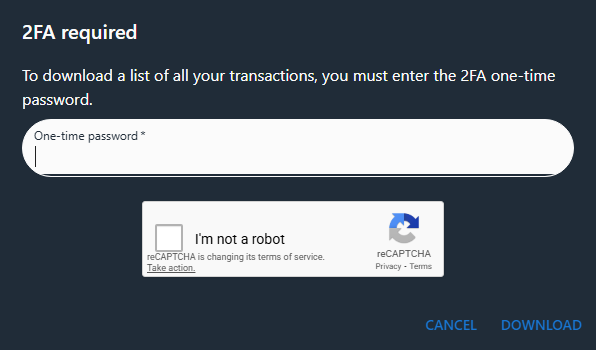
All data is inside the transactions.csv. For this one, we already have access to his bank account from question 6. There is a download button for all transactions; however, it asks for 2FA. Time to search our evidence once again.
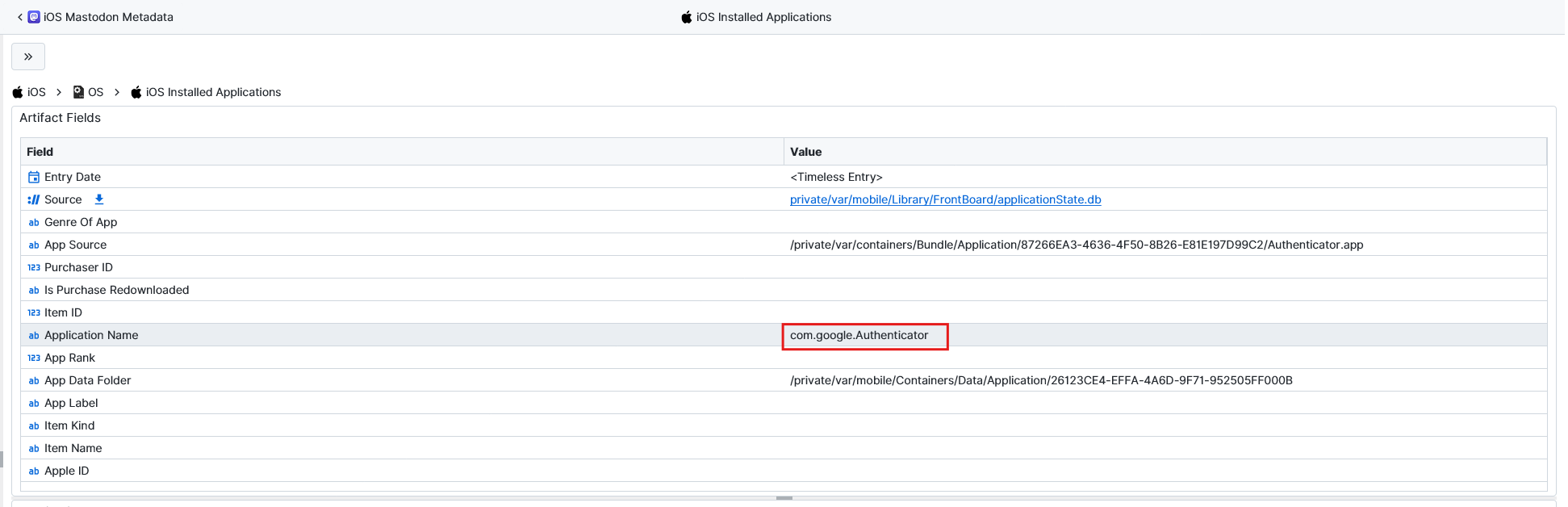
First thing I noticed is that Google Authenticator is installed on our iPhone from iOS installed Applications.
If we check further, our device private\var\root\Library\Lockdown\data_ark.plist, we can see that a backup has happened on our iPhone.
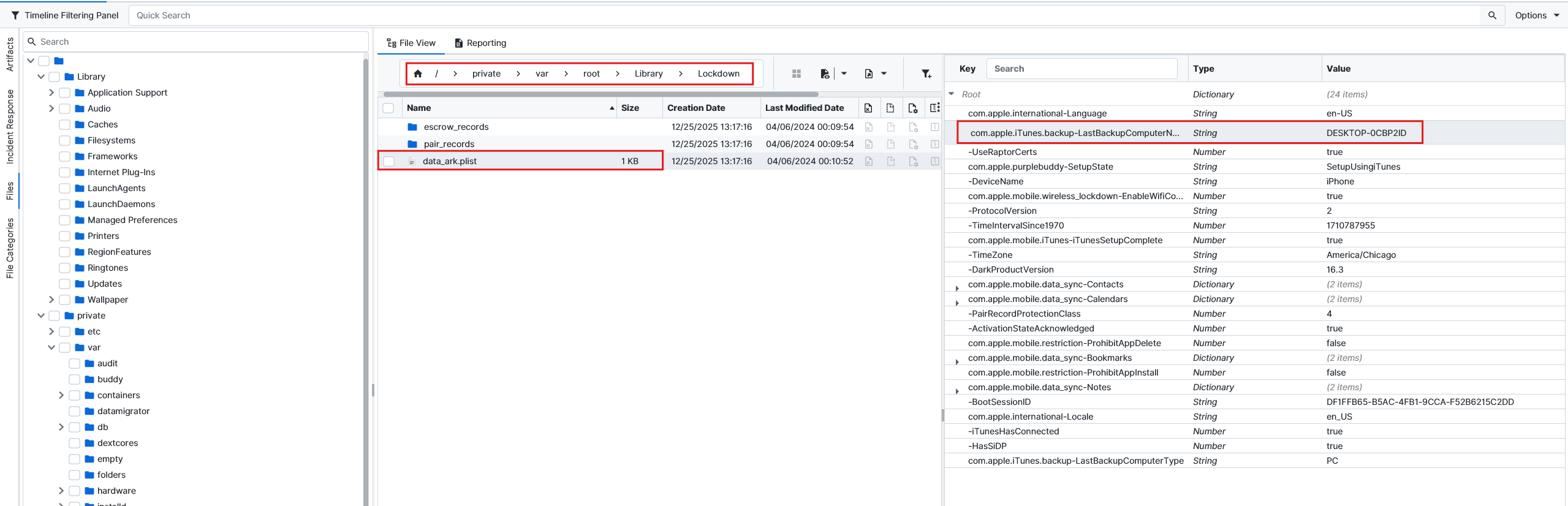
When we check our laptop evidence, we can see that it is true and we got a backup of our iPhone here.
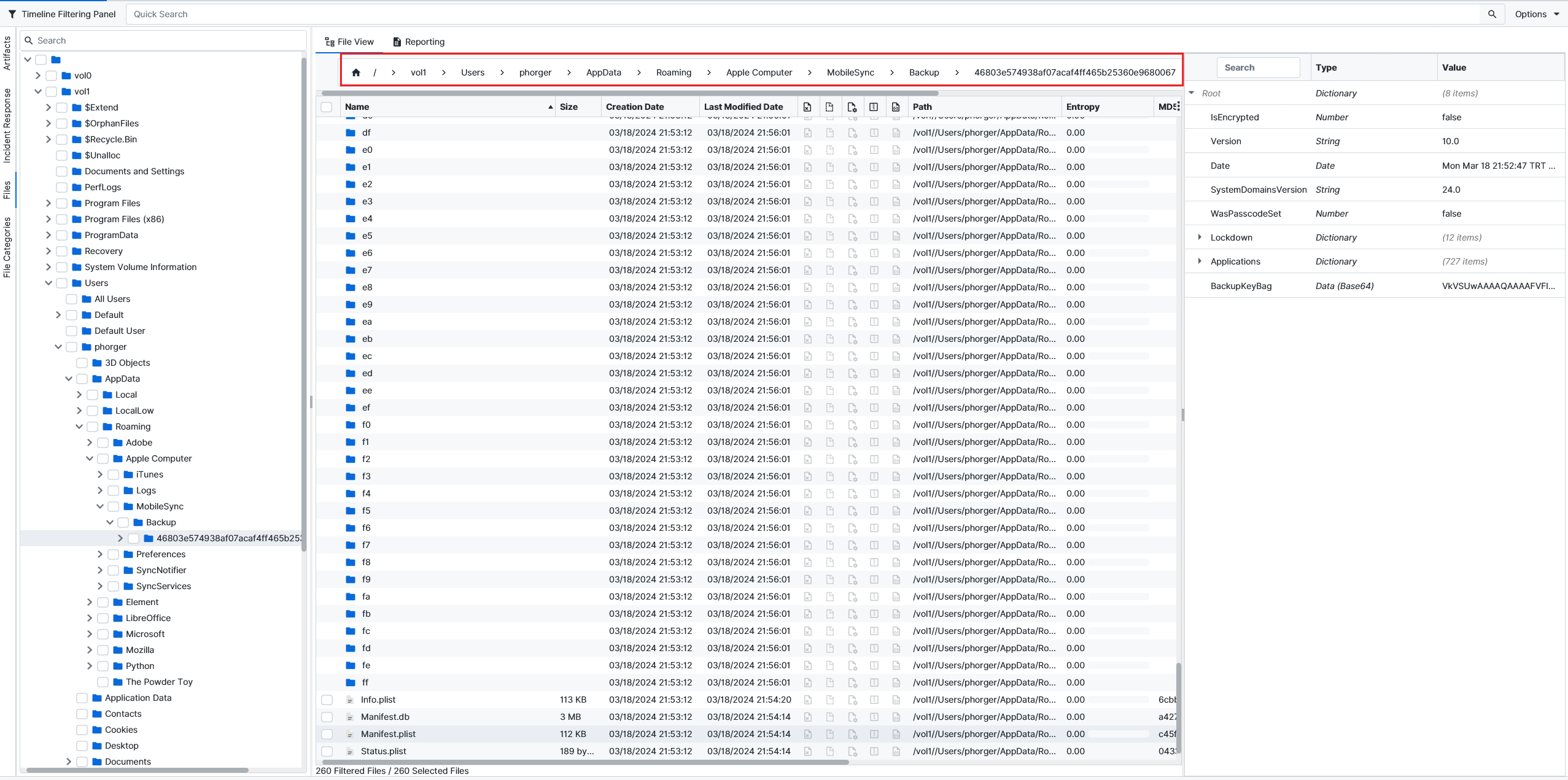
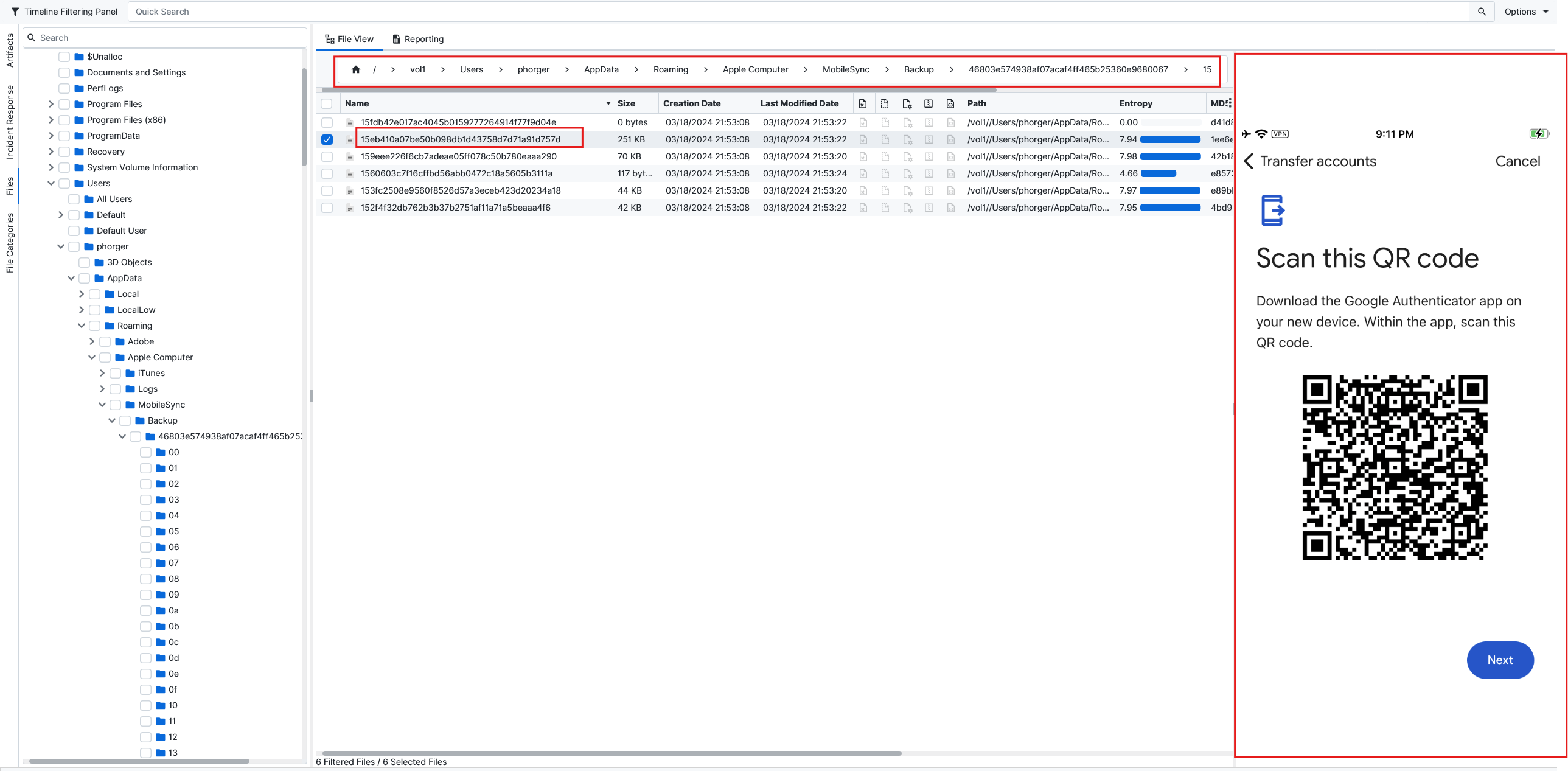
I started checking the folders one by one till I found this screenshot inside folder 15eb410a07be50b098db1d43758d7d71a91d757d. Since we found this QR, we can add it to our own Google Authenticator app to get a 2FA code and download the transaction logs.
×
