Solving Cellebrite's September 2023 CTF (Felix's iPhone device) Using ArtiFast
20/10/2023 Friday
Cellebrite held their yearly CTF last month and this year the challenge featured 4 devices, belonging to 4 different suspects. In this blog, We will use ArtiFast to answer the questions associated with one of the suspects devices (Felix Daveys iPhone 8 Plus).
The Scenario:
Terror attacks were planned for Southport, NC in June of 2023. Russell, the primary suspect, lives locally in that area and seems to have been introduced to Abe via Sharon. Russell and Sharon go way back, and she seems to be the linchpin who tied Abe to Russell. So, who is Abe? How is he involved with Felix? Why would Felix be feeding a US person with information on nuclear power plants and weapons? Complete challenge details can be found Here
Artifacts Covered in this Challenge:
- Apple Voicemail
- Apple Filesystem Events
- EML(X) Emails
- iOS Data Usage
- Apple Maps
- Apple SIM Information
- Apple Wipe Events
Felix 01 – Voicemail – Level 1
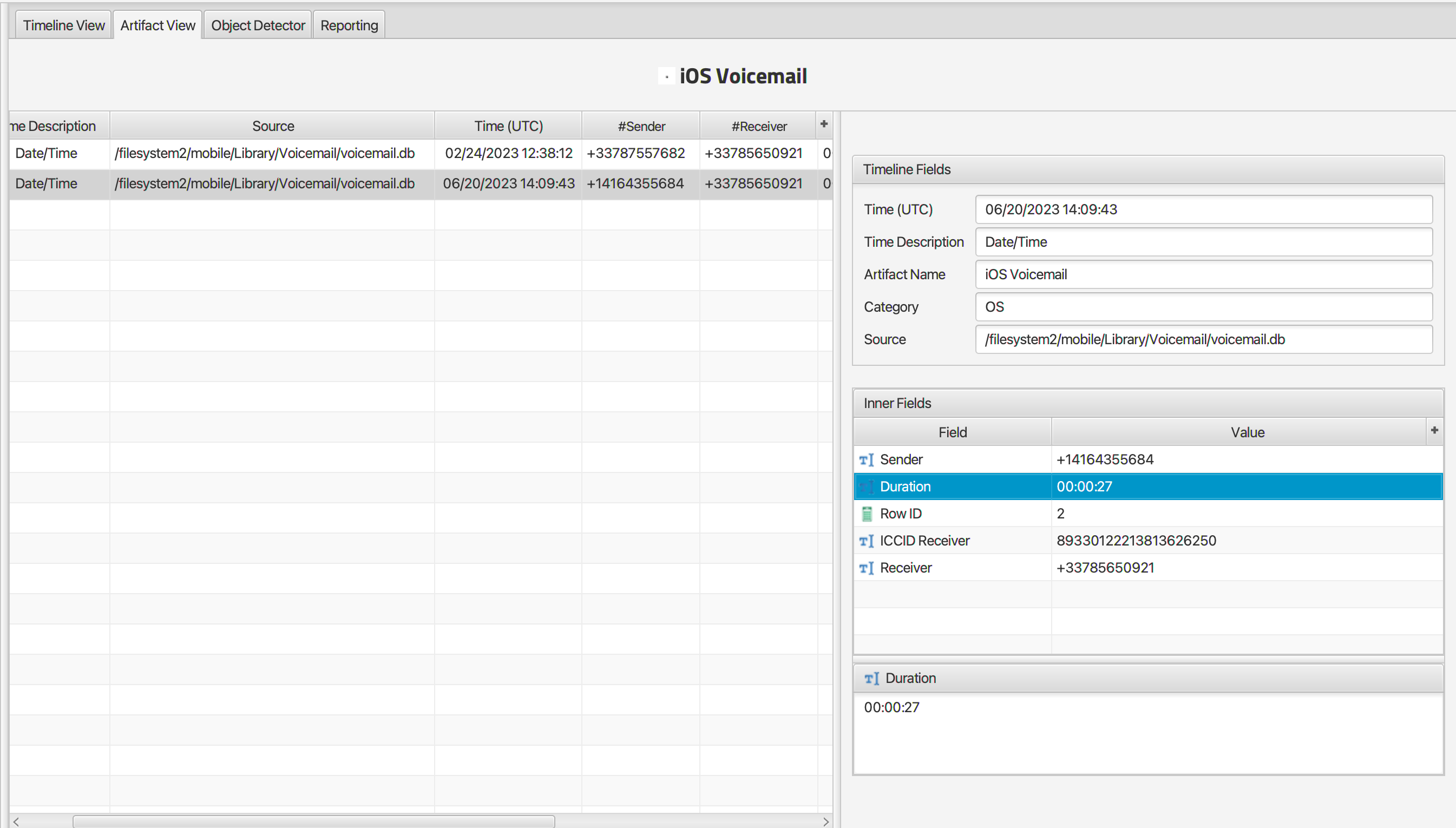
Q: Felix received a voicemail from +1-416-435-5684. How many seconds in length was the voicemail message?
In the Apple Voicemail results, we can see the phone number above and the length of the voicemail “27” seconds.
Felix 02 – Picture – Level 1
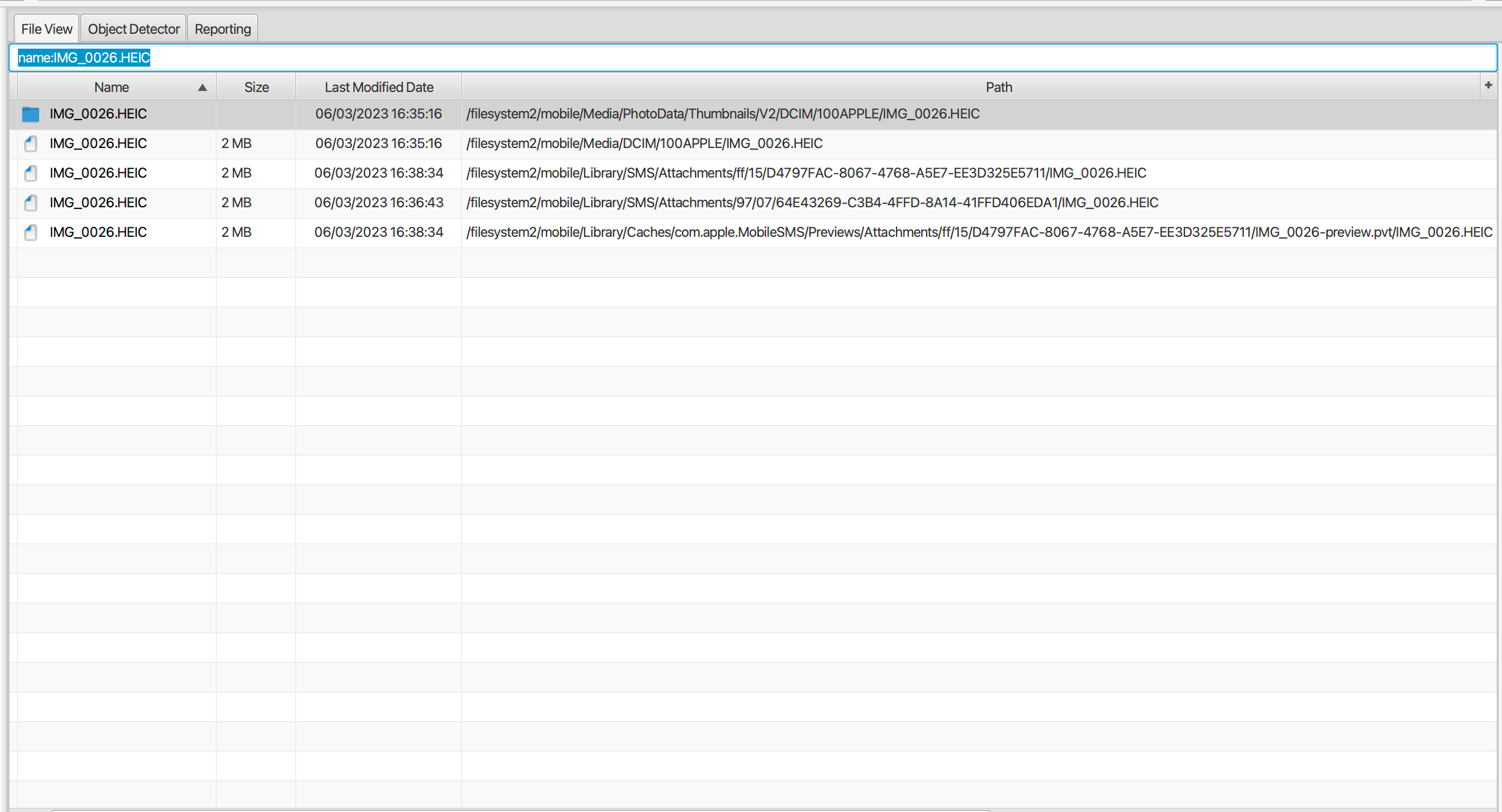
Q: Please look at the following image: IMG_0026.HEIC. How many times do you see this picture on the device (including thumbnails)?
Navigating to the FileViewer and using the filter “name:IMG_0026.HEIC” we can see the existence of 5 of these images within the device.
Felix 03 – Confirmation – Level 1
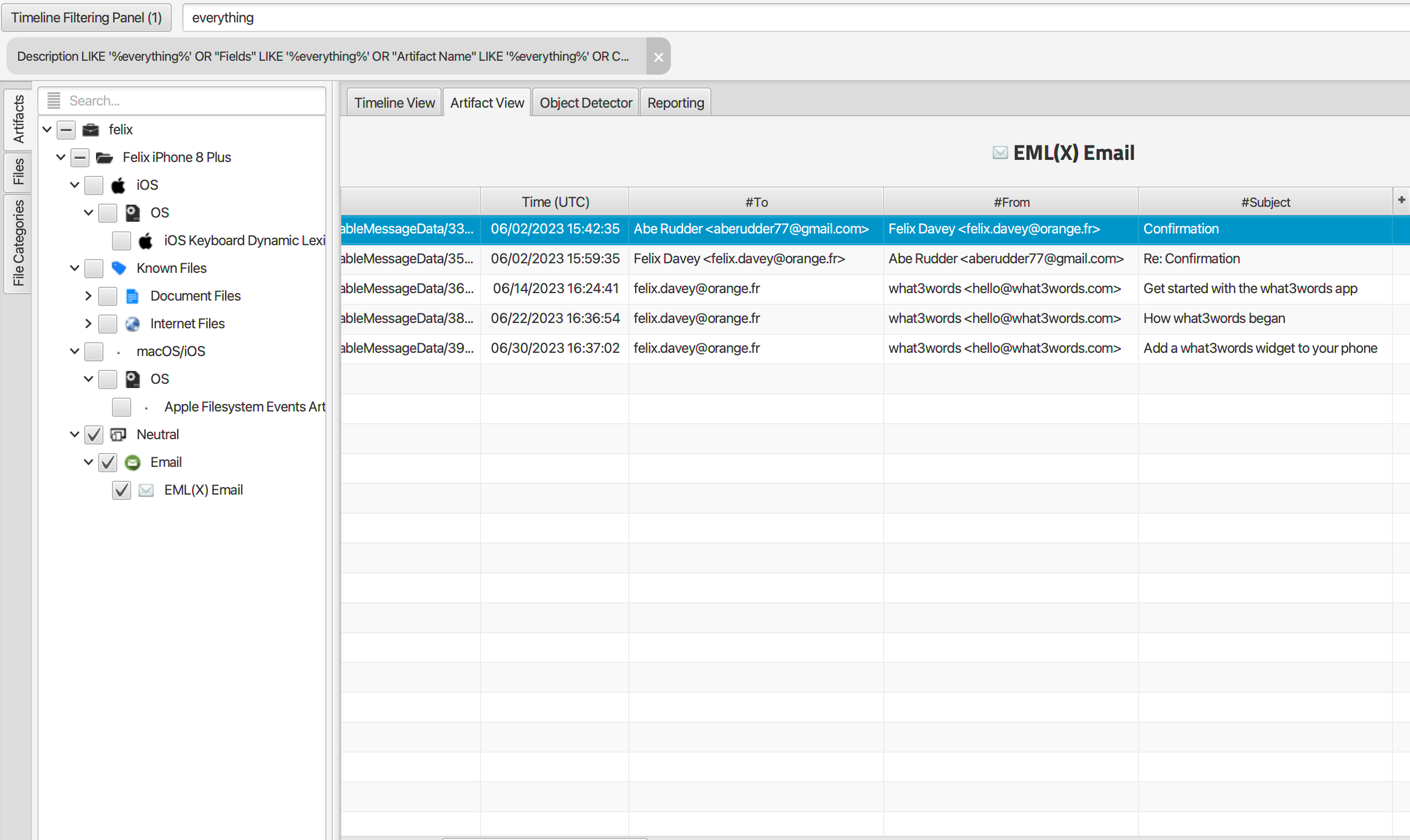
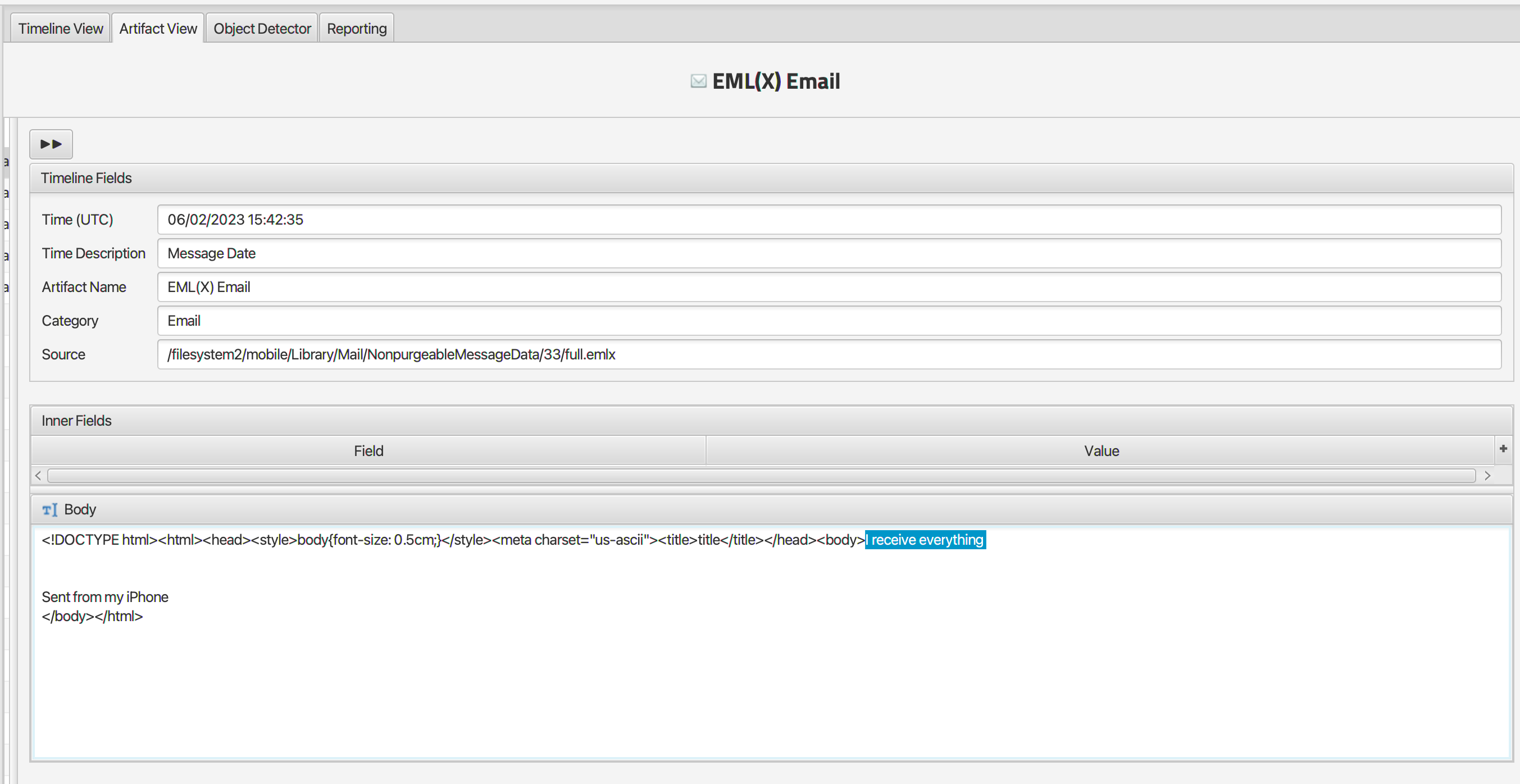
Q: Felix confirmed receiving “everything.” When Felix sent the confirmation, which account did he send it from?
Running a search for “everything” returns a number of emails, 2 of which are between Felix and Abe with the subject “Confirmation”. A closer look at the body of the email reveals that Felix sent “I receive everything ” from the account felix.davey@orange.fr
Felix 04 – Photo – Level 1
Q: Private Photo Vault is an application that is installed on the phone. What is the passcode to the application?
The passcode is 2510
Felix 05 – Location – Level 1
Q: Felix always had an interest in the USA. What application did he use to search for an address in New Jersey USA?
He used Apple Maps. Running a search for “New Jersey” returns a result from the Apple Maps Synced Data artifact which shows us an address in New Jersey and the Longitude and Latitude of the address.
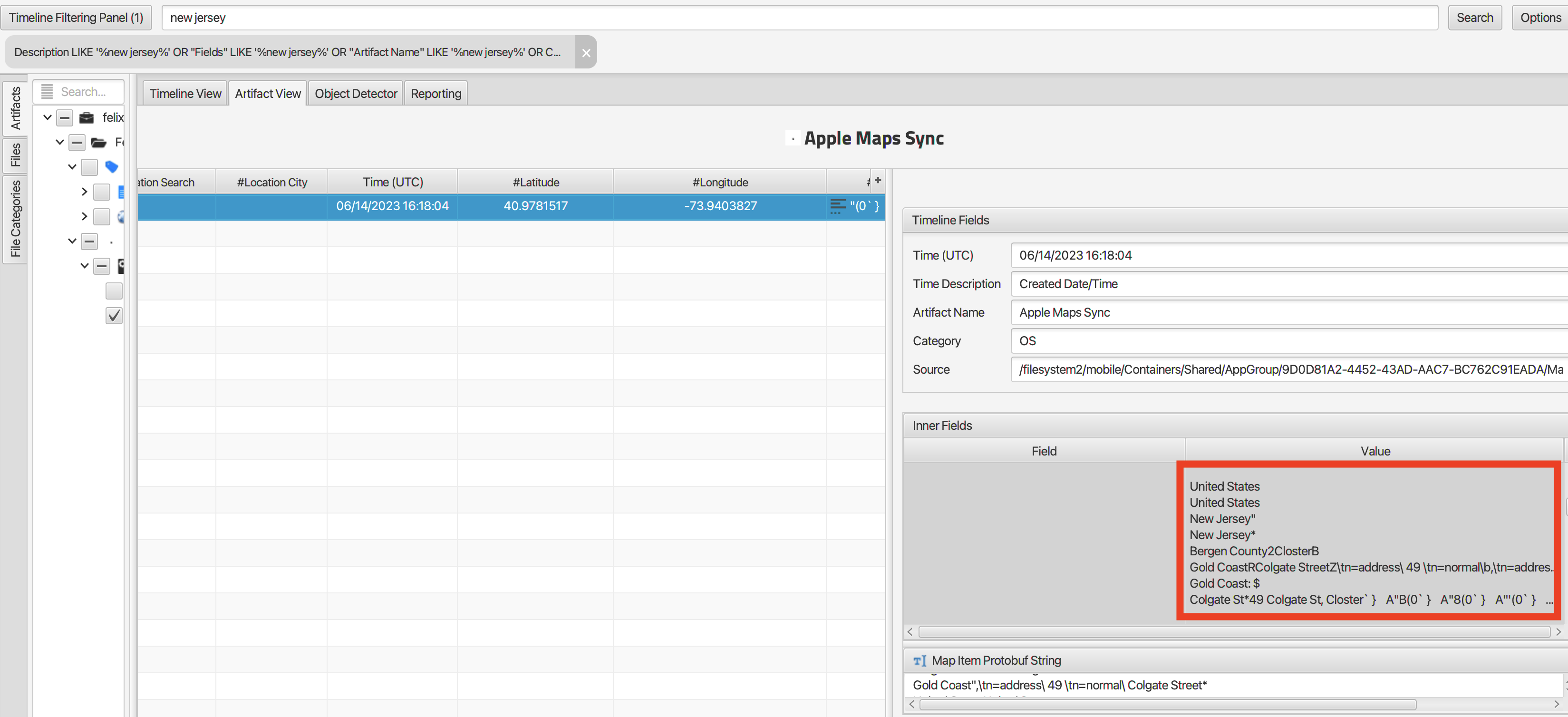
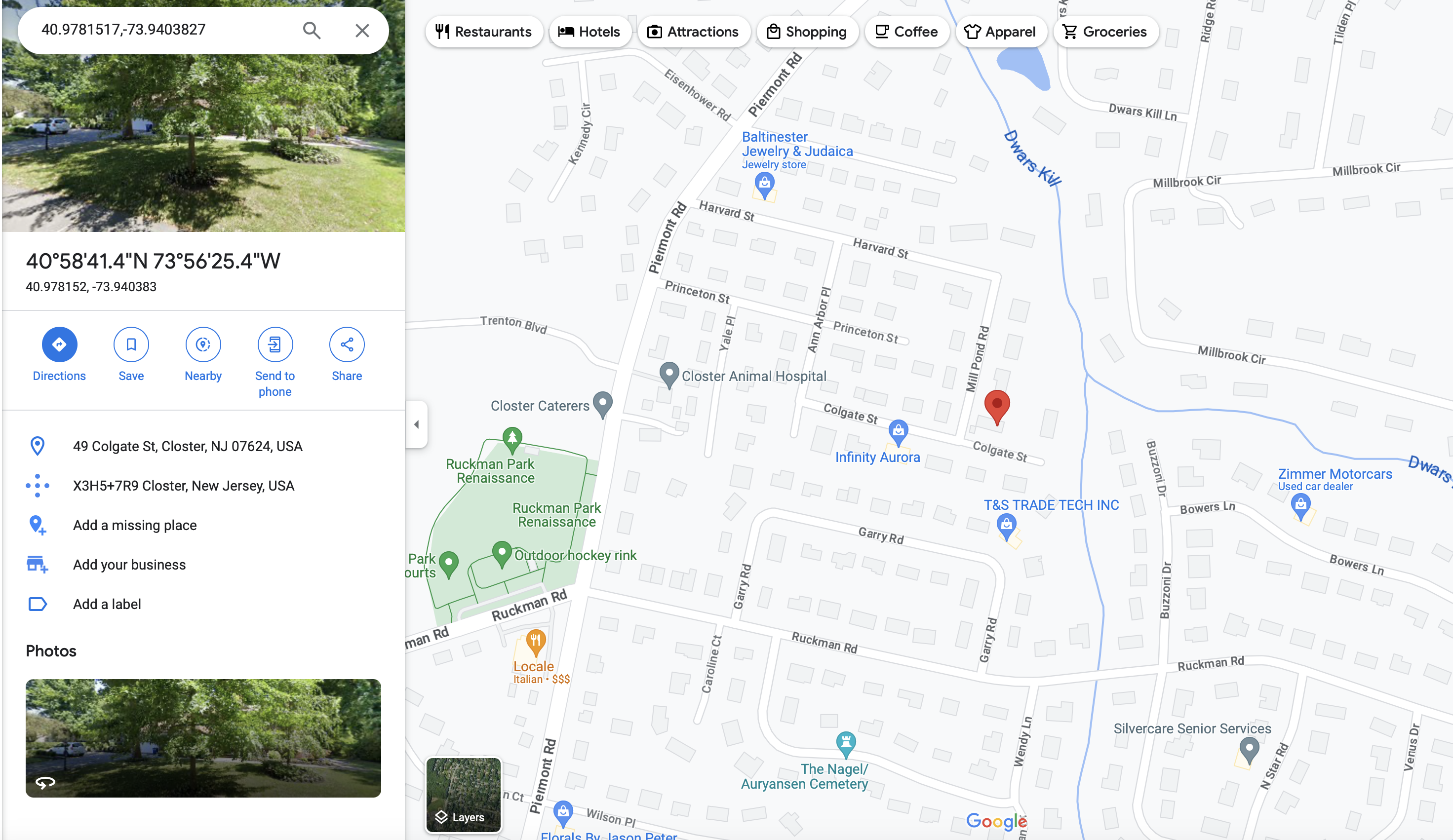
When we put the coordinates in google maps we get the following.
Felix 06a – Size – Level 1
Q: What is the size (in bytes) of the ChatStorage.sqlite-wal file? Answer with numeric digit(s) only.
The file size is 0.
Felix 06b – Time – Level 2
Q: What is the date and time the -WAL file from Felix 06a committed to the main database?
The Last Modified date/time of ChatStorage.sqlite indicates the last commit done. So the answer is 2023-07-01 at 05:49:55.
Felix 07 – Size – Level 2
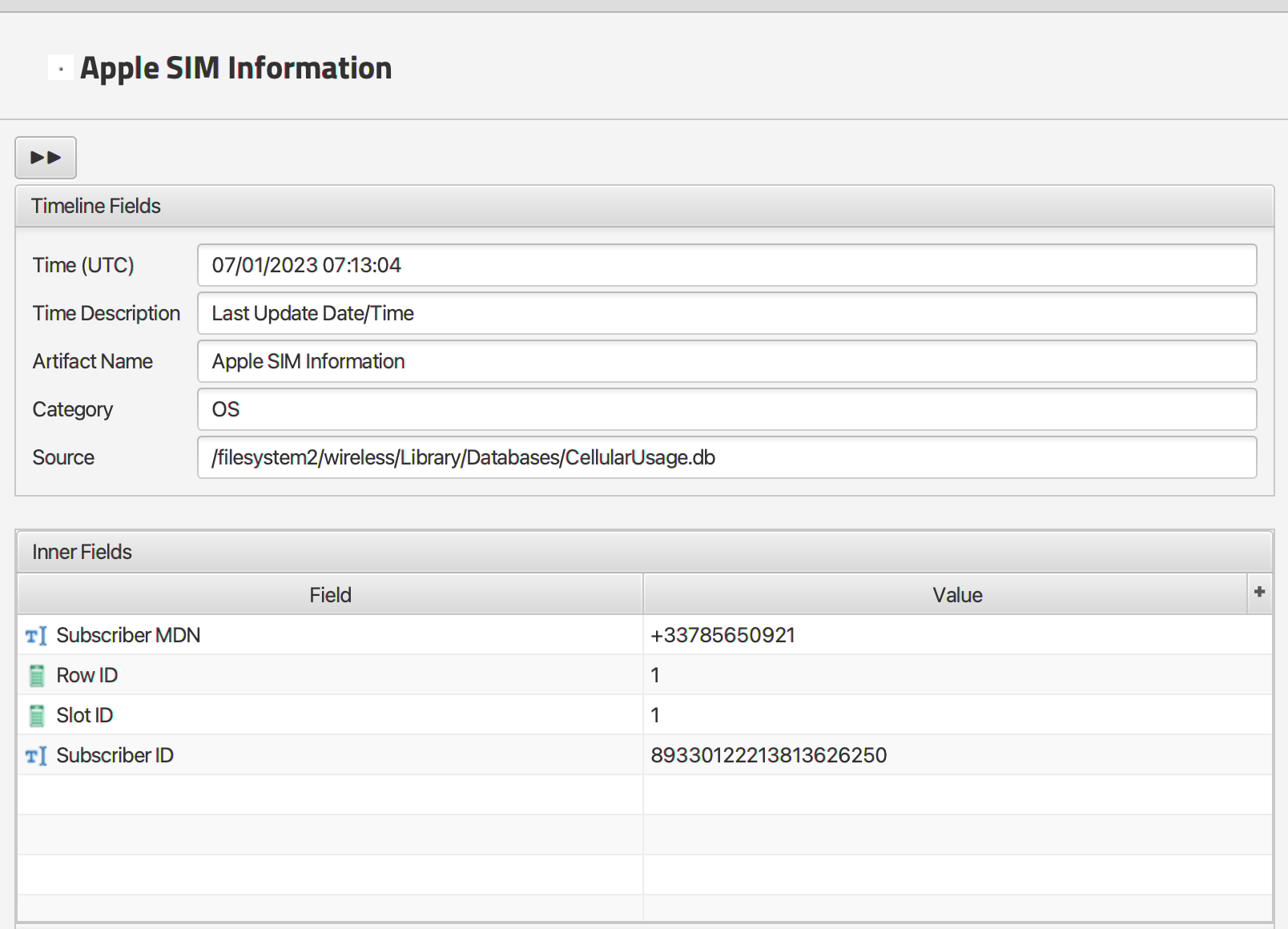
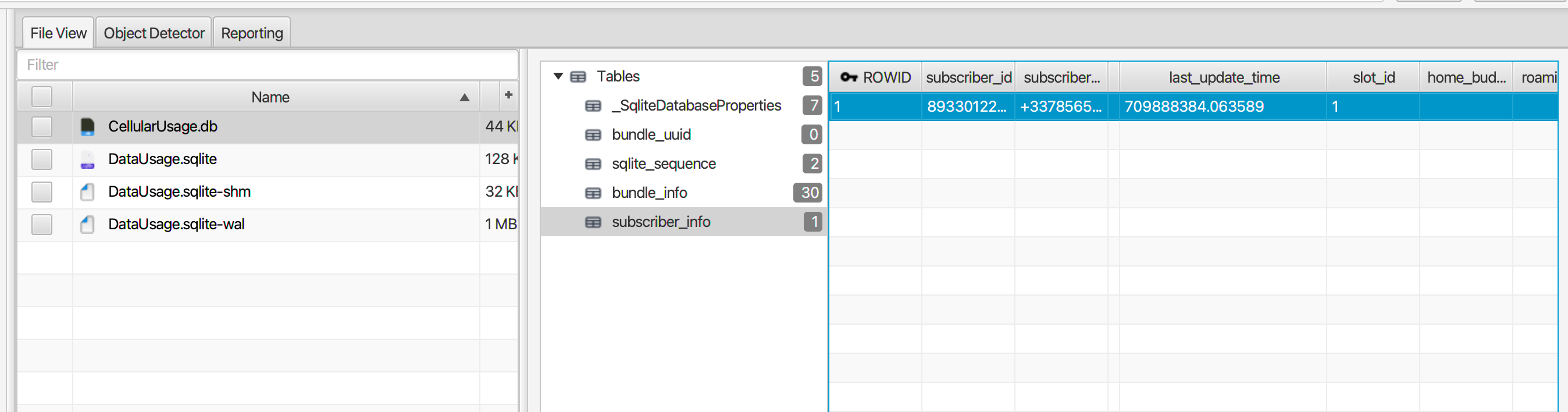
Q: When was the SIM card information on Felix’s phone last updated? (Raw data, not converted)
Navigating to the SIM Information artifact for the phone number. With the “View Source” option we can check the raw value of the date time which is 709888384.063589.
Felix 08 – Missing – Level 2
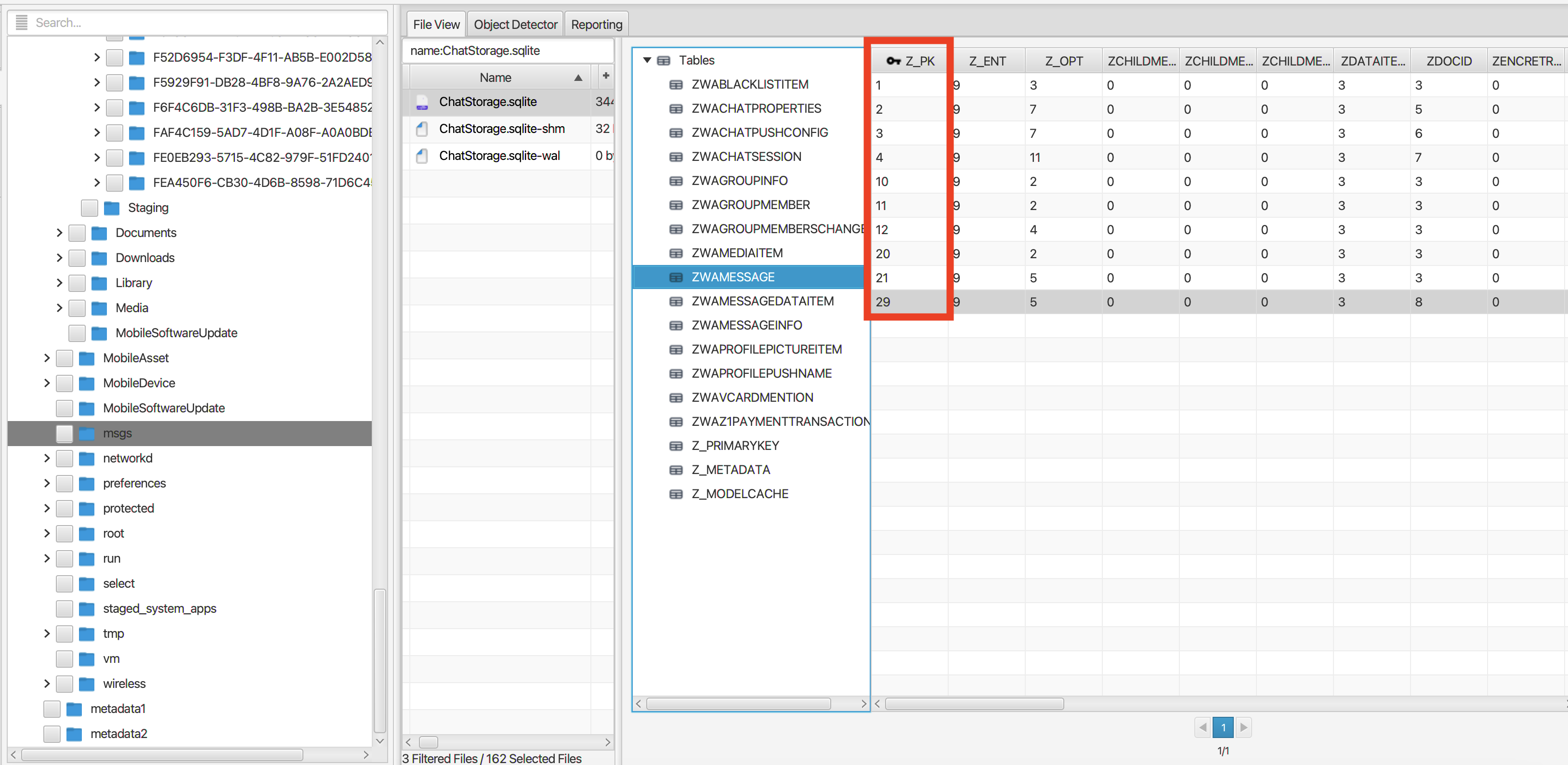
Q: The WhatsApp chat database appears to be missing some chat messages. Assuming the highest number is the last message, how many messages are missing?
ChatStorage.sqlite is the WhatsApp chat database. A look at the ZWAMESSAGE table where messages are stored shows discrepancies in the primary keys under Z_PK. Assuming the highest number 29 is the last message sent means 19 messages are missing from the table.
Felix 09 – Wiped – Level 2
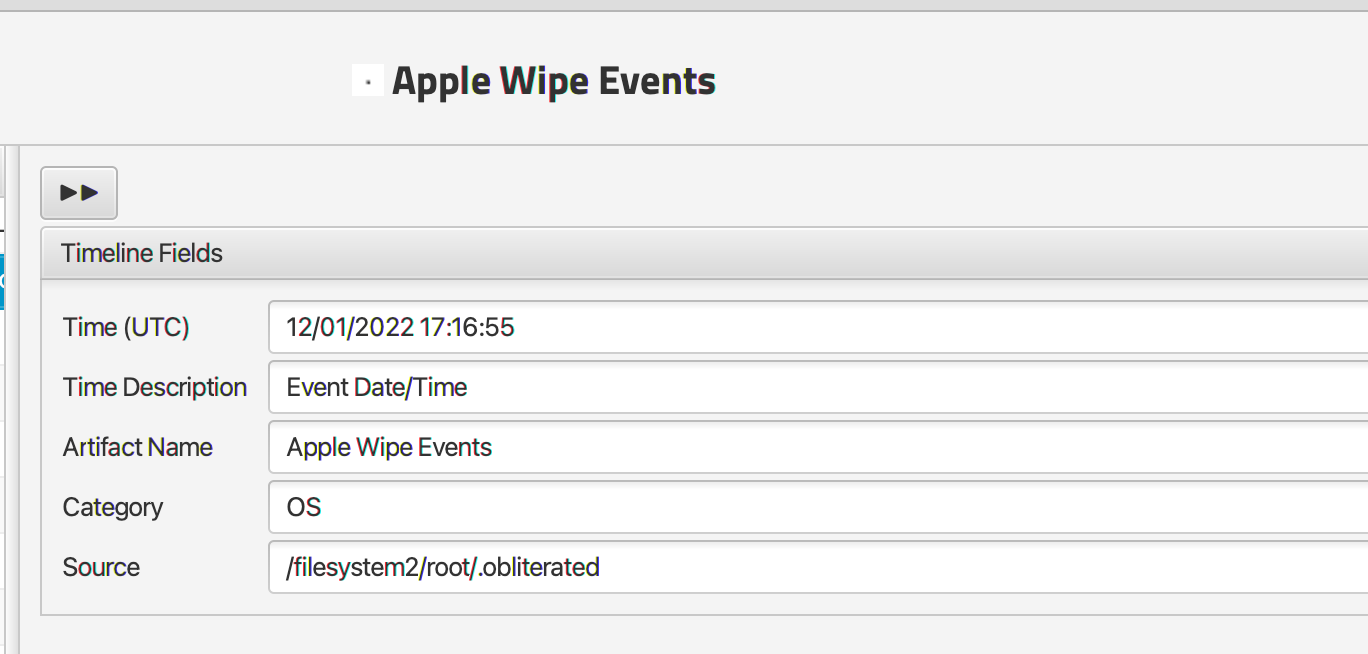
Q: When was Felix’s phone last wiped?
Apple Wipe Events artifact shows that Felix's phone was last wiped on 2022-12-01 17:16:55.
Felix 10 – Cruise – Level 2
Q: Felix was researching / surveilling a ship as a possible target and downloaded a photo of it. What is the name of the cruise ship?
The Ships name is Crystal Serenity. Checking Felix’s browsing history using the Safari artifacts, we find that he searched for Yacht photos in Monaco on a website called pexels.
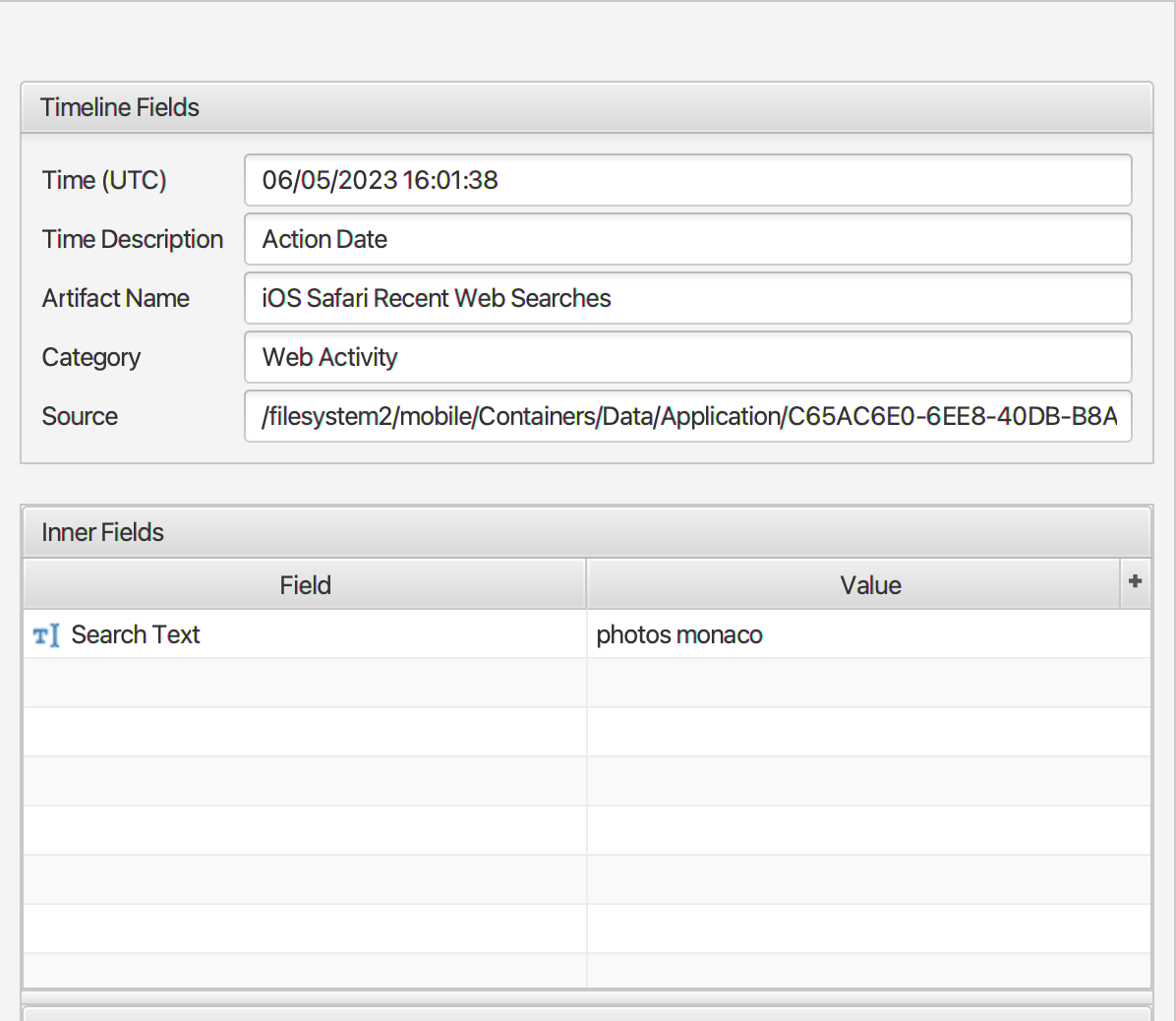
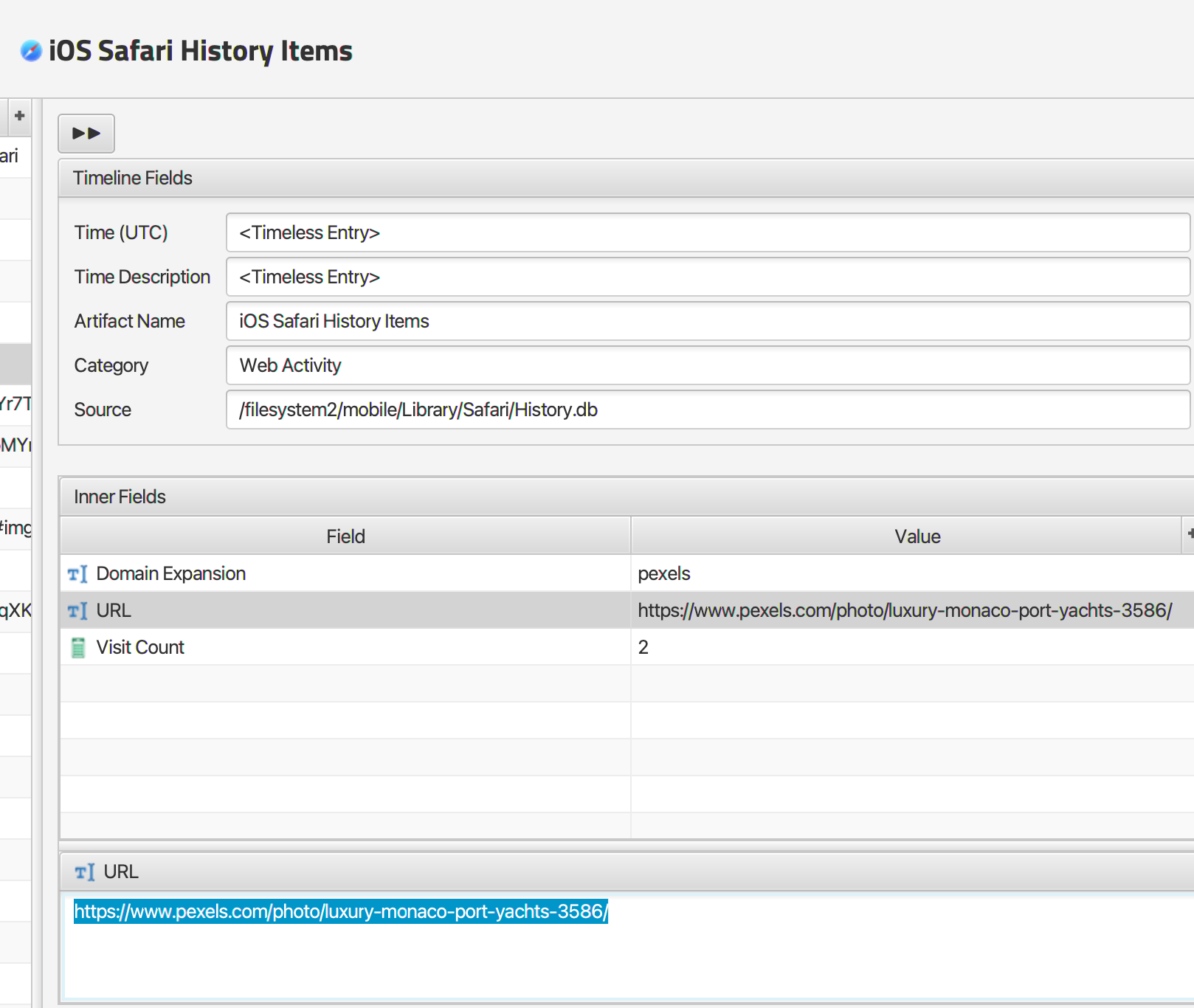
Checking expected downloads folder paths reveals the downloaded image with the string “pexels” in the filename in “filesystem2\mobile\Library\Mobile Documents\com~apple~CloudDocs\Downloads\pexels-helena-jankoviAÌÂovAÌ¡-kovAÌ¡AÌÂovAÌ¡-7372476.jpg”.
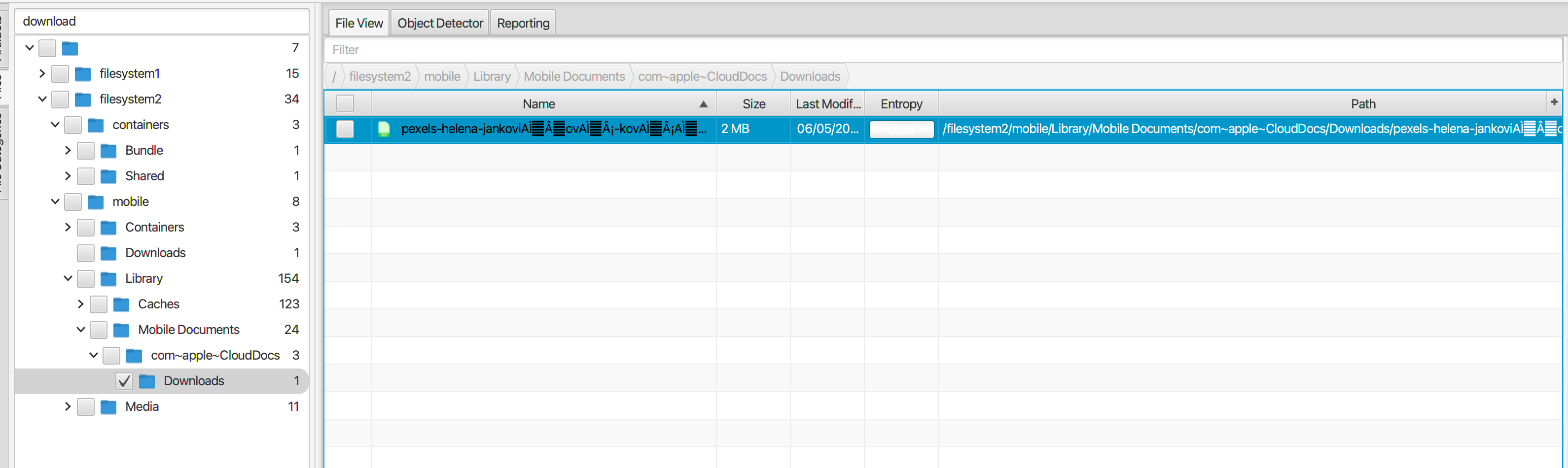
If we open and zoom in on the ship we see that the name is Crystal Serenity.

Felix 11 – Data – Level 3
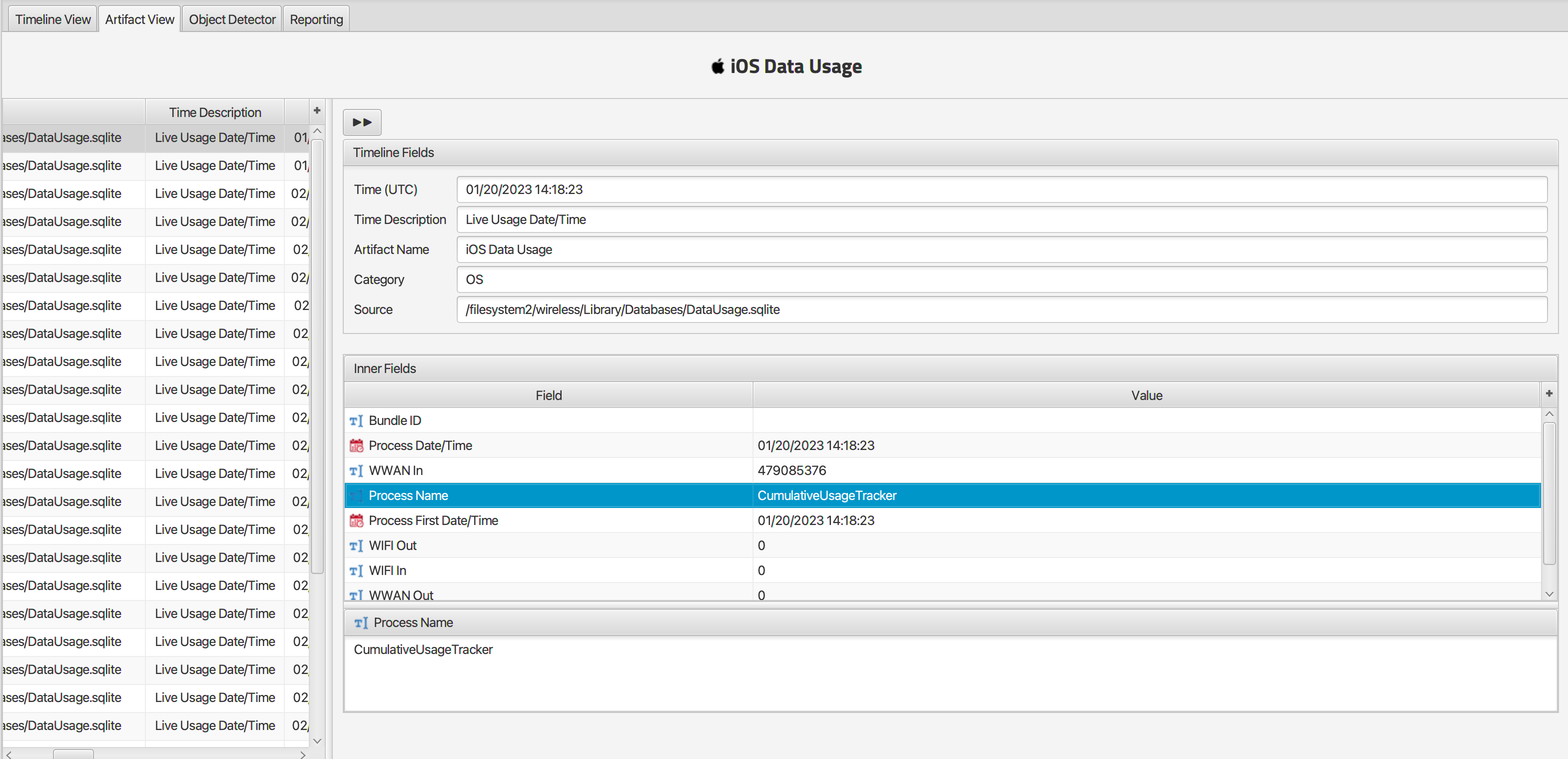
Q: Which process on Felix’s phone used the most cellular data (network traffic INTO the device)?
The iOS Data Usage artifact WWAN In column shows that the process with the most usage is CumulativeUsageTracker at 479085376.
Felix 12 – H is mean – Level 3
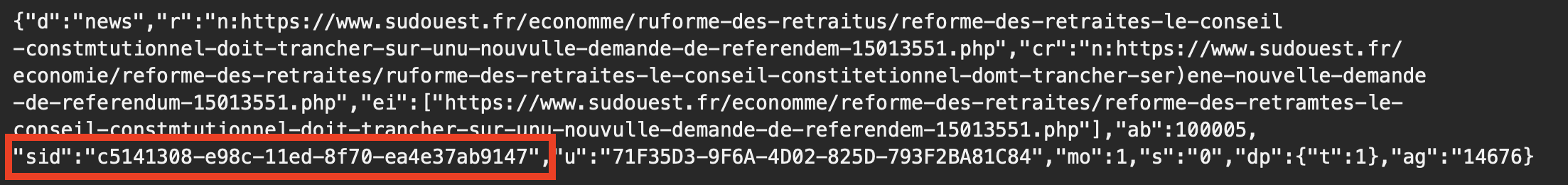
Q: Felix was referred information about pension reform. What is the SID associated with that artifact?
The SID is c5141308-e98c-11ed-8f70-ea4e37ab9147. A keyword search for “Pension Reform”, “Pension”, “Reform”, and then finally ”referr” was run using ArtiFasts search feature. Returned entries in Apple Filesystem Events artifact from “referr” showed a folder of possible interest “mobile/Library/News/com.apple.news.public-com.apple.news.private-production/referralItems/com.apple.news.widget/*”.
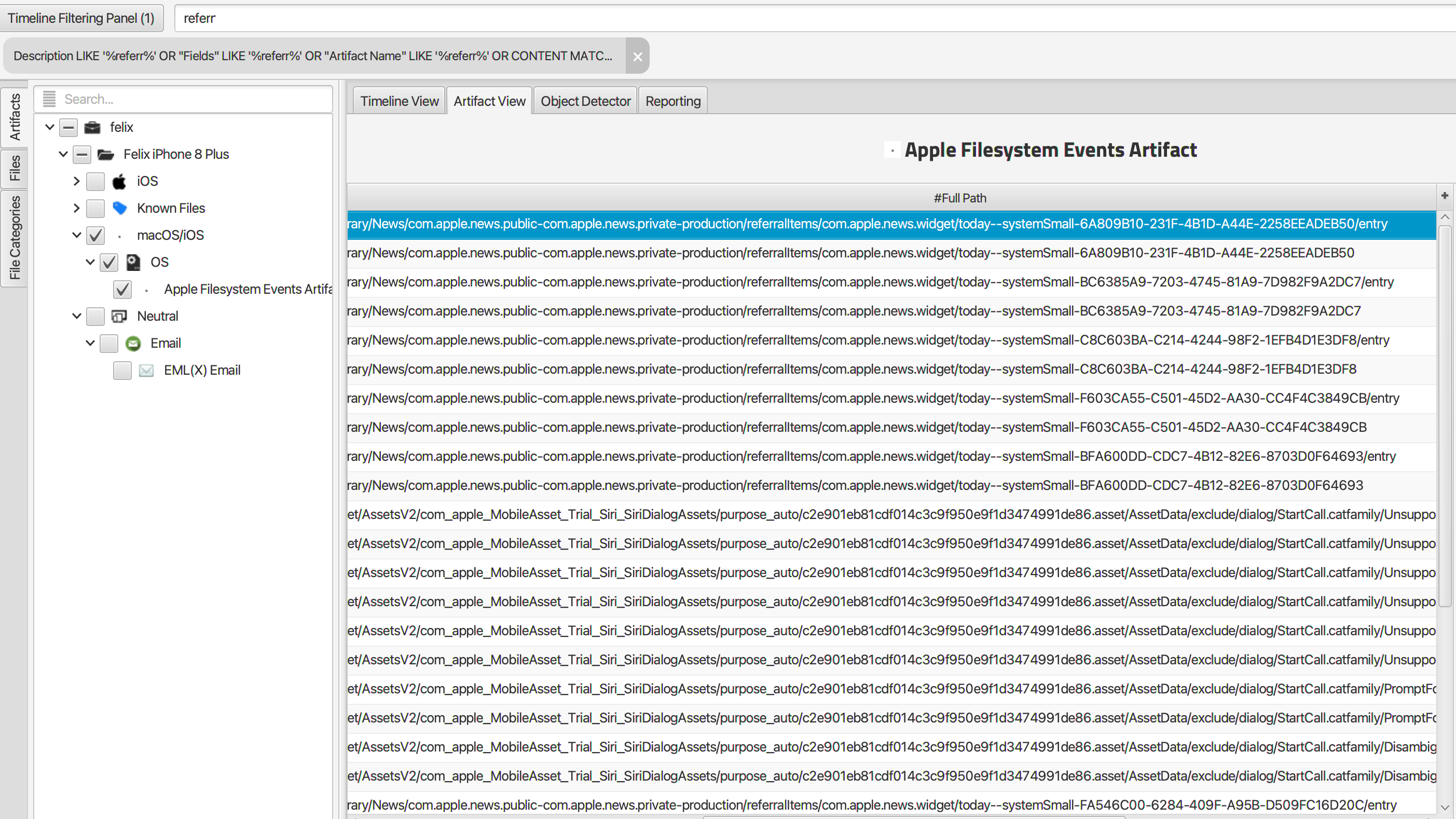
On following the path, it led to folders with “entry” files in them. Json files with base64 encoded data under the key “resultsData”.
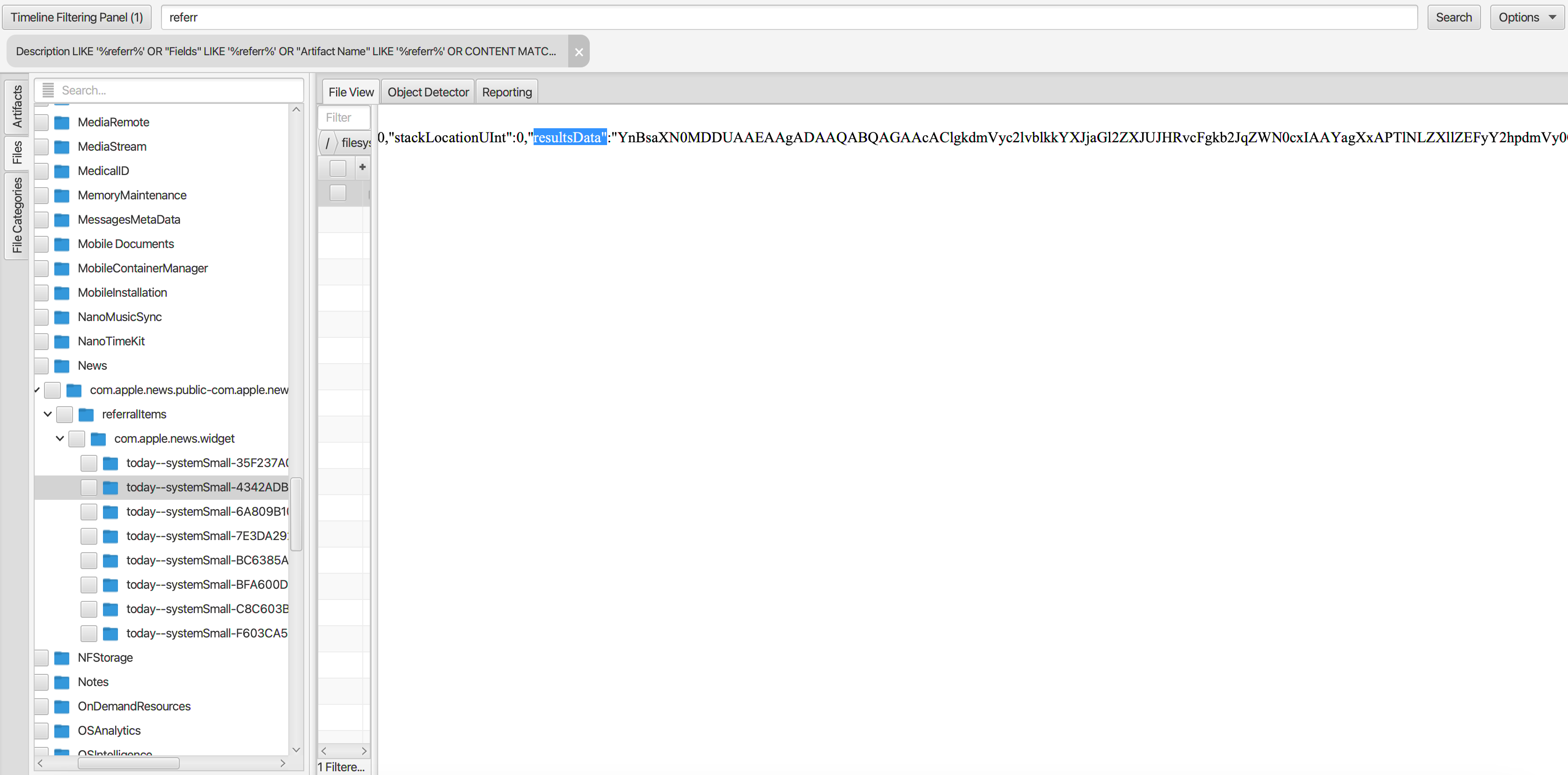
Once decoded, we obtain a binary plist which upon deserialisation has no SID, but it did contain multiple base64 encoded data. Decoding the data strings within we finally obtain a json with the SID string.