Android Imgur
24/10/2025 Friday
Imgur is a free image-sharing and hosting app and website that allows
users to upload, view, and share photos, GIFs, and memes. It serves as
both an image host and a social platform where users can explore
trending visual content and engage with a vibrant online community. It
is a cross-platform app, available on the web, iOS, and Android, making
it accessible to users across different devices.
Digital Forensics Values of Android Imgur
The artifacts recovered from the Android Imgur app’s left-behind data
can provide valuable forensic evidence. These artifacts can be used to
identify user account credentials, such as usernames and email
addresses, and to reconstruct user activity within the app.
Specifically, they can reveal what media content was viewed, uploaded,
or shared by the user, along with associated timestamps that indicate
when these actions occurred.
Location of Android Imgur Artifacts
Android Imgur artifacts can be found at the following locations:
*/data/data/com.imgur.mobile/databases/imgur.db
*/data/data/com.imgur.mobile/shared_prefs/com.imgur.mobile_preferences.xml
Analyzing Android Imgur Artifact with ArtiFast
This section will discuss how to use ArtiFast to extract Android Imgur
artifact from Android machines’ files and what kind of digital forensics
insights we can gain from the artifact.
After you have created your case and added evidence for the
investigation, at the Artifact Selection phase, you can select Android
Imgur artifact parsers:
×
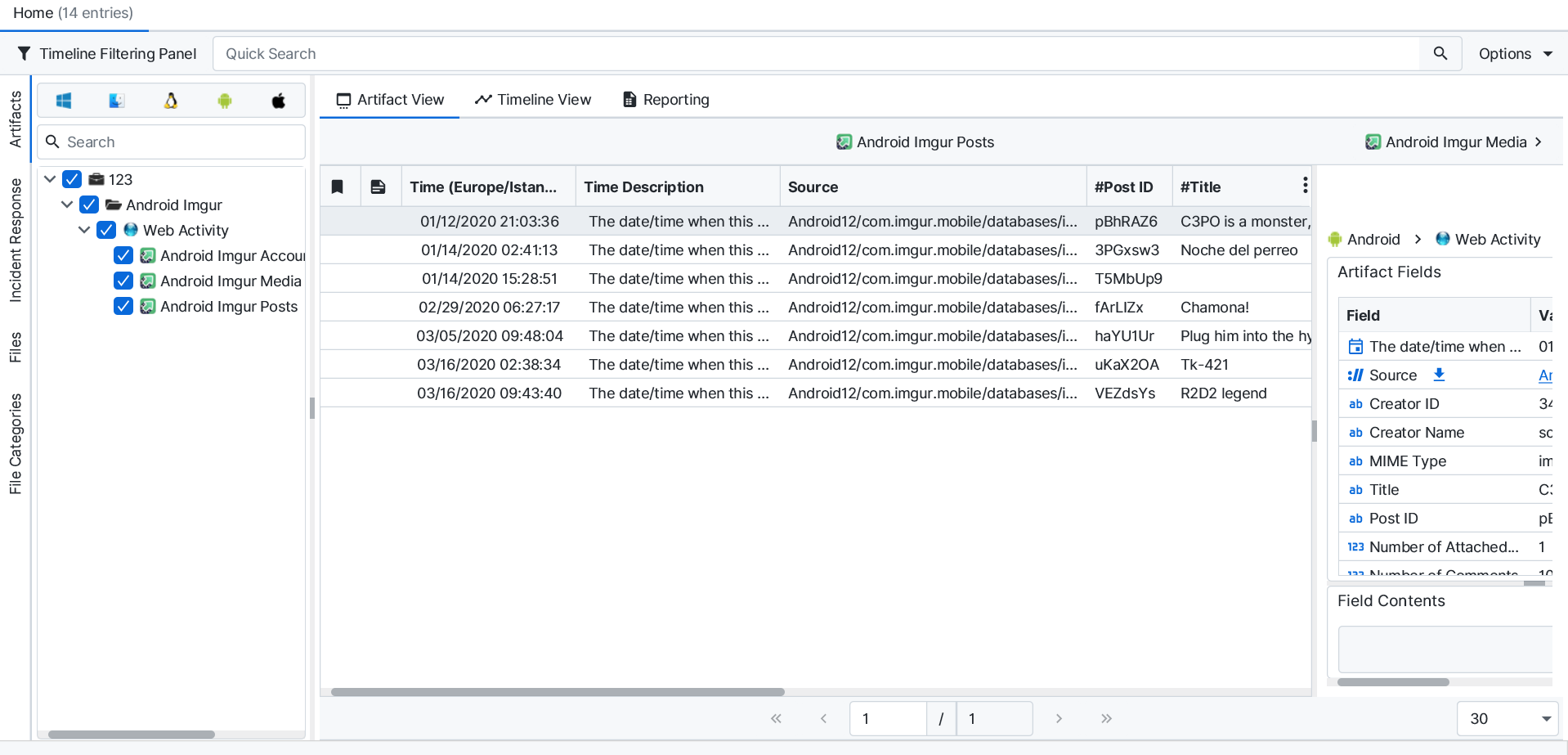
Once ArtiFast parsers plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Android Imgur artifacts in ArtiFast.
Android Imgur Media
- Username: The username.
- Account ID: The account Unique Identifier.
- Email Address: The email addresses registered by this account holder.
Android Imgur Posts
- Post ID: The post ID.
- MIME Type: The type of the data stored in this post.
- Title: The title of this post.
- Creator ID: The ID of the creator of this post.
- Creator Name: The name of the creator of this post.
- Post Date/Time: The date/time when this post has been published on Imgur.
- Number of Attached Images: The number of the attached images to this post.
- Number of Comments: The number of comments on this post.
Android Imgur Account Information
- Username: The username.
- Account ID: The account Unique Identifier.
- Email Address: The email addresses registered by this account holder.
For more information or suggestions please contact: kalthoum.karkazan@forensafe.com
