Investigating Default Web Browser on Windows
23/06/2023 Friday
A web browser is an application that is developed to browse the internet and access the websites. Although all browsers are trying to provide their users with the best browsing experience, each one of them has its own unique features. The default browser is the browser chosen by the user to be launched automatically by the OS whenever a link is clicked. Different users choose different browsers to be their default browsers according to which one provides the features that match their preferences.
Digital Forensics Value of Default Browser
Most of the illegal actions include some web activities, so knowing the default browser can guide the investigators and helps them narrowing the searching scope and revealing more information by investigating the founded default browser’s related artifacts. It also can contribute in understanding the accused’s personality and his own personal preferences.
Location and Structure of Default Browser Artifact
The following registry location contains the default browser artifact:
HKCU\Software\Microsoft\Windows\Shell\Associations\UrlAssociations\https\UserChoice
Analyzing Default Browser Artifact with ArtiFast
This section will discuss how to use ArtiFast to extract Default Browser artifact from Windows machines and what kind of digital forensics insight we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Windows OS Default Browser artifact:
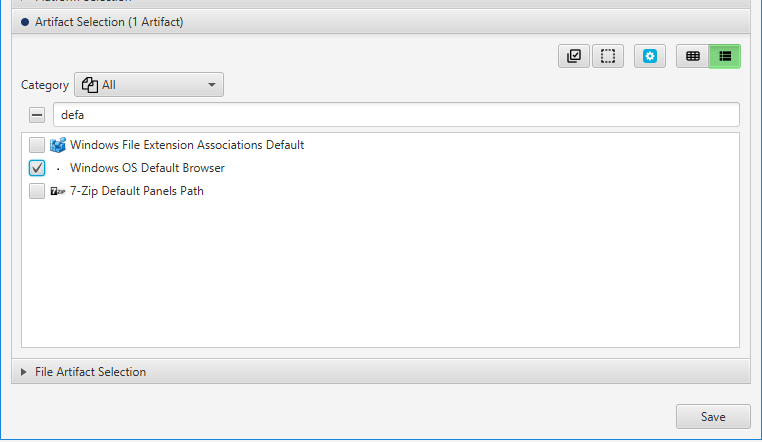
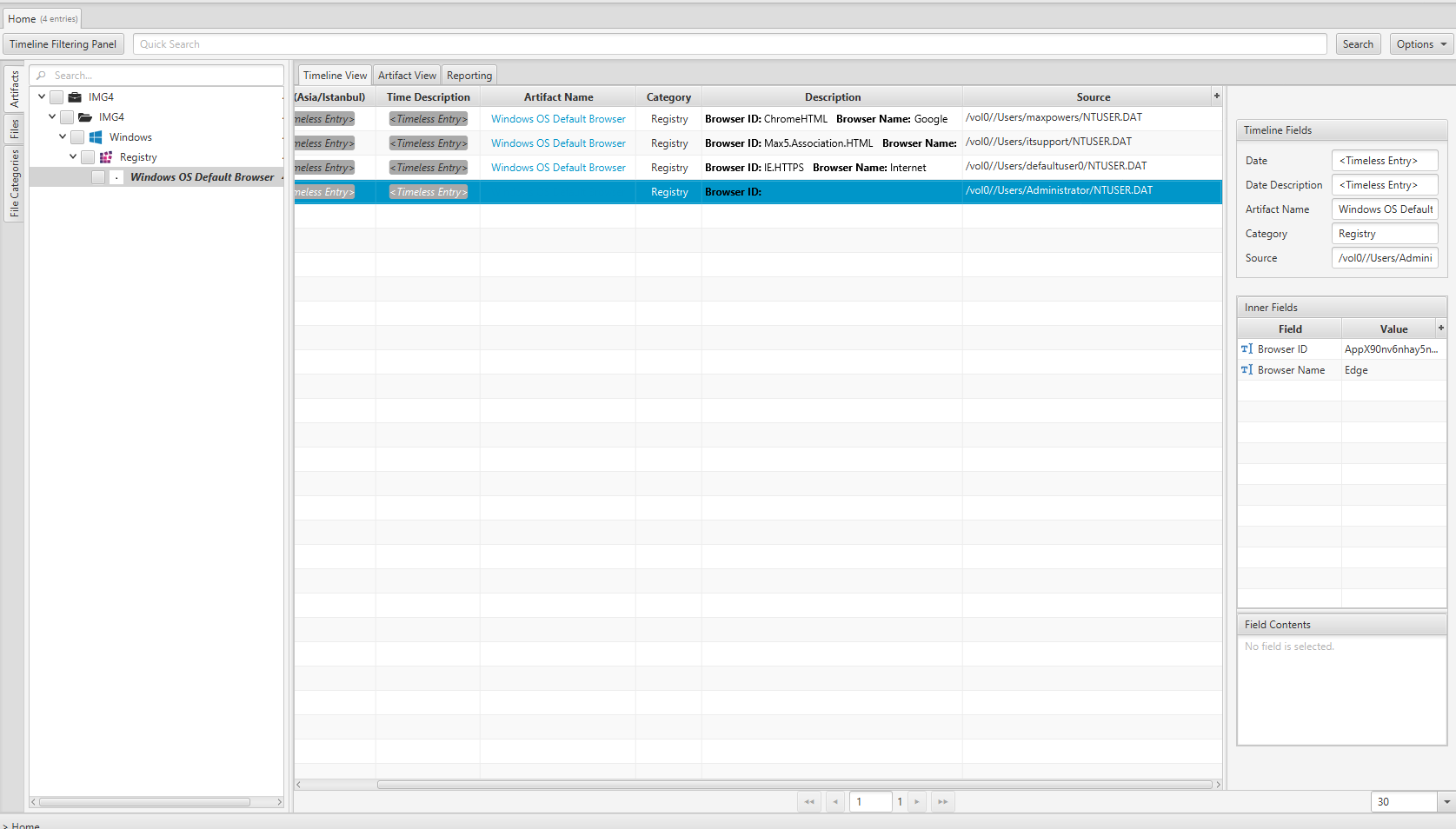
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Windows Default Browser artifact in ArtiFast.
Windows OS Default Browser
- Browser Name - The name of the default browser.
- Browser ID - The ID of the default browser.
For more information or suggestions please contact: kalthoum.karkazan@forensafe.com
