Investigating PowerShell
09/07/2021 Friday
PowerShell is an object-oriented framework, which consists of a command line shell and scripting language. The shell comes installed by default on every Windows computer and can be installed on Mac and Linux computers. It enables its users to automate administrative tasks and manage configurations in the Windows environment. PowerShell is built on top of the .NET framework, it automates tasks with cmdlets, scripts, executables, and standard .NET classes. It contains hundreds of basic cmdlets such as getting an item's location, moving ,copying, and removing an item. PowerShell also allows for new cmdlet functions to be written using any text editor.
Digital Forensics Value of PowerShell Artifacts
PowerShell is a popular tool among sysadmins and experienced Windows users. It can cause huge configuration changes to a system and give users access to the filesystem as well as other data stores such as registry. Being able to know how the shell was used is of forensic value. Windows 10 PowerShell version 5 saves the history of executed commands which is not done in the older versions of Windows.
Location of PowerShell Artifacts
When a command is executed in PowerShell, it is recorded and stored at
the location:
C:\Users\[Username]\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_History.txt.
The command "(Get-PSReadlineOption).HistorySavePath" can be run
to show the current location of the file.
Structure of PowerShell Artifacts
The structure of the file containing the PowerShell recent commands is a text file. One command per line.
Analyzing PowerShell Artifacts with ArtiFast Windows
This section will discuss how to use ArtiFast Windows to extract
PowerShell artifacts from Windows machines and what kind of digital
forensics insight we can gain from the artifacts.
After you have created your case and added evidence for the
investigation, at the Artifact Parser Selection Phase, you can select
PowerShell Artifact:
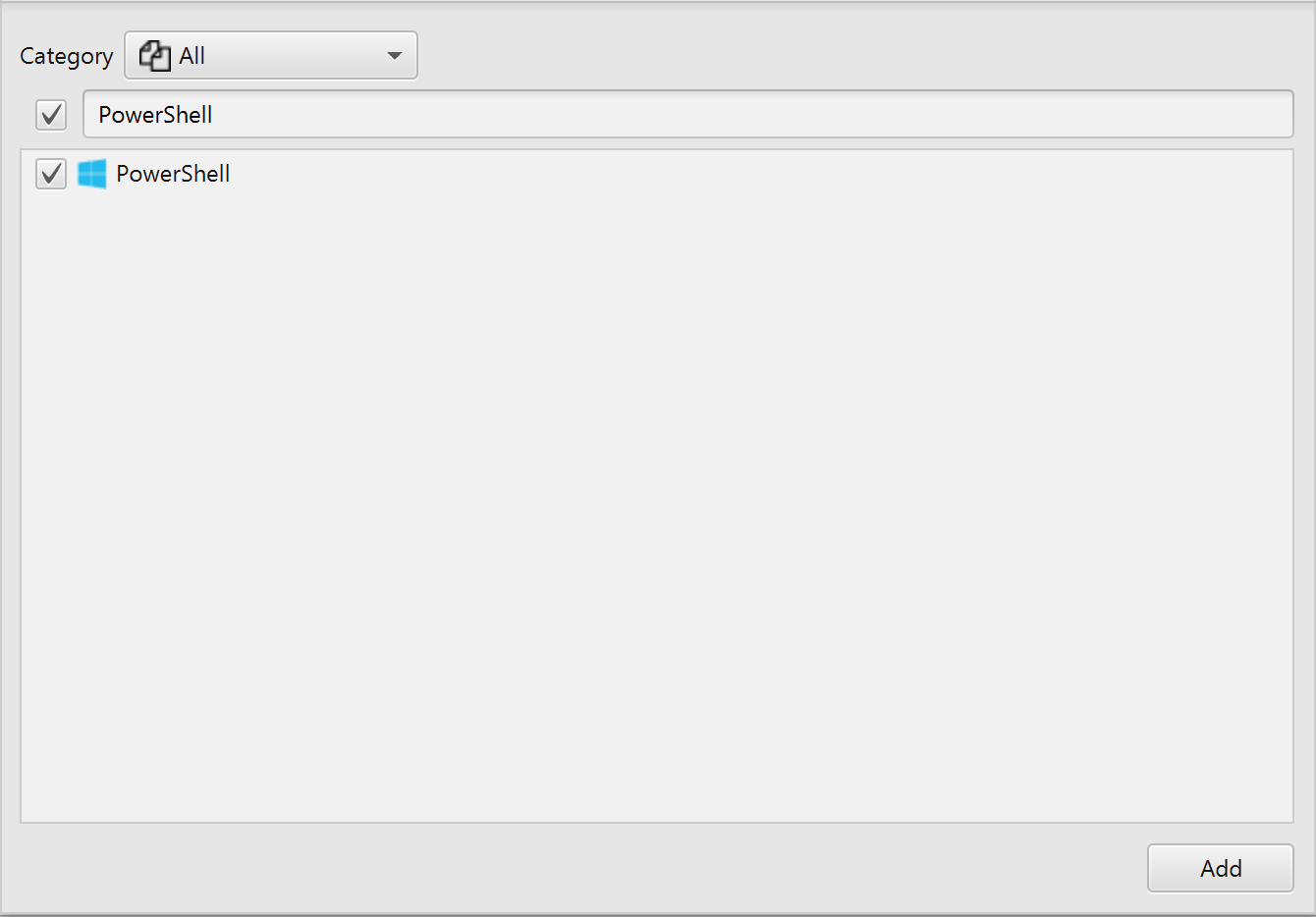
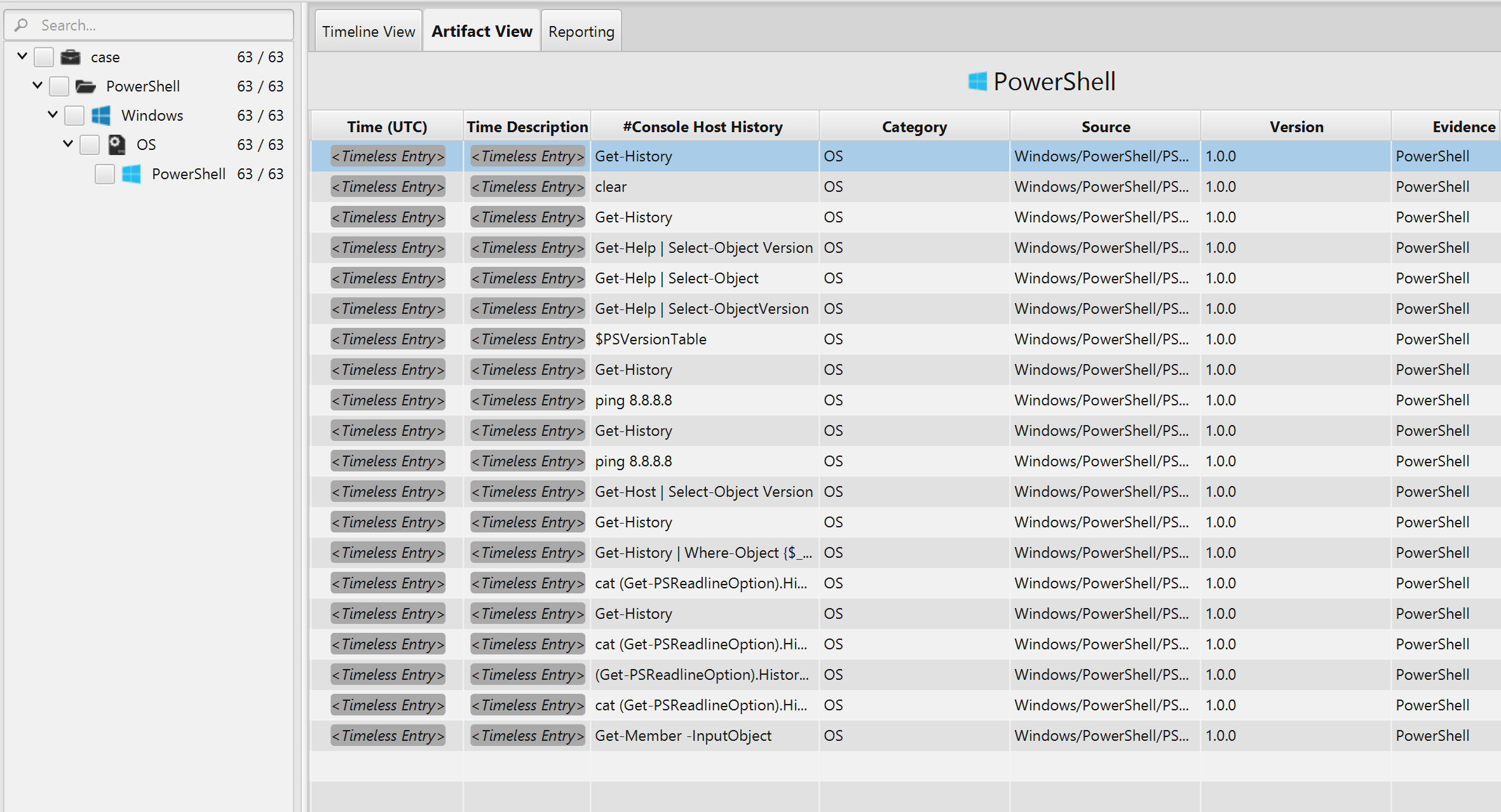
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via "Artifact View" or "Timeline View," with indexing, filtering, and searching capabilities. Below is a detailed description of the PowerShell artifact in ArtiFast software.
PowerShell Recent Commands Artifact
The artifact
contains the commands executed using the shell. The commands can be seen
in the "Console Host History" field. There are timestamps associated
with the command therefore ArtiFast parses them as timeless entries.
