Investigating Android IMO
17/11/2023 Friday
The Android IMO app, developed by PageBites Inc, is a free messaging application known for its user-friendly interface and strong focus on security. With features such as text messaging, voice and video calls, media sharing, and group chats, IMO offers comprehensive messaging experience. It employs end-to-end encryption for message privacy and allows users to set self-destruct timers for added security.
Digital Forensics Value of Android IMO
IMO as most of instant messaging application; holds significant value in digital forensics. With its widespread use and diverse features, analyzing the artifacts left behind by IMO can provide valuable insights for forensic investigations. As an integral mode of communication, IMO's messages, media files, and call records can offer crucial evidence in tracking and uncovering illicit activities.
Location and Structure of Android IMO Artifacts
Android IMO artifacts records are in database in the SQLite format which can be found at the following location:
\data\data\com.imo.android.imoim\
Analyzing Android IMO Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract Android IMO artifact from Android device's files and what kind of digital forensics insights we can gain from the artifact.
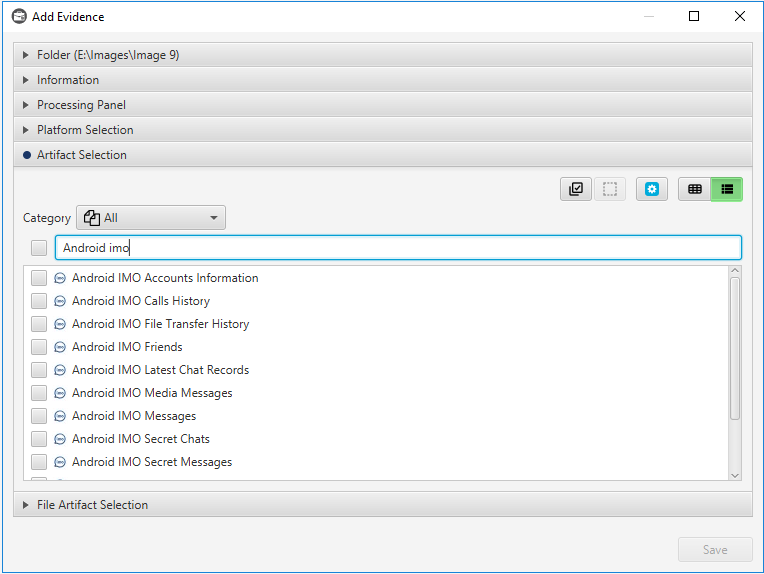
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Android IMO artifact:
×
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Android IMO artifact in ArtiFast.
Android IMO Account Information
- Account Name: The username.
- Phone Number: The user’s phone number.
- Country Code: The phone number’s country code.
Android IMO Friends Information
- Friend Name: The friend’s username.
- Display Name: Friend’s display name.
- Number of Times Contacted: The number of times user contacted this friend.
Android IMO File Transfer History
- Time: File transfer date and time.
- File Name: The file name.
- File Size: The file size.
- File Path: The file location’s path.
- Extension: The file extension.
- Direction: Indicates whether the file was sent or received.
Android IMO Calls
- Time: Date and time of the call.
- Caller/Callee Name: Username of the Caller or Callee.
- Chat Type: Indicates whether the call is incoming or outgoing.
- Duration: Call duration in milliseconds.
- Call State: Indicates whether the call was answered or missed.
- Call Type: Indicates whether the call was a video or audio call.
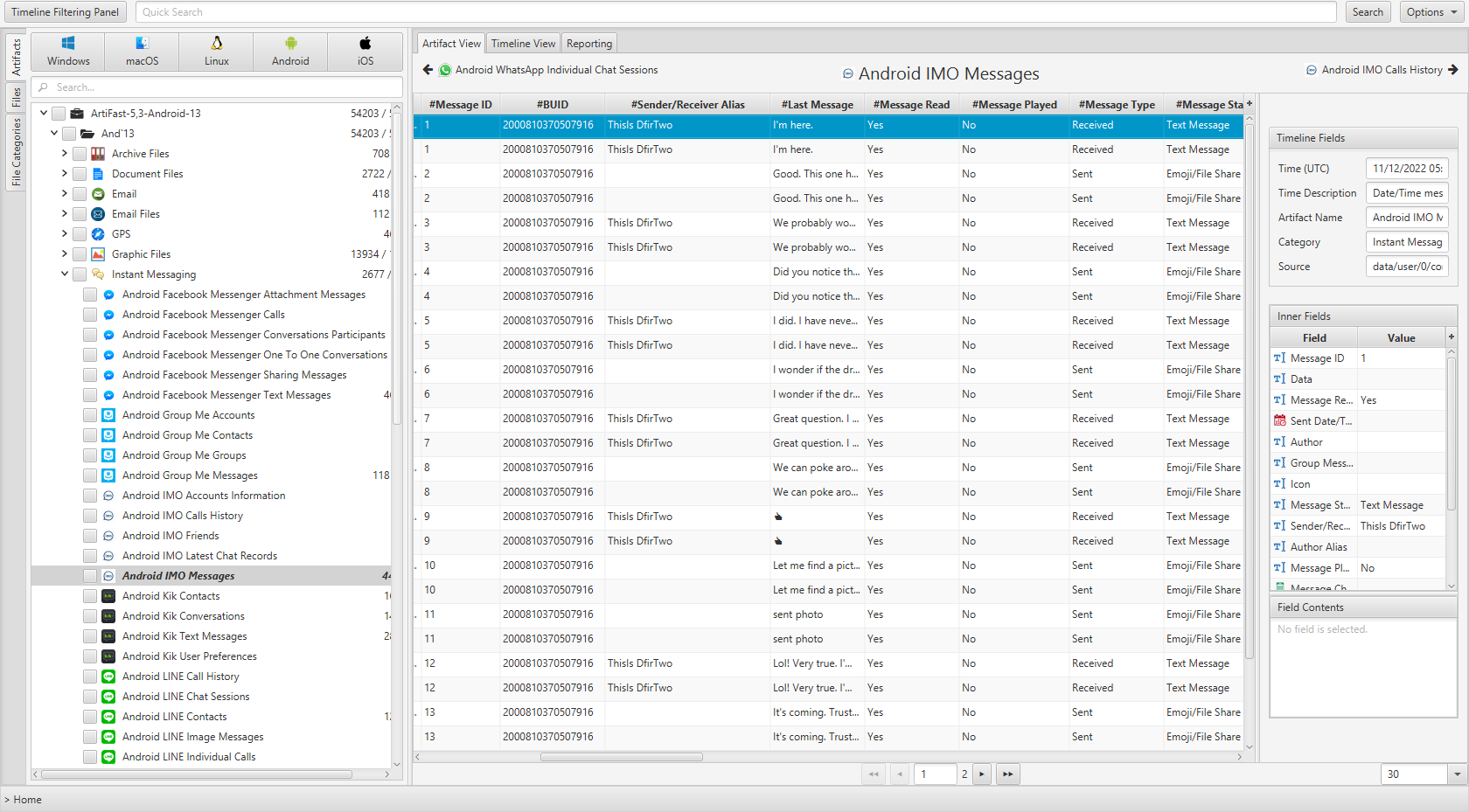
Android IMO Messages
- Time: Date and time when the message was received.
- Alias: User’s alias identifier.
- Last Message: Last message in this chat.
- Message Type: Indicates whether the message was sent or received.
- Message State: Indicates whether the message contains text, emoji, or else.
- Message Read: Indicates whether the message was read or not.
Android IMO User Channels
- Time: Date and time of the last message in the channel.
- User Channel ID: Channel’s ID.
- Channel Name: Channel’s name.
- Description: Channel’s description.
- Channel Type: Channel’s type.
- Channel Status: Channel’s owner related information.
Android IMO Secret Messages
- Time: Date and time when the message was received.
- Name: Participants’ username.
- Last Message: Last message in this chat.
- Message Type: Indicates whether the message was sent or received.
- Message body: Message text.
Android IMO Stories
- Time: Date and time when the story was shared.
- Data: Information about the story’s media.
- Object URL: Shared Object’s URL.
- Type: Photo/Video.
- Duration: Video duration in seconds.
For more information or suggestions please contact: ekrma.elnour@forensafe.com
