Investigating Android Downloads
06/10/2023 Friday
When an Android device’s user downloads a file from the internet or receives it via emailing/messaging apps, this file is often end up to be stored by default in the Downloads folder on the device. This folder can contain a variety of file types, including documents, images, videos, audio files, and application packages (APK files).
Digital Forensics Value of Android Downloads
Downloads folder on an Android device can serve as a rich source of digital evidence, so examining the contents of it can help forensic experts reconstruct events, establish timelines, identify patterns of behavior, and uncover important details related to various types of digital crimes and activities.
Location of Android Downloads Artifacts
Android Downloads artifacts can be found at the following location:
com.android.providers.downloads/databases/downloads.db
Analyzing Android Downloads Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract Android Downloads artifact from Android device's files and what kind of digital forensics insights we can gain from the artifact.
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Android Downloads artifact:
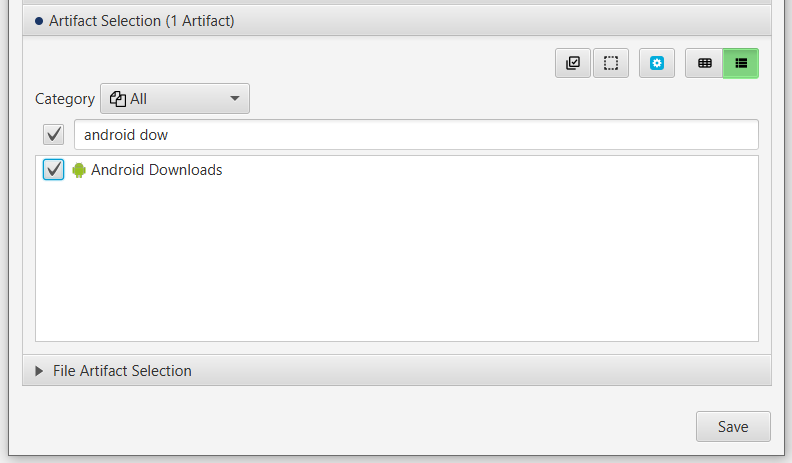
×
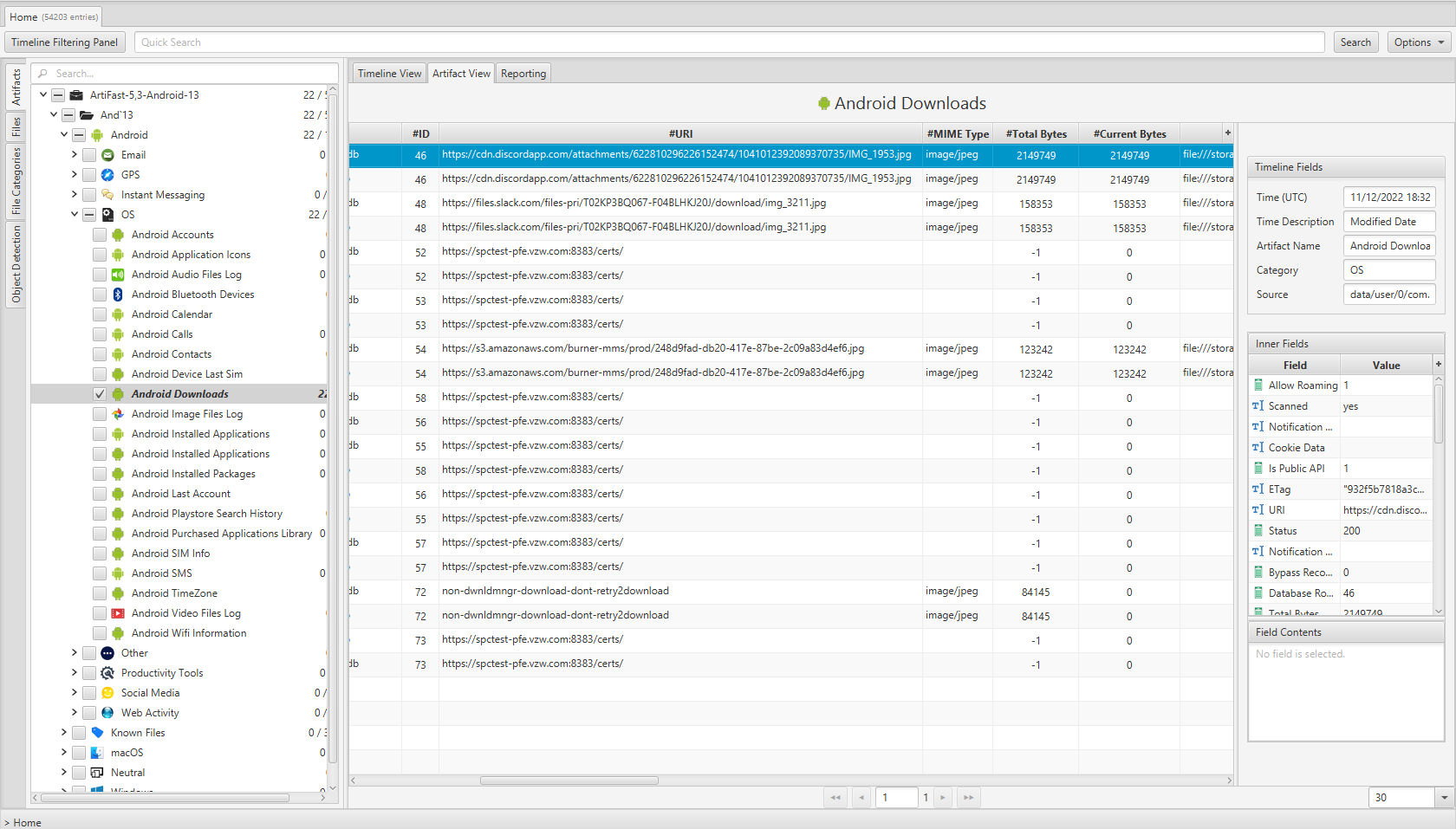
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Android Calls artifact in ArtiFast.
Android Downloads
- Modified Date: Last modified date/time.
- ID: Downloaded file ID.
- Download Source: The URL of the downloaded file.
- MIME Type: The type of the data stored in this file.
- Total Bytes: The total size of the downloaded file in bytes.
- Current Bytes: The number of bytes that have been downloaded already.
- Status: Indicates whether this file has been downloaded successfully or not.
- Saved To: The local path where this file has been saved to.
- Deleted: Indicates whether this file has been deleted or not.
- Notification Package: Notification package.
- Title: The name of the downloaded file.
- Media Provider URI: The URI of the media provider App.
- Error Message: The reason for the error happened while downloading this file.
- Database Row ID: Downloaded file ID.
- Visibility: Indicates whether this file is visible in the downloaded folder or not.
- ETag: ETag of this file.
- Description: The description of the downloaded file.
For more information or suggestions please contact: kalthoum.karkazan@forensafe.com
