Investigating Android Accounts
15/09/2023 Friday
As we use our smartphones to access various apps, we often provide our login credentials to those applications. Android accounts artifact contains information related to the different user accounts registered in the mobile phone throughout various applications.
Digital Forensics Value of Android Accounts
Android Accounts artifact stores records of all the user accounts that have been used on a device, including email accounts, social media accounts, and other online services. This data can be critical in identifying who has accessed the device and what they have accessed.
Location of Android Accounts Artifacts
Android Accounts artifacts can be found at the following locations:
/system_ce/0/accounts_ce.db
/system_de/0/accounts_de.db
data/com.android.vending/shared_prefs/lastaccount.xml
data/com.google.android.gms/shared_prefs/BackupAccount.xml
Analyzing Android Accounts Artifacts with ArtiFast
This section will discuss how to use ArtiFast to extract Android Accounts artifact from Android machines’ files and what kind of digital forensics insights we can gain from the artifact.
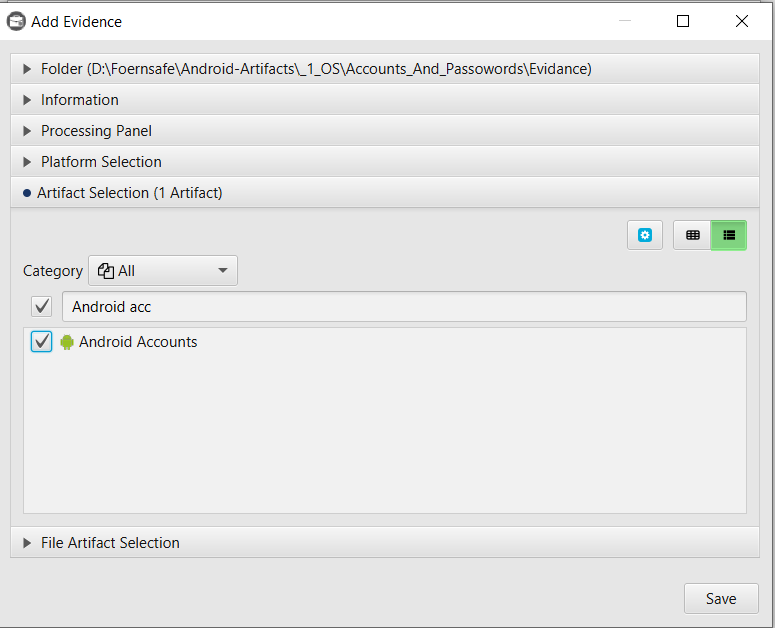
After you have created your case and added evidence for the investigation, at the Artifact Selection phase, you can select Android Accounts artifact:
×
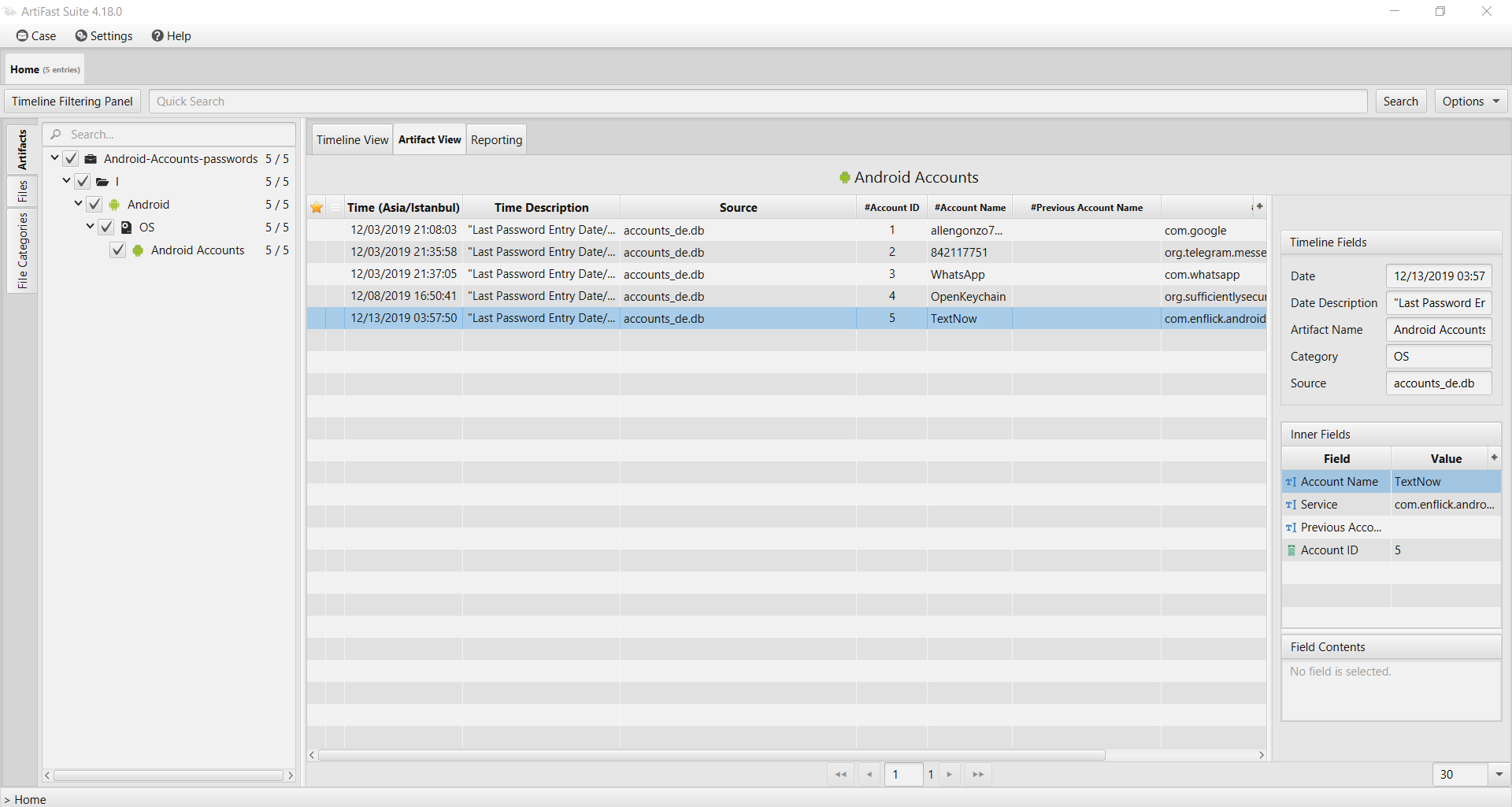
Once ArtiFast parser plugins complete processing the artifact for analysis, it can be reviewed via “Artifact View” or “Timeline View,” with indexing, filtering, and searching capabilities. Below is a detailed description of Android Accounts artifact in ArtiFast.
Android Accounts
- Date: The date and time when the password was last entered.
- Account Name: User account name.
- Service: The name of the application as seen by the device.
- Previous Account Name: User previous account name.
- Account ID: User account ID.
For more information or suggestions please contact: ekrma.elnour@forensafe.com
